Prisma AIRS
Harvest IP-Tags from Kubernetes Clusters Secured by Panorama Managed Prisma AIRS AI Runtime Firewall
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Harvest IP-Tags from Kubernetes Clusters Secured by Panorama Managed Prisma AIRS AI Runtime Firewall
Harvest IP-tags from containers secured by Panorama-managed Prisma AIRS AI Runtime Firewall.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
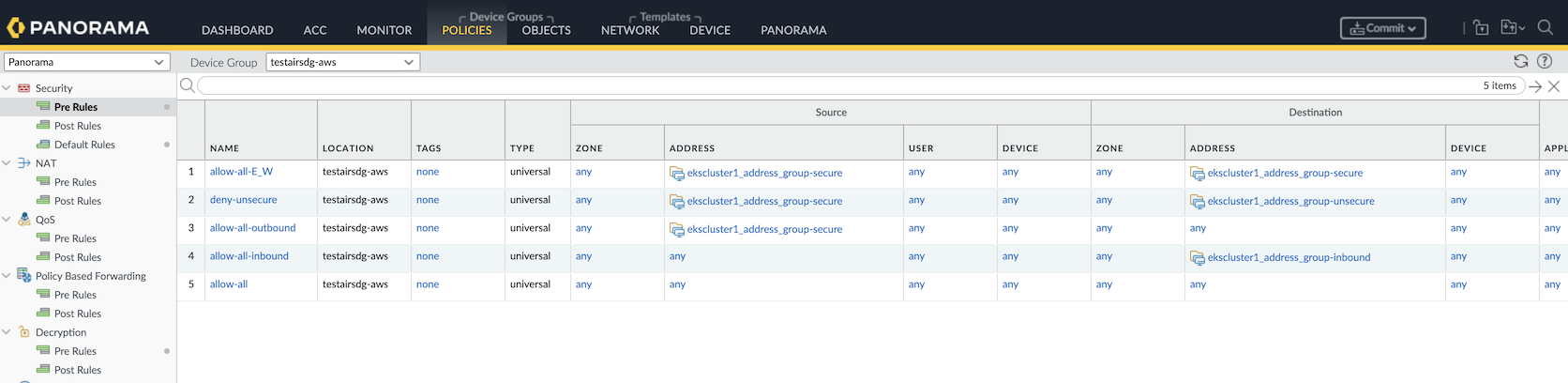
- Follow the Panorama configuration steps to secure VM workloads and Kubernetes clusters.While installing the `helm` chart, ensure you annotate the namespace to secure all the pods within your annotated namespace.Review the annotations in a namespace by running the following command:kubecetl describe namespace <secure-namespace-name> // output Annotations: paloaltonetworks.com/firewall=pan-fwSee Configure Panorama to Secure a Kubernetes Deployment for details on the following steps.Onboard a cluster in Panorama for IP-tags harvesting.Onboard Panorama Plugin for Kubernetes version 3.0.4(Panorama Plugins Kubernetes Setup Cluster and Add Cluster) for harvesting the application’s IP-tags from within the cluster.Refer here for details on setting up a cluster and its credentials.Add a Notify Group to which you want to send the IP-address-to-tag mapping information.Add a Monitoring Definition (Panorama Kubernetes Monitoring Definition) for each onboarded cluster.Set up the Dynamic Address Group . This is needed to configure the Kubernetes plugin to push the tags to the specified device groups.Create security policy rules by attaching the Dynamic Address Group you created above to the destination address. The following screenshot shows security policy rules securing different traffic paths.
![]() Select Commit → Commit and Push, to push the policy configurations from Panorama to the Panorama-managed firewall deployed in your workload.
Select Commit → Commit and Push, to push the policy configurations from Panorama to the Panorama-managed firewall deployed in your workload.Secure East-West Traffic Between Secured Pods: Demo Setup
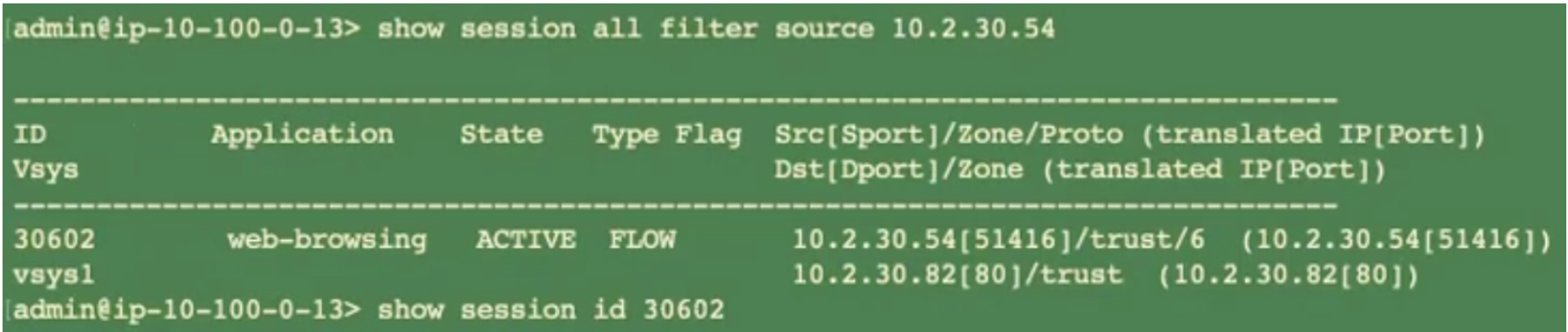
This demo illustrates Prisma AIRS AI Runtime Firewall deployed in a single-arm architecture on AWS to secure container traffic. Follow similar steps to secure the container traffic on any other cloud such as GCP and Azure. - View the list of pods in your secured namespace, that you annotated while installing a Kubernetes application using `helm`.kubectl get pods -A -o wideThe demo environment has two pods in the secured namespace and one pod in an unsecured namespace.Generate east-west traffic: Enter one of the secured pods within the secured namespace and send an HTTP request to another secure pod:// Enter the first secure pod kubectl exec -it <secure-pod-name> -n <secure-namespace> --bash // Send an HTTP request to the second pod wget http://<another-secure-pod-IP-address>Monitor east-west traffic on your Prisma AIRS AI Runtime Firewall.The output confirms a “web-browsing” session between the two pods.// Show pods-to-pods communication show session all filter source <IP-address> # This is the IP address of the first source pod // See the detailed session with the seesion Id from the previous command show session id 30602 // The output indicates the east-west security policy rule being applied on this secure-to-secure traffic between the two pods: rule: allow-all-E_W
![]()
![]()