SD-WAN
Plan Your Topology for SD-WAN with Auto VPN
Table of Contents
Expand All
|
Collapse All
SD-WAN Docs
-
-
-
-
- 3.4
- 3.3
- 3.2
- 3.1
- 3.0
- 2.2
- 2.1
- 2.0
- 1.0
-
Plan Your Topology for SD-WAN with Auto VPN
Create a VPN cluster to group branches and hubs that communicate with each other into
a logical group.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
In your SD-WAN configuration, you must configure one or more VPN
clusters to determine which branches communicate with which hubs and creates a
secure connection between the branch and hub devices. VPN clusters are logical
groupings of devices, so consider things such as geographical location or function
when logically grouping your devices.
PAN-OS 10.0.2 and earlier releases support only the hub-spoke SD-WAN VPN
topology.
SD-WAN full mesh VPN
topology
is supported in PAN-OS 10.0.3 and later releases.
PAN-OS®
10.0.3 and
later releases
support
both hub-spoke and full mesh SD-WAN VPN topologies. In a hub-spoke
topology, a centralized firewall hub at a primary office or location acts as the
gateway between branch devices. The hub-to-branch connection is a VPN tunnel. In
this configuration, traffic between branches must pass through the hub.
The first time you configure a virtual SD-WAN
interface with direct internet access (DIA) links for an SD-WAN hub or branch firewall, a VPN cluster called
autogen_hubs_cluster is automatically created and
the SD-WAN firewall is automatically added to the VPN cluster. This
allows the Panorama® management server to monitor SD-WAN application and link
performance for devices that are protected by the SD-WAN
firewall and accessing resources outside of your corporate network. Additionally,
any SD-WAN firewall with DIA links that you configure in the future
are automatically added to the autogen_hubs_cluster VPN
cluster containing all hubs and branches with DIA links to enable Panorama to
monitor application and link performance. The
autogen_hubs_cluster is purely for monitoring
application and link health, and not to create VPN tunnels between the hubs and
branches with DIA links. If you need to connect hubs and branches with VPN tunnels,
you must create a new VPN cluster and add all the required hubs and branches to that
cluster.
When you select the Pre-shared key as an
Authentication Type, a strong, random IKE pre-shared key
is created for all hubs and branches in the VPN cluster to secure the VPN tunnels,
and each firewall has a master key that encrypts the pre-shared key.
The SD-WAN plugin generates
the pre-shared key and encrypts it with the master key of Panorama. When you push
the SD-WAN plugin configuration to the firewall, the firewall must have the same
master key to decrypt the pre-shared key shared by the SD-WAN plugin. That is, the
master key must match between the Panorama
and its managed firewalls. Otherwise, the push will fail on the SD-WAN firewalls.
The system secures the pre-shared key, even from the administrator.
Beginning
with PAN-OS 9.1.2,
you
can refresh the IKE pre-shared key, which Panorama sends to all members of the
cluster.
Refresh the pre-shared key when cluster members aren't
busy.
(SD-WAN 3.2.0
and later versions)When you select
Certificate as the Authentication
Type, then the hubs and branches in the SD-WAN VPN
cluster is based on the certificate-based
authentication.
After the SD-WAN Plugin is upgraded to 2.1.0, the hub and branch
firewalls in a single VPN cluster must all run either PAN-OS 10.0.4 (or a later 10.0
release) or 10.1.0, not a combination of the two releases.
When viewing VPN clusters, if no data is present or the screen indicates that SD-WAN is undefined, check in the Compatibility Matrix that the Panorama
release you're using supports the SD-WAN plugin release you're trying
to use.
SD-WAN plugin 3.2.0 and later versions support IPv6 interfaces and
IPv6 tunnels. Whether an IPv4 or IPv6 IPSec tunnel is formed
between two Ethernet ports (or subinterface or AE interface) (DIA link) depends on
whether the Ethernet interface (or subinterface or AE interface) has an IPv4 or IPv6
address. If both of the interfaces have an IPv4 address, an IPv4 tunnel is brought
up. If both of the interfaces have an IPv6 address, an IPv6 tunnel is brought up. In
the case of dual stack, an IPv4 tunnel is brought up.
The tunnel interface IP address comes from the VPN pool. You can create an IPv6
address pool independent of an IPv4 address pool. If both IPv4 and IPv6 addresses
are configured, the tunnel interface is assigned an IPv4 address only, as shown in
the following table. If the IPv4 VPN address pool is exhausted and an IPv6 address
pool exists, the tunnel interface is assigned an IPv6 address. If only IPv4 is
configured, the tunnel will use an IPv4 address. If only IPv6 is configured, the
tunnel will use an IPv6 address.
| VPN Pool | Configured | ||
|---|---|---|---|
| IPv4 | Yes | Yes | No |
| IPv6 | Yes | No | Yes |
| Tunnel Interface IP | IPv4 Only | IPv4 Only | IPv6 Only |
PAN-OS & Panorama
In PAN-OS, create a VPN cluster to group branches and hubs that communicate with each
other into a logical group.
- Plan your branch and hub VPN topology to determine which branches communicate with each of your hubs. For more information, see plan your SD-WAN configuration.Log in to the Panorama Web Interface.(PAN-OS 9.1.2 and later versions, and SD-WAN plugin 1.0.2 and later versions) Specify IP address ranges for the IPSec VPN tunnels that Auto VPN configuration creates.Auto VPN configuration creates a VPN tunnel between a hub and branches and assigns IP addresses to the tunnel endpoints. Enter subnet ranges that you want Auto VPN to use as VPN tunnel addresses. You can enter up to 20 IP prefix/netmask ranges. Auto VPN draws from that pool for VPN tunnel addresses, drawing from the largest range (for the address family) first, and then drawing from the next largest range when necessary. You must configure at least one range for the pool. If you don’t perform this step before pushing the configuration to a hub or branch, the Commit and Push will fail.If you upgrade from an earlier SD-WAN Plugin release, you must check that your ranges are still correct. If they aren't, enter new ranges. After you Commit, all tunnels are dropped and new tunnels are used, so perform this task during a time you have low traffic.
- Select PanoramaSD-WANVPN Clusters.At the bottom of the screen, select VPN Address Pool.
![]() Select IPv4 or IPv6 and Add an address pool with one or more (up to 20) Member IP address and netmask ranges, for example, 192.168.0.0/16 or 2001::/16, respectively.Click OK.
Select IPv4 or IPv6 and Add an address pool with one or more (up to 20) Member IP address and netmask ranges, for example, 192.168.0.0/16 or 2001::/16, respectively.Click OK.![]() (SD-WAN plugin 2.2.0 and later versions) Don't simply change an existing address pool if Prisma Access is onboarded. If you need to change an address pool, perform the following steps during a maintenance window to update the branch and the Panorama CN with your address pool changes:
(SD-WAN plugin 2.2.0 and later versions) Don't simply change an existing address pool if Prisma Access is onboarded. If you need to change an address pool, perform the following steps during a maintenance window to update the branch and the Panorama CN with your address pool changes:- Use Panorama to access an SD-WAN branch and delete the existing onboarding that the address pool change will impact; then do a local Commit.
- Update the VPN address pool, and then do a local Commit.
- Perform the Panorama onboarding again, and then do a local Commit and Push.
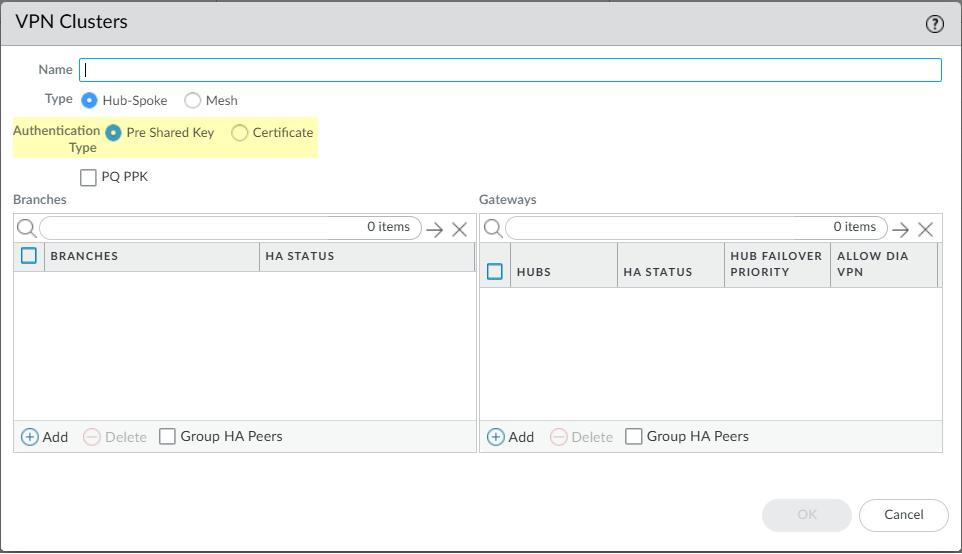
Configure the VPN cluster. Repeat this step to create VPN clusters as needed.- Select PanoramaSD-WANVPN Clusters and Add a VPN cluster.Enter a descriptive name for the VPN cluster.Underscores and spaces are not supported in the VPN cluster name and result in monitoring (PanoramaSD-WANMonitoring) data for the cluster not to be displayed. Choose the name of the VPN cluster carefully so you do not need to change the name in the future. SD-WAN monitoring data is generated based on the old cluster name and cannot be reconciled to a new cluster name, and will cause issues with the number of reported clusters when monitoring your VPN clusters or generating reports.Select the VPN cluster Type.Only Hub-Spoke VPN cluster type is supported in PAN-OS 10.0.2 and earlier 11.0 versions. Beginning with PAN-OS 10.0.3, you can Create a Full Mesh VPN Cluster with DDNS Service.(SD-WAN plugin 3.2.0 and later versions) Select the Authentication type: Pre Shared Key or Certificate. It's mandatory to specify the authentication type to add a device in a VPN cluster. A VPN cluster should have the same authentication type selected for all its devices.
![]() When you select the authentication type for a VPN cluster, only the branches and hubs that are configured with the same authentication type (as the VPN cluster) can be added to the VPN cluster. For example, when you select certificate as the authentication type for a VPN cluster, then all the hubs and branches that are added to the cluster should be configured with certificate as the authentication type.You can't modify the authentication type or VPN cluster name of a VPN cluster that has been configured already. To make a change, remove the VPN cluster and its SD-WAN devices and configure it again using the new authentication type or VPN cluster name. By default, we support the pre-shared authentication type for the devices in a VPN cluster (if the certificate method is not selected manually).
When you select the authentication type for a VPN cluster, only the branches and hubs that are configured with the same authentication type (as the VPN cluster) can be added to the VPN cluster. For example, when you select certificate as the authentication type for a VPN cluster, then all the hubs and branches that are added to the cluster should be configured with certificate as the authentication type.You can't modify the authentication type or VPN cluster name of a VPN cluster that has been configured already. To make a change, remove the VPN cluster and its SD-WAN devices and configure it again using the new authentication type or VPN cluster name. By default, we support the pre-shared authentication type for the devices in a VPN cluster (if the certificate method is not selected manually).- One you've configured the VPN cluster, you cannot change the cluster name or its authentication type (both cluster and device level).
- You cannot have different authentication types within a single VPN cluster. That is, a VPN cluster authentication type must match with all the SD-WAN devices in the VPN cluster. Any difference would result in a commit failure.
- You can have different VPN clusters with different authentication types configured.
- In a VPN cluster, you cannot have SD-WAN devices with different authentication types selected. If an SD-WAN hub is part of two VPN clusters, then the two clusters should be configured with the same authentication type.
If you want to change the authentication type to Certificate for an existing VPN cluster, delete the VPN cluster and create it again with the authentication type of your choice.After creating a VPN cluster with certificate authentication type, if you want to downgrade to an PAN-OS or SD-WAN plugin version that does not support certificate authentication type, follow these steps:- Delete the existing VPN cluster. SD-WAN device authentication will automatically change to pre-shared key on downgrade.
- Downgrade to the PAN-OS or SD-WAN plugin version of your preference. See the system requirements for SD-WAN for the minimum PAN-OS and SD-WAN plugin versions required for configuring the certificate authentication type.
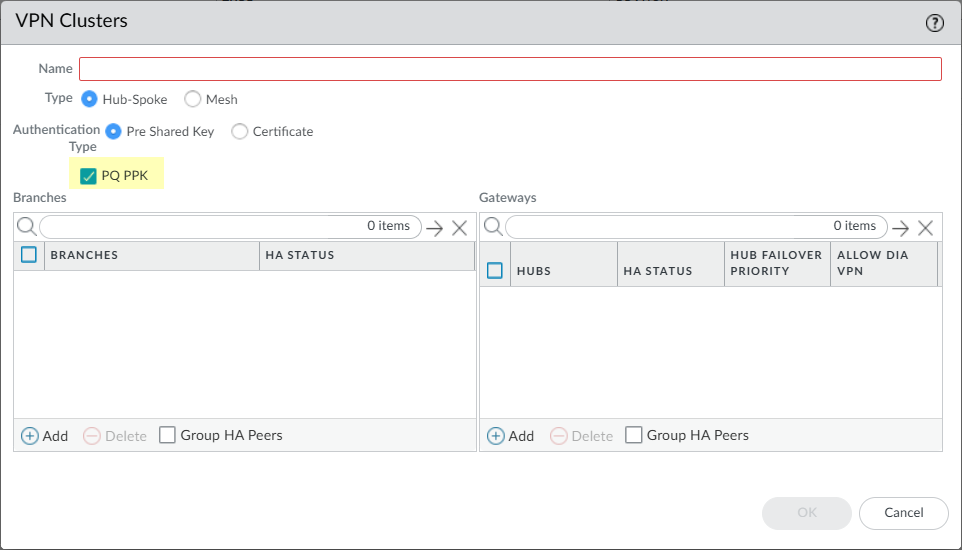
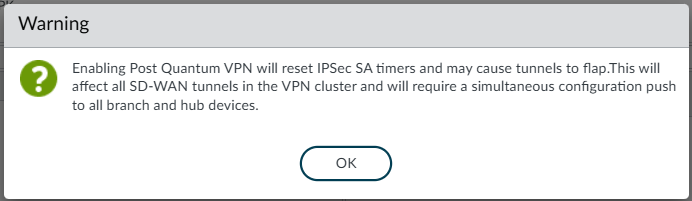
Follow the steps mentioned in the Upgrade and Downgrade Considerations before you upgrade or downgrade your current SD-WAN plugin.(PAN-OS 11.1.8 and later 11.1 versions, SD-WAN plugin 3.2.3 and later 3.2 versions) (PAN-OS 11.2.5 and later 11.2 versions, SD-WAN plugin 3.3.3 and later 3.3 versions) As quantum computing technology advances, traditional encryption methods used in VPNs and other secure communications become increasingly vulnerable to attacks. In Advanced NGFW SD-WAN, we have introduced post-quantum VPN to address this emerging threat with quantum-resistant encryption methods to protect your SD-WAN overlay.Post-Quantum pre-shared key (PQ PPK) is one of the key components of post-quantum VPN that enhances the security of your IPSec tunnels by adding an additional layer of quantum-resistant encryption. The SD-WAN plugin allows you to enable post-quantum VPN features for your VPN clusters and manage the associated settings. When enabled, the plugin automatically generates and manages strong PQ PPKs for your IPSec tunnels. The SD-WAN plugin configures IKE and IPSec Crypto profiles to use quantum-safe algorithms when post-quantum VPN is enabled.Select PQ PPK to enable PQ PPK for your SD-WAN overlay.![]() A warning appears:
A warning appears:![]() Select OK to enable post-quantum VPN for the VPN cluster. The SD-WAN plugin will automatically generate 10 strong PQ PPKs to use with the IPSec tunnels. The SD-WAN plugin will configure the IPSec tunnels to use PQ PPK with the negotiation mode set to preferred.
Select OK to enable post-quantum VPN for the VPN cluster. The SD-WAN plugin will automatically generate 10 strong PQ PPKs to use with the IPSec tunnels. The SD-WAN plugin will configure the IPSec tunnels to use PQ PPK with the negotiation mode set to preferred.![]()
- PQ PPK isn’t supported on the PA-220 firewall.
- PQ PPK is supported only with Pre Shared Key authentication type.
- When multiple VPN clusters with PQ PPK share a hub firewall, then the shared hub firewall cannot simultaneously support some clusters with PQ PPK enabled and others using standard PSK authentication. That is, all VPN clusters connected to a shared hub firewall must either use PSK or use PQ PPK.
- Existing VPN clusters won’t have post-quantum VPN configured by default. This approach ensures there is no disruption to existing IPSec connectivity. However, you have the flexibility to manually enable post-quantum VPN for an existing cluster if desired. When you do so, the IPSec tunnels won’t be immediately affected. Instead, the post-quantum capabilities will be negotiated when the keys expire or when the tunnel is renegotiated. This gradual adoption strategy enables you to implement quantum-safe encryption at your own pace, balancing security enhancements with operational stability.
If you want to refresh the PQ PPK list, use the Refresh PQPPK List in the VPN cluster configuration. It regenerates the new post-quantum pre-shared keys and updates the keys on all SD-WAN devices within the selected VPN cluster.(HA deployments only) For Panorama in HA configuration, all PQ PPK information is synchronized between the active and passive peers, ensuring seamless failover. Similarly, for HA active/passive firewalls, the PQ PPK list and all pre-shared keys, including post-quantum key information, are synchronized between the devices. This synchronization ensures that the PQ PPK configuration remains consistent and operational across the HA pair, maintaining the quantum-safe encryption capabilities of your SD-WAN overlay even during failover events.Add one or more branch devices that you determined need to communicate with each other.- (SD-WAN
plugin
1.0.1 and later
versions)
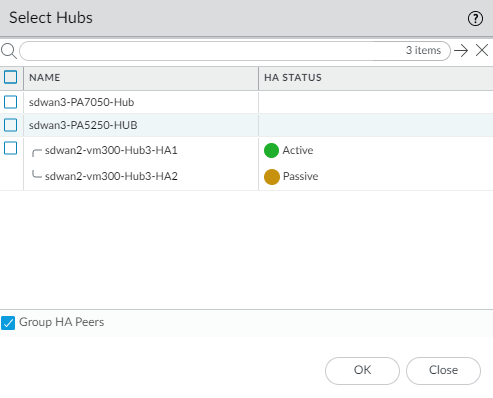
Select Group HA Peers
to display the branch devices that are HA peers together.
![]()
- Select the branch devices to add to the cluster.When configuring VPN clusters with high availability (HA) branch firewalls, both HA peers (active and passive) must be included. If you select one HA peer firewall for a branch, you're required to also select its corresponding HA peer. This ensures that both the active and passive HA peers are part of the VPN cluster configuration.
- Click OK.
Add one or more hub devices that you determined need to communicate with the branch devices.SD-WAN hubs in an HA configuration are considered as a single SD-WAN hub firewall.MPLS and satellite link types will form tunnels with only the same link type; for example, MPLS-to-MPLS and satellite-to-satellite. Tunnels won’t be created between an MPLS link and an Ethernet link, for example.For the SD-WAN versions earlier than 3.1.3, you can add up to four SD-WAN hub firewalls to a VPN cluster.(SD-WAN plugin 3.2.1 and later versions) You can add up to 16 SD-WAN hub firewalls to a VPN cluster. Only four of the 16 hubs can have the same hub priority within a VPN cluster due to ECMP. Any attempt to configure the same priority for more than four SD-WAN hubs would result in a commit error.- (SD-WAN plugin 1.0.1 and later versions) Select Group HA Peers to display the hub devices that are HA peers together.
- Select the hubs to add to the cluster and click
OK.When configuring VPN clusters with high availability (HA) hub firewalls, both HA peers (active and passive) must be included. If you select one HA peer firewall for a hub, you're required to also select its corresponding HA peer. This ensures that both the active and passive HA peers are part of the VPN cluster configuration.
![]()
- For any new or previously existing VPN cluster that has more
than one hub, you must prioritize the hubs to determine a) that
traffic be is sent to a particular hub, and b) the subsequent
hub failover order. The hub failover priority range is 1 to 4.
If you upgrade, the default priority is set to 4. The plugin
internally translates the hub failover priority to a BGP local
preference number as shown in the following table. The lower the
priority value, the higher the priority and local preference. A
cluster supports a maximum of four
hubs for the
SD-WAN
versions earlier than 3.1.3. With
SD-WAN
plugin 3.2.1 and later
versions,
you can add up to 16 SD-WAN
hub firewalls to a VPN cluster. An
active/passive HA pair counts as one hub. Multiple hubs can have
the same priority; an HA pair must have the same priority.
Panorama uses the branch’s BGP template to push the local
preference of the hubs to the branches in the cluster.
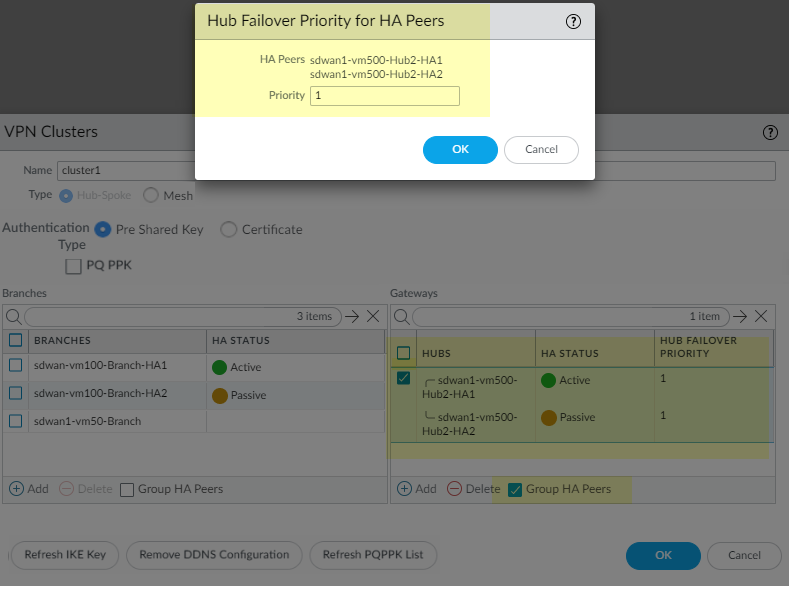
Hub Failover Priority Local Preference 1250220031504100If multiple hubs have the same priority, Panorama enables ECMP in two places on each branch firewall to determine how branches select the path. ECMP is enabled for the virtual router (NetworkVirtual RoutersECMP) and ECMP Multiple AS Support is enabled for BGP (NetworkVirtual RoutersBGPAdvanced). If all hubs in the cluster have a unique priority, ECMP is disabled on the branches. If a hub priority configuration changes, Panorama reevaluates whether to enable or disable ECMP.- If you selected Group HA Peers,
select the pair and click in the Hub Failover
Priority field; enter a single
Priority (range is 1 to 4),
which applies to both hubs in the HA pair, and click
OK.
![]() The Hub Failover Priority for HA Peers window appears only for configured HA pairs. If you add a new HA pair, you must configure the Hub Failover Priority for each of the two new peers independently.You will get an error message if you assign different priorities to hubs that are ungrouped HA peers and then you select Group HA Peers and Submit.
The Hub Failover Priority for HA Peers window appears only for configured HA pairs. If you add a new HA pair, you must configure the Hub Failover Priority for each of the two new peers independently.You will get an error message if you assign different priorities to hubs that are ungrouped HA peers and then you select Group HA Peers and Submit. - For hubs that are not HA pairs, select a hub and click
in the Hub Failover Priority
field; enter a priority (range is 1 to 4).
![]()
- If you selected Group HA Peers,
select the pair and click in the Hub Failover
Priority field; enter a single
Priority (range is 1 to 4),
which applies to both hubs in the HA pair, and click
OK.
Click OK to save the VPN cluster.(PAN-OS 9.1.2 and later versions, and SD-WAN plugin 1.0.2 and later versions) Advertise additional prefixes at the branch to the hub.The firewall automatically redistributes (advertises) all non-public, connected routes from the branch to the hub. You can also redistribute any additional prefixes from the branch to the hub. The Prefix(es) to Redistribute field accepts a list of prefixes, rather than just a single prefix.- Select PanoramaSD-WANDevices and select a branch firewall.Select BGP and Add one or more IP addresses with netmask to Prefix(es) to Redistribute.Click OK.Commit and Commit to Panorama.(SD-WAN plugin 2.0.1 and later 2.0 versions) If your hub firewalls in a hub-spoke VPN cluster have DHCP or PPPoE interfaces, you must use DDNS. Select NetworkInterfacesEthernet and in the Template field, select Template-stack for a hub.(SD-WAN plugin 2.0.1 and later 2.0 versions) Select the interfaces whose IP address indicates Dynamic-DHCP Client or PPPOE, click Override on the bottom of the screen, and click OK to close.(SD-WAN plugin 2.0.1 and later 2.0 versions) Verify on Panorama that the DDNS settings were configured.
- Select NetworkInterfacesEthernet and select the same interface again.Select AdvancedDDNS.See that the DDNS settings were automatically configured with a Hostname and the Vendor set to Palo Alto Networks DDNS.Click OK.(SD-WAN plugin 2.0.1 and later 2.0 versions) Commit and Commit to Panorama.Push the configuration to the hub(s).When Panorama creates virtual SD-WAN interfaces for hubs, Panorama doesn't necessarily create the interfaces using contiguous interface numbers. It might randomly skip an interface number, for example, sdwan.921, sdwan.922, sdwan.924, sdwan.925. Despite the discontiguous numbering, Panorama creates the correct number of SD-WAN interfaces. Use the operational CLI command show interface sdwan? to see the SD-WAN interfaces.
- Select Commit and Push to Devices.Edit Selections on the lower left side of the screen.
![]() Deselect Filter Selected.Click on Deselect All.Select your hub Device Group. Select Include Device and Network Templates at the bottom of the screen. You must push to hubs before pushing to branches.Most branches have dynamic IP addresses through their service providers, so branches must initiate the IKE/IPSec connection because the hub doesn’t have the branches’ IP address. To ensure that the hub is ready to receive the IKE/IPSec connections, the hub’s configuration must be committed and pushed before the branch’s configuration. Thus, when the branch configurations are pushed and the branches initiate the connection to the hub, the hub is ready.
Deselect Filter Selected.Click on Deselect All.Select your hub Device Group. Select Include Device and Network Templates at the bottom of the screen. You must push to hubs before pushing to branches.Most branches have dynamic IP addresses through their service providers, so branches must initiate the IKE/IPSec connection because the hub doesn’t have the branches’ IP address. To ensure that the hub is ready to receive the IKE/IPSec connections, the hub’s configuration must be committed and pushed before the branch’s configuration. Thus, when the branch configurations are pushed and the branches initiate the connection to the hub, the hub is ready.![]() Select the Templates tab and Deselect All.The Push Scope is the Device Group. Push the configuration to the hub(s).Push the configuration to the branch(es) by repeating the prior step, but selecting your branch Device Group.(PAN-OS 9.1.2 and later versions, and SD-WAN plugin 1.0.2 and later versions) Refresh the IKE pre-shared key.If you need to change the current IKE key that is used to secure the IPSec connections between VPN cluster devices, perform this step to randomly generate a new key for the cluster.Perform this step when cluster members aren't busy.
Select the Templates tab and Deselect All.The Push Scope is the Device Group. Push the configuration to the hub(s).Push the configuration to the branch(es) by repeating the prior step, but selecting your branch Device Group.(PAN-OS 9.1.2 and later versions, and SD-WAN plugin 1.0.2 and later versions) Refresh the IKE pre-shared key.If you need to change the current IKE key that is used to secure the IPSec connections between VPN cluster devices, perform this step to randomly generate a new key for the cluster.Perform this step when cluster members aren't busy.- Select PanoramaSD-WANVPN Clusters and select a cluster.At the bottom of the screen, select Refresh IKE Key.
![]() A message appears notifying you that Refreshing the IKE key will generate a new security association (SA) for every SD-WAN firewall in the VPN cluster. This may cause a service disruption. Do you wish to continue? Yes | No Select Yes if you wish to continue.Commit.After you Refresh IKE Key, you must commit to the entire cluster; a partial commit will bring down tunnels.Push to Devices.
A message appears notifying you that Refreshing the IKE key will generate a new security association (SA) for every SD-WAN firewall in the VPN cluster. This may cause a service disruption. Do you wish to continue? Yes | No Select Yes if you wish to continue.Commit.After you Refresh IKE Key, you must commit to the entire cluster; a partial commit will bring down tunnels.Push to Devices.Strata Cloud Manager
In strata cloud manager, create a VPN cluster to group branches and hubs that communicate with each other into a logical group.The SD-WAN interface profile defines the characteristics of the ISP connection, specifies the speed of links and how frequently the firewall monitors the link, and specifies the link tag. When you specify the same Link Tag on multiple links, you’re grouping (bundling) those physical links into a link bundle or fat pipe.- Log in to Strata Cloud Manager.Select ConfigurationNGFW and Prisma AccessSetupAuto VPN and Add VPN Cluster.Check (enable) SD-WAN.Add the hub firewalls to the VPN cluster.
- Add Hub Devices to select one or more firewalls to Add as hubs.Up to four hubs are supported for a VPN cluster.
- Click the firewall in the Hub Devices list.
- Set the hub firewall Priority.Range is 1 to 4. The lower the priority value, the higher the priority and local preference. A cluster supports a maximum of four hubs. An active/passive HA pair counts as one hub. Multiple hubs can have the same priority; an HA pair must have the same priority.
- Select a Logical Router.
- (Optional) Check (enable) DIA VPN and select a DIA VPN Link Tag.
- Update.
- Repeat this step for all hub firewalls that you add to the VPN cluster.
Add the branch firewalls to the VPN cluster.- Add Hub Devices to select one or more firewalls to Add as hubs.
- Select a Logical Router.
- (Optional) Select a BGP Redistribution Profile.
- Update.
- Repeat this step for all branch firewalls that you add to the VPN cluster.