Device Security
Onboard Device Security on VM-Series with Software NGFW Credits
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Onboard Device Security on VM-Series with Software NGFW Credits
Use Software NGFW credits to onboard Device Security on VM-Series.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
|
A Palo Alto Networks VM-Series is a virtualized
form factor of a Palo Alto Networks next-generation firewall and is intended for use
in a virtualized or cloud environment. When you use Software NGFW credits to fund VM-Series with either fixed or flexible virtual CPUs (vCPUs), you can
include Device Security in the deployment profile during the firewall
registration process.
You can also use Software NGFW credits to fund CN-Series with an
Device Security subscription as long as the firewalls are under Panorama
management. For onboarding instructions of a CN-Series with
Device Security, see Device Security Support for CN-Series Firewall.
The following onboarding procedure is for VM-Series with an Device Security subscription. It assumes that you have already purchased Software
NGFW credits and activated them. At this point, you can use
the Software NGFW credits to purchase VM-Series.
- Create one or more deployment profiles for VM-Series.Create a deployment profile for each type of VM-Series model you want to deploy.
- Log in to the Customer Support Portal (CSP), and—if you have multiple accounts—choose the account you want to use.
- Select ProductsSoftware NGFW Credits to view the Software NGFW Credits Dashboard.
- Locate your purchased NGFW Credits pool on the dashboard and Create Deployment Profile.
![]()
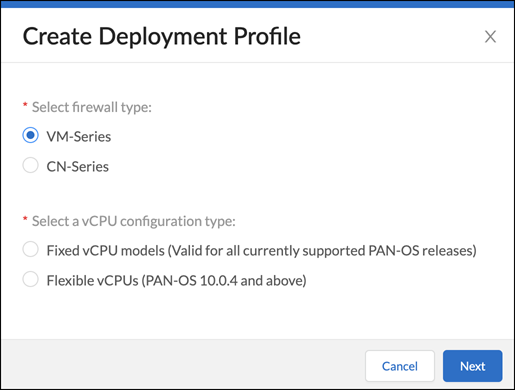
- Select VM Series and either Fixed vCPU models (Valid for all currently supported PAN-OS releases) or Flexible vCPUs (PAN-OS 10.0.4 and above) and then click Next.
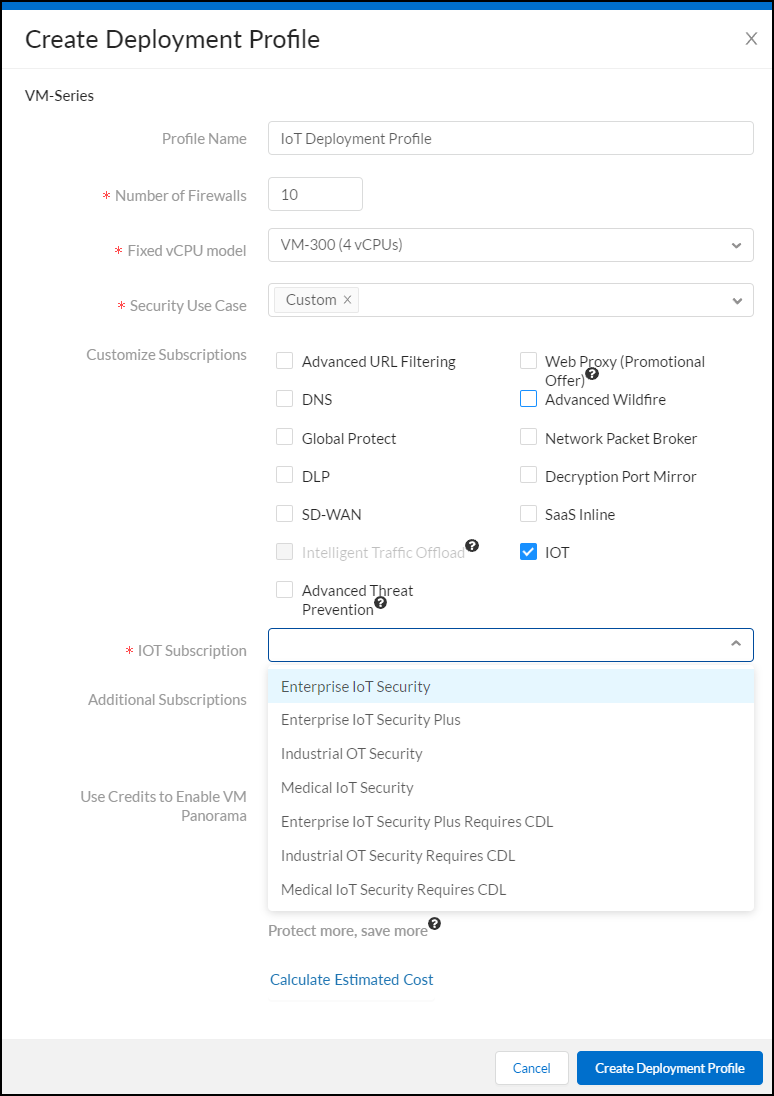
- Assuming you selected Fixed vCPU models (Valid for all currently supported PAN-OS releases), configure the following and then Create Deployment Profile:Profile Name: Enter a name for the deployment profile.Number of Firewalls: Enter the maximum number of firewalls that can be associated with this deployment profile.Fixed vCPU model: Choose a VM-Series model from the list.Security Use Case: Choose Custom.Customize Subscriptions: Clear all preselected items and select IOT.IOT Subscription: Choose the type of Device Security subscription to activate on the VM-Series. The different types are based on vertical themes with or without traffic log retention in Strata Logging Service.Use Credits to Enable VM Panorama: (clear all)
![]() After creating the deployment profile, it appears in the Current Deployment Profiles table on the AssetsSoftware NGFW Credits page.
After creating the deployment profile, it appears in the Current Deployment Profiles table on the AssetsSoftware NGFW Credits page. - (Optional) After you click Create Deployment Profile, you can return to the configuration and click Calculate Estimated Cost to see an estimation of how many Flex credits will be deducted from your account and your remaining balance. If you hover your cursor over the question mark next to the estimate, you can see the credit breakdown for each component.
- If you have other types of firewall models to deploy, create additional deployment profiles, one for each type.
Activate Device Security subscriptions based on the deployment profile in Common Services.- Log in to the hub with your Palo Alto Networks Customer Support credentials.The hub fetches available deployment profiles for this account from the CSP.
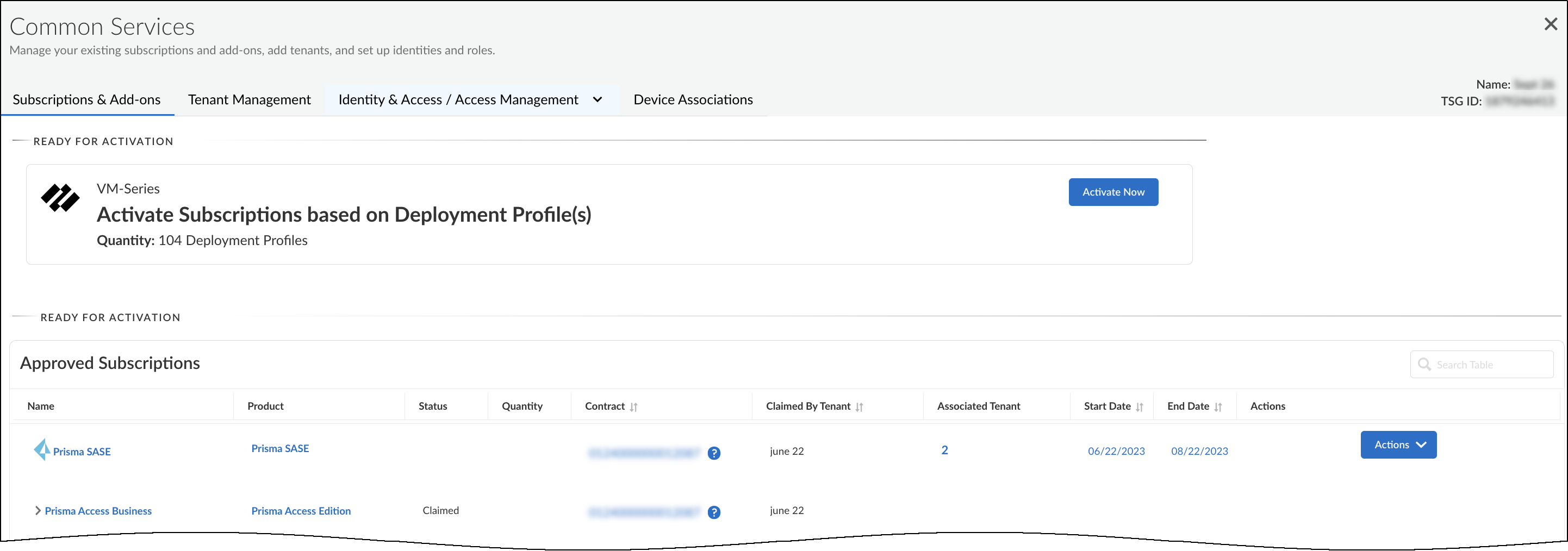
- Select Common ServicesSubscriptions & Add-ons.The deployment profile you created appears in the Ready for Activation section at the top of the page.
![]()
- Click Activate Now.The Activate Subscriptions based on Deployment Profile(s) page appears.
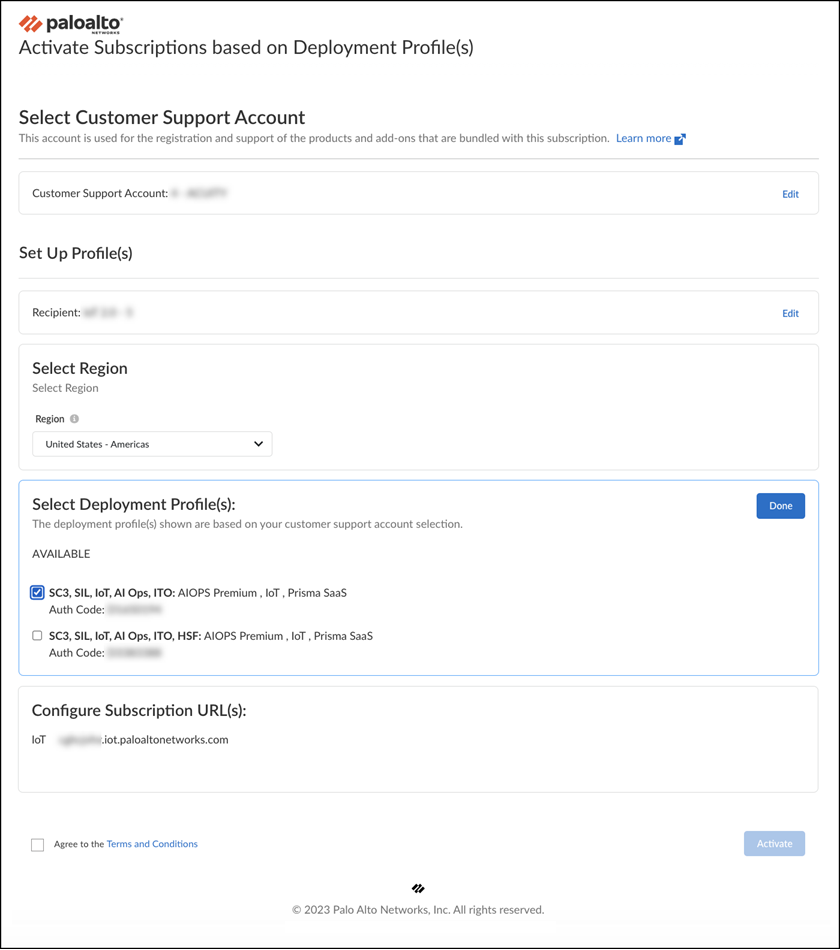
- Configure the following Device Security subscription activation settings:Customer Support Account: Choose your CSP account with the deployment profile.Recipient: Use an existing tenant or create a new one.To create a new tenant, hover your cursor over All Tenants at the top of the Select Tenant drop-down and then click the Add icon ( + ) that appears on the right. Enter a unique name for the tenant service group (TSG) and choose a business vertical.Select Region: When activating an Device Security subscription that doesn’t require a Strata Logging Service, select the region where the logging service will ingest network traffic logs that the VM-Series send it for Device Security to access and analyze.When activating an Device Security subscription that does require a Strata Logging Service, you must first already have an activated Strata Logging Service instance in the same tenant service group (TSG). Device Security will then use this instance by default. The TSG might already have another product with an activated Strata Logging Service (PA+CDL or AIOps+CDL for example), or you might have migrated an activated standalone to the TSG before activating the Device Security subscription. In either case, the region will be automatically populated based on the region of the existing data lake in the TSG.Select Deployment Profile(s): Select the deployment profile you previously created.There are two sections for deployment profiles: Available and Unavailable. Deployment profiles appear in the Unavailable section if a required component is missing. For example, if the Device Security subscription in the deployment profile requires a Strata Logging Service but the tenant service group (TSG) doesn’t have one, the deployment profile will be in the Unavailable section. You will need to activate the required before attempting to activate Device Security in such scenarios.When you create multiple deployment profiles, it's possible that they have different Device Security subscriptions. When using them in the same IoT tenant, the Device Security subscription type in the first deployment profile takes precedence over others added afterward.Configure Subscription URL(s): Enter a unique subdomain to complete the <subdomain>.iot.paloaltonetworks.com URL for your Device Security application. This will be the URL where you log in to the Device Security portal.
![]()
- Agree to the Terms and Conditions and then Activate.The hub displays the Tenant Management page where you can see the Device Security initialization status for the TSG. The initialization generally takes a few minutes to complete.
Associate firewalls through the deployment profile with the Device Security subscription in the TSG.- Register a VM-Series using one of the two methods described in Register the VM-Series (Software NGFW Credits) and then Submit the registration.When registering a VM-Series that cannot access the CSP, you must enter a UUID, a CPU ID, the number of vCPUs on the firewall, and the amount memory allocated to the firewall. This information is in the General Information section on the Dashboard page of the web interface on your firewall. You can copy it from there and paste it in the Register Firewall form. You can also download this information from the firewall web interface to a text file by selecting DeviceLicensesActivate Feature using Auth CodeDownload Authorization File. Then on the Register Firewall page in the CSP, Upload a File for UUID & CPUID.After you submit the firewall registration, the CSP associates this firewall through the deployment profile with the TSG. It typically takes a few minutes for the registration and association to complete. When completed, you can see the firewall on the Common ServicesDevice Associations tab in the hub.During the firewall registration, the number of Software NGFW credits needed to fund the virtual firewall are automatically deducted from your pool of credits.
- Associate more firewalls to the TSG through the same deployment profile or, if they are different types of firewall models, through other deployment profiles you have created for them.It’s not currently possible to extend, renew, or offboard Device Security licenses that have been activated on VM-Series funded by Software NGFW credits. In addition, Enterprise License Agreements (ELA) and Device Security FedRAMP Moderate licenses are not supported.
Configure the VM-Series to provide network traffic logs with Device Security.Now that you’ve onboarded Device Security onto your VM-Series, follow the steps in Prepare Your Firewall for Device Security to configure it to log network traffic and forward the traffic logs to the logging service, which then streams network traffic metadata to Device Security for analysis.