CN-Series
Enable Inspection of Tagged VLAN Traffic
Table of Contents
Expand All
|
Collapse All
CN-Series Firewall Docs
-
-
-
- Deployment Modes
- In-Cloud and On-Prem
-
-
-
Enable Inspection of Tagged VLAN Traffic
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Complete the following procedure to enable the CN-Series firewall to inspect tagged VLAN traffic.
To inspect VLAN tagged traffic, you must update the configuration of all virtual
wires on Panorama to allow all VLAN tags. Then you must annotate your application
pod YAML file to assign VLAN tags to the app pod interfaces. This annotation tells
the CN-NGFW which tags are applied to packets that are sent through the
firewall.
Double
VLAN tagging is not supported.
- Enable all VLANs on all interfaces of CN-NGFW.
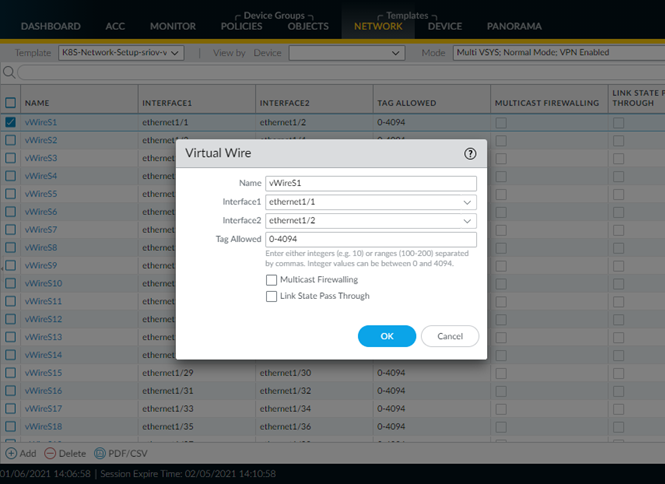
- Log in to Panorama.Select NetworkVirtual Wires.Select the K8S-Network-Setup template from the Template drop-down.Select the first virtual wire.Set Tag Allowed to 0-4094.Repeat this procedure for each virtual wire.Commit your changes.
![]() Append the application pod YAML file with the following annotations to apply a static VLAN ID per interface.Only one VLAN tag is supported per interface.paloaltonetworks.com/interfaces: '[ {"name" : "eth0"}, {"name" : "net1", "vlan" : <VLAN-ID> }{"name" : "net2", "vlan" : <VLAN-ID> }]’For example:annotations: k8s.v1.cni.cncf.io/networks: bridge-conf-1,bridge-conf-2,bridge-conf-0,pan-cni paloaltonetworks.com/firewall: pan-fw paloaltonetworks.com/interfaces: '[ {"name" : "eth0"}, {"name" : "net1", "vlan" : 101 }, {"name" : "net2", "vlan" : 102 }, {"name" : "net3", "vlan" : 103 } ]'
Append the application pod YAML file with the following annotations to apply a static VLAN ID per interface.Only one VLAN tag is supported per interface.paloaltonetworks.com/interfaces: '[ {"name" : "eth0"}, {"name" : "net1", "vlan" : <VLAN-ID> }{"name" : "net2", "vlan" : <VLAN-ID> }]’For example:annotations: k8s.v1.cni.cncf.io/networks: bridge-conf-1,bridge-conf-2,bridge-conf-0,pan-cni paloaltonetworks.com/firewall: pan-fw paloaltonetworks.com/interfaces: '[ {"name" : "eth0"}, {"name" : "net1", "vlan" : 101 }, {"name" : "net2", "vlan" : 102 }, {"name" : "net3", "vlan" : 103 } ]'