Prisma AIRS
Analyze Risk in Network Traffic
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Analyze Risk in Network Traffic
Analyze the unprotected cloud assets and the traffic flow between them.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Analyze network traffic patterns, identify security threats, and understand
protection coverage across your cloud infrastructure. This comprehensive view
displays assets protected by Prisma AIRS AI Runtime: Network
intercept and VM-Series firewalls, including virtual machines,
containers, and serverless workloads.
Use this risk analysis to prioritize your security deployments by focusing on the
highest-risk assets first.
Deploy Prisma AIRS AI Runtime: Network intercept or VM-Series to protect critical applications and vulnerable workloads
based on their threat exposure and business impact.
Workload Protection Overview: Prisma AIRS AI
Runtime: Network intercept protects AI applications, AI models, and cloud-native
applications, while VM-Series firewalls secure traditional enterprise
applications, legacy workloads, and network infrastructure.
- Log in to Strata Cloud Manager.
- Navigate to Insights Prisma AIRS Prisma AIRS AI Runtime: Network intercept.
![]()
- Select the Operational view to analyze the bidirectional communication flows between users to applications, applications to the AI model, applications to the internet, and applications to applications.
- Select the Security view to assess the threat landscape and deploy AI network intercepts as needed.
Risk Assessment and Prioritization
The following views help you to:
- Identify high-risk assets that need immediate firewall deployment
- Understand traffic patterns to configure appropriate protection policies
- Prioritize your security efforts based on actual risk exposure
Models View
Configure AI model
protection and AI data protection policies in your AI security profile,
including prompt injection detection and toxic content filtering, then push
the security policy rules to Prisma AIRS AI Runtime:
Network intercept to secure model inference traffic and prevent unauthorized
access.
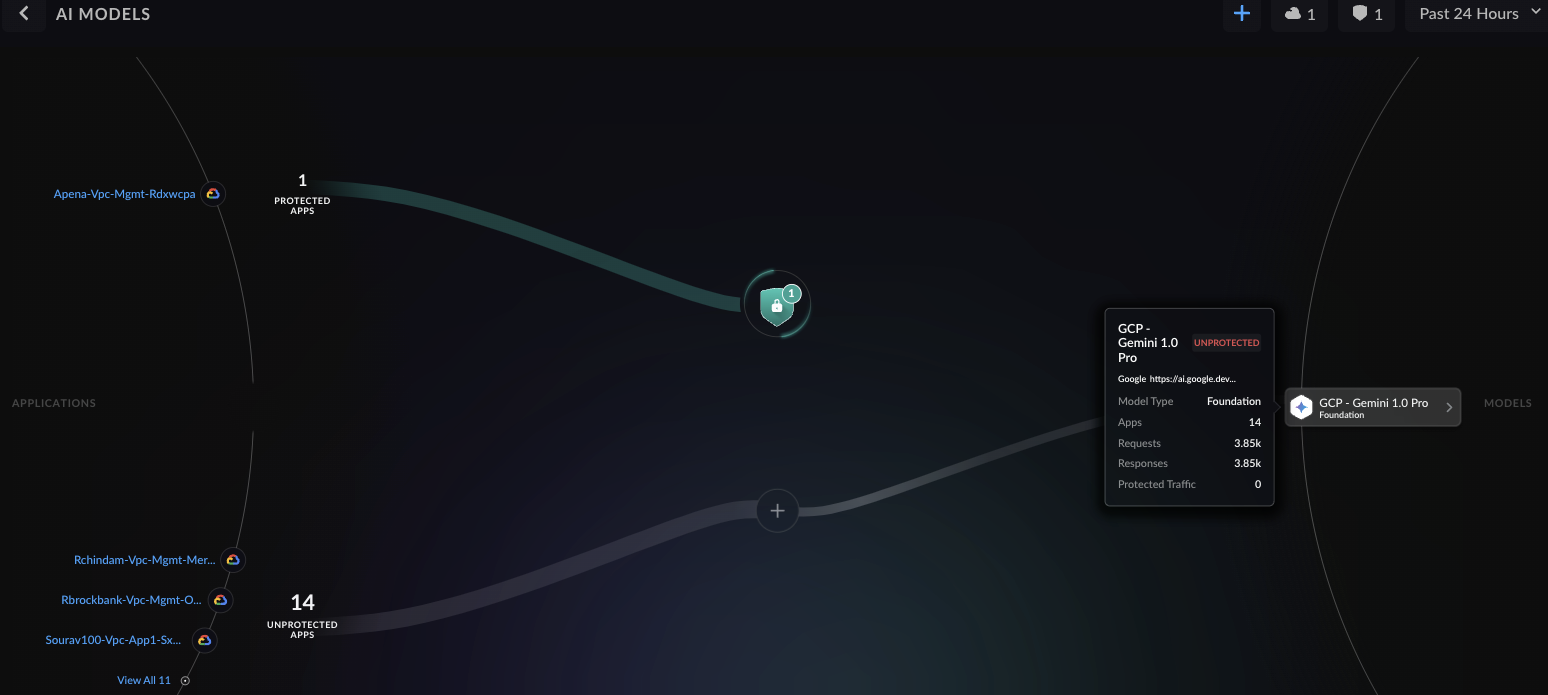
- In the Operational view, click the MODELS protections icon. The model discovery helps you to:
- See which applications communicate with which AI models.
- Identify AI models receiving traffic from protected and unprotected apps.
- View protection status, model name, and traffic
statistics (requests, responses, protected traffic) when
hovering over an AI model.
![]()
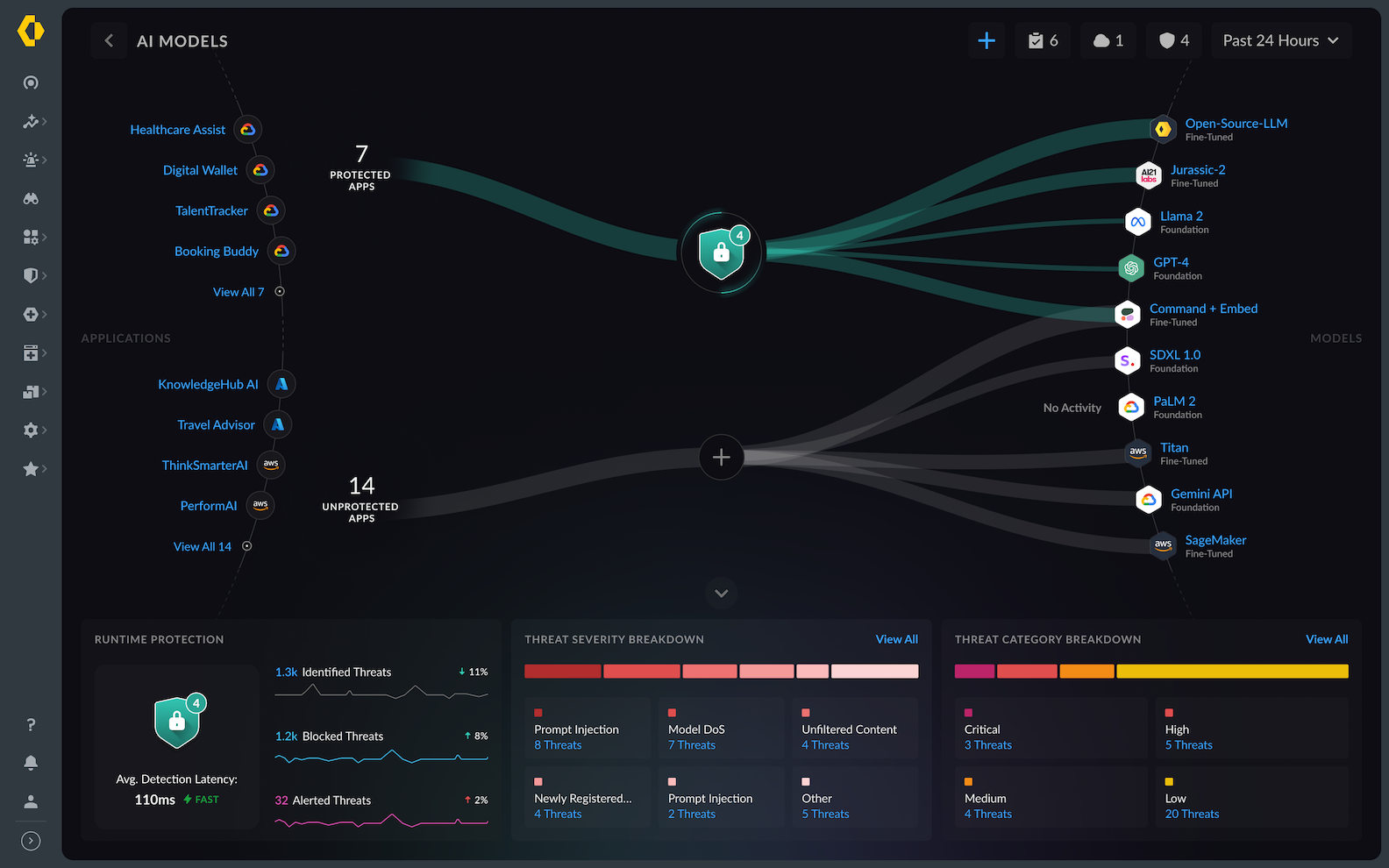
- Identify and prioritize the security threats.
- Summarize alerted model threats, such as prompt injection,
malicious URLs, and sensitive data leakage.
![]()
Click on each application and model to assess how each maps and communicates with other assets in your network architecture.Select Add Protection ("+" icon) and place Prisma AIRS: Network intercept between AI models and applications.Refer to Deploy Prisma AIRS AI Runtime and VM-Series Firewalls for your cloud provider's workflow.Internet View
Assess outbound network traffic flow from user applications to internet destinations. Deploy Prisma AIRS AI Runtime: Network intercept or VM-Series immediately for internet-facing AI applications. Configure AI application protection in your AI security profile, then push the security policy rules to the firewalls. Set up threat monitoring for all AI services receiving traffic from external sources. - Hover over and click the INTERNET protection icon to identify:
- Internet-facing applications.
- Protected and unprotected apps in your cloud environment.
- Safe and unsafe internet destinations reached by the apps.
- Security threats in the network flow between apps and the internet.
- Threat details by clicking on each app.
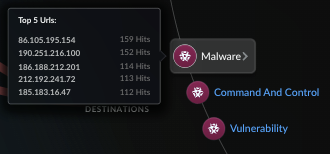
![]() Hover over an internet destination URL to see the IP addresses of the top 5 URLs accessing that destination.
Hover over an internet destination URL to see the IP addresses of the top 5 URLs accessing that destination.![]() Select Add Protection ("+" icon) and place Prisma AIRS: Network intercept or VM-Series between the internet and applications.Refer to Deploy Prisma AIRS AI Runtime and VM-Series Firewalls for your cloud provider's workflow.
Select Add Protection ("+" icon) and place Prisma AIRS: Network intercept or VM-Series between the internet and applications.Refer to Deploy Prisma AIRS AI Runtime and VM-Series Firewalls for your cloud provider's workflow.Users View
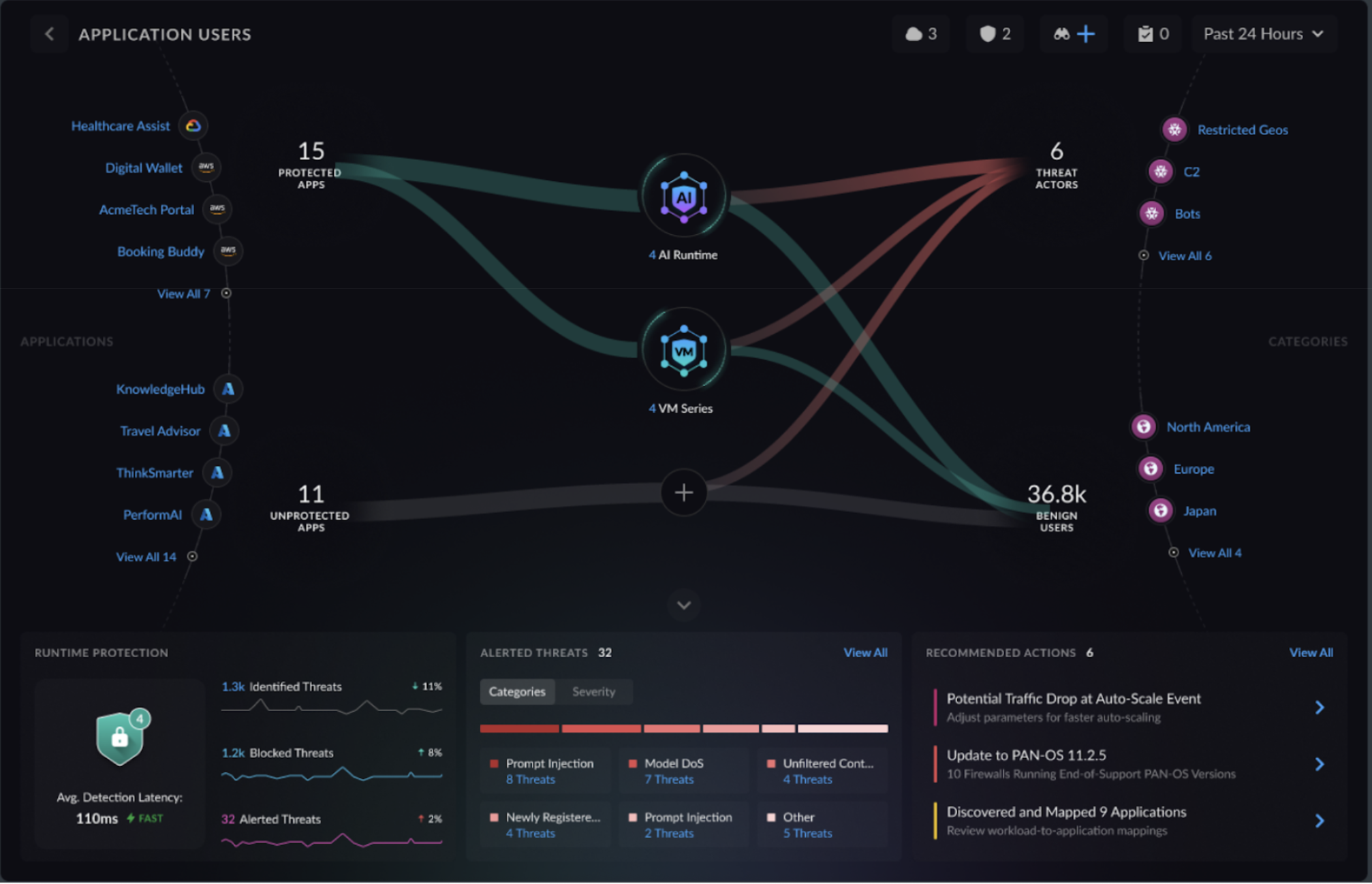
Assess inbound network traffic from external applications to internal user applications. Deploy Prisma AIRS: Network intercept or VM-Series immediately to secure the exposed application endpoints receiving external traffic. Configure an AI security policy by enabling AI application protections, then push the security policy rule to your deployed firewall to prevent malicious attacks and unauthorized data access. - Hover over and click the USERS protection icon to:
- Highlight unprotected traffic flows.
- Identify the protected and unprotected apps.
- Determine threat actors, suspicious users, and benign users.
- View application threat details by clicking on each application.
![]() Select Add Protection ("+" icon) and place Prisma AIRS: Network intercept between users and applications.Refer to Deploy Prisma AIRS AI Runtime and VM-Series Firewalls for your cloud provider's workflow.
Select Add Protection ("+" icon) and place Prisma AIRS: Network intercept between users and applications.Refer to Deploy Prisma AIRS AI Runtime and VM-Series Firewalls for your cloud provider's workflow.
Application Threats Breakdown
Assess application threats discovery shows the discovered threats from both Prisma AIRS AI Runtime: Network intercept and VM-Series firewall. ![]()
- Select the Security view on the Strata Cloud Manager dashboard.Click on the Apps icon. This view will:
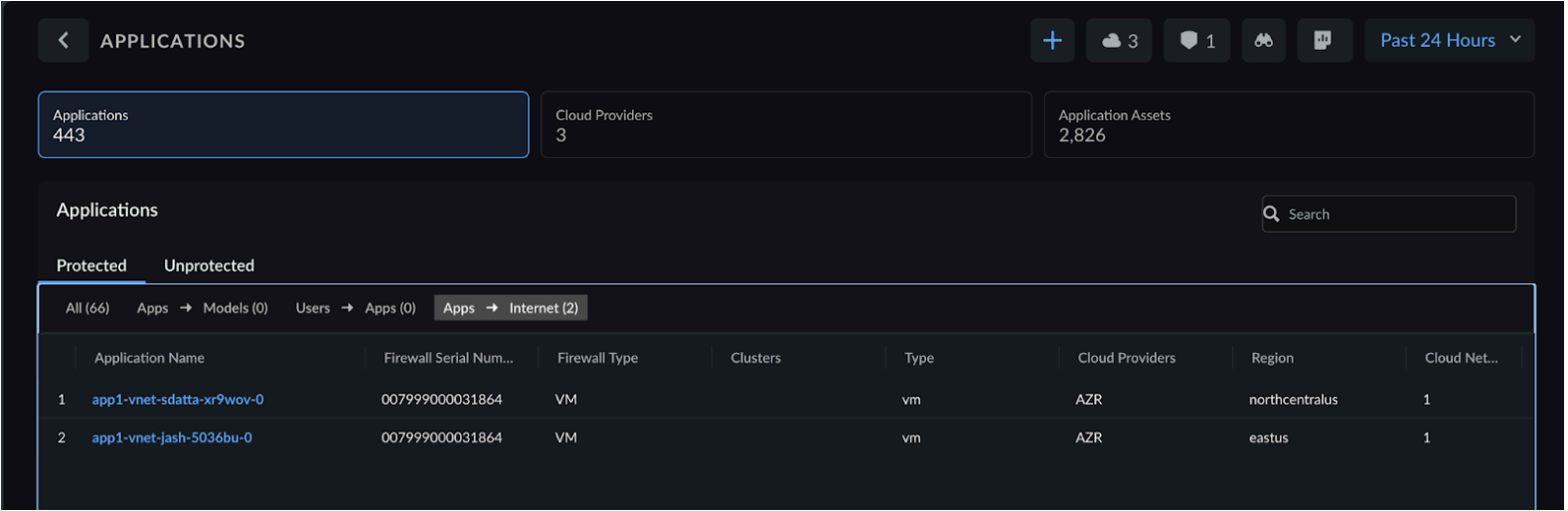
- Group application threats under Applications, Cloud Providers, and Application Assets.
- Classify applications as protected or unprotected applications, including metadata such as Application Asset IP address, Cloud Networks, Region, Cloud Provider, and Tags used to categorize the apps.
- Drill down to see the network traffic flows between Apps → Models, Users → Apps, and Apps → Internet.
The application details include:- Firewall Serial Number: Displays the unique identifier for each firewall protecting your applications.
- Firewall Type: Identifies whether protection is provided by
Prisma AIRS AI Runtime: Network intercept
or VM-Series.Network Traffic Flow Paths: Shows traffic flows and indicates which firewall platform inspects each application
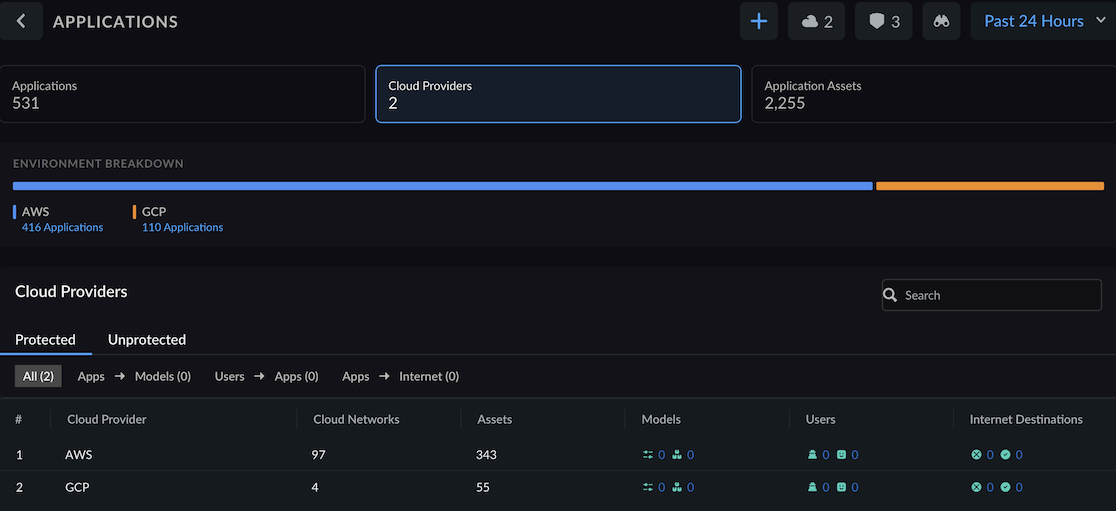
Select Application Breakdown to view applications grouped by your cloud workloads, such as VMs and Pods (including containerized environments, Clusters, VMs, and Serverless architectures).This breakdown shows applications scoped in the "Application definition" during Cloud account onboarding in Strata Cloud Manager.Select the Cloud Providers tab to view the application threat breakdown by the cloud provider.![]() When reviewing the Application breakdown section on the Applications page, you might observe that the sum of VM and Pod applications doesn't always equal the total number of applications displayed at the top of the page. This is because some applications are categorized as both VM and Pod types, leading to their inclusion in both respective counts within the breakdown.However, the total application count prominently displayed remains accurate, representing the unique number of applications across all types, without any double-counting.Select the Application Assets view to analyze the threat breakdown based on traffic generated from interactions between endpoints and applications.
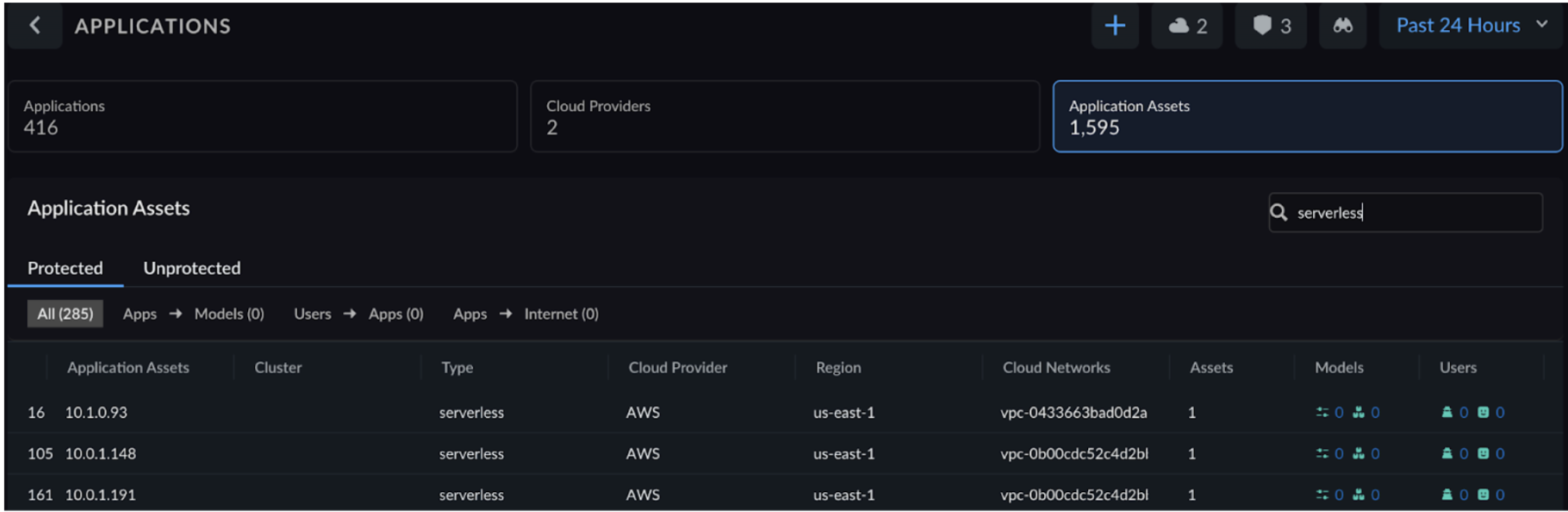
When reviewing the Application breakdown section on the Applications page, you might observe that the sum of VM and Pod applications doesn't always equal the total number of applications displayed at the top of the page. This is because some applications are categorized as both VM and Pod types, leading to their inclusion in both respective counts within the breakdown.However, the total application count prominently displayed remains accurate, representing the unique number of applications across all types, without any double-counting.Select the Application Assets view to analyze the threat breakdown based on traffic generated from interactions between endpoints and applications.![]() For Azure, the feature discovers Function Apps and identifies associated outbound IP addresses. On AWS, it discovers Lambda functions and their linked Elastic Network Interfaces (ENIs). This information allows you to understand which serverless assets are exposed to the internet versus which are contained within protected networks.
For Azure, the feature discovers Function Apps and identifies associated outbound IP addresses. On AWS, it discovers Lambda functions and their linked Elastic Network Interfaces (ENIs). This information allows you to understand which serverless assets are exposed to the internet versus which are contained within protected networks.