Download PDF
Cloud NGFW for AWS
AWS Account(s) Linkage
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
AWS Account(s) Linkage
Learn about how to link your AWS account.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
A Cloud NGFW for AWS tenant is the central management entity that connects Palo Alto
Networks’ Next-Generation Firewall (NGFW) service with your AWS environment. This
linkage involves different types of AWS accounts—subscribed, onboarded, and
allowlisted—each serving a specific purpose in managing access, billing, and service
control.
Types of AWS Account Linkages
| Functions | Description |
|---|---|
| Subscribed Accounts | AWS accounts that have completed the Cloud NGFW for AWS subscription via AWS Marketplace. These accounts are billing-enabled, allowing Cloud NGFW to send metering records to the AWS Marketplace metering service via the billing link established with these account(s). |
| Onboarded Accounts | AWS accounts that are explicitly delegated to Palo Alto Networks using an IAM role. This allows the Cloud NGFW service to access AWS resources in the AWS account for storing logs in CloudWatch log groups, or Kinesis Firehose, for accessing decryption certificates in AWS Secrets Manager, for harvesting resource tags, and optionally creating and deleting NGFW endpoints. |
| Allowlisted Accounts (v2 tenants only) | AWS accounts that have explicit access permissions granted to create VPC endpoints for a specific Cloud NGFW resource. These accounts may or may not be previously onboarded or subscribed. |
Subscribed Accounts
When you get started from an AWS member account or AWS Firewall Manager account, you
subscribe from your AWS Marketplace console to create a new Cloud NGFW tenant
with your AWS account. You can also log in to an additional AWS account and
again subscribe from your AWS Marketplace console to add an AWS account to an
existing Cloud NGFW tenant.
This action establishes a billing link between the Cloud NGFW tenant
and your AWS account. enabling metering records to be sent from Cloud NGFW to
the AWS Marketplace Metering Service. Your Cloud NGFW resources remain intact
during this transition.
If you have previously started from Strata Cloud Manager and
implicitly created a Cloud NGFW tenant, you can now generate a unique billing
code in SCM by specifying your AWS account ID. Then, log in to the
same AWS account, navigate to AWS Marketplace, and subscribe to Cloud
NGFW using the provided billing code.
In either case, this action establishes a billing link between the
Cloud NGFW tenant and your AWS account. enabling metering records to be sent
from Cloud NGFW to the AWS Marketplace Metering Service. Your Cloud NGFW
resources remain intact during this transition.
When you subscribe from multiple AWS accounts to the same Cloud NGFW
tenant, the Cloud NGFW tenant centralizes billing using the subscribed AWS
accounts. If the first account unsubscribes, the Cloud NGFW platform dynamically
selects the second subscribed account for sending metering and overage
records.
For more information, see
- Subscribe to an existing Cloud NGFW tenant started from an AWS member account
- Subscribe to an existing Cloud NGFW tenant started from Strata Cloud Manager
Onboarded Accounts
You can also onboard up to 200 AWS accounts to the tenant by
establishing cross-account access using AWS IAM roles
that allow Cloud NGFW to access AWS resources (for storing logs in
CloudWatch log groups, or Kinesis Firehose, for accessing decryption
certificates in AWS Secrets Manager, harvesting resource tags, and optionally
creating and managing NGFW endpoints) in the AWS account.
Each onboarded account must provide specific IAM roles and permissions
to the Cloud NGFW service for granular administration and control. From then on,
all administrative actions are governed by AWS IAM policies, ensuring secure and
auditable delegation of permissions.
Onboarded Accounts
You can also onboard up to 200 AWS accounts to the tenant by
establishing cross-account access using AWS IAM roles
that allow Cloud NGFW to access AWS resources (for storing logs in
CloudWatch log groups, or Kinesis Firehose, for accessing decryption
certificates in AWS Secrets Manager, harvesting resource tags, and optionally
creating and managing NGFW endpoints) in the AWS account.
Each onboarded account must provide specific IAM roles and permissions
to the Cloud NGFW service for granular administration and control. From then on,
all administrative actions are governed by AWS IAM policies, ensuring secure and
auditable delegation of permissions.
For more information, see:
Onboarding AWS Account to Cloud NGFW Console
- Initiate the AWS account onboarding process.
- Log in to your AWS account.
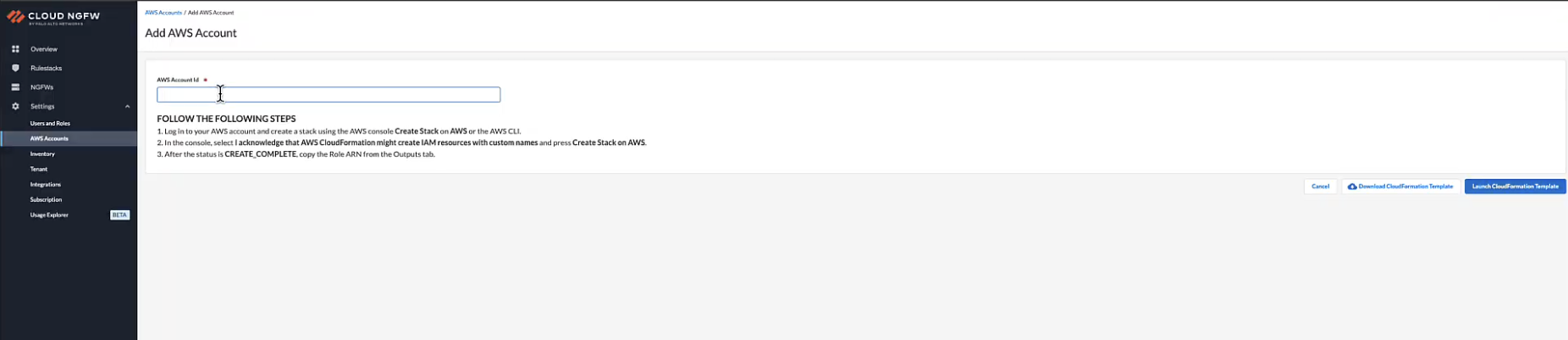
- Go to Settings > AWS Accounts.
- Click Add AWS Account.
![]()
- Enter the AWS Account ID.
![]()
- Click Launch CloudFormation Stack.
![]()
- This step will open a new browser tab and redirect you to the AWS CloudFormation console.
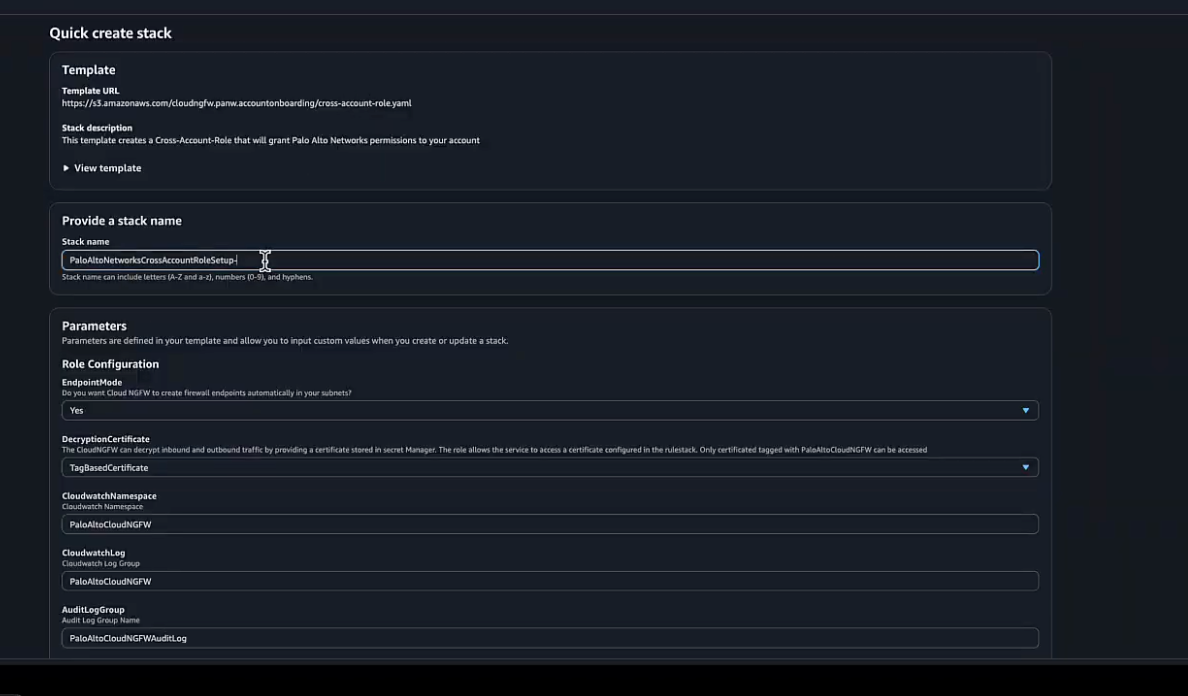
Configure the CloudFormation Stack.- Once redirected to the Quick create stack page in AWS, verify that the Template URL is correctly pre-populated. The Stack name field will also be pre-filled; you can keep the default name.
- Review the parameters like PolicyName, AccessRoleName, and ExternalId and ensure they are correct.
![]()
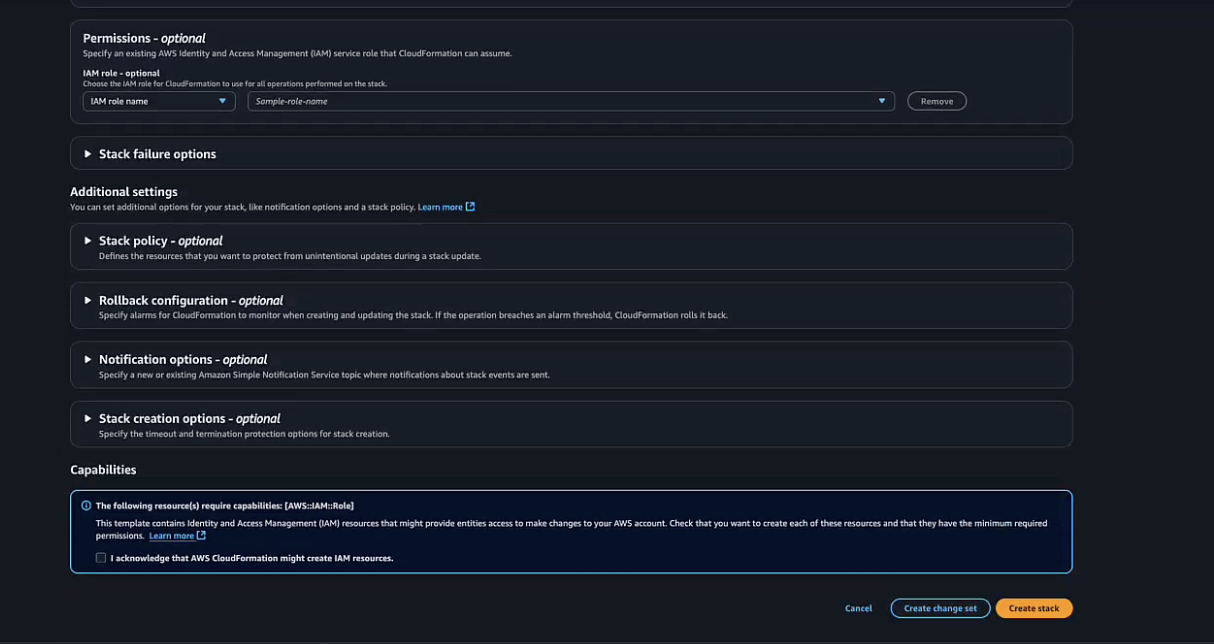
- Select I acknowledge that AWS CloudFormation might create IAM resources with custom names checkbox.
- Click Create Stack.The stack creation process will begin.
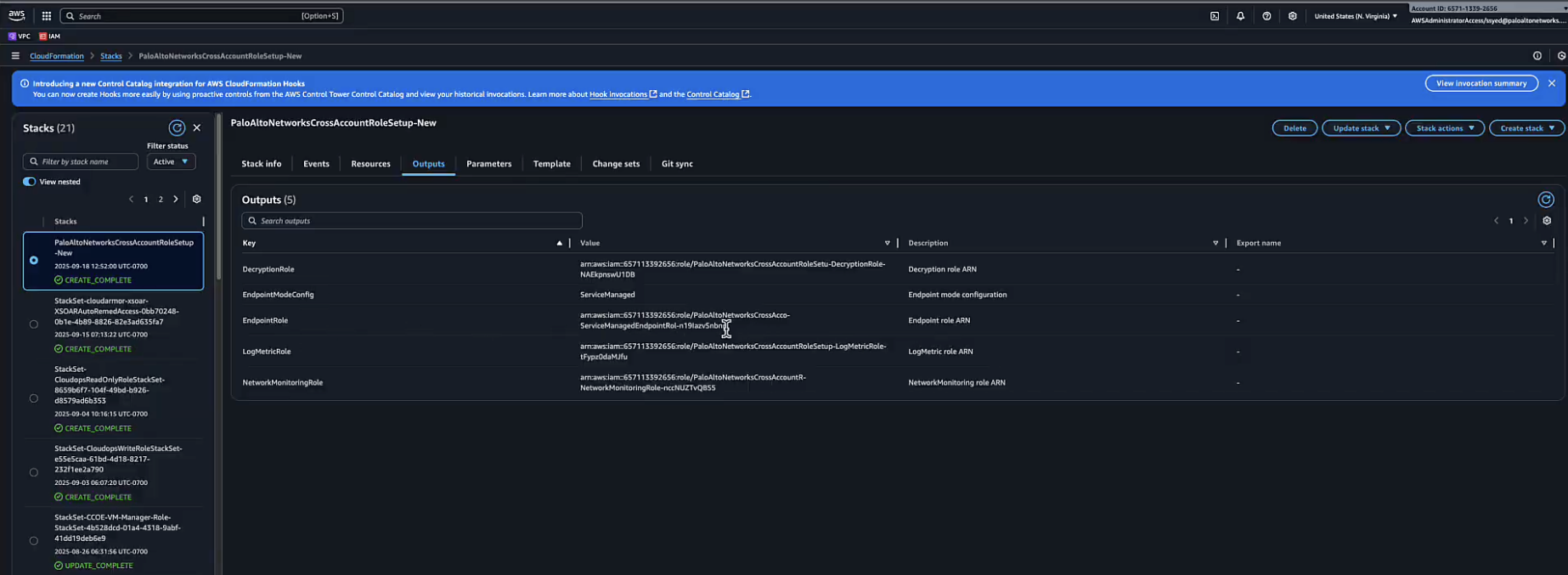
Monitor Stack Creation and Retrieve OutputsYou will be redirected to the Stacks page in the AWS console. The status of your new stack will be CREATE_IN_PROGRESS. Wait for the stack creation to complete. You may need to refresh the page to see the updated status.- Once the status changes to CREATE_COMPLETE, select the stack and
click the Outputs tab.
![]()
- The Outputs tab contains key information needed to complete the onboarding, such as the EndpointRoleARN, LoggingMetric Role, and Deployment Role.
Complete Onboarding with retrieved information.- Go to the Cloud NGFW console.
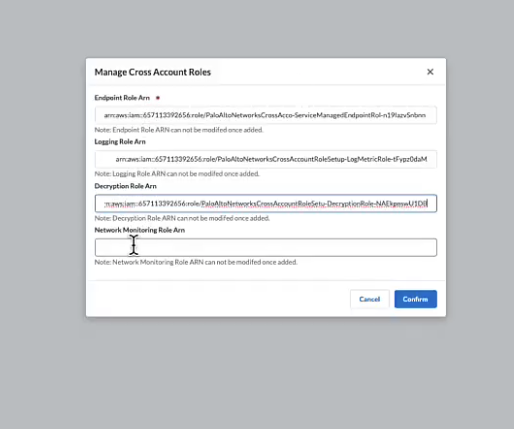
- Click Manage Cross-Account Roles.
![]()
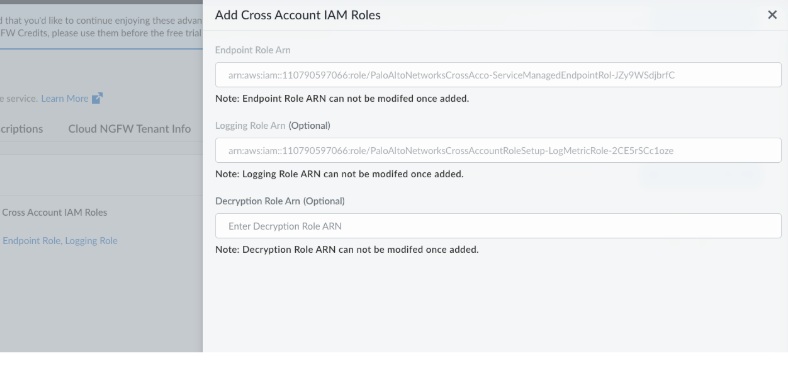
- A new pop-up window will appear. Paste the EndpointRoleARN, LoggingMetric Role, Deployment Role ARN, and NetworkMonitoring Role ARN from the AWS CloudFormation outputs into the corresponding fields.
- Click Save.
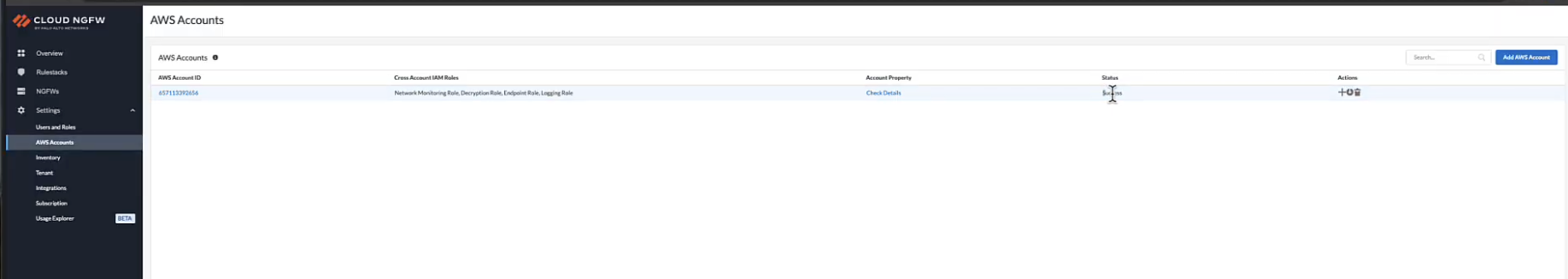
![]() The system will now validate the connection to the AWS account. Once the validation is successful, the AWS account is onboarded and will appear in your list of accounts with a SUCCESS status.
The system will now validate the connection to the AWS account. Once the validation is successful, the AWS account is onboarded and will appear in your list of accounts with a SUCCESS status.Onboarding AWS Account in Strata Cloud Manager
If you have previously started from strata cloud manager, you can access the Cloud NGFW page in the Strata Cloud Manager console to onboard an AWS account in Strata Cloud Manager.To enable Strata Cloud Manager (SCM) to manage your Cloud NGFW for AWS resources, you must onboard your AWS account to the SCM UI. This process involves creating cross-account roles in your AWS environment and providing the Amazon Resource Names (ARNs) to SCM.Prerequisites:- You must have an SCM user role with write access, such as Superuser or Network Administrator.
- The AWS account you are onboarding must not already be subscribed to a Cloud NGFW tenant.
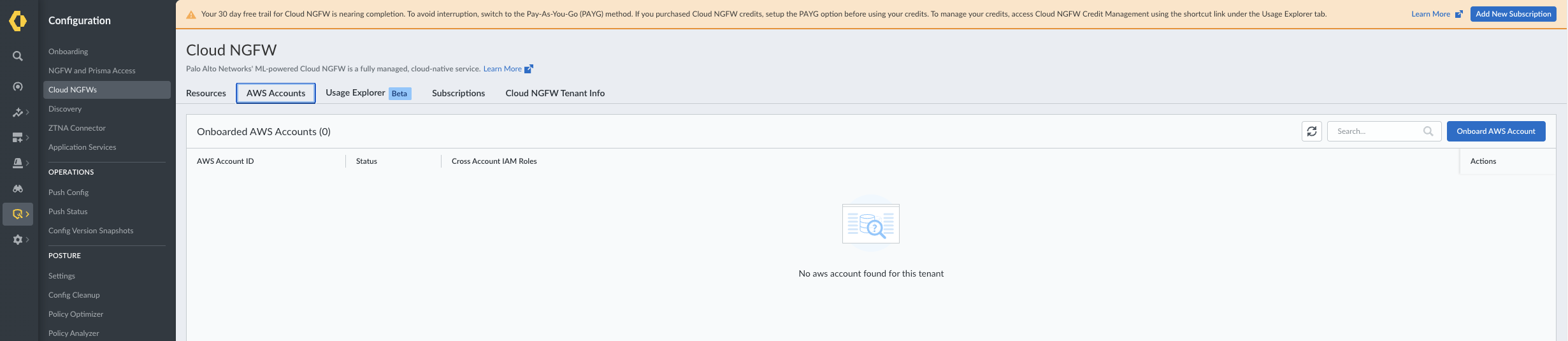
The following are the steps to onboard an AWS account in SCM:- From the SCM UI, go to Cloud NGFW.In the AWS Accounts section, click Onboard AWS Account.
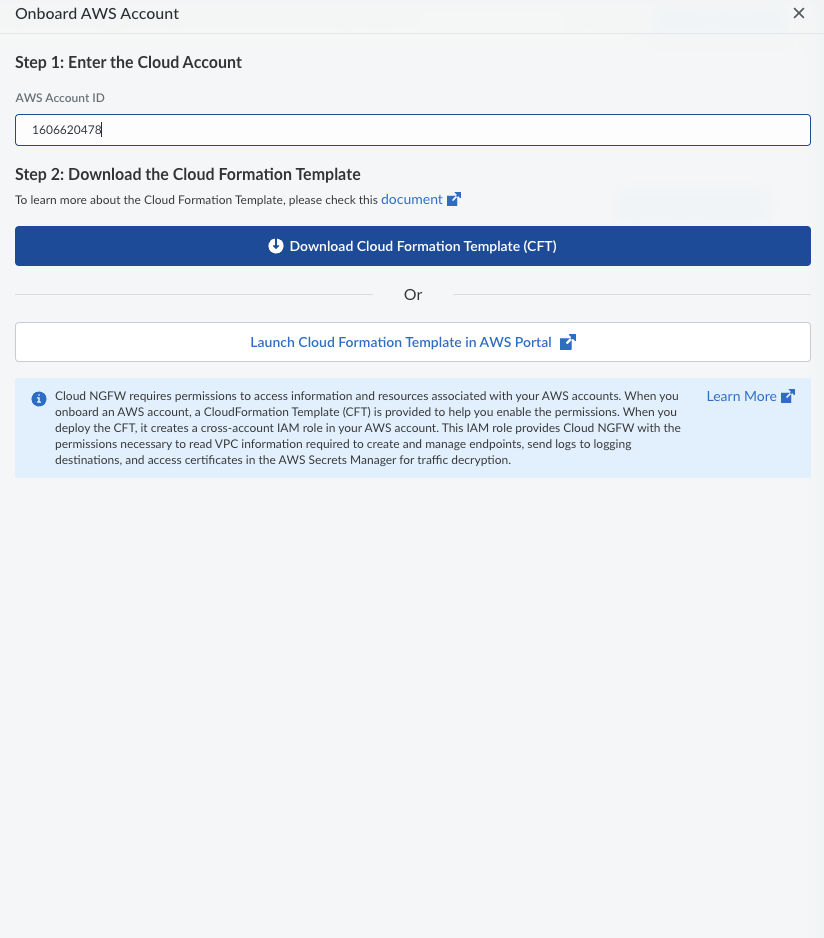
![]() In the Onboard AWS Account pop-up window, enter your AWS Account ID in Step 1: Enter the Cloud Account.
In the Onboard AWS Account pop-up window, enter your AWS Account ID in Step 1: Enter the Cloud Account.![]() In Step 2: Download the Cloud Formation Template, click Download Cloud Formation Template (CFT) or Launch Cloud Formation Template in AWS Portal. This template helps you to create the necessary cross-account IAM roles in your AWS account. The roles provide SCM with the permissions to read VPC information, create and manage endpoints, and send logs.Go to your AWS account and deploy the CFT to create the required roles:Logging Role, Endpoint Role, Network Monitoring Role, and Decryption Role . For more information, see Create Cloud NGFW for AWS EndpointsOnce the roles are created in your AWS account, copy the Amazon Resource Names (ARNs) for each role.Return to the SCM UI. In the Add Cross Account IAM Roles section, manually enter the copied ARNs for each of the four roles.
In Step 2: Download the Cloud Formation Template, click Download Cloud Formation Template (CFT) or Launch Cloud Formation Template in AWS Portal. This template helps you to create the necessary cross-account IAM roles in your AWS account. The roles provide SCM with the permissions to read VPC information, create and manage endpoints, and send logs.Go to your AWS account and deploy the CFT to create the required roles:Logging Role, Endpoint Role, Network Monitoring Role, and Decryption Role . For more information, see Create Cloud NGFW for AWS EndpointsOnce the roles are created in your AWS account, copy the Amazon Resource Names (ARNs) for each role.Return to the SCM UI. In the Add Cross Account IAM Roles section, manually enter the copied ARNs for each of the four roles.![]() After providing the role ARNs, click Onboard to complete the process. The SCM UI will validate the roles, and the AWS account will be successfully onboarded.
After providing the role ARNs, click Onboard to complete the process. The SCM UI will validate the roles, and the AWS account will be successfully onboarded.Allowlisted Accounts (v2 tenants only)
When creating a Cloud NGFW resource, you can add one or more of your AWS accounts to its allow-list. From then on, a VPC endpoint service, corresponding to the Cloud NGFW resource, will manifest in your (allow-listed) AWS account(s). You can then create endpoints in your VPC to redirect traffic to the Cloud NGFW resources.