Enterprise DLP
Activate Endpoint DLP
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Activate Endpoint DLP
Activate Endpoint DLP to stop accidental or malicious data lose over peripheral
devices.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
| Prisma Access (Managed by Strata Cloud Manager) |
|
Activate Endpoint DLP for single tenant or multitenant Customer Support Portal (CSP)
account to prevent exfiltration of sensitive data to peripheral devices such as USB
devices, printers, and network shares, or to control access to them. Before you
active the Endpoint DLP license, you must enable set up the Prisma Access Agent configuration file to enable the Endpoint DLP functionality and then install the
Prisma Access Agent on all endpoints you want to protect.
Activating the Endpoint DLP license gives you access to Enterprise Data Loss Prevention (E-DLP)
advanced detection methods, data patterns, and data profiles.
For production Prisma Access Agent and Endpoint DLP deployments, Palo Alto Networks requires mobile device management (MDM) deployment to install
Prisma Access Agent on endpoints to enable Endpoint DLP. This is required
because:
- When transitioning from GlobalProtect to Prisma Access Agent, the endpoint doesn't support granting required manual extension access if you previously installed GlobalProtect using MDM deployment.
- Successfully setting up Prisma Access Agent for Endpoint DLP requires many different settings and configurations. Palo Alto Networks requires MDM deployment of Prisma Access Agent to reduce the chance of misconfiguration on multiple endpoints and increase the chance of a successful deployment.
Endpoint DLP doesn't support GlobalProtect. You must install Prisma Access Agent to use Endpoint DLP.
Single Tenant
Activate Endpoint DLP to prevent exfiltration of sensitive data over peripheral
devices for a single tenant Customer Support Portal account.
- Contact your Palo Alto Networks representative to purchase the Endpoint DLP subscription.Click the magic link provided to you by Palo Alto Networks when you purchased the Endpoint DLP subscription.Activate Subscription to begin activating Endpoint DLP.
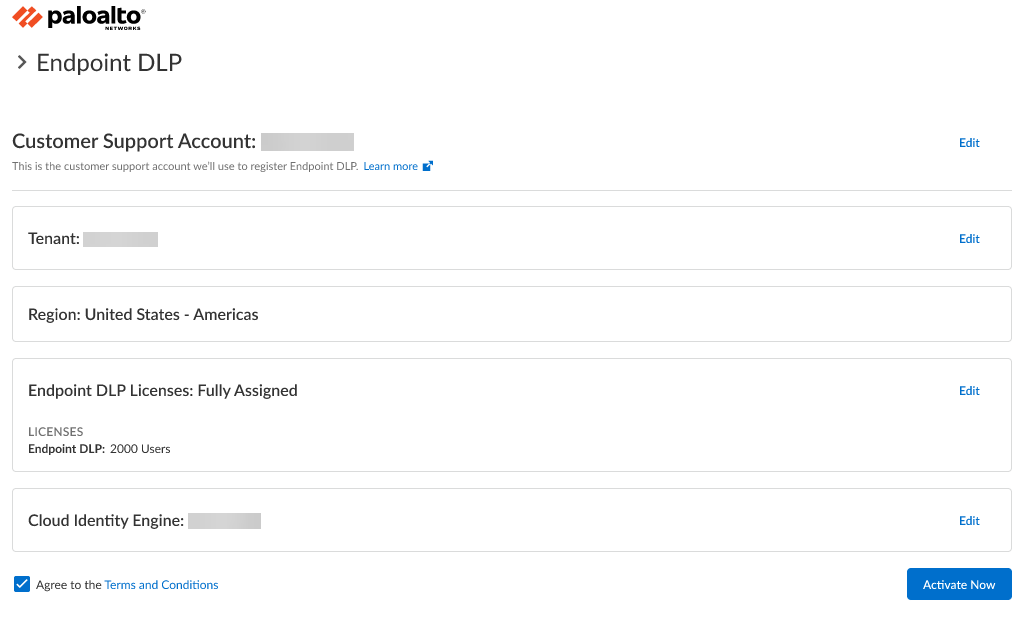
![]() Enter your Email Address and click Next to continue.This email address must match the email that received the magic link to activate Endpoint DLP and must have a valid Palo Alto Networks Customer Support Portal account.Click Create a New Account if you're a security administrator who does not yet have a valid Palo Alto Networks Customer Support Portal account for your organization. This is required before you can continue activating Endpoint DLP.Verify the tenant details for which you're activating Endpoint DLP.This information is populated by default when the magic link is generated. Palo Alto Networks recommends verifying the following tenant details before activation to resolve any issues before activation.
Enter your Email Address and click Next to continue.This email address must match the email that received the magic link to activate Endpoint DLP and must have a valid Palo Alto Networks Customer Support Portal account.Click Create a New Account if you're a security administrator who does not yet have a valid Palo Alto Networks Customer Support Portal account for your organization. This is required before you can continue activating Endpoint DLP.Verify the tenant details for which you're activating Endpoint DLP.This information is populated by default when the magic link is generated. Palo Alto Networks recommends verifying the following tenant details before activation to resolve any issues before activation.- Customer Support Account—Endpoint DLP must be activate on the same Customer Support Portal account as Enterprise DLP.
- Region—Region is populated by default and is based on the region configured for the Customer Support Portal tenant. This can’t be changed.
- Endpoint DLP Licenses—Endpoint DLP license must be Fully Assigned and display the total number of supported users.
Agree to the Terms and Conditions.Activate Now.![]() Set up Prisma Access Agent and install it on your endpoints.(Manual Install for Trials and Evaluations) Palo Alto Networks supports manual Prisma Access Agent installs only for trials and evaluations. Your security administrators might not use an MDM to install Prisma Access Agent or a configuration profile to enable Endpoint DLP. In this case, after you install Prisma Access Agent on the endpoint, Prisma Access Agent prompts the end user to Open System Settings and enable the following two extensions:
Set up Prisma Access Agent and install it on your endpoints.(Manual Install for Trials and Evaluations) Palo Alto Networks supports manual Prisma Access Agent installs only for trials and evaluations. Your security administrators might not use an MDM to install Prisma Access Agent or a configuration profile to enable Endpoint DLP. In this case, after you install Prisma Access Agent on the endpoint, Prisma Access Agent prompts the end user to Open System Settings and enable the following two extensions:- PASrv
- Enforcer
The end user must enable these to extensions on Prisma Access Agent to use Endpoint DLP when installing Prisma Access Agent without using a configuration profile to manage the Endpoint DLP configuration.- Ensure your network allows access to pool.ntp.org.Prisma Access Agent requests NTP timestamps from pool.ntp.org to ensure endpoints are not affected by any system time change by the end user.If Prisma Access Agent can't request NTP timestamps, it experiences communication issues with Enterprise DLP and the file explorer on the endpoint device may become unresponsive when moving files from one folder to another if the file movement matches the data-in-motion Endpoint DLP policy rule.(SSL Decryption) If you configured SSL decryption for Prisma Access, you must add the following decryption exclusion entry for Enterprise DLP.*.dss.paloaltonetworks.comDownload the Prisma Access Agent package.You must first download the Prisma Access Agent from Strata Cloud Manager so that you can deploy it to your mobile users' endpoints using third-party mobile device management (MDM) software.Skip this step if you already uploaded the Prisma Access Agent package to your MDM.Upload the Prisma Access Agent package to your MDM and install Prisma Access Agent all endpoints you want to protect.You must use one of the supported mobile device management (MDM) installation methods if the endpoint currently has GlobalProtect or Cortex XDR installed. Prisma Access Agent does not support manual installation if GlobalProtect or Cortex XDR are already installed on the endpoint.Allow the Prisma Access Agent processes for your Endpoint Detection and Response (EDR) tools.At a minimum, you must allow all DLP (Microsoft Windows) or pangdlp (macOS) Endpoint DLP processes.However, Palo Alto Networks recommends allowing all Prisma Access Agent processes to prevent your EDR tools from flagging Endpoint DLP and other Prisma Access Agent processes as malicious. Not allowing these processes might result in unexpected behavior and might prevent Endpoint DLP functionality.Set up Endpoint DLP.
- Edit the Endpoint DLP data filtering settings and snippet settings to define the operational parameters.Enable Optical Character Recognition on Strata Cloud Manager to scan files with images containing sensitive information.Create an Endpoint DLP policy rule to control access to peripheral devices and prevent exfiltration of sensitive data.The Prisma Access Agent displays the Endpoint DLP service as disabled until you push an Endpoint DLP policy rule from Strata Cloud Manager to the Prisma Access Agent installed on the endpoint.(Optional) Save evidence for investigative analysis with Enterprise DLP to connect an AWS storage bucket, Azure storage bucket, or SFTP server to Enterprise DLP to automatically store evidence of inspected traffic.(Optional) Add peripheral devices to Endpoint DLP.(Optional) Create a peripheral group to group similar types of peripheral devices together for easier application of Endpoint DLP policy rules.(Optional) Create a User Coaching Notification Template for Endpoint DLP.The End User Coaching Notification Template allows you to configure the notification displayed to your users in the Access Experience User Interface (UI) when they generate a DLP incident.For the Product Name, select Endpoint Data Loss Prevention. Configure the Applied Rules and Notification Message as needed.
Multitenant
Activate Endpoint DLP to prevent exfiltration of sensitive data over peripheral devices for a multitenant Customer Support Portal (CSP) account.- Contact your Palo Alto Networks representative to purchase the Endpoint DLP subscription.Click the magic link provided to you by Palo Alto Networks when you purchased the Endpoint DLP subscription.Activate Subscription to begin activating Endpoint DLP.
![]() Enter your Email Address and click Next to continue.This email address must match the email that received the magic link to activate Endpoint DLP and must have a valid Palo Alto Networks Customer Support Portal account.Click Create a New Account if you're a security administrator who does not yet have a valid Palo Alto Networks Customer Support Portal account for your organization. This is required before you can continue activating Endpoint DLP.Verify you're activating Endpoint DLP for the correct Customer Support Portal account.In Specify the Tenant, select the child tenant for which you want to activate Endpoint DLP.Enterprise DLP must be active on the tenant for which you activating Endpoint DLP.Click Done to continue.Verify the tenant details for which you're activating Endpoint DLP.
Enter your Email Address and click Next to continue.This email address must match the email that received the magic link to activate Endpoint DLP and must have a valid Palo Alto Networks Customer Support Portal account.Click Create a New Account if you're a security administrator who does not yet have a valid Palo Alto Networks Customer Support Portal account for your organization. This is required before you can continue activating Endpoint DLP.Verify you're activating Endpoint DLP for the correct Customer Support Portal account.In Specify the Tenant, select the child tenant for which you want to activate Endpoint DLP.Enterprise DLP must be active on the tenant for which you activating Endpoint DLP.Click Done to continue.Verify the tenant details for which you're activating Endpoint DLP.- Region—Region is populated by default and is based on the child tenant you selected in the previous step. This can’t be changed.
- Endpoint DLP Licenses—Endpoint DLP license must be Fully Assigned and display the total number of supported users.
For the Cloud Identity Engine, select the CIE instance associated with your Customer Support Portal account and click Done.Agree to the Terms and Conditions.Activate Now.![]() Set up Prisma Access Agent and install it on your endpoints.(Manual Install for Trials and Evaluations) Palo Alto Networks supports manual Prisma Access Agent installs only for trials and evaluations. Your security administrators might not use an MDM to install Prisma Access Agent or a configuration profile to enable Endpoint DLP. In this case, after you install Prisma Access Agent on the endpoint, Prisma Access Agent prompts the end user to Open System Settings and enable the following two extensions:
Set up Prisma Access Agent and install it on your endpoints.(Manual Install for Trials and Evaluations) Palo Alto Networks supports manual Prisma Access Agent installs only for trials and evaluations. Your security administrators might not use an MDM to install Prisma Access Agent or a configuration profile to enable Endpoint DLP. In this case, after you install Prisma Access Agent on the endpoint, Prisma Access Agent prompts the end user to Open System Settings and enable the following two extensions:- PASrv
- Enforcer
The end user must enable these to extensions on Prisma Access Agent to use Endpoint DLP when installing Prisma Access Agent without using a configuration profile to manage the Endpoint DLP configuration.- Ensure your network allows access to pool.ntp.org.Prisma Access Agent requests NTP timestamps from pool.ntp.org to ensure endpoints are not affected by any system time change by the end user.If Prisma Access Agent can't request NTP timestamps, it experiences communication issues with Enterprise DLP and the file explorer on the endpoint device may become unresponsive when moving files from one folder to another if the file movement matches the data-in-motion Endpoint DLP policy rule.(SSL Decryption) If you configured SSL decryption for Prisma Access, you must add the following decryption exclusion entry for Enterprise DLP.*.dss.paloaltonetworks.comDownload the Prisma Access Agent package.You must first download the Prisma Access Agent from Strata Cloud Manager so that you can deploy it to your mobile users' endpoints using third-party mobile device management (MDM) software.Skip this step if you already uploaded the Prisma Access Agent package to your MDM.Upload the Prisma Access Agent package to your MDM and install Prisma Access Agent all endpoints you want to protect.You must use one of the supported mobile device management (MDM) installation methods if the endpoint currently has GlobalProtect or Cortex XDR installed. Prisma Access Agent does not support manual installation if GlobalProtect or Cortex XDR are already installed on the endpoint.Allow the Prisma Access Agent processes for your Endpoint Detection and Response (EDR) tools.At a minimum, you must allow all DLP (Microsoft Windows) or pangdlp (macOS) Endpoint DLP processes.However, Palo Alto Networks recommends allowing all Prisma Access Agent processes to prevent your EDR tools from flagging Endpoint DLP and other Prisma Access Agent processes as malicious. Not allowing these processes might result in unexpected behavior and might prevent Endpoint DLP functionality.Set up Endpoint DLP.
- Edit the Endpoint DLP data filtering settings and snippet settings to define the operational parameters.Enable Optical Character Recognition on Strata Cloud Manager to scan files with images containing sensitive information.Create an Endpoint DLP policy rule to control access to peripheral devices and prevent exfiltration of sensitive data.The Prisma Access Agent displays the Endpoint DLP service as disabled until you push an Endpoint DLP policy rule from Strata Cloud Manager to the Prisma Access Agent installed on the endpoint.(Optional) Save evidence for investigative analysis with Enterprise DLP to connect an AWS storage bucket, Azure storage bucket, or SFTP server to Enterprise DLP to automatically store evidence of inspected traffic.(Optional) Add peripheral devices to Endpoint DLP.(Optional) Create a peripheral group to group similar types of peripheral devices together for easier application of Endpoint DLP policy rules.(Optional) Create a User Coaching Notification Template for Endpoint DLP.The End User Coaching Notification Template allows you to configure the notification displayed to your users in the Access Experience User Interface (UI) when they generate a DLP incident.For the Product Name, select Endpoint Data Loss Prevention. Configure the Applied Rules and Notification Message as needed.