AI Access Security
Define Policy to Control GenAI App Usage
Table of Contents
Expand All
|
Collapse All
AI Access Security Docs
Define Policy to Control GenAI App Usage
Create policies to control the use of GenAI apps in your enterprise.
Create policies to control the use of GenAI apps in your enterprise.
Where Can I Use This? | What Do I Need? |
|---|---|
| One of the following:
|
You can create policies to control the use of GenAI Apps in your enterprise.
Policies created using Web Security in
Strata Cloud Manager
and
Security Policies in Panorama
respectively give you precise and granular control of all your GenAI app
usage.- InStrata Cloud Manager, even though you can create policies through Security Policies for GenAI Apps, it is recommended that you use Web Security to create policies efficiently.
- It is not recommended to have both GenAI and non GenAI apps in the same policy ifEnterprise Data Loss Prevention (E-DLP)license is not active.
For
Strata Cloud Manager
, the Default Web Access Policies like
Global Web Access
and Global Catch
All
policies are used to control outbound traffic and web
applications. To control the use of GenAI applications in your enterprise with an
out of the box policy, use the Default GenAI App Access
policies (under Default Web Access Policies). Use Custom Web Access Policies to create
custom policies to control the use of GenAI apps. For
Panorama
, use
the existing procedure to create security policies to create polices
to control the use of GenAI apps in your enterprise.Create Custom Policy Rules to Control GenAI App Usage (Strata Cloud Manager)
Strata Cloud Manager
)Create custom policy rules in
Strata Cloud Manager
to control GenAI App usage in
your organization.Your Web Security policy rules are
evaluated and enforced ahead of your Security policy rules. In the event a
Web Security and Security policy rule both apply to the same traffic, the Web
Security policy rule Action and
Enterprise DLP
inspection configuration
take precedence over the Security policy rule. After a successful match to a Web
Security policy rule, no further policy rule evaluation is performed.For example, you create Web Security policy rule and Security policy rule that
apply to
User Group A
and multiple GenAI apps. - Web Security Policy Rule AallowsUser Group Aaccess to the specified GenAI apps and has anEnterprise DLPData Profile Aassociated with the GenAI apps to prevent exfiltration of sensitive data.
- Security Policy Rule BblocksUser Group A's access to the same specified GenAI apps.
In this case, when any user in
User Group A
accesses
a GenAI app specified in the Web Security and Security policy rules they are
allowed and Enterprise DLP
inspection and verdict rendering is performed
because Web Security Policy Rule A
is higher in the
policy rulebase evaluation order. - Use theAI Access SecurityInsights dashboard to discover risks posed by GenAI apps.TheAI Access SecurityInsights dashboard provides detailed and comprehensive visibility into GenAI app usage across your organization. You can discover risky GenAI app use cases, individual risky GenAI apps, as well as risky users accessing GenAI apps.
- Perform the initialAI Access Securityconfiguration.This includes creating anEnterprise Data Loss Prevention (E-DLP)data profile to define the sensitive data match criteria and the Vulnerability Protection profile used to stop attempts to exploit system flaws or gain unauthorized access to systems.ForNGFW, this also includes creating an internal trust zone and an outbound untrusted zone.
- Log in toStrata Cloud Manager.
- Selectand select your targetManageConfigurationNGFW & Prisma AccessSecurity ServicesWeb SecurityConfigure Scope.
- SelectandSecurity SettingsThreat ManagementCustomizeVulnerability Protectionfor your Web Security policy rules.The Vulnerability Protection settings you configure here are applied to Web Security policy rules.
- Select theVulnerability Protection Profileyou created during the initial configuration.
- Configure the remaining Vulnerability Protection settings as needed.
- Save.
- SelectPoliciesto continue creating policy rules to control GenAI app usage.
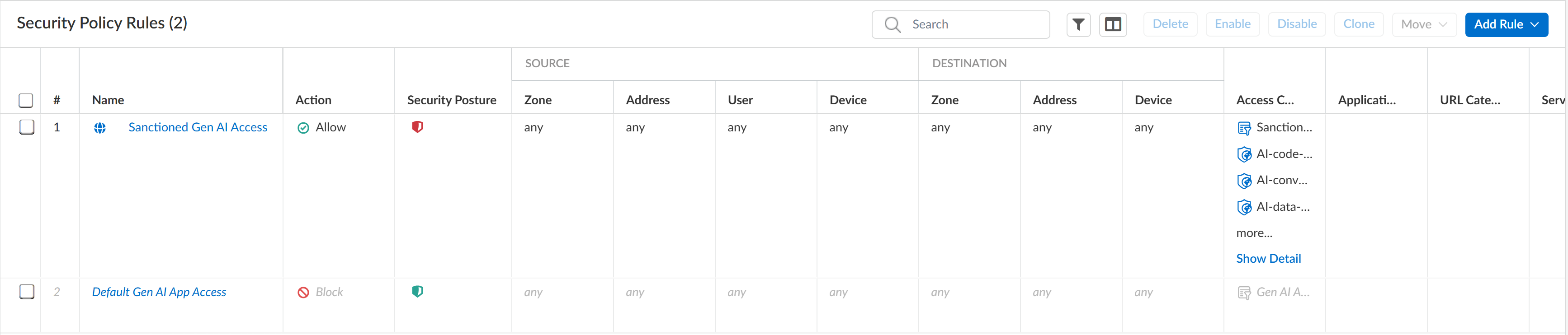
- Modify the predefinedSanctioned GenAI Accesspolicy rule.
- Select the predefinedSanctioned GenAI Accesspolicy rule andEnable.
- Click the predefinedSanctioned GenAI Accesspolicy rule to modify it.
- Make the required changes for the predefinedSanctioned GenAI Accesspolicy rule.
- Save.
![]()
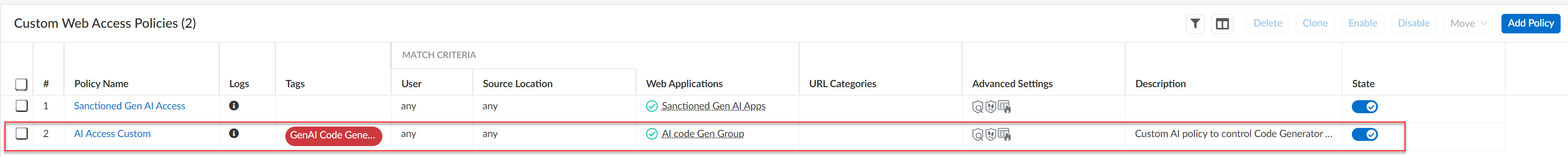
- Create a custom Web Access policy rule.
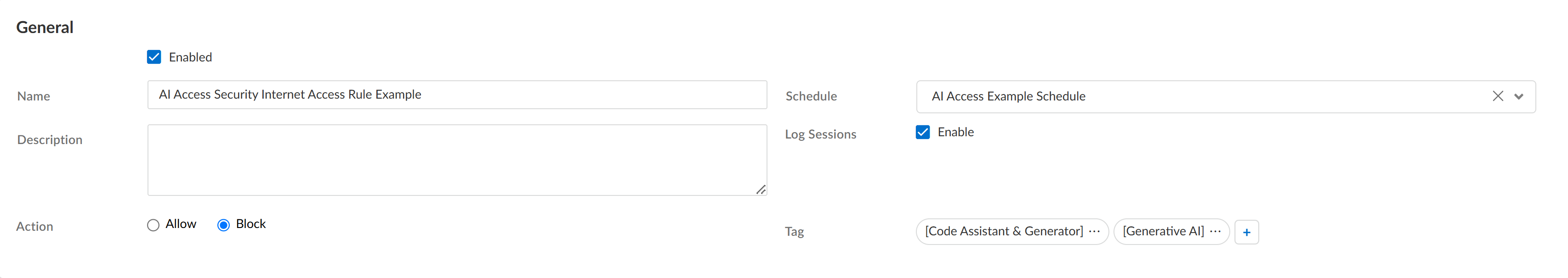
- Add Policy.
- Enter a descriptiveName.
- Enablethe Web Access policy rule.
- (Optional) Add aDescriptionfor the Web Access policy rule, and add a predefinedTagor create a new one.
- (Optional) Configure aScheduleto specify the times the Web Access policy rule is active.
![]()
- Define traffic to enforce based on the trafficSource(where it originates).For example, based on your risk discovery investigation you determine unauthorized users associated withUser Group Aaccess a GenAI app sanctioned for use byUser Group B. In this case you can create a Web Access policy rule to block access to the GenAI and addUser Group Aas the user groupSource.
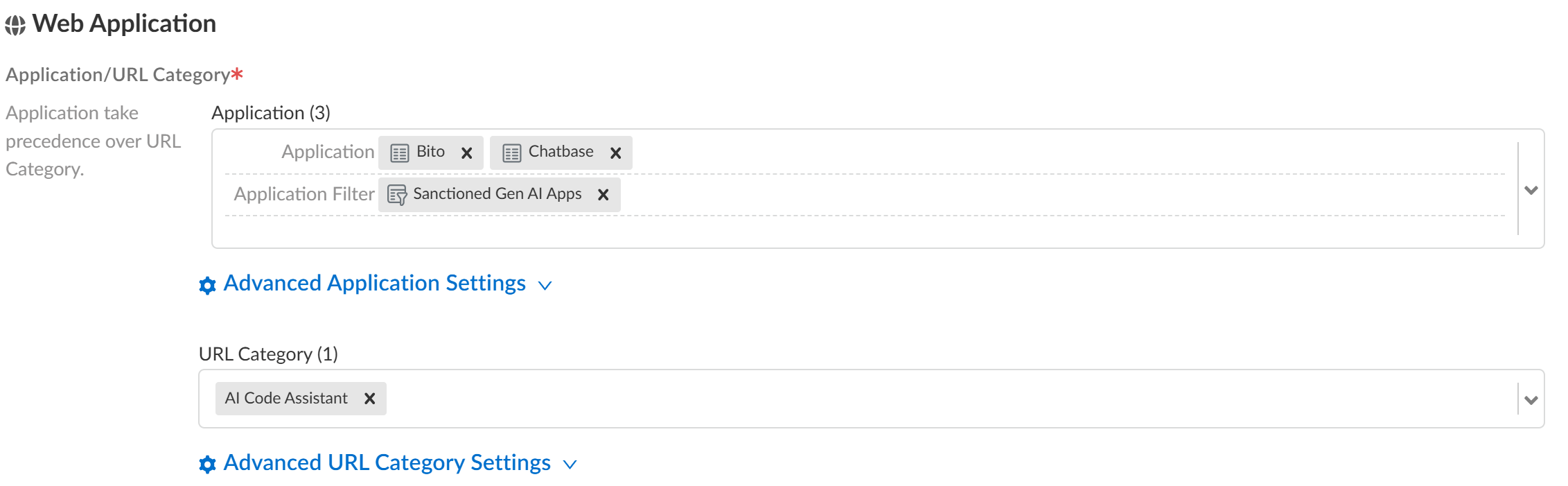
- ConfigureBlocked Web ApplicationsandAllowed Web Applicationsto define which GenAI apps you want to block or allow access to.(Allowed Web Applications) Only add supported GenAI apps to the list of allowed apps.
- Application—Add one or more GenAI apps.
- Application Category—An application category, otherwise referred to as an application filter, dynamically groups applications based on application filters you define.For example, you can use a predefined or custom GenAI app filter to dynamically control access to GenAI apps in your organization rather than adding individual GenAI apps or creating an application group that must be updated manually each time a change is required.
- Application Group—An application group is a static grouping of individual apps that you create.
(Allowed Web Applications) When adding your allowed application, click theDLPcolumn and add a DLP Rule.Enterprise Data Loss Prevention (E-DLP)is required to prevent exfiltration of sensitive data and to generateSensitive Assetsdata when discovering risks posed by GenAI apps.![]()
- Configure the rest of the Custom Web Access policy rule as needed.
- Save.
![]()
- Push ConfigandPush.
Create Custom Policy Rules to Control GenAI App Usage (Panorama)
Panorama
)Create policy rules in
Panorama™ management server
to control GenAI App usage in your
enterprise.- Use theAI Access SecurityInsights dashboard to discover risks posed by GenAI apps.TheAI Access SecurityInsights dashboard provides detailed and comprehensive visibility into GenAI app usage across your organization. You can discover risky GenAI app use cases, individual risky GenAI apps, as well as risky users accessing GenAI apps.
- Perform the initialAI Access Securityconfiguration.This includes creating anEnterprise Data Loss Prevention (E-DLP)data profile to define the sensitive data match criteria and the Vulnerability Protection profile used to stop attempts to exploit system flaws or gain unauthorized access to systems.ForNGFW, this also includes creating an internal trust zone and an outbound untrusted zone.
- Log in to thePanorama™ management serverweb interface.
- Selectand specify the Device Group.PoliciesSecurity
- Adda new Security policy rule.
- Configure the Security policy ruleGeneral,Source, andDestinationsettings.Refer to the Security Policy Administration Guide for detailed information about writing a Security policy rule.
- General—Give the Security rule a descriptiveName. You also have the option to provide aDescriptionfor the Security policy rule and to apply tags to help identify the purpose of the Security policy rule.
- Source—Define from where traffic must originate for the Security policy rule to apply.For theSource Zone, you can select an internal trust zone. If you want the Security policy rule to apply to all traffic regardless of where it originated, selectAnyfor all source settings.For example, based on your risk discovery assessment you determine that access to a GenAI app is over provisioned and must be narrowed to specific users. In this case you can write anAllowpolicy rule and add the requiredSource User.
- Destination—Define the target destination for traffic for the Security policy rule to apply.For theDestination Zone, you can select an outbound untrust zone. If you want the Security policy rule to apply to all traffic regardless of what the traffic destination is, selectAnyfor all destination settings.
- In theApplicationsettings, specify the GenAI Application Group, Application Filter, or Applications.(Allowed Web Applications) Only add supported GenAI apps to the list of allowed apps.
- Application—Add one or more GenAI apps.
- Application Category—An application category, otherwise referred to as an application filter, dynamically groups applications based on application filters you define.For example, you can use a predefined or custom GenAI app filter to dynamically control access to GenAI apps in your organization rather than adding individual GenAI apps or creating an application group that must be updated manually each time a change is required.
- Application Group—An application group is a static grouping of individual apps that you create.
![]()
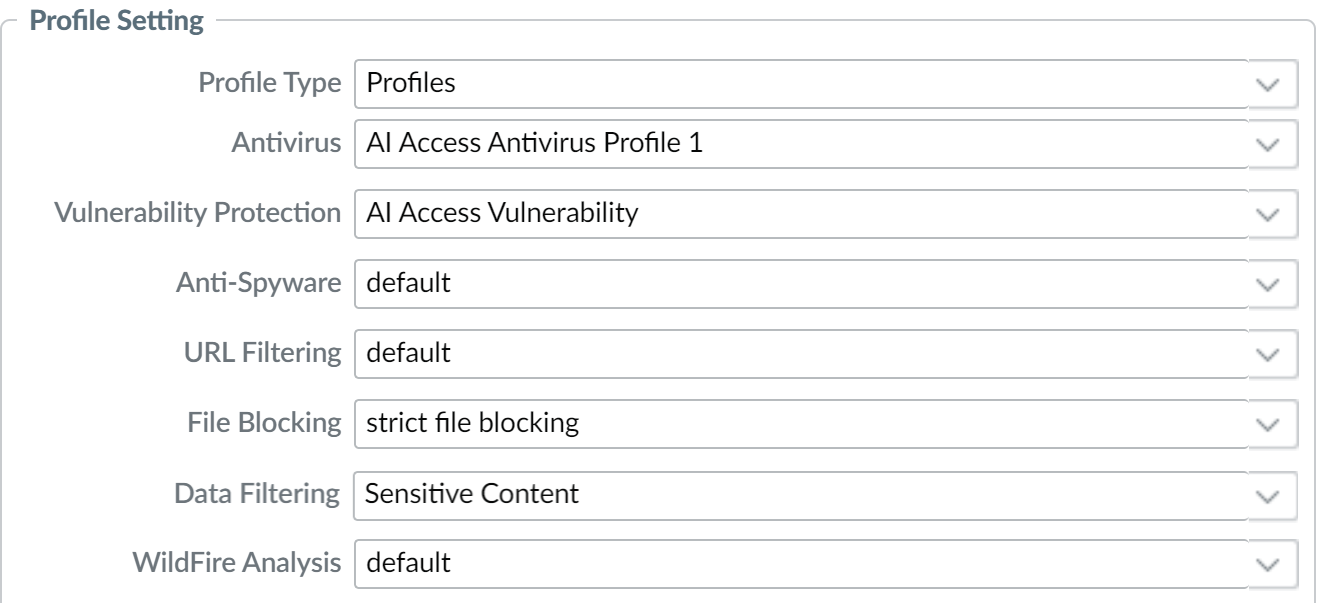
- Configure the Security policy ruleActions. Decide what Actions you want to take on your policy rule. As a best practice, attach Security Profiles to enable the firewall to scan all allowed traffic for threats. SelectProfilesfrom theProfile Typedrop-down and then select the individual Security Profiles to attach to the rule. Choose the required actions for the following settings for your GenAI apps:
- For theAction, configure the Action theNGFWtakes when traffic from Security policy ruleSourceto theDestinationis detected.For example, selectAllowif you want to allow access to one or more GenAI apps orDenyif you want to block all access to one or more GenAI apps.
- For theProfile Type, selectProfile.At a minimum you must add theVulnerability ProtectionandData Filteringprofiles. These are required to generateThreatsandSensitive Assetsdata when discovering risks posed by GenAI apps. The remaining profiles are optional and can be configured as needed. For each of the Security Profile types below you can select an existing profile or create a new one.
![]() In theActionstab,Profile Settingtakes precedence overAction Setting. So, as a best practice, ensure that both settings are matched properly. For example, even if you have the Action Setting asAllowand one of the Profile Settings asBlockfor ChatGPT, it will be blocked.
In theActionstab,Profile Settingtakes precedence overAction Setting. So, as a best practice, ensure that both settings are matched properly. For example, even if you have the Action Setting asAllowand one of the Profile Settings asBlockfor ChatGPT, it will be blocked.
- Commit and push the new configuration to your managed firewalls to complete theEnterprise DLPplugin installation.This step is required forEnterprise DLPdata filtering profile names to appear in Data Filtering logs.TheCommit and Pushcommand isn't recommended forEnterprise DLPconfiguration changes. Using theCommit and Pushcommand requires the additional and unnecessary overheard of manually selecting the impacted templates and managed firewalls in the Push Scope Selection.
- Full configuration push from Panorama
- SelectandCommitCommit toPanoramaCommit.
- SelectandCommitPush to DevicesEdit Selections.
- SelectDevice GroupsandInclude Device and Network Templates.
- ClickOK.
- Pushyour configuration changes to your managed firewalls that are usingEnterprise DLP.
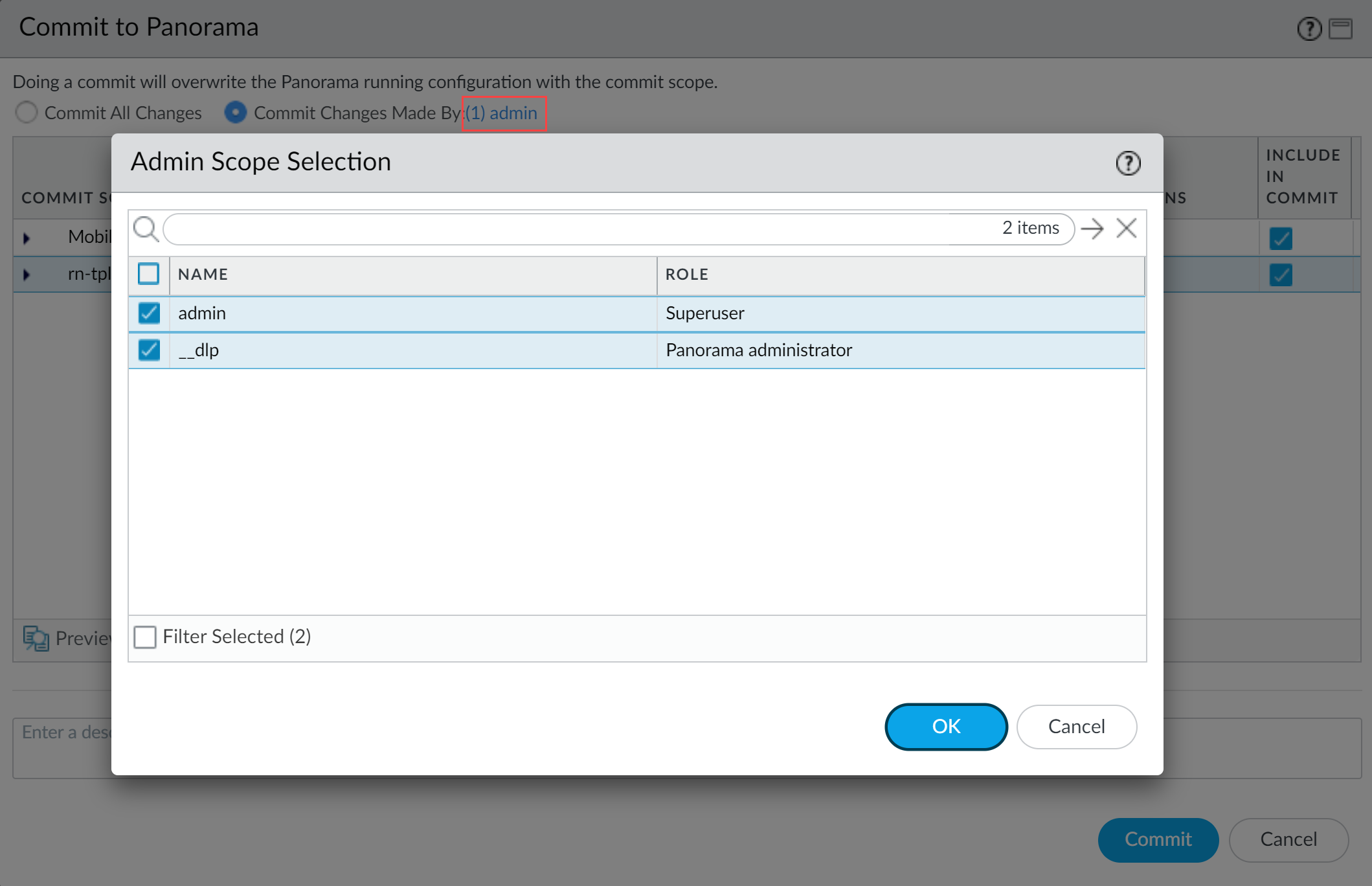
- Partial configuration push from PanoramaAlways include the temporary__dlpadministrator when performing a partial configuration push. This is required to keepPanoramaand the DLP cloud service in sync.For example, you have anadminPanoramaadmin user who is allowed to commit and push configuration changes. Theadminuser made changes to theEnterprise DLPconfiguration and only wants to commit and push these changes to managed firewalls. In this case, theadminuser is required to also select the__dlpuser in the partial commit and push operations.
- Select.CommitCommit toPanorama
- SelectCommit Changes Made Byand then click the current Panorama admin user to select additional admins to include in the partial commit.In this example, theadminuser is currently logged in and performing the commit operation. Theadminuser must clickadminand then select the__dlpuser. If there are additional configuration changes made by otherPanoramaadmins they can be selected here as well.ClickOKto continue.
![]()
- Commit.
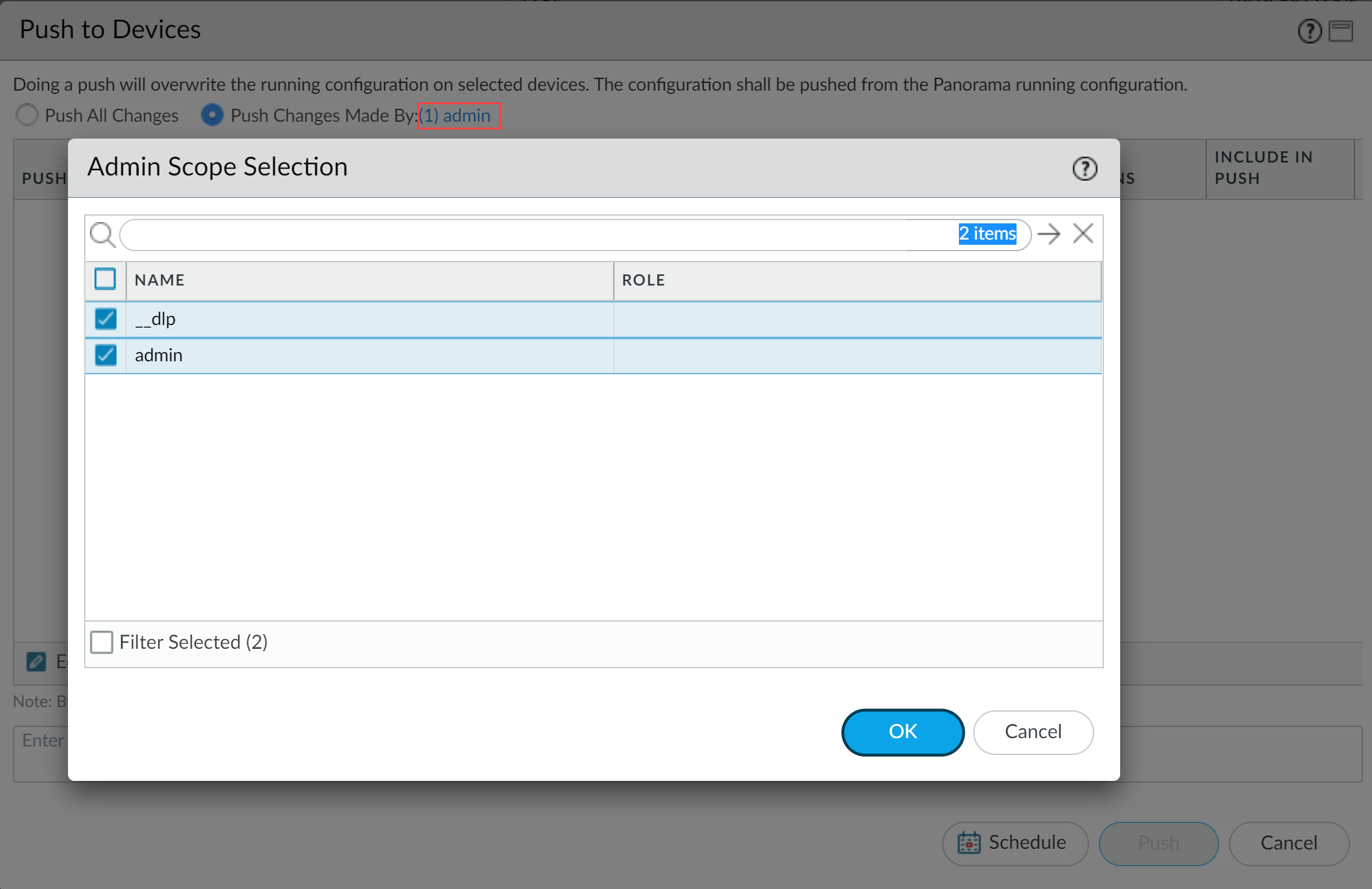
- Select.CommitPush to Devices
- SelectPush Changes Made Byand then click the currentPanoramaadmin user to select additional admins to include in the partial push.In this example, theadminuser is currently logged in and performing the push operation. Theadminuser must clickadminand then select the__dlpuser. If there are additional configuration changes made by otherPanoramaadmins they can be selected here as well.ClickOKto continue.
![]()
- SelectDevice GroupsandInclude Device and Network Templates.
- ClickOK.
- Pushyour configuration changes to your managed firewalls that are usingEnterprise DLP.