Download PDF
Cloud NGFW for AWS
Cloud NGFW for AWS Advanced Threat Protection
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Cloud NGFW for AWS Advanced Threat Protection
Advanced threat protection is an intrusion prevention system (IPS).
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
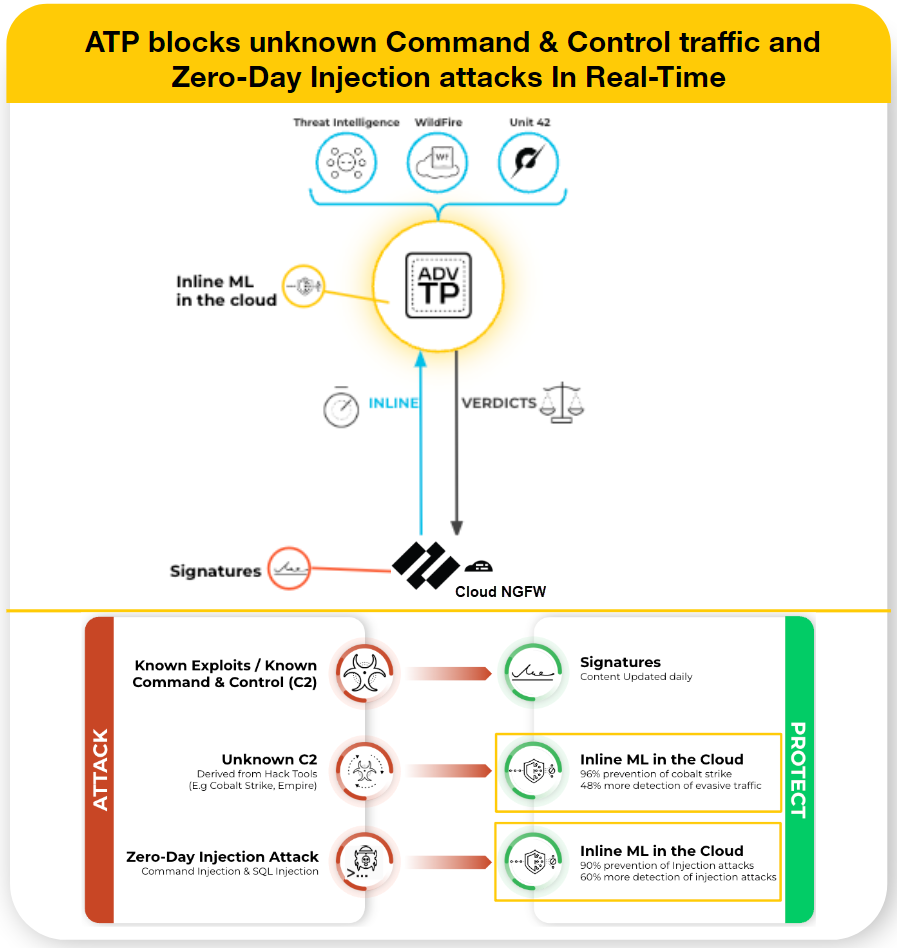
Advanced Threat Prevention (ATP) is an intrusion prevention system (IPS) solution
that can detect and block malware, vulnerability exploits, and command and control
(C2) across all ports and protocols, using a multilayered prevention system with
components operating on Cloud NGFW for AWS and in the cloud. The Threat Prevention
cloud operates a multitude of detection services using the combined threat data from
Palo Alto Networks services to create signatures, each possessing specific
identifiable patterns, and are used by the Cloud NGFW for AWS to enforce security
policy rules when matching threats and malicious behaviors are detected. These
signatures are categorized based on the threat type and are assigned unique
identifier numbers. To detect threats that correspond with these signatures, Cloud
NGFW for AWS operates analysis engines that inspect and classify network traffic
exhibiting anomalous traits.
After enabling Advanced
Threat Prevention, use Panorama to configure associated Advanced Threat
Prevention policies.
In addition to the signature-based detection mechanism, Advanced Threat Prevention
provides an inline detection system to prevent unknown and evasive C2 threats,
including those produced through the Empire framework, as well as command injection
and SQL injection vulnerabilities. The Advanced Threat Prevention cloud operates
extensible deep learning models that enable inline analysis capabilities on Cloud
NGFW for AWS, on a per-request basis to prevent zero-day threats from entering the
network as well as to distribute protections. This allows you to prevent unknown
threats using real-time traffic inspection with inline detectors. These deep
learning, ML-based detection engines in the Advanced Threat Prevention cloud analyze
traffic for unknown C2 and vulnerabilities that utilize SQL injection and command
injection to protect against zero-day threats. To provide a threat context and
comprehensive detection details, reports are generated that can include the tools
and techniques used by the attacker, the scope, and impact of the detection, as well
as the corresponding cyberattack classification as defined by the MITRE
ATT&CK® framework.
Native Policy Management
Advanced Threat Prevention (ATP) is configured automatically when you create a
new local rulestack. For rulestacks that you previously created before March
2024, manually enable ATP using the Cloud NGFW for AWS console.
To enable ATP for a rulestack:
- Log into the Cloud NGFW console.Select Rulestacks.Select Security Profiles.In the Threat Prevention section, use the toggle to enable Advanced Threat Prevention.
![]() A confirmation dialog appears, indicating that the ATP feature may result in charges being applied. Click Enable. View your AWS billing subscription for details.You use Panorama to configure your ATP subscription within your network security deployment. While it may not be necessary to implement all of the processes comprising ATP, Palo Alto Networks recommends reviewing all of the tasks to familiarize yourself with the available options for a successful deployment.
A confirmation dialog appears, indicating that the ATP feature may result in charges being applied. Click Enable. View your AWS billing subscription for details.You use Panorama to configure your ATP subscription within your network security deployment. While it may not be necessary to implement all of the processes comprising ATP, Palo Alto Networks recommends reviewing all of the tasks to familiarize yourself with the available options for a successful deployment.Panorama Policy Management
Advanced Threat Prevention (similar to other Palo Alto Networks security services) is administered through security profiles, which in turn is dependent on the configuration of network enforcement policies as defined through security policy rules.You use the Cloud NGFW for AWS to enable Advanced Threat Prevention for the rulestack, however, you must use Panorama to configure the policies that comprise the security service.To configure Advanced URL Filtering policy rules using Panorama:- Login to Panorama.Check that you have the appropriate license subscription for Advanced URL Filtering. In Panorama, select Device > Licenses. Verify that the license expiration date is in the future.Set up Advanced Threat Prevention using Panorama.Commit your changes.Palo Alto Networks provides several options to monitor activity processed by the Advanced Threat Prevention security service. See Monitor Advanced Threat Prevention for more information.