Prisma Access
Configure HIP Redistribution in Prisma Access
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure HIP Redistribution in Prisma Access
How to configure HIP redistribution in a Prisma Access (Managed by Panorama)
deployment.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
When a mobile user whose endpoint has the GlobalProtect app installed connects to Prisma
Access, Prisma Access collects the user’s HIP information from the endpoint’s
GlobalProtect app, which makes the HIP report available in Prisma Access.
To use HIP redistribution, users must have the GlobalProtect app installed on their
endpoint. While Prisma Access supports Clientless VPN, you can't redistribute HIP
information for Clientless VPN users.
HIP redistribution is applicable to both mobile users and users at remote networks.
However, for users at remote networks, an on-premises gateway must detect that the user
is internal to the organization’s network using internal host detection before the
on-premises gateway can send HIP information to Prisma Access.
In Prisma Access, you configure internal host detection when you configure your mobile user deployment.
To assure consistent policy enforcement, you can use HIP redistribution to allow Prisma
Access to distribute users’ HIP information to other
Panorama appliances, gateways, firewalls, and virtual systems in your deployment, as
well as distribute HIP information from those devices to Prisma Access in some cases. This ability allows you to consistently apply
HIP-based policy enforcement for users’ traffic, including policies for internet-bound
traffic or for traffic that is accessing an internal application or resource in your
organization’s headquarters or data center. Redistributing HIP information to the
Panorama appliance also lets you view detailed HIP information for Prisma Access
users from that appliance.
Keep in mind that GlobalProtect internal and external
gateways don't support bi-directional HIP redistribution. Therefore, the best practice
is to use your Panorama appliance as your redistribution point. In this deployment, you
would configure your internal and external gateways to send the HIP reports to Panorama
and have Panorama forward them on to your firewalls for consistent policy enforcement
across your environment.
Configure HIP Redistribution in Prisma Access (Strata Cloud Manager)
Learn how to redistribute HIP information.
HIP report redistribution is enabled by default in
Strata Cloud Manager. To view the redistribution details
or to disable redistribution, follow the steps below.
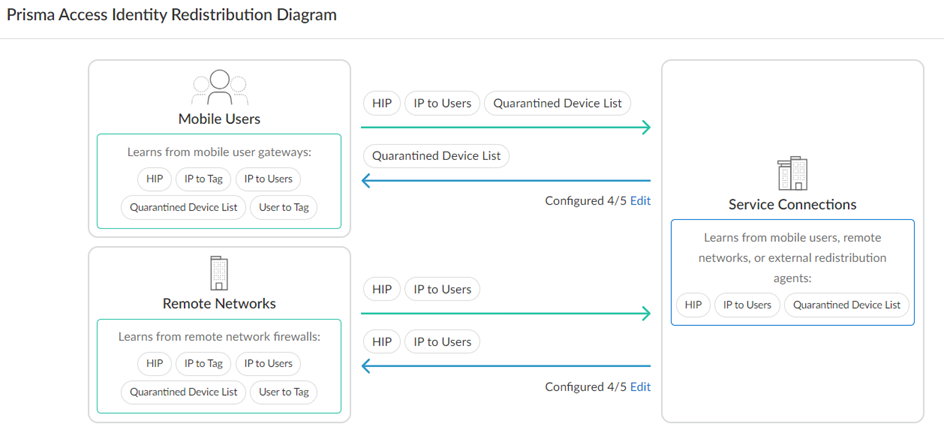
- In Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessIdentity ServicesIdentity Redistribution.The Prisma Access Identity Redistribution Diagram displays the default HIP report redistribution settings between mobile users and service connections as well as between remote networks and service connections.
![]() To disable redistribution between a segment, click Edit and then click Edit next to the relevant source remote network.Disable HIP.
To disable redistribution between a segment, click Edit and then click Edit next to the relevant source remote network.Disable HIP.
Configure HIP Redistribution in Prisma Access (Panorama)
Learn how to redistribute HIP information.
To allow Prisma Access to collect and redistribute HIP information, complete the
following task.
- Allow Prisma Access to redistribute HIP information.
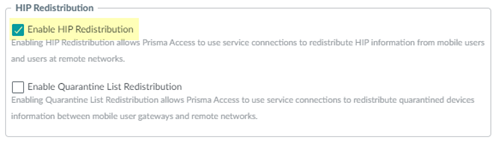
- In Panorama, select PanoramaCloud ServicesConfigurationService Setup.Click the gear icon to edit the settings.In the Advanced tab, select Enable HIP Redistribution.Enabling HIP Redistribution enables Prisma Access to redistribute the HIP reports received from the GlobalProtect app to internal firewalls and to Panorama.
![]() Configure Panorama to receive HIP reports from Prisma Access.
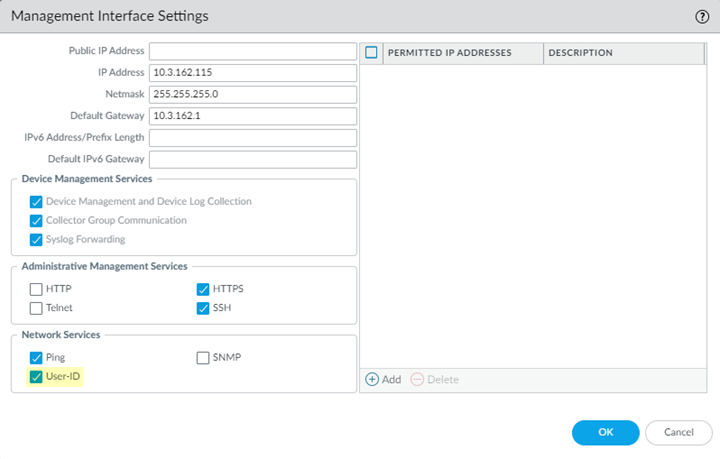
Configure Panorama to receive HIP reports from Prisma Access.- Select PanoramaSetupInterfaces.Select the Management interface.Select User-ID.
![]() Configure Panorama to collect the User-ID mapping from Prisma Access.
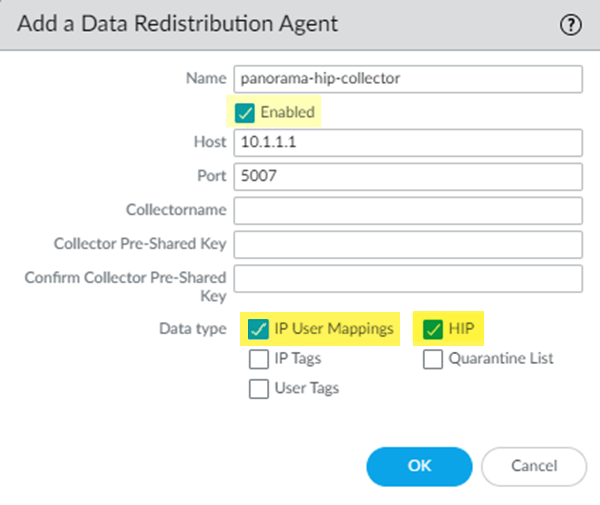
Configure Panorama to collect the User-ID mapping from Prisma Access.- From the Panorama that manages Prisma Access, select PanoramaData RedistributionAgents (for Panorama 10.x appliances) or PanoramaUser IdentificationUser-ID Agents (for 9.1.x Panorama appliances).Add a User-ID Agent and give it a Name.Enter one of the following values in the Host field, depending on the types of HIP information you want to collect.
- To collect HIP information for mobile users, enter the User-ID Agent Address (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address).
- To collect HIP information from users at a remote network locations with an internal gateway, enter the IP address of the internal gateway.
- To collect HIP information from users are a remote network connection, enter the EBGP Router address (PanoramaCloud ServicesStatusNetwork DetailsRemote NetworksEBGP Router as the User-ID host.
Enter 5007 in the port field.By default, the User-ID agent uses port 5007 to listen for HIP information requests.Make sure that your network does not block access to this port between Prisma Access and the Active Directory server or User-ID Agent.Select Enabled to enable Panorama to communicate with the User-ID agent.Select IP User Mappings and HIP to enable Panorama to receive IP address-to-username mappings and GlobalProtect HIP data from all mobile user locations.Click OK.![]() Repeat Step 3 for each service connection to which you want to configure HIP report collection.
Repeat Step 3 for each service connection to which you want to configure HIP report collection.