Network Security
Policy Object: Application Filter
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Policy Object: Application Filter
Use application filters to dynamically group applications based on application
attributes that you define.
Create an Application Filter to dynamically group applications based on
application attributes that you define. This is useful when you want to safely
enable access to applications that you do not explicitly sanction, but want users to
be able to access. Here, you'll find:
- A filter for commonly-used office programsAllow employees access to a variety of office programs to do business and get their work done (like Evernote or Google Docs). Use the category business-systems and the subcategory office-programs.New and updated office programs will continue to match this filter.
- A filter to smoothly enable new App-IDs.New App-IDs can cause a change in policy enforcement for traffic that is newly or differently classified. To mitigate impact to your security policy enforcement, create an application filter using the New App-ID characteristic.Choose to filter all new App-IDs, or target the filter to match to certain types of new App-IDs that might have network-wide or critical impact (for example, authentication or software development applications).New App-IDs are released monthly, so a security rule that allows the latest App-IDs gives you a month’s time to assess new applications and make any necessary adjustments to your Security policy.
Create an Application Filter
Create an Application Filter (Strata Cloud Manager)
Safely enable access to applications that you do not explicitly sanction, but that
you want users to be able to access.
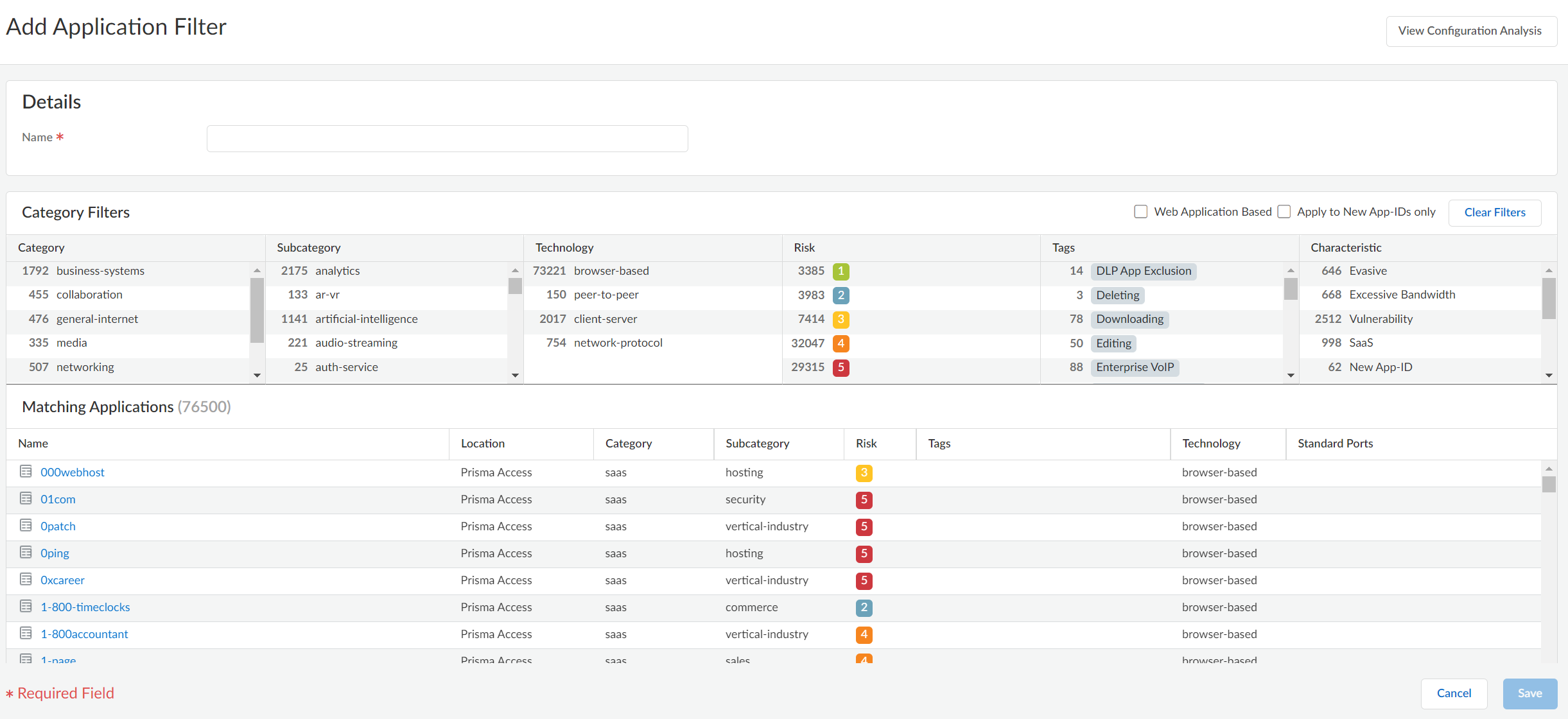
An application filter is an object that dynamically groups applications based on
application attributes that you define, including category, subcategory, technology,
risk factor, and characteristic. This is useful when you want to safely enable
access to applications that you do not explicitly sanction, but that you want users
to be able to access. For example, you may want to enable employees to choose their
own office programs (such as Evernote, Google Docs, or Microsoft Office 365) for
business use. To safely enable these types of applications, you could create an
application filter that matches on the Category
business-systems and the Subcategory
office-programs. As new applications office programs
emerge and new App-IDs get created, these new applications will automatically match
the filter you defined; you will not have to make any additional changes to your
policy rulebase to safely enable any application that matches the attributes you
defined for the filter.
- Select ConfigurationObjectsApplication Filters.Add Application Filter and give it a descriptive Name.Define the filter by selecting attribute values from the Category, Subcategory, Technology, Risk, Characteristic, and Tags sections. As you select values, notice that the list of matching applications at the bottom of the dialog narrows. When you have adjusted the filter attributes to match the types of applications you want to safely enable, select Save.
![]() Commit the configuration.
Commit the configuration.Create an Application Filter (PAN-OS & Panorama)
Use application filters to dynamically group applications based on application attributes that you define.An application filter is an object that dynamically groups applications based on application attributes that you define, including category, subcategory, technology, risk factor, and characteristic. This is useful when you want to safely enable access to applications that you do not explicitly sanction, but that you want users to be able to access. For example, you may want to enable employees to choose their own office programs (such as Evernote, Google Docs, or Microsoft Office 365) for business use. To safely enable these types of applications, you could create an application filter that matches on the Category business-systems and the Subcategory office-programs. As new applications office programs emerge and new App-IDs get created, these new applications will automatically match the filter you defined; you will not have to make any additional changes to your policy rulebase to safely enable any application that matches the attributes you defined for the filter.- Select ObjectsApplication Filters.Add a filter and give it a descriptive Name.(Optional) Select Shared to create the object in a shared location for access as a shared object in Panorama or for use across all virtual systems in a multiple virtual system firewall.Define the filter by selecting attribute values from the Category, Subcategory, Technology, Risk, Characteristic, and Tags sections. (Tags can streamline Security rule creation and maintenance). As you select values, notice that the list of matching applications at the bottom of the dialog narrows. When you have adjusted the filter attributes to match the types of applications you want to safely enable, click OK.
![]() Commit the configuration.
Commit the configuration.