Configure GTP Stateful Inspection
Table of Contents
11.1 & Later
Expand all | Collapse all
-
- Intelligent Security and the UEIP Database
- Intelligent Security with PFCP for User Equipment to IP Address Correlation
- Configure Intelligent Security using PFCP for User Equipment to IP Address Correlation
- Configure Intelligent Security Using RADIUS for User Equipment to IP Address Correlation
- Configure Intelligent Security Using GTP for User Equipment to IP Address Correlation
Configure GTP Stateful Inspection
Enable GTP security, configure a Mobile Network Protection
profile, and attach the profile to a Security policy rule to secure
GTP traffic.
GTP comprises three types of traffic—control
plane (GTP-C), user plane (GTP-U), and charging (GTP’ derived from
GTP-C) traffic. Enabling GTP security on the Palo Alto Networks® firewall
allows you to statefully inspect, validate, filter, and perform
security checks on GTPv2-C, GTPv1-C and GTP-U protocol messages.
Use
the following workflow to enable stateful inspection and protocol
validation for GTPv1-C, GTPv2-C, and GTP-U traffic. In addition,
you can configure the firewall to inspect GTP-U content, filter
GTP outer sessions based on APN, IMSI-Prefix and RAT, and enable
overbilling protection for mobile subscribers. After you enable
GTP, the options for configuring GTP security and monitoring GTP
traffic become available on the firewall. Firewalls securing GTP
traffic can be deployed in an active/passive HA; active/active HA
is not supported.
- Enable GTP Security.
- Log in to the firewall web interface.Select DeviceSetupManagementGeneral Settings. Select GTP Security.Click OK.Commit the change.Select DeviceSetupOperations and Reboot Device.Enabling or disabling GTP Security requires a commit and a reboot; the best practice is to commit and reboot at this point. After you enable GTP Security, the options for configuring and monitoring GTP traffic become available on the firewall. If you disable GTP Security, you must also Commit your change and reboot the firewall. After you disable GTP Security, the firewall does not perform GTP stateful inspection, but still checks GTP packets against Security policy rules and still applies App-ID.(Optional) You can gracefully enable GTP stateful inspection to minimize disruption when you deploy a new firewall or migrate GTP traffic.
- Access the CLI.>set gtp nodrop yesThe firewall continues to perform GTP stateful inspection and generate logs, but won’t drop GTPv2, GTPv1-C, or GTP-U packets that fail GTP stateful inspection. When you later decide to re-enable the firewall to drop packets that fail GTP stateful inspection, use the CLI operational command: set gtp nodrop no (this is the default setting).>show gtp infoThe firewall displays whether GTP stateful inspection is gracefully enabled (gtp no drop: True) or not (gtp no drop: False).Create a Mobile Network Protection profile to inspect GTP traffic.
- Select ObjectsSecurity ProfilesMobile Network Protection and Add a new profile.Give the profile a descriptive Name.If the firewall is in Multiple Virtual System Mode, enable the profile to be Shared by all virtual systems.Set up Mobile Network Protection Profile for the GTP version(s) you want to inspect and configure the available options for filtering, overbilling protection, and logging GTP messages for your compliance and troubleshooting needs.Create a Security policy rule to allow GTP traffic on your network.
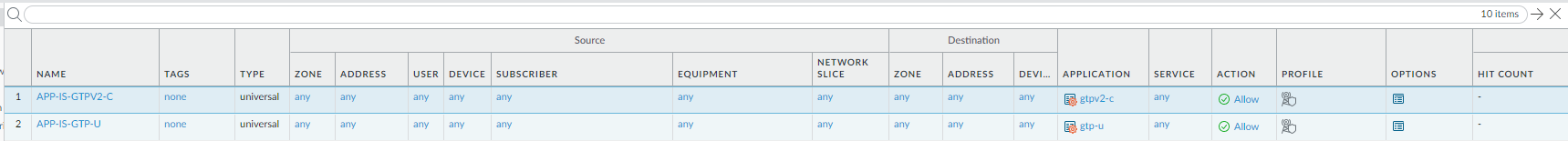
- Select PoliciesSecurity and Add a descriptive Name for the rule in the General tab.In the Source tab, Add the Source Zone.In the Destination tab, Add the Destination Zone.Restrict access to specific components in the EPC network; consider using address objects in the Destination Address field to enable access to specific IP addresses.In the Application tab, Add the applications that correspond to the network services you want to safely allow. For example, select gtp-v1, gtp-v2, and gtp-u. Make sure to select the applications you enabled for inspection in the GTP Protection profile.In the Service/URL Category tab, change the Service from application-default to any.In the Actions tab, set the Action to Allow.Attach the Mobile Network Protection profile to the Security policy rule. For Profile Type, select Profiles and select the Mobile Network Protection profile you set up earlier.Verify that Log at Session End is enabled. GTP session start and GTP session end events are logged only when you enable Log at Session Start and Log at Session End in a Security policy rule. The session start and session end logs are available under MonitorLogsGTP. All other GTP events are logged based on the settings you enabled in the Mobile Network Protection profile and are also available under MonitorLogsGTP.By default, the log storage quota for GTP is 2% of the total log storage capacity for the firewall model. Because GTP logs are high volume, increase the log quota (DeviceSetupManagement) or set up log forwarding to an external server.Click OK.
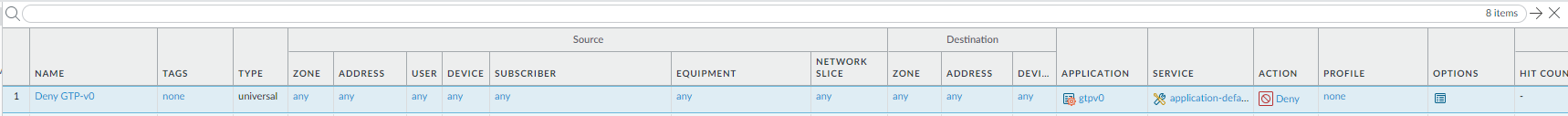
![]() (Optional) Block GTPv0 traffic coming into your network. Add a Security policy rule to deny application gtpv0. 3GPP recommends that a GTPv2 or GTPv1 entity that listens to the GTPv0 port should silently discard any GTPv0 messages it receives. The 3GPP Rel-8 GTPv1 specification removed support for GTPv1 to GTPv0 interworking; hence, a Palo Alto Networks firewall does not support stateful inspection of GTPv0 traffic.
(Optional) Block GTPv0 traffic coming into your network. Add a Security policy rule to deny application gtpv0. 3GPP recommends that a GTPv2 or GTPv1 entity that listens to the GTPv0 port should silently discard any GTPv0 messages it receives. The 3GPP Rel-8 GTPv1 specification removed support for GTPv1 to GTPv0 interworking; hence, a Palo Alto Networks firewall does not support stateful inspection of GTPv0 traffic.![]() Commit your policies to the running configuration on the firewall.Monitor GTP Traffic to verify that you set up GTP inspection effectively for your visibility and logging needs, and to view the GTP traffic in your network.
Commit your policies to the running configuration on the firewall.Monitor GTP Traffic to verify that you set up GTP inspection effectively for your visibility and logging needs, and to view the GTP traffic in your network.