Prisma Access
Redistribute HIP Information with Prisma Access
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Redistribute HIP Information with Prisma Access
Configure Prisma Access to redistribute HIP reports within
your enterprise.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To ensure consistent Host Information Profile (HIP) policy enforcement and to simplify policy
management, you can redistribute HIP information received from
mobile users and users at remote networks that use the GlobalProtect app from Prisma
Access to other gateways, firewalls, and Panorama appliances in your enterprise,
including the Panorama that manages Prisma Access.
The following section describes some common Prisma Access deployments where HIP
redistribution is useful for consistent policy enforcement and HIP report
viewing:
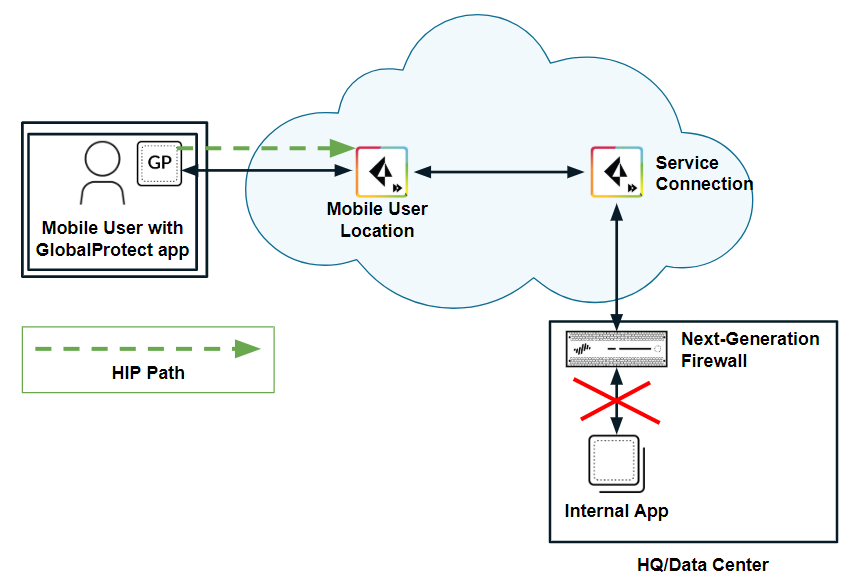
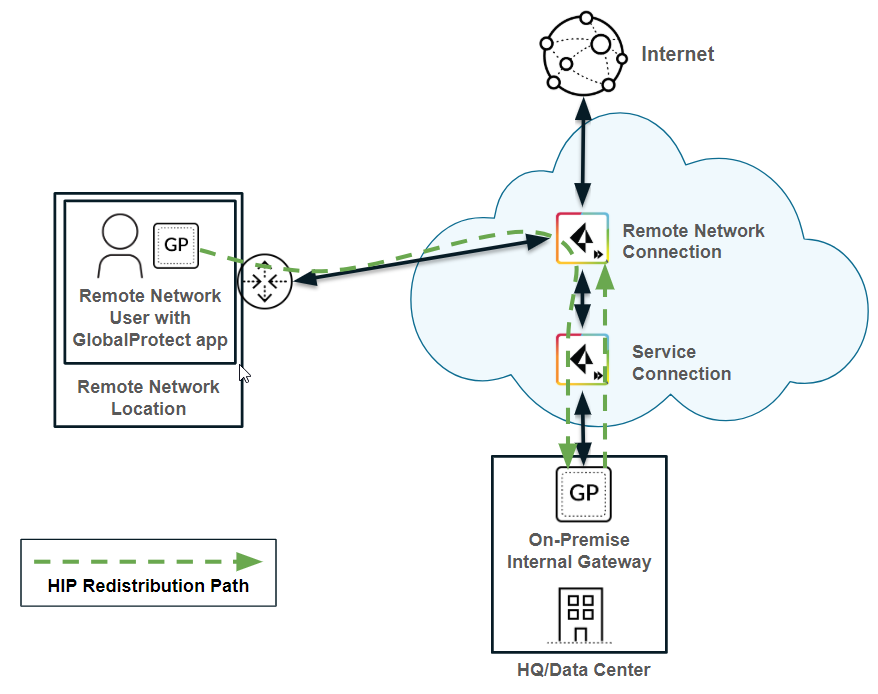
- HIP redistribution from Prisma Access to a next-generation firewall—If you have a next-generation firewall in your organization’s data center or headquarters location, and have configured that firewall with HIP-based security policies, you cannot enforce those policies for Prisma Access mobile users until you redistribute HIP redistribution from Prisma Access to the firewall.The following figure shows a mobile user whose endpoint is protected with the GlobalProtect app. The user attempts to access an internal app at an HQ/data center whose access is controlled by a next-generation firewall with HIP-based security policies. When the user logs in to the GlobalProtect app, the app collects HIP information and sends it to Prisma Access; however, Prisma Access does not redistribute this information to the on-premises firewall. Since the firewall does not have the user’s HIP information, it blocks the user’s access to the app.
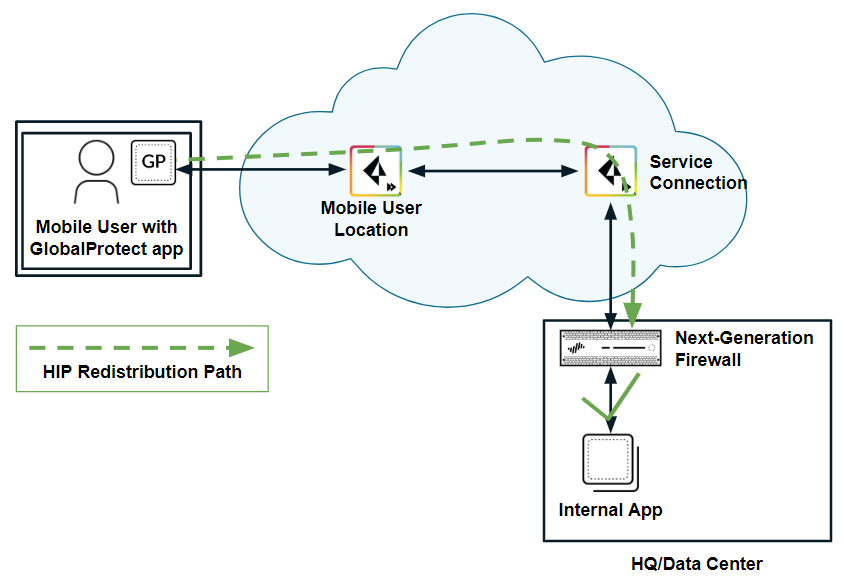
![]() HIP redistribution allows you to distribute the mobile users’ HIP information to the on-premises firewall. The firewall can then check the user’s HIP information against its configured security policies and grant the user access to the app.
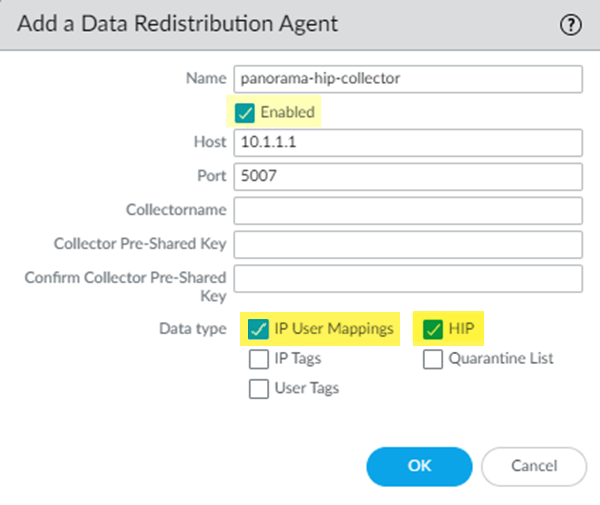
HIP redistribution allows you to distribute the mobile users’ HIP information to the on-premises firewall. The firewall can then check the user’s HIP information against its configured security policies and grant the user access to the app.![]() To redistribute HIP information from Prisma Access to the firewall, you allow Prisma Access to redistribute HIP information, then Add a User-ID Agent (PanoramaUser IdentificationUser-ID Agents for 9.1.x Panorama appliances or PanoramaData Redistribution for Panorama 10.x appliances) on the firewall, and specify the Prisma Access User-ID Agent Address (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address) as the Host (10.1.1.1 in the following example) and 5007 as the Port.
To redistribute HIP information from Prisma Access to the firewall, you allow Prisma Access to redistribute HIP information, then Add a User-ID Agent (PanoramaUser IdentificationUser-ID Agents for 9.1.x Panorama appliances or PanoramaData Redistribution for Panorama 10.x appliances) on the firewall, and specify the Prisma Access User-ID Agent Address (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address) as the Host (10.1.1.1 in the following example) and 5007 as the Port.![]()
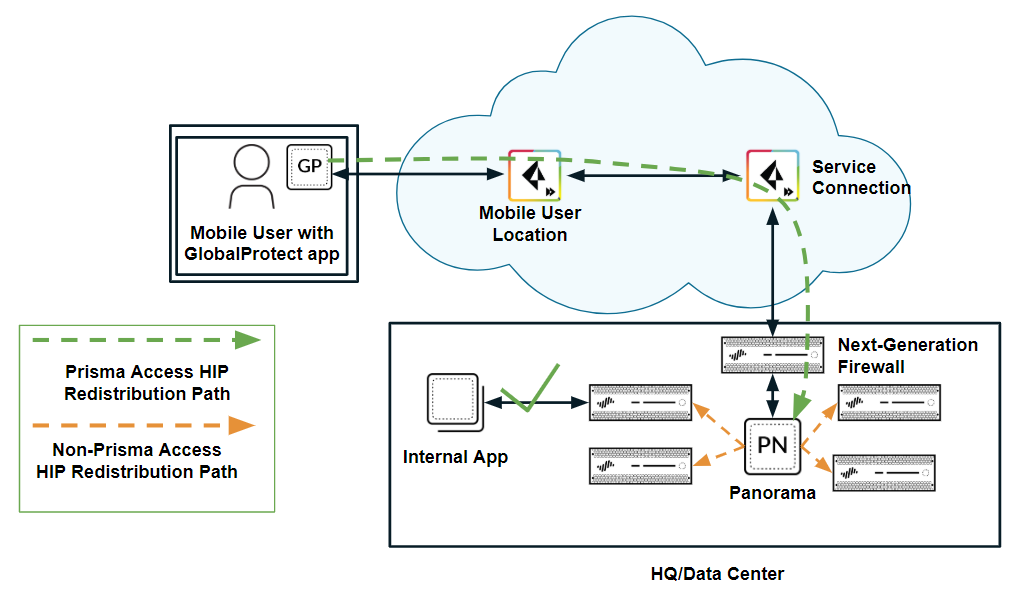
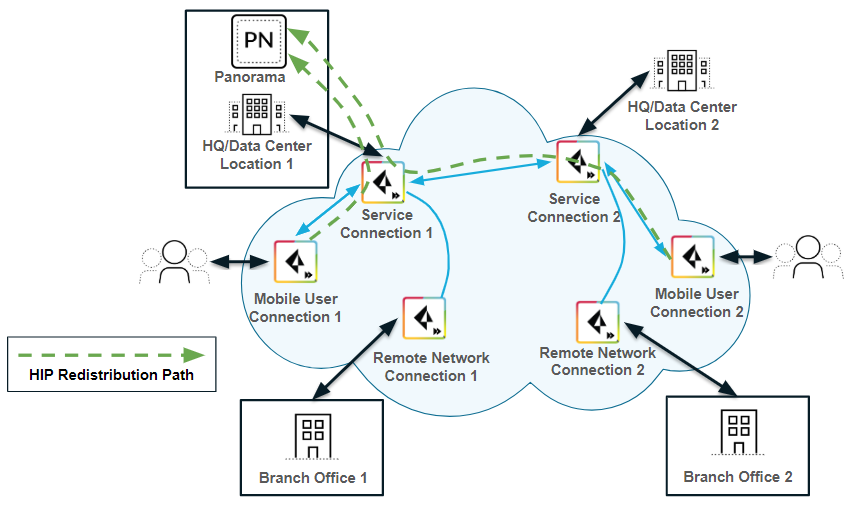
- HIP redistribution from Prisma Access to Panorama—If you have multiple firewalls or gateways in your organization with HIP-based security policies, you can redistribute the HIP information from Prisma Access to the Panorama that manages Prisma Access by creating a User-ID agent in Panorama and specifying the Prisma Access User-ID Agent Address as the User-ID Host. You can then redisribute HIP reports from that Panorama appliance to the other managed Panorama appliances, gateways, firewalls, and virtual systems in your enterprise, using the same workflow that you use to redistribute User-ID information to managed firewalls and enforce consistent policy for internal apps and resources, as shown in the following figure.
![]() Alternatively, you can configure each internal firewall or gateway in your enterprise to directly collect HIP information from Prisma Access, without using Panorama as a central location, by creating a User-ID Agent in each device. Note, however, that Prisma Access uses service connections to send HIP information, and service connection bandwidth consumption might increase if Prisma Access sends a large number of HIP reports.
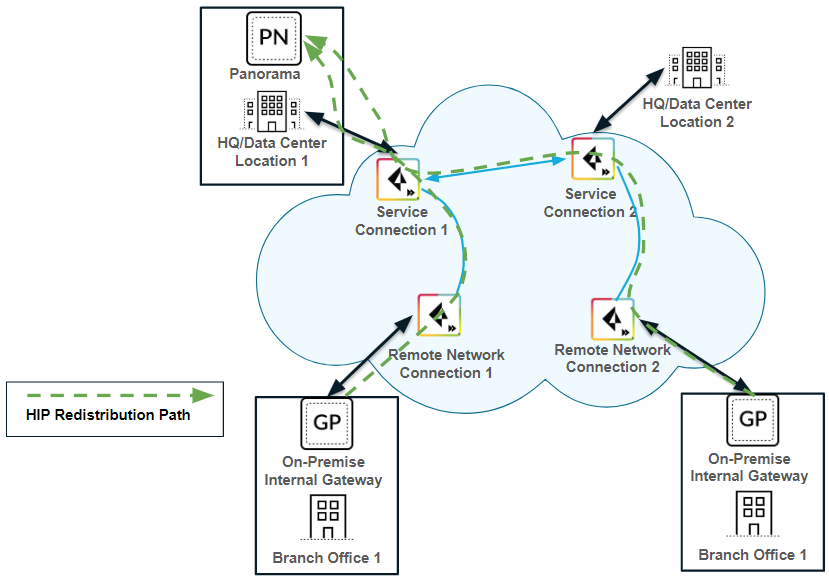
Alternatively, you can configure each internal firewall or gateway in your enterprise to directly collect HIP information from Prisma Access, without using Panorama as a central location, by creating a User-ID Agent in each device. Note, however, that Prisma Access uses service connections to send HIP information, and service connection bandwidth consumption might increase if Prisma Access sends a large number of HIP reports. - HIP redistribution from a user at a remote network to Prisma Access—The previous use cases showed Prisma Access collecting HIP information from mobile users. If you want to apply HIP-based policies in Prisma Access for a user at a remote network location, you need a way to distribute the HIP information from the remote network user’s GlobalProtect app to Prisma Access.The following example shows a user at a remote network location whose internet access is located on the remote network connection. In Prisma Access, you control the user’s internet access at the remote network location with security policies created in the Remote_Network_Device_Group or in a shared device group. To properly enforce the policies at the remote network location for the user, you need to configure Prisma Access to retrieve the user’s HIP information from the internal gateway.In this example, the GlobalProtect gateway at the HQ/data center that is configured as an internal gateway using internal host detection checks the user’s HIP information from the user’s GlobalProtect app. The internal gateway detects that the user is inside the remote network location and collects both User-ID and HIP information from the user.To distribute this HIP information from the internal gateway to Prisma Access, create a User-ID agent in Panorama and specify the IP address of the internal gateway as the host.
![]()
- View detailed HIP logs from Panorama—When mobile users log in using the GlobalProtect app, the app sends the HIP information to Prisma Access. Panorama retrieves the log results from Strata Logging Service to view the results of the HIP Match logs (MonitorLogsHIP Match); however, you cannot view detailed HIP reports until you configure Panorama to redistribute HIP report details from Prisma Access to Panorama.
![]() To redistribute detailed HIP information from mobile users to Panorama, create a User-ID agent in Panorama and specify the User-ID Agent Address (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address) as the User-ID host.If you have configured an on-premises gateway as an internal gateway at a remote user location, you can also send the HIP information for users at remote networks to Panorama by creating a User-ID agent in Panorama and specifying the remote network EBGP Router address (PanoramaCloud ServicesStatusNetwork DetailsRemote NetworksEBGP Router) as the User-ID host.
To redistribute detailed HIP information from mobile users to Panorama, create a User-ID agent in Panorama and specify the User-ID Agent Address (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address) as the User-ID host.If you have configured an on-premises gateway as an internal gateway at a remote user location, you can also send the HIP information for users at remote networks to Panorama by creating a User-ID agent in Panorama and specifying the remote network EBGP Router address (PanoramaCloud ServicesStatusNetwork DetailsRemote NetworksEBGP Router) as the User-ID host.![]()
Enable and configure HIP redistribution in Prisma Access: