Prisma Access
Enable Mobile Users to Authenticate to Prisma Access
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Enable Mobile Users to Authenticate to Prisma Access
Define authentication settings for mobile users to connect
to Prisma Access.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can authenticate mobile users to Prisma
Access using any of the supported authentication
types. Follow these steps to set up authentication for GlobalProtect
or Explicit Proxy mobile users.
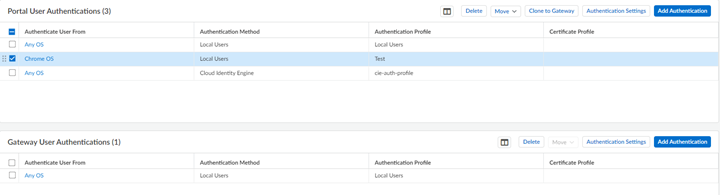
- Go to ConfigurationNGFW and Prisma Access and go to either your Mobile Users: GlobalProtect or Explicit Proxy configuration and Add Authentication.
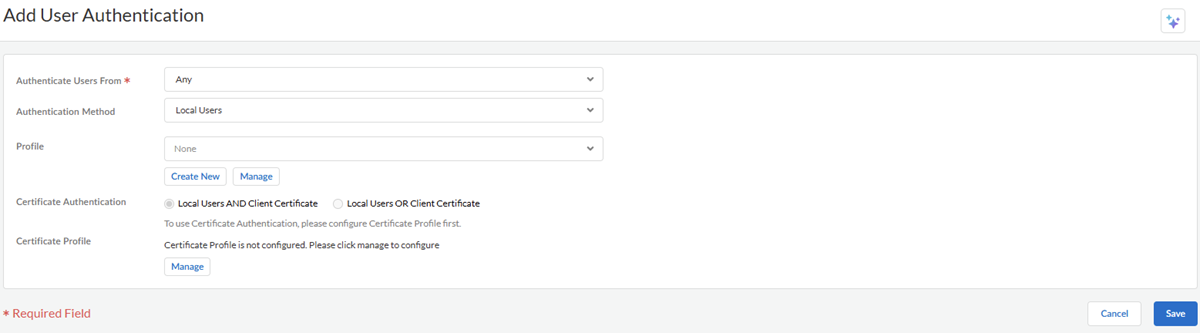
![]() Choose your Authentication Method from the supported authentication types.If you haven’t already integrated Prisma Access with your authentication services, here’s how.Choose the authentication Profile you configured to enable Prisma Access to connect to the service you want to use to authenticate users.
Choose your Authentication Method from the supported authentication types.If you haven’t already integrated Prisma Access with your authentication services, here’s how.Choose the authentication Profile you configured to enable Prisma Access to connect to the service you want to use to authenticate users.-
Specify the SAML authentication Profile if you used SAML in Step 2, or create a new SAML authentication profile to use with Prisma Access.
- Specify the CIE authentication Profile if you used CIE in Step 2 , or create a new CIE authentication profile to use with Prisma Access.
-
Specify the Kerberos authentication Profile if you used Kerberos in Step 2, or create a new Kerberos authentication profile to use with Prisma Access.
Specify certificate authentication settings:![]()
- For enhanced security, use a certificate (in addition to your authentication service) to obtain usernames and authenticate users to Prisma Access. To authenticate users based on a client certificate, one of the certificate fields, such as the Subject Name field, must identify the username. Mobile users that successfully authenticate through client certificate authentication, do not have the option to sign out of the GlobalProtect app.With Prisma Access, you can choose to require for mobile users to pass both certificate authentication and authentication based on the authentication type or to grant access to mobile users as long as they’ve successfully passed only one of those checks.
- Certificate ProfileUse an optional certificate profile to verify the certificates mobile users present to Prisma Access with a connection request. The certificate profile specifies the contents of the username and user domain fields; lists CA certificates; criteria for blocking a session; and offers ways to determine the revocation status of CA certificates. Because the certificate is part of the authentication for the mobile user, you must pre-deploy certificates used in certificate profiles to your users before their initial login.The certificate profile specifies which certificate field contains the username (Subject or Subject Alt). If the certificate profile specifies Subject in the Username Field, the certificate presented by the endpoint must contain a common-name for the endpoint to connect. If the certificate profile specifies a Subject-Alt with an Email or Principal Name as the Username Field, the certificate must contain the corresponding fields, which will be used as the username when the GlobalProtect app authenticates to Prisma Access.
Specify a Cookie Lifetime for the cookie that stores the users’ authentication credentials.After the IdP authenticates the user, Prisma Access stores the authentication state of the user in the Authentication Cache Service (ACS). The validity period of the authentication is based on the Cookie Lifetime value you specify here.To prevent issues with users not being able to download large files before the cookie lifetime expires, or the cookie expiring when users are accessing a single website for a long period of time, Palo Alto Networks recommends that you configure a Cookie Lifetime of at least one day. If Explicit Proxy users have a cookie lifetime expiration issue, they can browse to a different website to re-authenticate to ACS and refresh the ACS cookie.