Prisma AIRS
Deploy Prisma AIRS AI Runtime Firewall for Panorama Managed Firewall
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Deploy Prisma AIRS AI Runtime Firewall for Panorama Managed Firewall
This page helps you to configure your Prisma AIRS AI Runtime
Firewall deployment for Panorama support.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
To manually deploy and bootstrap, refer to the section on Manually Deploy and Bootstrap Prisma AIRS AI Runtime Firewall.
- Log in to Strata Cloud Manager.Navigate to AI SecurityAI Runtime Firewall.Click Add Protections ("+" icon).Refer to Deploy Prisma AIRS AI Runtime Firewall for the configurations as per your cloud deployment.In Protection Settings:Select Manage by Panorama option (You can configure the deployment configuration for both Panorama standalone and Panorama High Availability (HA).
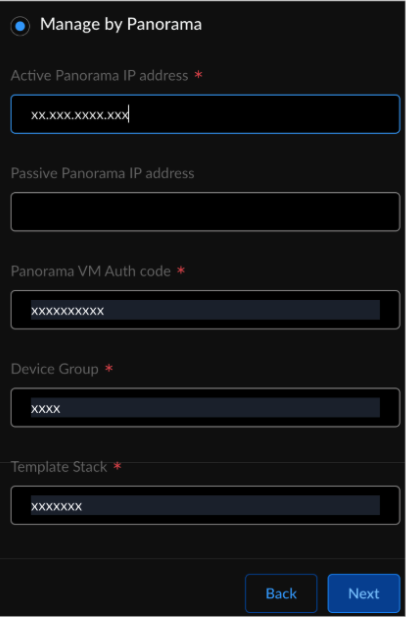
![]() Enter the following configurations:
Enter the following configurations:- Active Panorama IP address. (Copy the Panorama active/passive IP addresses by navigating to Panorama web interface → PANORAMA→ High availability.
- Optional Passive Panorama IP address.
- Panorama VM auth code (Generate the VM Auth Key on Panorama).
- Device Group name.
- Template Stack name.
Select Next.In the Review Architecture screen:- Enter a unique Terraform template name. (Use only lowercase letters, numbers, and hyphens. (Don't use a hyphen at the beginning or end, and limit the name to under 19 characters).
- Create terraform template.
- Save and Download Terraform Template.
- Close the deployment workflow to exit.
Unzip the downloaded file. Navigate to <unzipped-folder> with 2 directories: `architecture` and `modules`. Deploy the Terraform templates in your cloud environment following the `README.md` file in the `architecture` folder.Initialize and apply the Terraform for the security_project.The security_project contains the Terraform plan to create a Prisma AIRS AI Runtime Firewall architecture. This Terraform plan creates the required resources to deploy network intercept inline prevention, including the managed instance groups, load balancers, and health checks.cd architecture //Change directory to architecture/security_project cd security_project terraform init terraform plan terraform applyRun the application Terraform to peer the application VPCs.
The application_security Terraform generates the following output:cd ../application_project terraform init terraform plan terraform applyApply complete! Resources: 12 added, 0 changed, 0 destroyed.Configure Panorama to Secure VM Workloads and Kubernetes Clusters. Configure interfaces, zones, NAT policy, routers, and security policy rules.Optional Enable Prisma AIRS AI Runtime Firewall to connect with Panorama. See the section below.The Panorama deployment doesn't need IP-tags configuration. Panorama uses the existing Panorama Plugin for Kubernetes to pull the IP-tags and notify Device Groups to push the IP-tags to the managed firewalls.Enable Prisma AIRS AI Runtime Firewall Connectivity to Panorama
Follow these steps if your Panorama can’t connect to a Panorama managed Prisma AIRS AI Runtime Firewall. If you have a security group on the Panorama, add the Prisma AIRS AI Runtime Firewall in Panorama security group's IP address. This allows Panorama to communicate with the Prisma AIRS AI Runtime Firewall on the public IP address.This section shows an example of adding the IP address of an AI network intercept to Panorama in the AWS environment. Follow the similar steps for your cloud environment.Before you begin, ensure you deploy Prisma AIRS AI Runtime Firewall for Panorama support in your cloud environment.- Sign in to the AWS Management Console.Navigate to EC2 > Instances.Search for the AI network intercept you deployed using the deployment Terraform in the above section.Copy the Public IPv4 address for this network intercept.Search for the Panorama instances (active/passive) deployed in AWS. Click on the Instance ID on one of the Panoramas.Select the Security tab and click on the Security groups link.Select the Inbound rules tab and click Edit inbound rules.Click Add rule.Select All traffic and add the public IP address of Prisma AIRS AI Runtime Firewall you copied above.Save rules.