Device Security
Quarantine a Device Using Forescout
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Quarantine a Device Using Forescout
Use Device Security integration with Forescout to quarantine devices of concern.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
Through the Device Security integration with Forescout, you can send a request
to Forescout to quarantine devices or to remove devices from quarantine.
Strata Cloud Manager
Use Device Security integration with Forescout to quarantine devices of concern
from Device Security in Strata Cloud Manager.
Put a Device in Quarantine Using Forescout
Put a Device in Quarantine Using Forescout
If you want to quarantine a device because you saw an alert that concerns you,
use the quarantine option on
the AlertsSecurity Alerts page. You can also do this in the
Action menu in the Alerts section on a Device Details page.
Putting a device in quarantine requires Device Security owner or
administrator privileges.
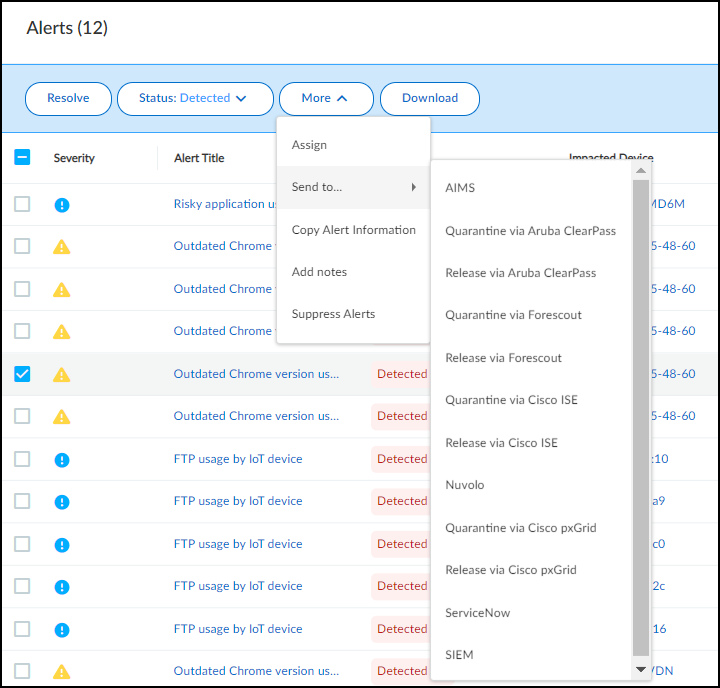
- Select an alert on AlertsSecurity Alerts in Device Security in Strata Cloud Manager.Click MoreSend toQuarantine via Forescout.
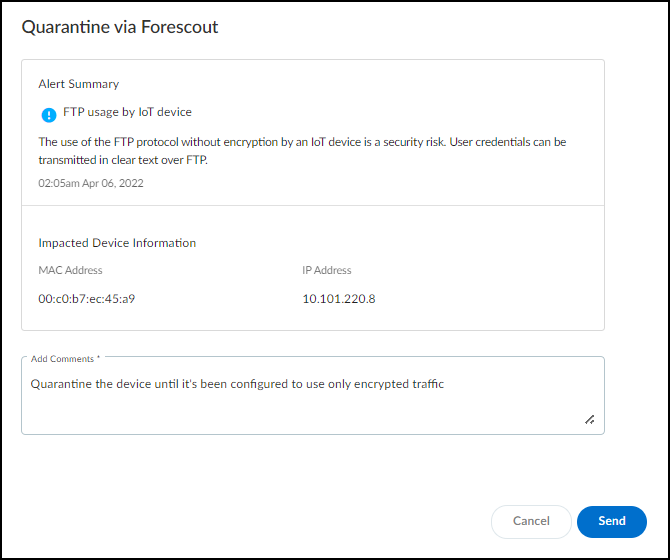
![]() Add a comment.After you enter a comment, the Send button changes from gray to blue, indicating that you can proceed.
Add a comment.After you enter a comment, the Send button changes from gray to blue, indicating that you can proceed.![]() Click Send.Device Security sets the PanwIoTQuarantine host property to on and the XSOAR engine sends it to all configured Forescout instances using the Forescout API:https://<Forescout_IP_address>/fsapi/niCore/HostsThe instance or instances that have an endpoint with a matching MAC address then take action based on how Forescout administrators choose to use the host property. For example, they might configure Forescout to send a Disconnect-Request message to the switch through which the impacted device accesses the network and disconnects it. When the device reconnects, Forescout assigns the device to a quarantine VLAN where it remains in quarantine while you investigate the cause of the alert. Once it’s resolved, you can then use the Release via Forescout option.After you click Send, a link appears. When you click it, a new browser window opens to the XSOAR playbook for this action.
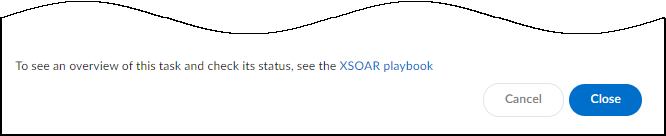
Click Send.Device Security sets the PanwIoTQuarantine host property to on and the XSOAR engine sends it to all configured Forescout instances using the Forescout API:https://<Forescout_IP_address>/fsapi/niCore/HostsThe instance or instances that have an endpoint with a matching MAC address then take action based on how Forescout administrators choose to use the host property. For example, they might configure Forescout to send a Disconnect-Request message to the switch through which the impacted device accesses the network and disconnects it. When the device reconnects, Forescout assigns the device to a quarantine VLAN where it remains in quarantine while you investigate the cause of the alert. Once it’s resolved, you can then use the Release via Forescout option.After you click Send, a link appears. When you click it, a new browser window opens to the XSOAR playbook for this action.![]() To confirm that the command was sent, click the link to the XSOAR playbook for this action.For the link in Device Security to open the corresponding playbook in Cortex XSOAR, you must already be logged in to your XSOAR instance before clicking it.The green boxes in the playbook indicate that a particular step was successfully performed. Following the path through the playbook gives you feedback about whether an action was carried out successfully or, if not, where the process changed course.
To confirm that the command was sent, click the link to the XSOAR playbook for this action.For the link in Device Security to open the corresponding playbook in Cortex XSOAR, you must already be logged in to your XSOAR instance before clicking it.The green boxes in the playbook indicate that a particular step was successfully performed. Following the path through the playbook gives you feedback about whether an action was carried out successfully or, if not, where the process changed course.Release a Device from Quarantine Using Forescout
Release a Device from Quarantine Using ForescoutReleasing a device from quarantine is the same procedure as putting it in quarantine except that you click MoreSend toRelease via Forescout on the AlertsSecurity Alerts page. This option is also available in the Action menu in the Alerts section on a Device Details page.Releasing a device from quarantine requires Device Security owner or administrator privileges.![]() The XSOAR engine sends Forescout the PanwIoTQuarantine host property with the value set to off (PanwIoTQuarantine=off) using the Forescout API:https://<Forescout_IP_address>/fsapi/niCore/HostsThe instance or instances that have an endpoint with a matching MAC address take action based on how Forescout administrators choose to use the host property. For example, if the Forescout administrators use this host property to disconnect an impacted device and reassign its VLAN, then Forescout would send another Disconnect-Request message to the switch through which the device connects to the network. This time when the device reconnects and requests network access, Forescout accepts the device back onto the network and puts it in its normally assigned VLAN.
The XSOAR engine sends Forescout the PanwIoTQuarantine host property with the value set to off (PanwIoTQuarantine=off) using the Forescout API:https://<Forescout_IP_address>/fsapi/niCore/HostsThe instance or instances that have an endpoint with a matching MAC address take action based on how Forescout administrators choose to use the host property. For example, if the Forescout administrators use this host property to disconnect an impacted device and reassign its VLAN, then Forescout would send another Disconnect-Request message to the switch through which the device connects to the network. This time when the device reconnects and requests network access, Forescout accepts the device back onto the network and puts it in its normally assigned VLAN.
Legacy IoT Security
Use Device Security integration with Forescout to quarantine devices of concern
from the Device Security portal.
Put a Device in Quarantine Using Forescout
Put a Device in Quarantine Using Forescout
If you want to quarantine a device because you saw an alert that concerns you,
use the quarantine option on
the AlertsSecurity AlertsAll Alerts page. You can also do this in the
Action menu in the Alerts section on a Device Details page.
Putting a device in quarantine requires Device Security owner or
administrator privileges.
- Select an alert on AlertsSecurity AlertsAll Alerts in the Device Security portal.Click MoreSend toQuarantine via Forescout.
![]() Add a comment.After you enter a comment, the Send button changes from gray to blue, indicating that you can proceed.
Add a comment.After you enter a comment, the Send button changes from gray to blue, indicating that you can proceed.![]() Click Send.Device Security sets the PanwIoTQuarantine host property to on and the XSOAR engine sends it to all configured Forescout instances using the Forescout API:https://<Forescout_IP_address>/fsapi/niCore/HostsThe instance or instances that have an endpoint with a matching MAC address then take action based on how Forescout administrators choose to use the host property. For example, they might configure Forescout to send a Disconnect-Request message to the switch through which the impacted device accesses the network and disconnects it. When the device reconnects, Forescout assigns the device to a quarantine VLAN where it remains in quarantine while you investigate the cause of the alert. Once it’s resolved, you can then use the Release via Forescout option.After you click Send, a link appears. When you click it, a new browser window opens to the XSOAR playbook for this action.
Click Send.Device Security sets the PanwIoTQuarantine host property to on and the XSOAR engine sends it to all configured Forescout instances using the Forescout API:https://<Forescout_IP_address>/fsapi/niCore/HostsThe instance or instances that have an endpoint with a matching MAC address then take action based on how Forescout administrators choose to use the host property. For example, they might configure Forescout to send a Disconnect-Request message to the switch through which the impacted device accesses the network and disconnects it. When the device reconnects, Forescout assigns the device to a quarantine VLAN where it remains in quarantine while you investigate the cause of the alert. Once it’s resolved, you can then use the Release via Forescout option.After you click Send, a link appears. When you click it, a new browser window opens to the XSOAR playbook for this action.![]() To confirm that the command was sent, click the link to the XSOAR playbook for this action.For the link in Device Security to open the corresponding playbook in Cortex XSOAR, you must already be logged in to your XSOAR instance before clicking it.The green boxes in the playbook indicate that a particular step was successfully performed. Following the path through the playbook gives you feedback about whether an action was carried out successfully or, if not, where the process changed course.
To confirm that the command was sent, click the link to the XSOAR playbook for this action.For the link in Device Security to open the corresponding playbook in Cortex XSOAR, you must already be logged in to your XSOAR instance before clicking it.The green boxes in the playbook indicate that a particular step was successfully performed. Following the path through the playbook gives you feedback about whether an action was carried out successfully or, if not, where the process changed course.Release a Device from Quarantine Using Forescout
Release a Device from Quarantine Using ForescoutReleasing a device from quarantine is the same procedure as putting it in quarantine except that you click MoreSend toRelease via Forescout on the AlertsSecurity AlertsAll Alerts page. This option is also available in the Action menu in the Alerts section on a Device Details page.Releasing a device from quarantine requires Device Security owner or administrator privileges.![]() The XSOAR engine sends Forescout the PanwIoTQuarantine host property with the value set to off (PanwIoTQuarantine=off) using the Forescout API:https://<Forescout_IP_address>/fsapi/niCore/HostsThe instance or instances that have an endpoint with a matching MAC address take action based on how Forescout administrators choose to use the host property. For example, if the Forescout administrators use this host property to disconnect an impacted device and reassign its VLAN, then Forescout would send another Disconnect-Request message to the switch through which the device connects to the network. This time when the device reconnects and requests network access, Forescout accepts the device back onto the network and puts it in its normally assigned VLAN.
The XSOAR engine sends Forescout the PanwIoTQuarantine host property with the value set to off (PanwIoTQuarantine=off) using the Forescout API:https://<Forescout_IP_address>/fsapi/niCore/HostsThe instance or instances that have an endpoint with a matching MAC address take action based on how Forescout administrators choose to use the host property. For example, if the Forescout administrators use this host property to disconnect an impacted device and reassign its VLAN, then Forescout would send another Disconnect-Request message to the switch through which the device connects to the network. This time when the device reconnects and requests network access, Forescout accepts the device back onto the network and puts it in its normally assigned VLAN.