Step 2: Create the Application Allow Rules
Table of Contents
Expand all | Collapse all
-
- What Is a Best Practice Internet Gateway Security Policy?
- Why Do I Need a Best Practice Internet Gateway Security Policy?
- How Do I Deploy a Best Practice Internet Gateway Security Policy?
- Create User Groups for Access to Allowed Applications
- Decrypt Traffic for Full Visibility and Threat Inspection
-
- Transition Vulnerability Protection Profiles Safely to Best Practices
- Transition Anti-Spyware Profiles Safely to Best Practices
- Transition Antivirus Profiles Safely to Best Practices
- Transition WildFire Profiles Safely to Best Practices
- Transition URL Filtering Profiles Safely to Best Practices
- Transition File Blocking Profiles Safely to Best Practices
- Create Best Practice Security Profiles for the Internet Gateway
- Monitor and Fine-Tune the Policy Rulebase
- Remove the Temporary Rules
- Maintain the Rulebase
Step 2: Create the Application Allow Rules
Identify Your Application Allow List
before you create application allow rules. Create allow rules based on applications,
not on ports. Except for certain infrastructure applications that require user
access before the firewall can identify the user, allow access only to known users.
Create User Groups
for Access to Allowed Applications and limit user access to only the
specific users or user groups who have a business need to access each
application.
To convert port-based rules to application-based rules or to migrate from a
port-based firewall, follow the advice in Best Practices for Migrating to
Application-Based Policy, which leverages Policy Optimizer. Policy Optimizer
helps you analyze port-based rules and show you the exact applications that
match those rules. It also helps you find unused rules, rules with unused
applications (over-provisioned rules), and existing port-based rules.
Place specific rules above general rules in the Security policy rulebase. Otherwise, a general
rule might shadow a specific rule. (Shadowing is when you place a broad rule that
includes the same match criteria as a more specific rule higher in the rulebase than
the specific rule, so traffic intended to match the specific rule instead matches
the general rule.)
This part of the rulebase includes the allow rules for applications you identified as
part of your application allow list, including:
- Sanctioned applications you provision and administer for business and infrastructure purposes.
- General business applications users might need to get their jobs done.
- Tolerated applications you choose to allow for personal use.
Tag all sanctioned applications with
the predefined Sanctioned tag. Panorama and firewalls consider
applications without the Sanctioned tag as unsanctioned applications.
Attach best practices Security profiles to scan all allowed traffic for known and unknown
threats. If you haven't created these profiles, then Create Best
Practice Security Profiles for the Internet Gateway. Because you can’t
inspect what you can’t see, configure the firewall to Decrypt Traffic for
Full Visibility and Threat Inspection.
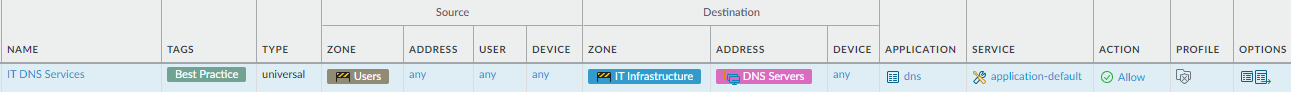
- Allow access to your corporate DNS servers.Allow traffic only to sanctioned DNS servers. Use the DNS Security service to prevent connections to malicious DNS servers.
Why Do I Need This Rule? Rule Highlights - Access to DNS provides network infrastructure services and is commonly exploited by attackers.
- Allowing access only on your internal DNS server reduces your attack surface.
- Because this rule is very specific, place it near the top of the rulebase.
- Create an address object to use for the destination address to ensure that users only access the DNS server in your data center.
- Because users need access to these services before they log in, allow access to any user.
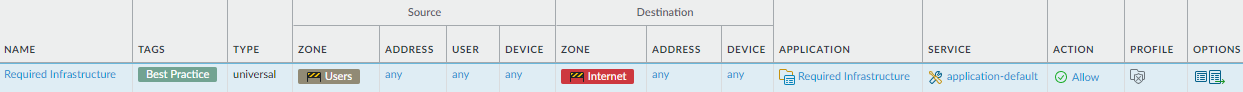
![]() Allow access to other required IT infrastructure resources.
Allow access to other required IT infrastructure resources.Why Do I Need This Rule? Rule Highlights - Enable applications that provide network infrastructure and management functions, such as NTP, OCSP, STUN, and ping.
- The preceding rule restricts allowed DNS traffic to the destination address in the data center, these applications might not reside in your data center and therefore require a separate rule.
- Because these applications run on the default port, allow access to any user (users might not yet be logged in and known because of when these services are needed), and have a destination address of any, add them to one application group and create one rule to enable access to all of them.
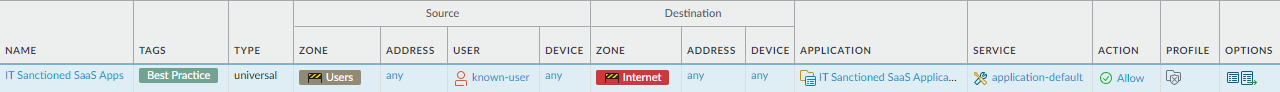
![]() Allow access to IT sanctioned SaaS applications.
Allow access to IT sanctioned SaaS applications.Why Do I Need This Rule? Rule Highlights - With SaaS applications, proprietary data resides in the cloud. This rule ensures that only known users have access to these applications (and the underlying data).
- Scan allowed SaaS traffic for threats.
- Create an application group to control all sanctioned SaaS applications.
- SaaS applications should always run on the application-default port.
- Restrict access to known users. See Create User Groups for Access to Allowed Applications.
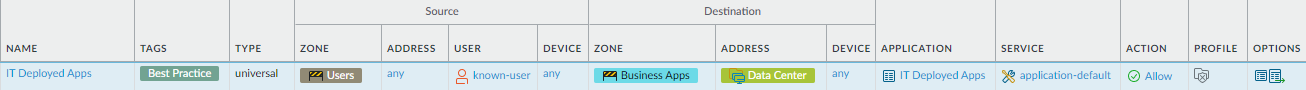
![]() Allow access to IT provisioned on-premises applications.
Allow access to IT provisioned on-premises applications.Why Do I Need This Rule? Rule Highlights - Attacks often use business-critical data center applications such as FTP during the exfiltration stage or exploit application vulnerabilities to move laterally.
- Many data center applications use multiple ports. Setting the Service to application-default safely enables applications on their standard ports. Don't allow applications on non-standard ports, which is often associated with evasive behavior.
- Create an application group to group all data center applications.
- Create an address group for your data center server addresses.
- Restrict access to known users. See Create User Groups for Access to Allowed Applications.
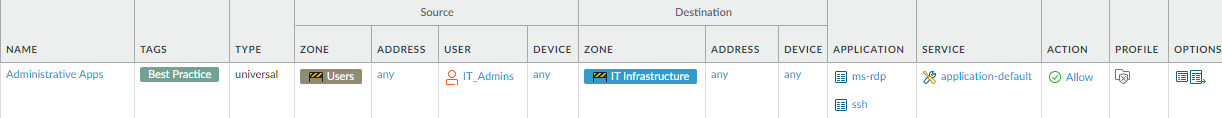
![]() Allow access to applications your administrative users need.
Allow access to applications your administrative users need.Why Do I Need This Rule? Rule Highlights - To reduce your attack surface, create user groups for access to allowed applications.
- Because administrators often need access to sensitive account data and remote access to other systems (for example RDP), to reduce your attack surface, allow access only to administrators who have a business need.
- This rule restricts access to users in the IT_admins group.
- Create a custom application for each internal application or application that runs on non-standard ports so you can enforce them on their default ports rather than opening additional ports on your network.
- If you have different user groups for different applications, create separate rules for granular control.
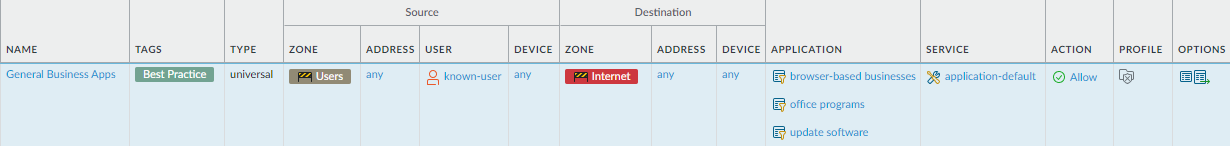
![]() Allow access to general business applications.
Allow access to general business applications.Why Do I Need This Rule? Rule Highlights - In addition to applications you sanction and administer for users, users often need access to other business applications, such as Zoom, Adobe online services, or G Suite.
- This rule enables you to safely allow web browsing while scanning for threats. See Create Best Practice Security Profiles for the Internet Gateway.
- Restrict access to only known users. See Create User Groups for Access to Allowed Applications.
- For visibility, create an application filter for each type of application you want to allow.
- Attach best practices Security profiles to prevent known and unknown threats in all traffic.
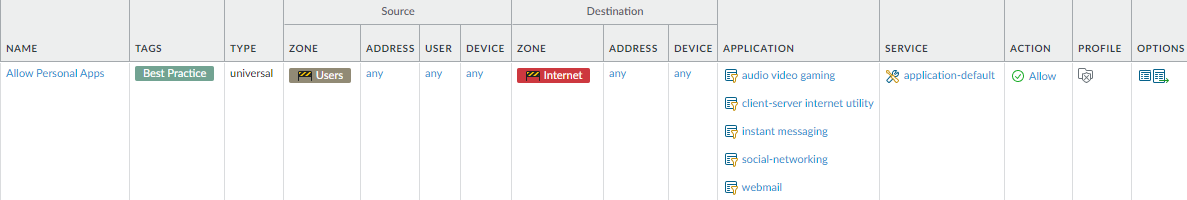
![]() (Optional) Allow access to personal applications.
(Optional) Allow access to personal applications.Why Do I Need This Rule? Rule Highlights - As the lines blur between work and personal devices, that all applications your users access are safely enabled and free of threats.
- Use application filters to safely enable access to personal applications when you create this initial rulebase. After you assess the applications in use, use the information to decide whether to remove the filter and allow a smaller subset of personal applications appropriate for your acceptable use policies.
- Restrict access to only known users. See Create User Groups for Access to Allowed Applications.
- For visibility, create an application filter for each type of application you want to allow.
- Attach best practices Security profiles to prevent known and unknown threats in all traffic.
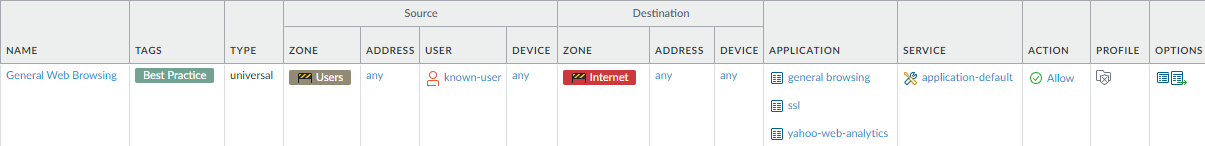
![]() Allow general web browsing.
Allow general web browsing.Why Do I Need This Rule? Rule Highlights - The previous rule allowed access to personal applications (many of them browser-based). This rule allows general web browsing.
- General web browsing is more risk-prone than other types of application traffic. Create best practices Security profiles and attach them to this rule in order to safely enable web browsing.
- Because threats often hide in encrypted traffic,decrypt traffic for full visibility and threat inspection to safely enable web browsing.
- Use the same best practice security profiles as the other rules and tighten the URL Filtering profile as much as possible.
- To help prevent devices with malware or embedded devices from reaching the internet, allow only known users.
- Use application filters to allow access to general types of applications.
- Explicitly allow SSL as an application to allow users to browse to HTTPS sites that you choose to exclude from decryption.
- Set the Service to application-default.
![]()