Upgrade an HA Firewall Pair
Table of Contents
11.1 & Later
Expand all | Collapse all
-
-
- Upgrade Panorama with an Internet Connection
- Upgrade Panorama Without an Internet Connection
- Install Content Updates Automatically for Panorama without an Internet Connection
- Upgrade Panorama in an HA Configuration
- Migrate Panorama Logs to the New Log Format
- Upgrade Panorama for Increased Device Management Capacity
- Upgrade Panorama and Managed Devices in FIPS-CC Mode
- Downgrade from Panorama 11.1
- Troubleshoot Your Panorama Upgrade
-
- What Updates Can Panorama Push to Other Devices?
- Schedule a Content Update Using Panorama
- Panorama, Log Collector, Firewall, and WildFire Version Compatibility
- Upgrade Log Collectors When Panorama Is Internet-Connected
- Upgrade Log Collectors When Panorama Is Not Internet-Connected
- Upgrade a WildFire Cluster from Panorama with an Internet Connection
- Upgrade a WildFire Cluster from Panorama without an Internet Connection
- Upgrade Firewalls When Panorama Is Internet-Connected
- Upgrade Firewalls When Panorama Is Not Internet-Connected
- Upgrade a ZTP Firewall
- Revert Content Updates from Panorama
-
Upgrade an HA Firewall Pair
Follow these steps to upgrade an HA firewall pair to PAN-OS 11.1 or
later.
Use the following steps to upgrade a pair of firewalls in a high availability (HA)
configuration. This procedure applies to both active/passive and active/active
configurations.
You can upgrade an HA firewall
pair using either the manual upgrade process or the orchestrated upgrade process.
Manual Upgrade
To avoid downtime when upgrading firewalls that are in a high availability (HA)
configuration, update one HA peer at a time: For active/active firewalls, it doesn’t
matter which peer you upgrade first (though for simplicity, this procedure shows you
how to upgrade the active-primary peer first). For active/passive firewalls, you
must suspend (fail over) and upgrade the active (primary) peer first. After you
upgrade the primary peer, you must unsuspend the primary peer to return it to a
functional state (passive). Next, you must suspend the passive (secondary) peer to
make the primary peer active again. After the primary peer is active and the
secondary peer is suspended, you can continue the upgrade. To prevent failover
during the upgrade of the HA peers, you must make sure preemption is disabled before
proceeding with the upgrade. You only need to disable preemption on one peer in the
pair.
When upgrading HA firewalls from PAN-OS 9.1 and earlier, you must upgrade each HA
peer to PAN-OS 10.1 before upgrading to the target release. When HA peers are two or
more feature releases apart, the firewall with the older release installed enters a
suspended state with the message Peer
version too old.
To avoid impacting traffic, plan to upgrade within the outage window. Ensure the
firewalls are connected to a reliable power source. A loss of power during an
upgrade can make firewalls unusable.
Orchestrated
Upgrade
(PAN-OS 12.1.2
and later releases) With upgrade orchestration, you can simplify and
automate the process of upgrading HA firewall pairs (running PAN-OS 10.2.x or a
later release). Upgrade orchestration orchestrates the workflow by eliminating most
of the manual steps that you need to execute on each device. The system follows a
careful and automated sequence:
- Upgrades the passive (or active-secondary) peer first.
- Automatically reboots the passive peer.
- After the first passive peer is back online and the HA status is synchronized, the system initiates HA failover and upgrades the other peer.
The feature
automatically performs pre-checks to validate that your environment is ready for the
upgrade. It verifies that both firewalls are connected to Panorama, confirms
configuration synchronization, and validates that the HA links are operational.
After these checks pass, the upgrade process begins automatically. After upgrade,
the system automatically performs the necessary reboots without your
intervention.
Before initiating HA Upgrade
Orchestration, you must ensure that the following prerequisites are met:
- Both HA firewalls are connected to Panorama.
- The configuration is synchronized between the active and passive firewalls.
- The base PAN-OS version is downloaded on all HA firewalls. Multi-download versions from Panorama are not supported.
- New upgrade jobs are restricted if another HA orchestration job is currently running.
In the event of an
orchestrated upgrade failure, you must perform a manual upgrade on the failed
firewall.
For PAN-OS 12.1.2, you must create an
admin user with the Panorama Admin role to run this feature. This requirement is
no longer needed in the later releases.
Manual Upgrade
- Save a backup of the current configuration file.Although the firewall automatically creates a backup of the configuration, it is a best practice to create and externally store a backup before you upgrade.Perform these steps on each firewall in the pair:
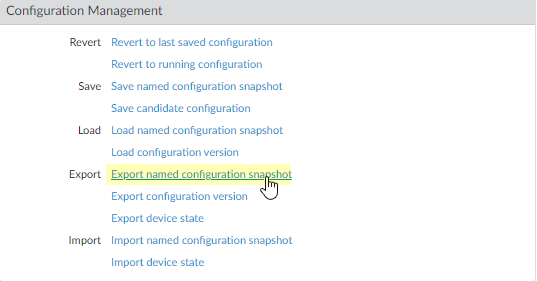
- Select DeviceSetupOperations and click Export named configuration snapshot.
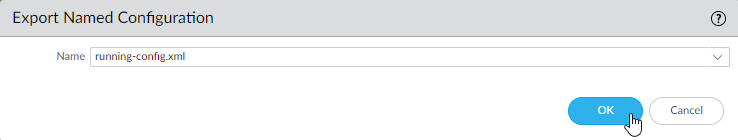
![]() Select the XML file that contains your running configuration (for example, running-config.xml) and click OK to export the configuration file.
Select the XML file that contains your running configuration (for example, running-config.xml) and click OK to export the configuration file.![]() Save the exported file to a location external to the firewall. You can use this backup to restore the configuration if you have problems with the upgrade.Select DeviceSupport and Generate Tech Support File.Click Yes when prompted to generate the tech support file.Ensure that each firewall in the HA pair is running the latest content release version.Refer to the Release Notes for the minimum content release version you must install for a PAN-OS 11.1 release. Make sure to follow the Best Practices for Applications and Threats Content Updates.
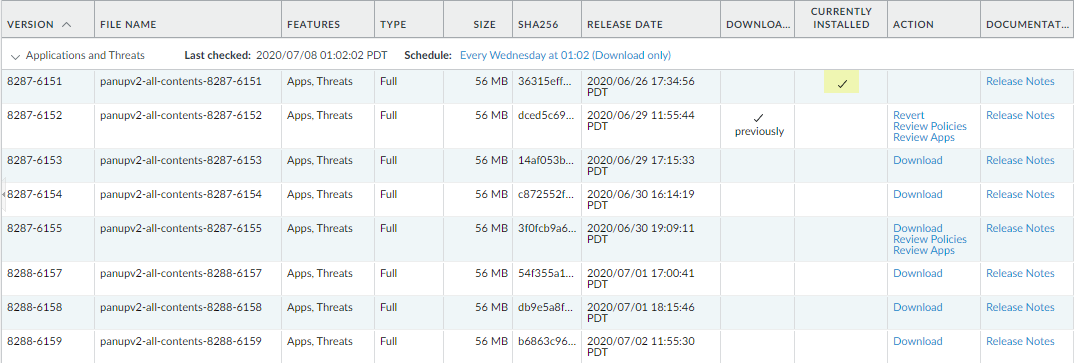
Save the exported file to a location external to the firewall. You can use this backup to restore the configuration if you have problems with the upgrade.Select DeviceSupport and Generate Tech Support File.Click Yes when prompted to generate the tech support file.Ensure that each firewall in the HA pair is running the latest content release version.Refer to the Release Notes for the minimum content release version you must install for a PAN-OS 11.1 release. Make sure to follow the Best Practices for Applications and Threats Content Updates.- Select DeviceDynamic Updates and check which Applications or Applications and Threats to determine which update is Currently Installed.
![]() If the firewalls are not running the minimum required content release version or a later version required for PAN-OS 11.1, Check Now to retrieve a list of available updates.Locate and Download the desired content release version.After you successfully download a content update file, the link in the Action column changes from Download to Install for that content release version.Install the update. You must install the update on both peers.Determine the Upgrade Path to PAN-OS 11.1 and later releasesReview PAN-OS Upgrade Checklist, the known issues and changes to default behavior in the Release Notes and Upgrade/Downgrade Considerations for each release through which you pass as part of your upgrade path.(Best Practices) If you are leveraging Strata Logging Service, install the device certificate on each HA peer.The firewall automatically switches to using the device certificate for authentication with Strata Logging Service ingestion and query endpoints on upgrade to PAN-OS 11.1.If you do not install the device certificate prior to upgrade to PAN-OS 11.1, the firewall continues to use the existing logging service certificates for authentication.Disable preemption on the first peer in each pair. You only need to disable this setting on one firewall in the HA pair but ensure that the commit is successful before you proceed with the upgrade.
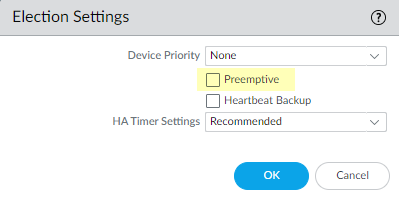
If the firewalls are not running the minimum required content release version or a later version required for PAN-OS 11.1, Check Now to retrieve a list of available updates.Locate and Download the desired content release version.After you successfully download a content update file, the link in the Action column changes from Download to Install for that content release version.Install the update. You must install the update on both peers.Determine the Upgrade Path to PAN-OS 11.1 and later releasesReview PAN-OS Upgrade Checklist, the known issues and changes to default behavior in the Release Notes and Upgrade/Downgrade Considerations for each release through which you pass as part of your upgrade path.(Best Practices) If you are leveraging Strata Logging Service, install the device certificate on each HA peer.The firewall automatically switches to using the device certificate for authentication with Strata Logging Service ingestion and query endpoints on upgrade to PAN-OS 11.1.If you do not install the device certificate prior to upgrade to PAN-OS 11.1, the firewall continues to use the existing logging service certificates for authentication.Disable preemption on the first peer in each pair. You only need to disable this setting on one firewall in the HA pair but ensure that the commit is successful before you proceed with the upgrade.- Select DeviceHigh Availability and edit the Election Settings.If enabled, disable (clear) the Preemptive setting and click OK.
![]() Commit the change.Suspend the primary HA peer to force a failover.(Active/passive firewalls) For firewalls in an active/passive HA configuration, suspend and upgrade the active HA peer first.(Active/active firewalls) For firewalls in an active/active HA configuration, suspend and upgrade the active-primary HA peer first.
Commit the change.Suspend the primary HA peer to force a failover.(Active/passive firewalls) For firewalls in an active/passive HA configuration, suspend and upgrade the active HA peer first.(Active/active firewalls) For firewalls in an active/active HA configuration, suspend and upgrade the active-primary HA peer first.- Select DeviceHigh AvailabilityOperational Commands and Suspend local device for high availability.In the bottom-right corner, verify that the state is suspended.The resulting failover should cause the secondary HA peer to transition to active state.The resulting failover verifies that HA failover is functioning properly before you upgrade.Install PAN-OS 11.1 on the suspended HA peer.
- On the primary HA peer, select DeviceSoftware and click Check Now for the latest updates.Only the versions for the next available PAN-OS release are displayed. For example, if the PAN-OS 11.1 is installed on the firewall, then only PAN-OS 11.1 releases are displayed.(PAN-OS 11.1.3 and later releases) By default, the preferred releases and the corresponding base releases are displayed. To view the preferred releases only, disable (clear) the Base Releases checkbox.Locate and Download PAN-OS 11.1.0.If your firewall does not have internet access from the management port, you can download the software image from the Palo Alto Networks Support Portal and then manually Upload it to your firewall.If your firewall does have internet access and you encounter a file download error, click Check Now again to refresh the list of PAN-OS images.After you download the image (or, for a manual upgrade, after you upload the image), Install the image.
![]() After the installation completes successfully, reboot using one of the following methods:
After the installation completes successfully, reboot using one of the following methods:- If you are prompted to reboot, click Yes.
- If you are not prompted to reboot, select DeviceSetupOperations and Reboot Device.
After the device finishes rebooting, view the High Availability widget on the Dashboard and verify that the device you just upgraded is in sync with the peer.![]() Restore HA functionality to the primary HA peer.
Restore HA functionality to the primary HA peer.- Select DeviceHigh AvailabilityOperational Commands and Make local device functional for high availability.In the bottom-right corner, verify that the state is Passive. For firewalls in an active/active configuration, verify that the state is Active.Wait for the HA peer running configuration to synchronize.In the Dashboard, monitor the Running Config status in the High Availability widget.On the secondary HA peer, suspend the HA peer.
- Select DeviceHigh AvailabilityOperational Commands and Suspend local device for high availability.In the bottom-right corner, verify that the state is suspended.The resulting failover should cause the primary HA peer to transition to Active state.Install PAN-OS 11.1 on the secondary HA peer.
- On the secondary peer, select DeviceSoftware and click Check Now for the latest updates.Locate and Download PAN-OS 11.1.0.After you download the image, Install it.After the installation completes successfully, reboot using one of the following methods:
- If you are prompted to reboot, click Yes.
- If you are not prompted to reboot, select DeviceSetupOperations and Reboot Device.
Restore HA functionality to the secondary HA peer.- Select DeviceHigh AvailabilityOperational Commands and Make local device functional for high availability.In the bottom-right corner, verify that the state is Passive. For firewalls in an active/active configuration, verify that the state is Active.Wait for the HA peer running configuration to synchronize.In the Dasbhoard, monitor the Running Config status High Availability widget.Re-enable preemption on the HA peer where it was disabled in the previous step.
- Select DeviceHigh Availability and edit the Election Settings.Enable (check) the Preemptive setting and click OK.Commit the change.Regenerate or re-import all certificates to adhere to OpenSSL Security Level 2.On upgrade to PAN-OS 11.1, it is required that all certificates meet the following minimum requirements:
- RSA 2048 bits or greater, or ECDSA 256 bits or greater
- Digest of SHA256 or greater
See the PAN-OS Administrator's Guide or Panorama Administrator's Guide for more information on regenerating or re-importing your certificates.Verify that both peers are passing traffic as expected.In an active/passive configuration, only the active peer should be passing traffic; both peers should be passing traffic in an active/active configuration.Run the following CLI commands to confirm that the upgrade succeeded:- (Active peers only) To verify that active peers are passing traffic, run the show session all command.
- To verify session synchronization, run the
show high-availability interface ha2
command and make sure that the Hardware Interface counters on the CPU
table are increasing as follows:
- In an active/passive configuration, only the active peer shows packets transmitted; the passive peer will show only packets received.If you enabled HA2 keep-alive, the hardware interface counters on the passive peer will show both transmit and receive packets. This occurs because HA2 keep-alive is bi-directional, which means that both peers transmit HA2 keep-alive packets.
- In an active/active configuration, you will see packets received and packets transmitted on both peers.
Orchestrated Upgrade
- (Best Practice) Save a backup of the current configuration file.Although the firewall automatically creates a backup of the configuration, it is a best practice to create and externally store a backup before you upgrade.Perform these steps on each firewall in the pair:
- Select DeviceSetupOperations and click Export named configuration snapshot.
![]() Select the XML file that contains your running configuration (for example, running-config.xml) and click OK to export the configuration file.
Select the XML file that contains your running configuration (for example, running-config.xml) and click OK to export the configuration file.![]() Save the exported file to a location external to the firewall. You can use this backup to restore the configuration if you have problems with the upgrade.(Best Practice) Select DeviceSupport and Generate Tech Support File.Click Yes when prompted to generate the tech support file.(Best Practice) Determine the Upgrade Path to PAN-OS 11.1 and later releasesReview PAN-OS Upgrade Checklist, the known issues and changes to default behavior in the Release Notes and Upgrade/Downgrade Considerations for each release through which you pass as part of your upgrade path.(Best Practices) If you are leveraging Strata Logging Service, install the device certificate on each HA peer.The firewall automatically switches to using the device certificate for authentication with Strata Logging Service ingestion and query endpoints on upgrade to PAN-OS 11.1 or later.If you do not install the device certificate prior to upgrade to PAN-OS 11.1 or later, the firewall continues to use the existing logging service certificates for authentication.Download images to firewalls.
Save the exported file to a location external to the firewall. You can use this backup to restore the configuration if you have problems with the upgrade.(Best Practice) Select DeviceSupport and Generate Tech Support File.Click Yes when prompted to generate the tech support file.(Best Practice) Determine the Upgrade Path to PAN-OS 11.1 and later releasesReview PAN-OS Upgrade Checklist, the known issues and changes to default behavior in the Release Notes and Upgrade/Downgrade Considerations for each release through which you pass as part of your upgrade path.(Best Practices) If you are leveraging Strata Logging Service, install the device certificate on each HA peer.The firewall automatically switches to using the device certificate for authentication with Strata Logging Service ingestion and query endpoints on upgrade to PAN-OS 11.1 or later.If you do not install the device certificate prior to upgrade to PAN-OS 11.1 or later, the firewall continues to use the existing logging service certificates for authentication.Download images to firewalls.- Select PanoramaSoftwareDevice DeploymentActionValidate to view the dependencies.
- Download the intermediate and base software images and the required dynamic content.
(Best Practices) Disable preemption on the first peer in each pair. You only need to disable this setting on one firewall in the HA pair but ensure that the commit is successful before you proceed with the upgrade.- Select DeviceHigh Availability and edit the Election Settings.If enabled, disable (clear) the Preemptive setting and click OK.
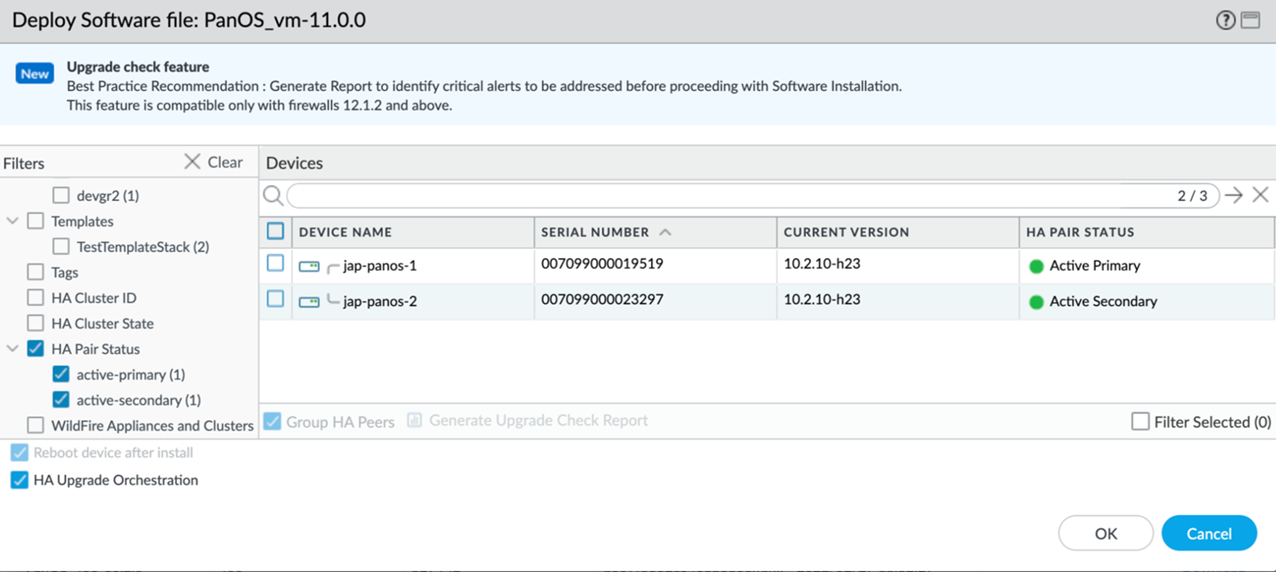
![]() Commit the change.(PAN-OS 12.1.2 and later releases) Initiate orchestrated upgrade on an HA firewall pair running PAN-OS 10.2.x or a later release.Before initiating the upgrade, select HA Pair Status to filter for firewalls in a high-availability configuration. This ensures that you are targeting the correct devices for the upgrade.When you select HA Upgrade Orchestration, the system automatically enables Group HA Peers and Reboot device after install. This ensures both firewalls are managed as a single entity and all necessary reboots are handled automatically.
Commit the change.(PAN-OS 12.1.2 and later releases) Initiate orchestrated upgrade on an HA firewall pair running PAN-OS 10.2.x or a later release.Before initiating the upgrade, select HA Pair Status to filter for firewalls in a high-availability configuration. This ensures that you are targeting the correct devices for the upgrade.When you select HA Upgrade Orchestration, the system automatically enables Group HA Peers and Reboot device after install. This ensures both firewalls are managed as a single entity and all necessary reboots are handled automatically.- Select HA Upgrade Orchestration.Select the firewall HA pairs that you want to upgrade, and click OK.
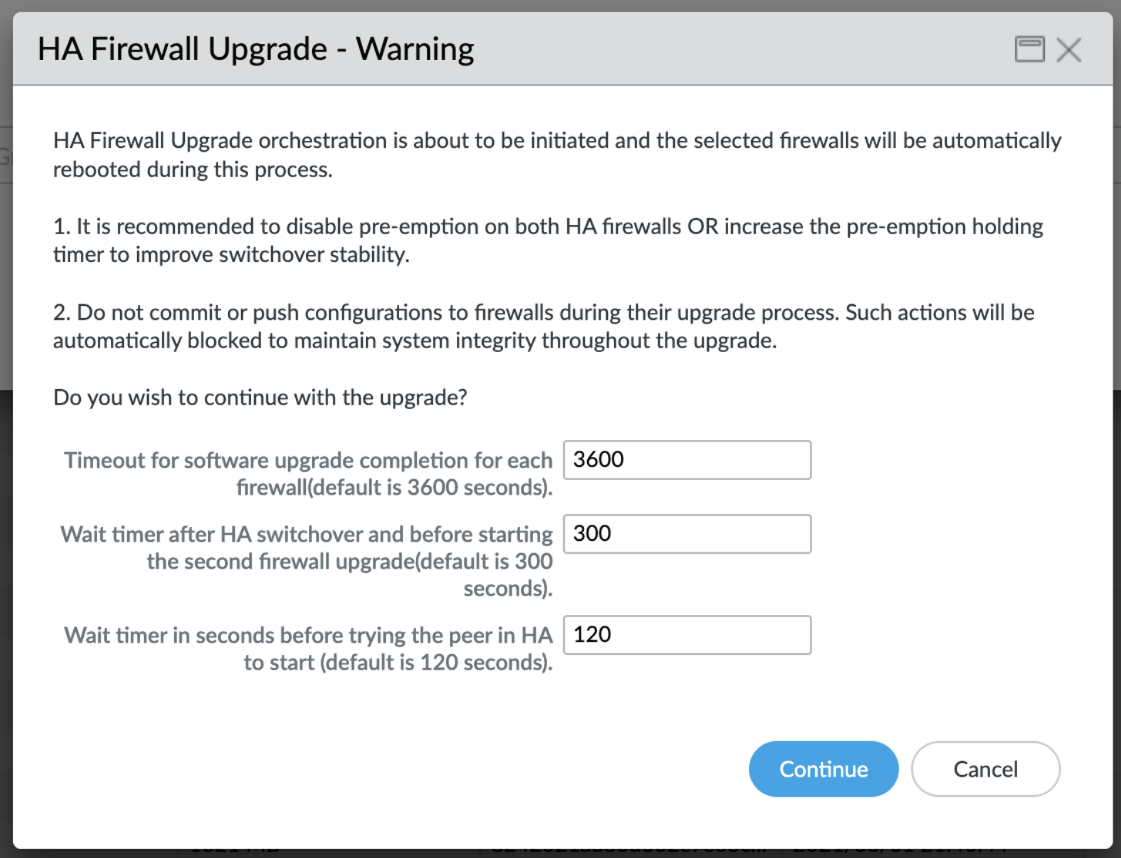
![]() A set of recommendations appear.Before you continue, review the provided recommendations and best practices. Additionally, you can adjust the following timers as required:
A set of recommendations appear.Before you continue, review the provided recommendations and best practices. Additionally, you can adjust the following timers as required:- Specify the maximum time within which a single firewall has to complete the software upgrade. Default is 3600 seconds.
- Specify the wait time after the HA switchover and before initiating the upgrade on the second firewall. Default is 300 seconds.
- Specify the time to wait before the system attempts to start the second firewall in the HA pair. The default is 120 seconds.
![]() Click Continue to start the orchestrated upgrade.In the Install Software dialog, click View Details to view the status of the upgrade.After the upgrade completes, re-enable preemption on the HA peer where it was disabled.
Click Continue to start the orchestrated upgrade.In the Install Software dialog, click View Details to view the status of the upgrade.After the upgrade completes, re-enable preemption on the HA peer where it was disabled.- Select DeviceHigh Availability and edit the Election Settings.Enable (check) the Preemptive setting and click OK.Commit the change.Regenerate or re-import all certificates to adhere to OpenSSL Security Level 2.On upgrade to PAN-OS 12.1.2, it is required that all certificates meet the following minimum requirements:
- RSA 2048 bits or greater, or ECDSA 256 bits or greater
- Digest of SHA256 or greater
See the PAN-OS Administrator's Guide or Panorama Administrator's Guide for more information on regenerating or re-importing your certificates.(Best Practices) Verify that both peers are passing traffic as expected.In an active/passive configuration, only the active peer should be passing traffic; both peers should be passing traffic in an active/active configuration.Run the following CLI commands to confirm that the upgrade succeeded:- (Active peers only) To verify that active peers are passing traffic, run the show session all command.
- To verify session synchronization, run the
show high-availability interface ha2
command and make sure that the Interface counters on the CPU table are
increasing as follows:
- In an active/passive configuration, only the active peer shows packets transmitted; the passive peer will show only packets received.If you enabled HA2 keep-alive, the interface counters on the passive peer will show both transmit and receive packets. This occurs because HA2 keep-alive is bi-directional, which means that both peers transmit HA2 keep-alive packets.
- In an active/active configuration, you will see packets received and packets transmitted on both peers.