Download PDF
Cloud NGFW for AWS
Getting Started from an AWS Firewall Manager Account
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Getting Started from an AWS Firewall Manager Account
Learn how to deploy your Cloud NGFW for AWS resource using the AWS Firewall
Manager.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
AWS Firewall Manager (FMS) is a security management service that allows you
to centrally configure and manage firewall rules across your accounts and
applications in AWS Organizations. Cloud NGFW for AWS is a managed firewall service
that provides advanced threat protection for your AWS VPCs.
By integrating AWS FMS with Cloud NGFW, you can centrally deploy Cloud NGFW
resources across all accounts and VPCs within your organization. This approach
provides several key benefits:
- Centralized Management: Manage Cloud NGFW policies from a central FMS location.
- Consistent Enforcement: Ensure that consistent security policies are applied across all accounts and VPCs.
- Simplified Administration: Automate the deployment and management of Cloud NGFW rules to simplify administration and respond to compliance notifications from a single dashboard.
The AWS Firewall Manager provides a guided workflow that allows you to
deploy the Cloud NGFW as an FMS policy. This workflow helps you:
- Select a deployment mode (Distributed or Centralized) and region.
- Create or select a global rulestack for your policy.
- Configure NGFW endpoints.
- Define the policy scope across your organization.
The AWS FMS integration with Cloud NGFW for AWS is currently supported in
16 AWS regions. For more information, see
Introducing Cloud NGFW for AWS, AWS Firewall Manager, and Getting Started from an AWS Firewall Manager
Account documentation.

The Cloud NGFW supports VPC resources only within FMS policy scope.
Limitations and Unsupported Features
The following features are not supported for firewalls deployed using AWS
FMS:
- Firewall Features:
- Multi-VPC resource sharing
- Egress NAT
- IPv6
- User-ID
- Multi Dimensional Scaling
- Rulestack Features:
- Dynamic Address Groups
- Data Loss Prevention
- Management:
- You cannot associate Cloud NGFW created by FMS with Panorama or Strata Cloud Manager for policy management.
Tenant Version Compatibility
Cloud NGFW tenants created after July 30, 2025, are V2 tenants. The
tenants created before July 30, 2025 are V1 tenants.
The AWS firewall manager integration with Cloud NGFW depends on the Cloud
NGFW tenant version:
- There is no impact on existing FMS deployments on V1 tenants.
- AWS Firewall Manager currently supports the deployment of V1 firewalls only. If you are on a V2 tenant with existing firewalls, the FMS association will fail. If you are on a V2 tenant with no existing firewalls, associating FMS will switch your tenant to V1 and create V1 firewalls. When you disassociate FMS, all V1 firewalls will be deleted, and your tenant will be switched back to V2.
To get started with AWS Firewall Manager account, perform the following steps:
- Subscribe to the Cloud NGFW for AWS service. The AWS account you use to subscribe to the Cloud NGFW service must be the same AWS Firewall Manager administrator account.As an IAM user in the AWS Firewall Manager account, begin by subscribing to the Cloud NGFW service through the AWS Marketplace. After completing your initial setup, return to the FMS dashboard in the AWS console. This procedure creates a Cloud NGFW tenant and automatically assigns you (the FMS administrator) with the TenantAdmin and GlobalFirewallAdmin roles.Associate the Palo Alto Cloud NGFW Service with the Firewall Manager.
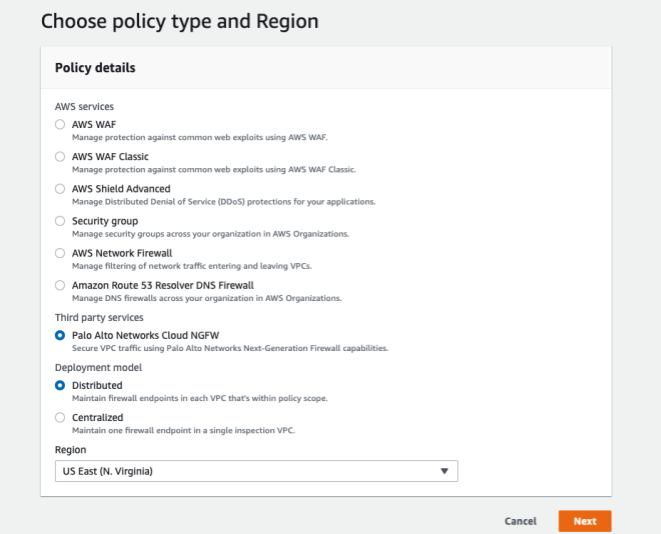
- Log in to the AWS Console and select ServicesAWS Firewall ManagerSettings.Under Third-Party Firewall Association Status, select Palo Alto Networks Cloud NGFW.Click Associate.Select Security PoliciesCreate Policy.Choose the policy type and region.
- Under Third-Party Services, select Palo Alto Networks Cloud NGFW.Select your Deployment Mode—Distributed or Centralized.Select the Region.Click Next.
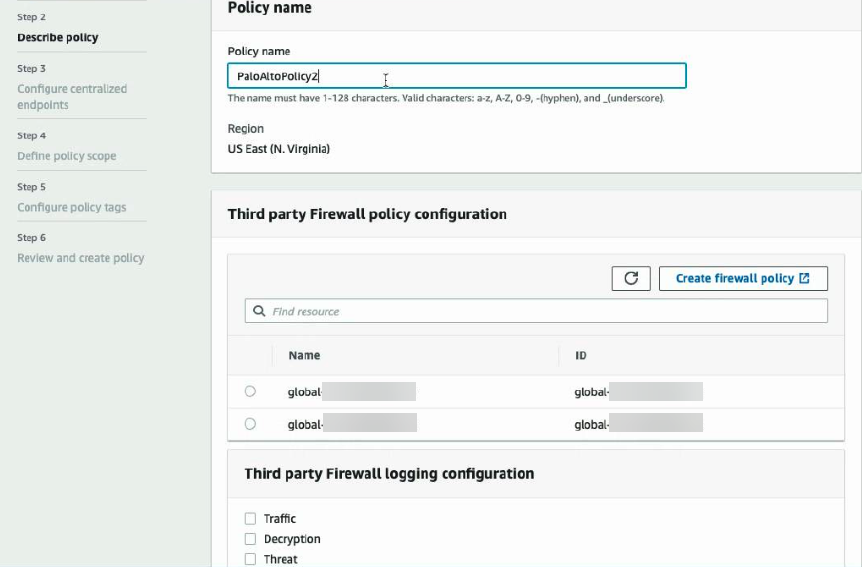
![]() Describe FMS policy for the Cloud NGFW on AWS.Provide a descriptive name for your FMS policy, configure or associate a global rulestack with the FMS policy, and configure log settings. FMS displays any existing global rulestacks (if available) and a link that takes to the Cloud NGFW console to create a global rulestack. Because the subscribing user (FMS administrator) is a GlobalRulestackAdmin, you don't have to make any changes to the user roles.
Describe FMS policy for the Cloud NGFW on AWS.Provide a descriptive name for your FMS policy, configure or associate a global rulestack with the FMS policy, and configure log settings. FMS displays any existing global rulestacks (if available) and a link that takes to the Cloud NGFW console to create a global rulestack. Because the subscribing user (FMS administrator) is a GlobalRulestackAdmin, you don't have to make any changes to the user roles.- Enter a descriptive Policy Name.Select or create Third Party Firewall Policy Configuration.In the FMS console, Third-Party Firewall Policy Configuration refers to a global rulestack in the context of the Cloud NGFW. If you have already created one or more global rulestacks, they are listed here. If you have not created a global rulestack, you can create one by clicking Create Firewall Policy. This redirects you to the Cloud NGFW console. For information about rulestacks and rulestack configuration, see rules and rulestacks.Create a Global Rulestack.
- Enter a descriptive Name for your rulestack.
- (optional) Enter a Description for your rulestack.
- Click Save.
- Return to the FMS console.
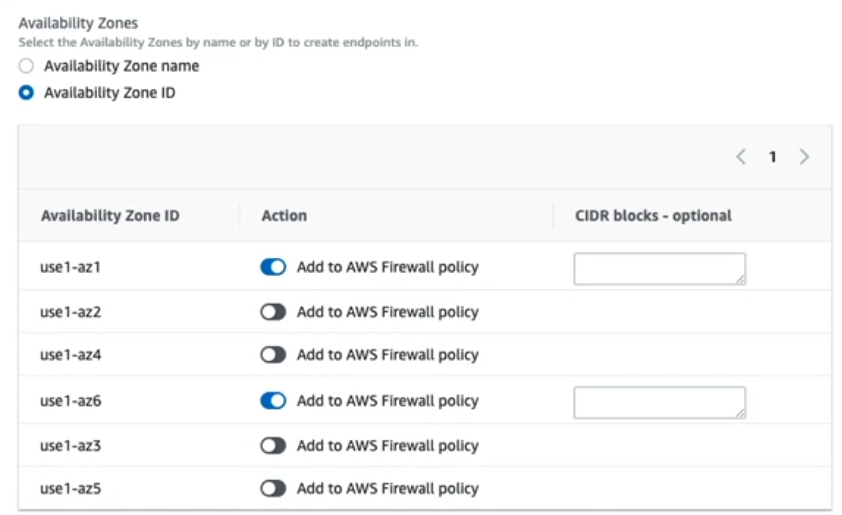
Configure logging.You can select Traffic, Decryption, or Threat logs. For each type of log, you must specify a destination—S3 Bucket, CloudWatch log group, or Kinesis Firehose delivery stream—from the drop-down. The drop-down displays previously configured destinations in your AWS environment.Click Next.![]() Configure NGFW endpoints.Cloud NGFW creates endpoints in your availability zones that need to be secured. These NGFW endpoints intercept and redirect traffic to Cloud NGFW for inspection and enforcement. The number and location of NGFW endpoints differs based on your deployment mode—distributed or centralized.You select the NGFW endpoint locations by choosing availability zone names or availability zone IDs. Keep in mind that availability zone names can differ between AWS accounts but availability zone IDs are consistent across all AWS accounts.
Configure NGFW endpoints.Cloud NGFW creates endpoints in your availability zones that need to be secured. These NGFW endpoints intercept and redirect traffic to Cloud NGFW for inspection and enforcement. The number and location of NGFW endpoints differs based on your deployment mode—distributed or centralized.You select the NGFW endpoint locations by choosing availability zone names or availability zone IDs. Keep in mind that availability zone names can differ between AWS accounts but availability zone IDs are consistent across all AWS accounts.- Select Availability Zone Name or Availability Zone ID. This selection determines what options—names or IDs—the FMS console lists.In the Action column, click the slider to add an availability zone to the Cloud NFGW FMS policy.(Optional) Add Classless Inter-Domain Routing (CIDR) blocks to specify the subnets used by the NGFW endpoints.You can specify a CIDR block for each selected availability zone or create a list of CIDR blocks for the FMS to assign to the selected availability zones. Each CIDR block must be a /28 CIDR block.If you don't specify any CIDR blocks, the FMS will take a best effort approach to find unassigned CIDR blocks in your VPC to create subnets for the NGFW endpoints. If no CIDR blocks are available in your VPC, the FMS displays a noncompliant error.Click Next.
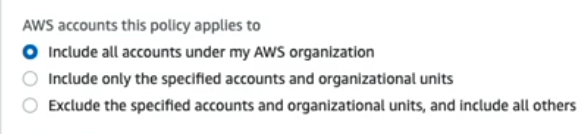
![]() Define Cloud NGFW FMS Policy Scope.Policy scope defines the AWS accounts or organizational units (OU) and resources that are covered by the Cloud NGFW FMS policy. You can apply the Cloud NGFW FMS policy rules across all AWS accounts and VPCs in your organization or specify a subset of accounts and/or VPCs.When you add a new AWS account or VPC to your organization, the FMS determines if your Cloud NGFW policy should be applied to that account or VPC. For example, you can apply the Cloud NGFW policy to all accounts except for a small, excluded subset. When a new account joins your organization, because it's not on the excluded list, the Cloud NGFW policy is applied.
Define Cloud NGFW FMS Policy Scope.Policy scope defines the AWS accounts or organizational units (OU) and resources that are covered by the Cloud NGFW FMS policy. You can apply the Cloud NGFW FMS policy rules across all AWS accounts and VPCs in your organization or specify a subset of accounts and/or VPCs.When you add a new AWS account or VPC to your organization, the FMS determines if your Cloud NGFW policy should be applied to that account or VPC. For example, you can apply the Cloud NGFW policy to all accounts except for a small, excluded subset. When a new account joins your organization, because it's not on the excluded list, the Cloud NGFW policy is applied.- Specify the accounts to include or exclude from the Cloud NGFW FMS policy.You can choose to Include all accounts under my AWS organization, Include on the specified accounts and organizational units, or Exclude specific accounts and organizational units, and include all others.If you choose to include or exclude a subset of accounts and OUs, the FMS console displays a field that allow you to specify those accounts and OUs. Click Edit List to create your include or exclude list.
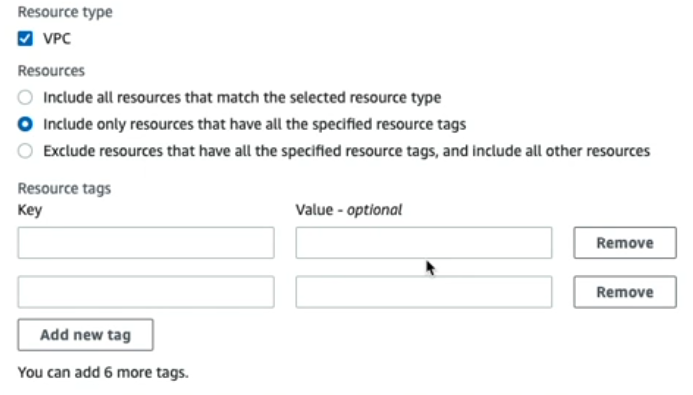
![]() Specify the VPC to include or exclude from the Cloud NGFW FMS policy.Similarly to the accounts and OUs, the can Include all resources that match the selected type, Include only resources that have all the specified resource tags, or Exclude resources that have all the specified resource tags, and include all others.If you choose to include or exclude a subset of VPCs, the FMS console displays options to provide a list of up to eight resource tags and values.
Specify the VPC to include or exclude from the Cloud NGFW FMS policy.Similarly to the accounts and OUs, the can Include all resources that match the selected type, Include only resources that have all the specified resource tags, or Exclude resources that have all the specified resource tags, and include all others.If you choose to include or exclude a subset of VPCs, the FMS console displays options to provide a list of up to eight resource tags and values.![]() Under Third Party Firewall Customer IAM Role, you can download a copy of the Cloud NGFW IAM Roles CloudFormation Template (CFT).Click Next.(Optional) Configure policy tags.You can apply tags (consisting of a key and optional value) to help search for and filter your Cloud NGFW resources created through the FMS.Click Next.Review your Cloud NGFW policy configuration.Click Create Policy to deploy the Cloud NGFW.
Under Third Party Firewall Customer IAM Role, you can download a copy of the Cloud NGFW IAM Roles CloudFormation Template (CFT).Click Next.(Optional) Configure policy tags.You can apply tags (consisting of a key and optional value) to help search for and filter your Cloud NGFW resources created through the FMS.Click Next.Review your Cloud NGFW policy configuration.Click Create Policy to deploy the Cloud NGFW.