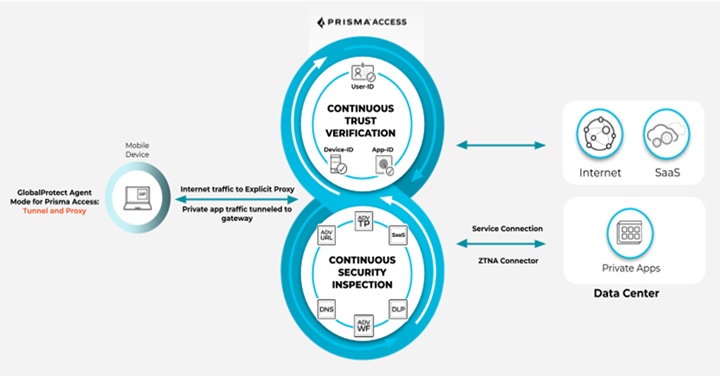
Prisma Access
GlobalProtect in Tunnel and Proxy Mode
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
GlobalProtect in Tunnel and Proxy Mode
Configure the GlobalProtect app to send internet-bound traffic to explicit proxy and
tunnel traffic to your private apps.
| Where Can I Use This? | What Do I Need? |
|---|---|
If you'd like to use this feature in your Prisma Access environment,
get in touch with your account team to learn more.
|
|
In Tunnel and Proxy mode, the GlobalProtect app sends
internet-bound traffic to the explicit proxy based on the rules you define in a PAC
file. For the remaining traffic, it uses the split tunneling rules and logic defined in
the PAC file to determine which traffic to send through the tunnel, and which traffic
can bypass the tunnel. If you don't have split tunnel rules defined, the app sends all
remaining traffic through the tunnel.
When running the GlobalProtect app in Tunnel and Proxy mode,
host information profile (HIP) functionality is only supported for traffic over a
GlobalProtect tunnel.
You need Strata Cloud Manager and GlobalProtect agent version
6.3.0 for GlobalProtect Proxy channel to support all the IPv4 TCP connections,
including non-proxy-aware traffic. To ensure seamless functionality, the DNS
configured on the endpoints must be able to resolve destination FQDN.
GlobalProtect in Tunnel and Proxy Mode (Strata Cloud Manager)
Configure GlobalProtect in Tunnel and Proxy Mode.
- Enable the Agent-based Proxy functionality for mobile users on Prisma Access.
- Enable explicit proxy.
- Select Configuration NGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit Proxy.
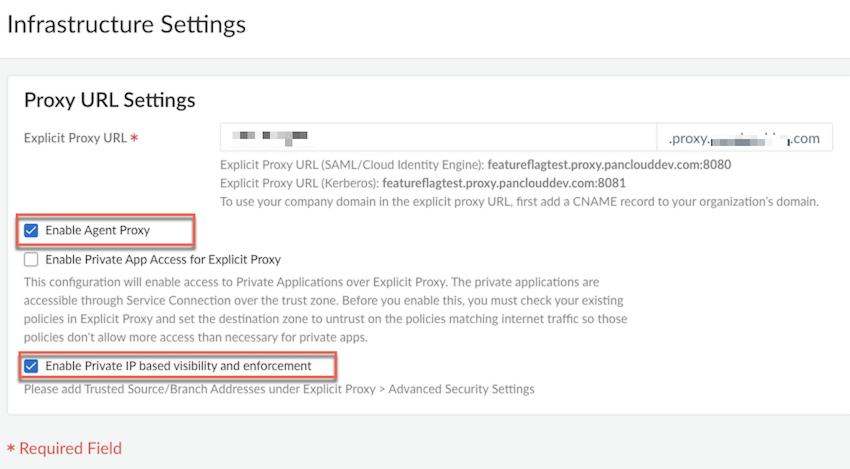
- In the Infrastructure Settings area, click Setup Proxy Settings and specify an Explicit Proxy URL.
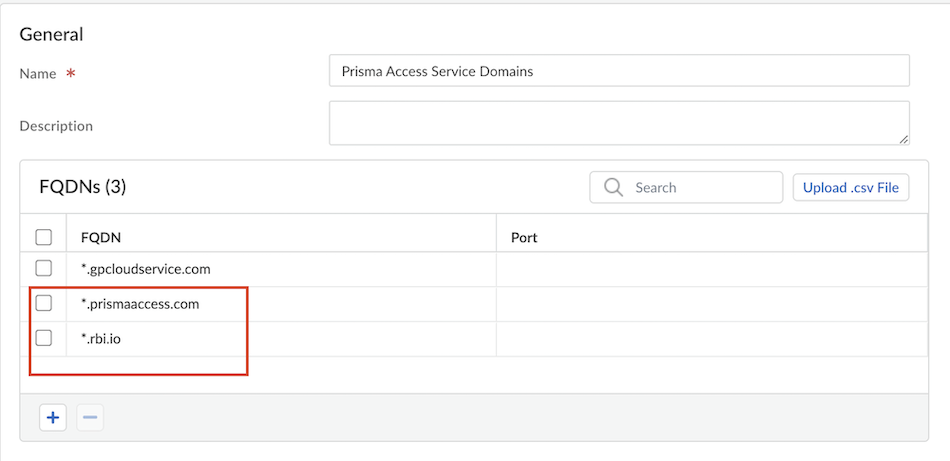
Enable Agent Proxy , and optionally Enable Private IP based visibility and enforcement, and click Save.![]() Choose the Prisma Access where you want to support mobile users.For the best user experience, if you're limiting the number of locations, choose locations that are closest to your end users. If a location isn't available in the country where your mobile users reside, choose a location that's closest to the mobile users.Create a Forwarding Profile to define the traffic you want to send through Explicit Proxy. While configuring the forwarding profile, bypass *.prismaaccess.com and *.gpcloudservice.com domains.
Choose the Prisma Access where you want to support mobile users.For the best user experience, if you're limiting the number of locations, choose locations that are closest to your end users. If a location isn't available in the country where your mobile users reside, choose a location that's closest to the mobile users.Create a Forwarding Profile to define the traffic you want to send through Explicit Proxy. While configuring the forwarding profile, bypass *.prismaaccess.com and *.gpcloudservice.com domains.![]() Attach the Forwarding Profile to your GlobalProtect app configuration.Select Configuration NGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit ProxyAdvanced Security Settings Authentication Settings and add the domains you need to bypass.All requests to the proxy undergo authentication. However, if you're passing IdP flows through the proxy, then you need to bypass them for the authentication to be successful.In this example, we are bypassing the GlobalProtect portal and Okta, but please customize these to the IdPs that you use.
Attach the Forwarding Profile to your GlobalProtect app configuration.Select Configuration NGFW and Prisma AccessConfiguration ScopePrisma AccessExplicit ProxyAdvanced Security Settings Authentication Settings and add the domains you need to bypass.All requests to the proxy undergo authentication. However, if you're passing IdP flows through the proxy, then you need to bypass them for the authentication to be successful.In this example, we are bypassing the GlobalProtect portal and Okta, but please customize these to the IdPs that you use.![]() Configure Tunnel and Proxy mode for the GlobalProtect app on Prisma Access.In Tunnel and Proxy mode, the connect method you set only applies to the traffic tunnel through GlobalProtect. The agent-based proxy functionality provides always-on Internet security after the GlobalProtect tunnel is established, and this security persists even after a user disconnects from the GlobalProtect app.
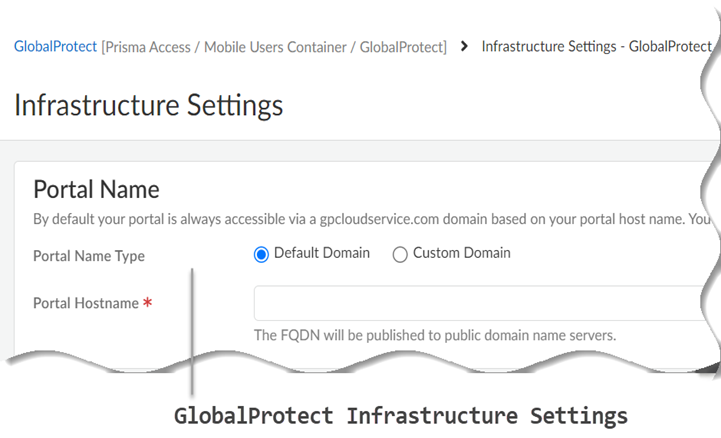
Configure Tunnel and Proxy mode for the GlobalProtect app on Prisma Access.In Tunnel and Proxy mode, the connect method you set only applies to the traffic tunnel through GlobalProtect. The agent-based proxy functionality provides always-on Internet security after the GlobalProtect tunnel is established, and this security persists even after a user disconnects from the GlobalProtect app.- Select Configuration NGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectInfrastructureInfrastructure Settings and specify the Portal Name.
![]()
- Default Domain—If you select this option, your portal hostname uses the default domain name: .gpcloudservice.com. In this case, simply enter a Portal Hostname to append to the default domain name. Prisma Access for Users will automatically create the necessary certificates and publish the hostname to public DNS servers.
- Custom Domain—You can also customize the portal address if you want the domain in the portal hostname to match your company domain name (for example, myportal.mydomain.com).
Enable mobile users to authenticate to Prisma Access.Enable GlobalProtect tunnel and proxy mode for Prisma Access in the GlobalProtect app settings to send internet traffic to the agent-based proxy.- Select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtect.
- On the GlobalProtect App tab, click Default to customize the app settings or Add App Settings add a new configuration.
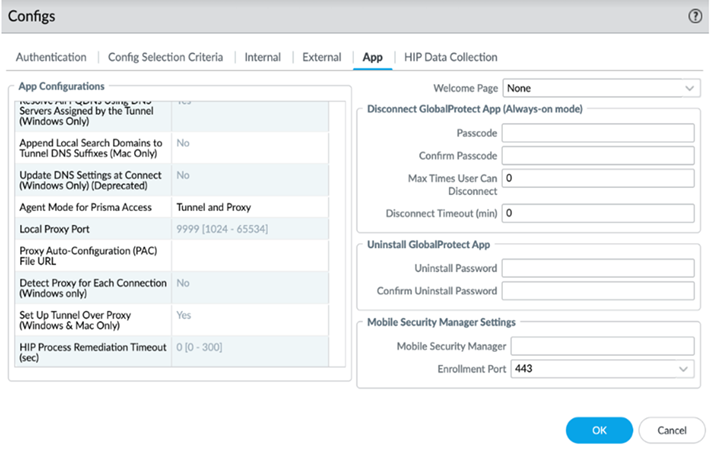
- Click Show Advanced Options and in the App Configuration section.
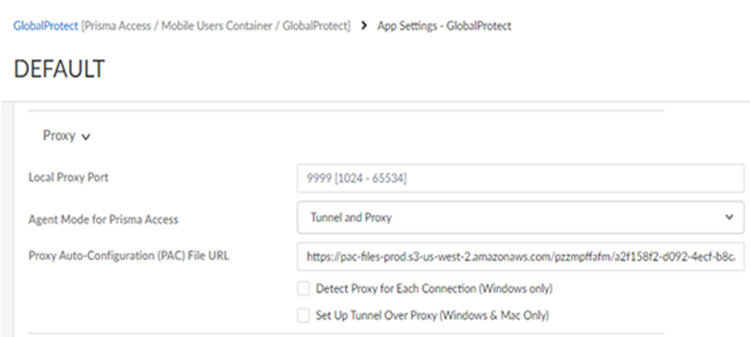
- In the Proxy section set Agent Mode for Prisma Access to Tunnel and Proxy to instruct the GlobalProtect app to send the internet traffic to the explicit proxy on Prisma Access and private app traffic to the VPN. After you configure the Tunnel and Proxy mode on Prisma Access, users can securely access the internet via Prisma Access even when users disconnect or disable the GlobalProtect app.
- (Optional) Configure the local proxy port. The port range is 1024 to 65534 and the default port is 9999. If the default port isn't available, GlobalProtect will try 10 other ports in the range of 9999 to 10009 and use the port that is available. You can also pick your own port number within the range.
- (Optional) Configure PAC Auto-Configuration (PAC) File URL if you want to push the new PAC URL for the proxy settings to the endpoint. The PAC URL pushes to the endpoint once the user connects. When the user disconnects the GlobalProtect app, the endpoint proxy configurations are automatically disabled and reverting to the previous settings.
- (Optional) Enable Allow User to Rediscover Network if you want the user to check the portal for any new settings.
- (Optional) Configure GlobalProtect App Config Refresh Interval (hours). By default, the GlobalProtect client refreshes the cached portal configuration every 24 hours. You can change the refresh interval based on your business requirements.
- Disable Set Up Tunnel Over Proxy (Windows & Mac Only).
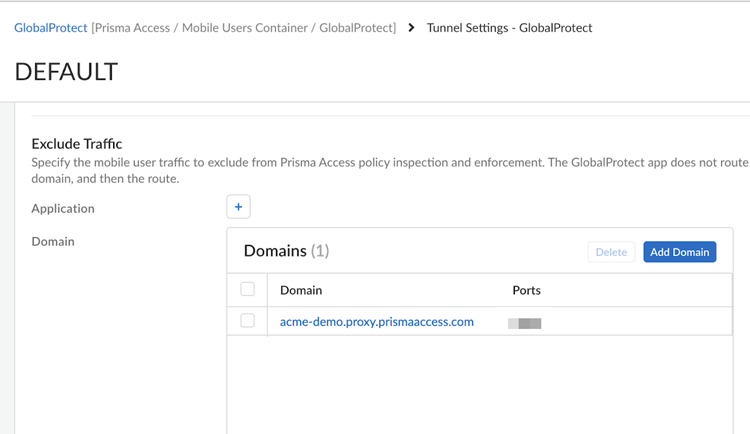
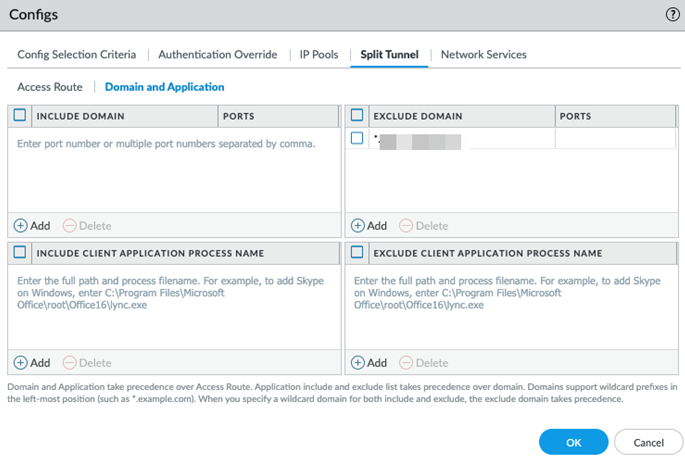
![]() In the Split Tunnel configuration, exclude the Explicit Proxy FQDN and the PAC file FQDN.
In the Split Tunnel configuration, exclude the Explicit Proxy FQDN and the PAC file FQDN.- Select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtect.
- On the GlobalProtect App tab, click Default to customize the Tunnel Settings or Add Tunnel Settings add a new configuration.
- Under Exclude Traffic, Add
Domain.
![]() Replace the FQDN in the image with your proxy FQDN.
Replace the FQDN in the image with your proxy FQDN.
Enable Always-On security by configuring the following settings on the Configuration NGFW andPrisma AccessConfiguration ScopePrisma AccessGlobalProtectGlobalProtect AppAdd App Settings page:- Set Disable GlobalProtect to Disallow, Allow with Passcode, or Allow with Ticket.Disable Allow user to Sign Out from GlobalProtect App.Configure decryption for Explicit Proxy traffic.
- Select ConfigurationNGFW and Prisma AccessSecurity ServicesDecryption.
- If you enable decryption, make sure you set up the
decryption certificate as a trusted root CA.
![]()
Configure security policy rules for explicit proxy traffic.- Select ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy.
- Follow the Internet Gateway Security Policy Best Practices.
(Optional) Configure the GlobalProtect app in Proxy and Tunnel mode in a non-default route network.- (Optional) Host a PAC file internally and add the Prisma Access explicit proxy FQDN as a proxy in the PAC file, or host the PAC file in a Forwarding Profile and add routes in your network for PAC service IP addresses.
- Forward authentication requests to the internet for the portal and gateway FQDNs and for IdP URLs.
- Set up routes to the explicit proxy FQDN or IP addresses on perimeter devices to allow users to access the internet via the explicit proxy.
- (Optional) Add DNS records to resolve the Prisma Access explicit proxy FQDN to an internal IP address if users can’t resolve public domains in the branch network and add destination NAT for the internal IP address to the explicit proxy FQDN or IP address.
- To enable users to access private apps directly when in the
office:
- Direct Access: Enable Internal Host Detection and keep the internal gateway list empty.
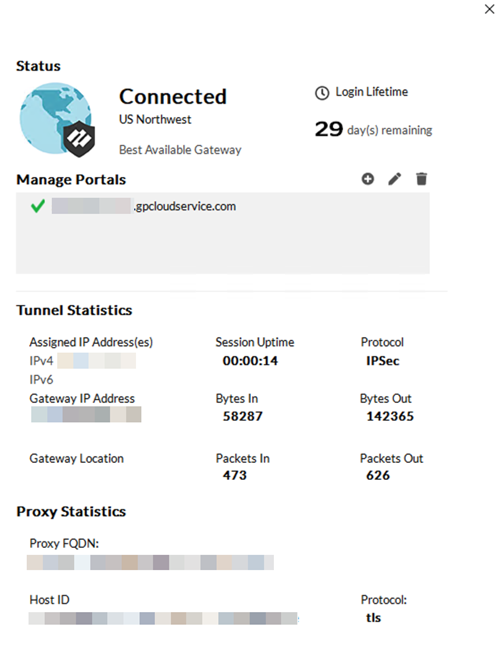
Click Save and Push Config to GlobalProtect and Explicit Proxy.Verify and troubleshoot the agent proxy deployment.- Verify the information about your network connection on the GlobalProtect app Connections tab under Settings.
- Open the GlobalProtect app.
- Select Settings to open the GlobalProtect Settings panel, and then select Connections.
![]() View and collect the GlobalProtect logs.View the PanGPS log to verify the proxy mode configuration on the GlobalProtect portal.You can verify that Proxy mode is configured by looking for the following event in the PanGPS log:OnProxyAgentMode: hybrid modeTo view GlobalProtect logs in Prisma Access, select Incidents & AlertsLog Viewer and:
View and collect the GlobalProtect logs.View the PanGPS log to verify the proxy mode configuration on the GlobalProtect portal.You can verify that Proxy mode is configured by looking for the following event in the PanGPS log:OnProxyAgentMode: hybrid modeTo view GlobalProtect logs in Prisma Access, select Incidents & AlertsLog Viewer and:- GlobalProtect, for authentication logs
- Traffic and Decryption for user access logs
Disconnect and Disable Tunnel and Proxy Mode with Always-On Connect MethodStarting from GlobalProtect version 6.3.1, when you configure Tunnel and Proxy mode for the GlobalProtect app along with Always-On mode as the connect method and you want to disconnect the tunnel and proxy mode, you must perform the following steps:- Disconnect the GlobalProtect app to disconnect the tunnel (VPN) connection. When you disconnect the app, the tunnel (VPN) connection gets disconnected and the app will still be connected through the proxy mode.
- Disable the GlobalProtect app to disconnect both the tunnel and proxy mode. When you disable the app, both the tunnel and proxy mode will be disconnected and the app will not be connected anymore.
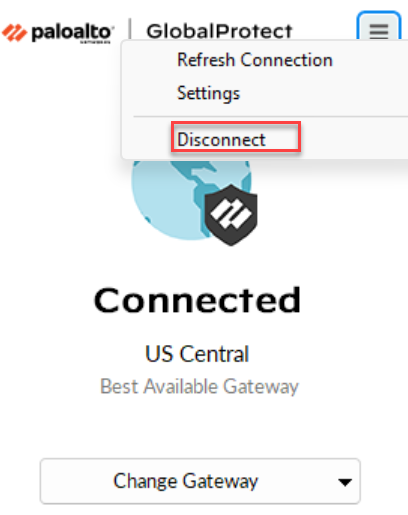
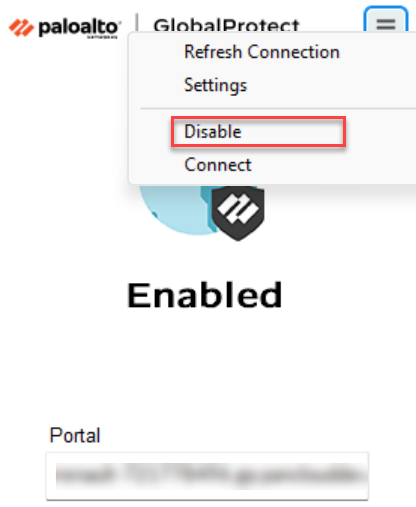
To disconnect and disable the GlobalProtect app configured with Tunnel and Proxy (hybrid mode) and Always-On connect method, you must:- Disconnect the GlobalProtect app using the
Disconnect option from the hamburger
menu. When you disconnect the app, the tunnel (VPN) connection gets
disconnected.
![]() After you disconnect the app, the VPN connection gets disconnected but the proxy mode is enabled. The app will still be connected through the proxy mode and the app displays the status as Enabled.If you want to reconnect the tunnel (VPN) connection, you can use the Connect option from the hamburger menu.
After you disconnect the app, the VPN connection gets disconnected but the proxy mode is enabled. The app will still be connected through the proxy mode and the app displays the status as Enabled.If you want to reconnect the tunnel (VPN) connection, you can use the Connect option from the hamburger menu.![]()
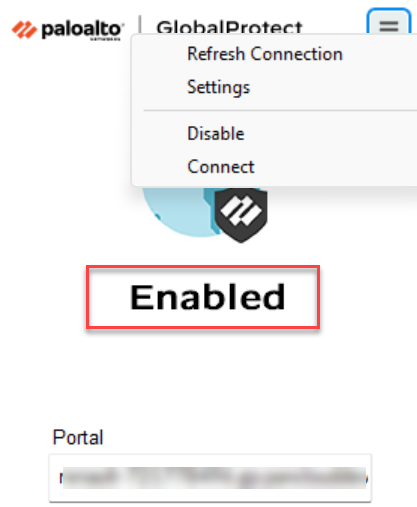
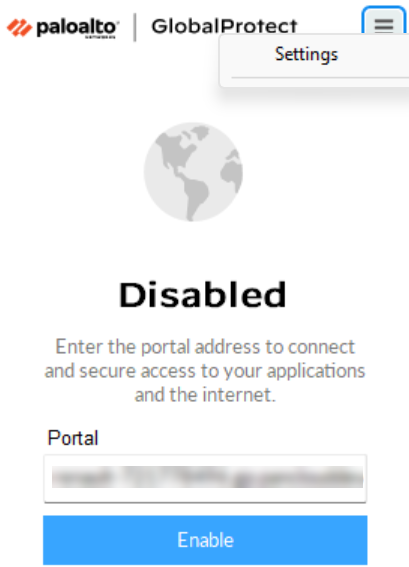
- Disable the app GlobalProtect app using the
Disable option from the hamburger menu.
After you disable the app, both the tunnel and proxy connection gets
disconnected.
![]()
The app will be disabled and it displays the status as Disabled.![]()
GlobalProtect in Tunnel and Proxy Mode (Panorama)
Configure GlobalProtect in Tunnel and Proxy Mode.If you convert a single-tenant Prisma Access (Managed by Panorama) deployment to multitenancy, only the first tenant (the tenant you migrated) supports this feature. Also, in this first tenant, you must set up your policy rules in the predefined Explicit_Proxy_Device_Group rather than in a custom device group. Any subsequent tenants you create for the multitenant deployment after the first do not support this feature.- Enable the Agent-based Proxy functionality for mobile users.
- Enable explicit proxy.
- Select PanoramaCloud ServicesConfigurationMobile Users—Explicit Proxy.
- Configure the explicit proxy setup to specify an Explicit Proxy URL.
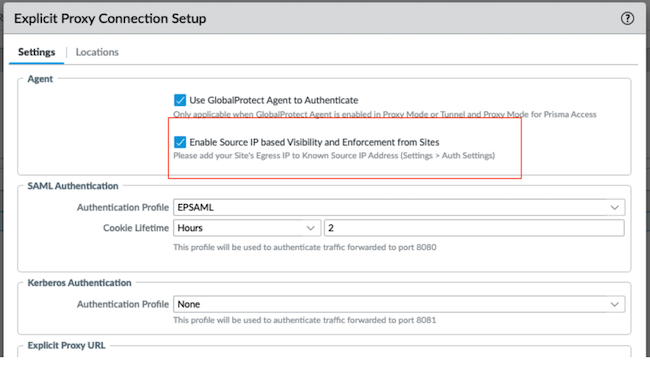
Select Use GlobalProtect app to Authenticate to enable the agent-based proxy functionality, and optionally Enable Source IP based Visibility and Enforcement from Sites.![]() Enter the PAC (Proxy Auto-Configuration) File URL. Ensure that you enter a port of 8080 in the PAC file.
Enter the PAC (Proxy Auto-Configuration) File URL. Ensure that you enter a port of 8080 in the PAC file.- The Proxy statement in the PAC file must use the Prisma Access FQDN you configured above.
- The PAC file must be configured to exclude the GlobalProtect gateways (*.gp.gpcoudservice.com).
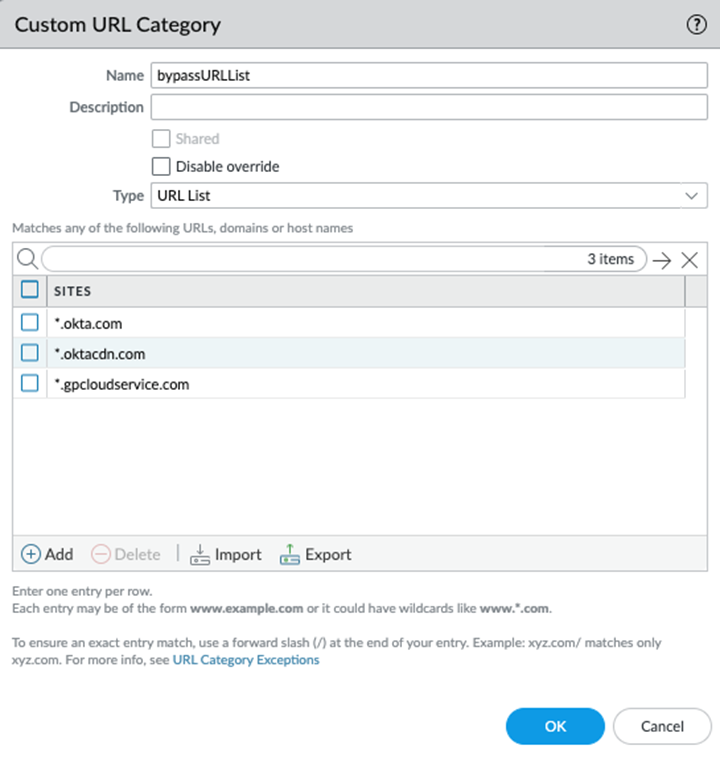
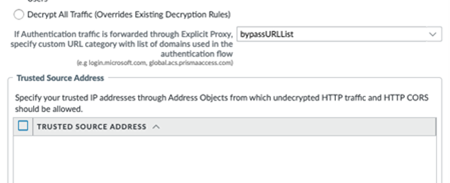
Select the Connection Name for the explicit proxy setup that you configured.Select the Locations and the regions where you want to deploy your explicit proxy for mobile users.Prisma Access adds a proxy node into each location that you select. Explicit proxy supports a subset of all Prisma Access. For the best user experience, if you are limiting the number of locations, choose locations that are closest to your end users. If a location is not available in the country where your mobile users reside, choose a location that is closest to the mobile users.Bypass identity providers (IDPs).All requests to the proxy are authenticated. However, if you're passing IDP flows through the proxy, then you need to bypass them for the authentication to be successful.In this example, we're bypassing the GlobalProtect portal and Okta, but please customize these to the IDPs that you use.- With the Explicit_Proxy_Device_Group selected, select ObjectCustom Objects URL Category and create a custom URL category.In the custom URL category, add all the FQDN domains that need to be bypassed from EP authentication.
![]() Select Cloud ServicesConfiguration Mobile UsersExplicit ProxySettingsAuthentication Settings and attach the custom URL category.
Select Cloud ServicesConfiguration Mobile UsersExplicit ProxySettingsAuthentication Settings and attach the custom URL category.![]() Commit and push to the Explicit_Proxy_Device_Group.Configure the GlobalProtect portal.In Tunnel and Proxy mode, the connect method you set only applies to the traffic tunnel through GlobalProtect. The agent-based proxy functionality provides always-on Internet security after the GlobalProtect tunnel is established, and this security persists even after a user disconnects from the GlobalProtect app.
Commit and push to the Explicit_Proxy_Device_Group.Configure the GlobalProtect portal.In Tunnel and Proxy mode, the connect method you set only applies to the traffic tunnel through GlobalProtect. The agent-based proxy functionality provides always-on Internet security after the GlobalProtect tunnel is established, and this security persists even after a user disconnects from the GlobalProtect app.- In the Onboarding section, click Configure.
- On the General tab, specify the Portal
Name Type:Use Default Domain— If you select this option, your portal hostname uses the default domain name: .gpcloudservice.com. In this case, simply enter a Portal hostname to append to the default domain name. Prisma Access will automatically create the necessary certificates and publish the hostname to public DNS servers.Use Company Domain— Select this option if you want the domain in the portal hostname to match your company domain name (for example, myportal.mydomain.com).
- Select an Authentication Profile that specifies how Prisma Access should authenticate mobile users or create a new one.
- (Optional) Select an Authentication Override Certificate to encrypt the secure cookies that mobile users use to authenticate to the portal and gateway.
- Enable Tunnel and Proxy mode on GlobalProtect.
- Select NetworkGlobalProtect Portals.
- Select the portal configuration to which you are adding the agent configuration, and then select the Agent tab.
- On the Agenttab, select App.
- In the App Configurations area, set the Agent Mode for Prisma Access to Tunnel and Proxy to send internet traffic to the Prisma Access explicit proxy and private app traffic to the VPN.
![]() Perform optional configurations.
Perform optional configurations.- (Optional) Configure the local proxy port. The port range is 1024 to 65534 and the default port is 9999. If the default port isn't available, GlobalProtect will try 10 other ports in the range of 9999 to 10009 and use the port that is available. You can also pick your own port number within the range.
- (Optional) Configure PAC Auto-Configuration (PAC) File URL if you want to push a custom PAC URL for the proxy settings to the endpoint. The PAC URL pushes to the endpoint once the user connects. When the user disconnects the GlobalProtect app, the endpoint proxy configurations are automatically disabled and reverting to the previous settings.
- (Optional) Enable Allow User to Rediscover Network if you want the user to check the portal for any new settings.
- (Optional) Configure GlobalProtect App Config Refresh Interval (hours). By default, the GlobalProtect client refreshes the cached portal configuration every 24 hours. You can change the refresh interval based on your business requirements.
In the split tunnel configuration, exclude the Explicit Proxy FQDN and the PAC file FQDN.Enable Always-On internet security by configuring the following settings:- Set Allow User to Disable GlobalProtect to Disallow, Allow with Passcode, or Allow with Ticket.Set Allow user to Sign Out from GlobalProtect App to No.(Optional) Configure decryption policy for explicit proxy traffic.If you enable decryption, make sure the decryption certificate is also set up as a trusted root CA.
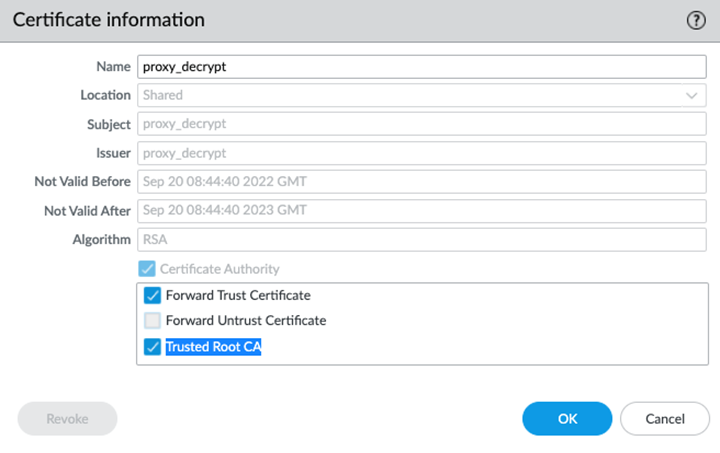
- Select DeviceCertificate ManagementCertificates and create a certificate that is a Trusted Root CA and a Forward Trust Certificate.
![]() Create a Decryption rule under Explicit_Proxy_Device Group with SSL forward proxy.Configure security policy rules for explicit proxy traffic.
Create a Decryption rule under Explicit_Proxy_Device Group with SSL forward proxy.Configure security policy rules for explicit proxy traffic.- Select ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessSecurity ServicesSecurity Policy..
- Follow the Internet Gateway Security Policy Best Practices.
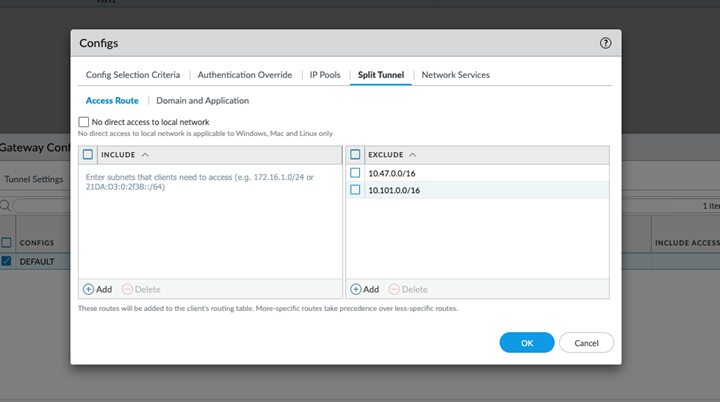
Configure split tunnel on Panorama.- Select NetworkMobile User TemplateGatewaysGlobalProtect_ExternalGatewayAgentClient SettingsSplit .Configure the tunnel based on routes and domains.
![]()
![]() (Optional) Configure the GlobalProtect app in Tunnel and Proxy mode in a non-default route network.
(Optional) Configure the GlobalProtect app in Tunnel and Proxy mode in a non-default route network.- (Optional) Host a PAC file internally and add the Prisma Access explicit proxy FQDN as a proxy in the PAC file, or host the PAC file in a Forwarding Profile and add routes in your network for PAC service IP addresses.
- Verify that GlobalProtect portal URL and IDP URLs are being forwarded to the Prisma Access Explicit Proxy.
- Set up routes to the explicit proxy FQDN or IP addresses on perimeter devices to allow users to access the internet via the explicit proxy.
- (Optional) Add DNS records to resolve the Prisma Access explicit proxy FQDN to an internal IP address if users can’t resolve public domains in the branch network and add destination NAT for the internal IP address to the explicit proxy FQDN or IP address.
- To enable users to access private apps directly when in the office:
- Direct Access—Enable Internal Host Detection and keep the internal gateway list empty.
Commit and your changes to Panorama and Commit and Push the configuration changes to Prisma Access Mobile Users and Explicit Proxy.Verify and troubleshoot the agent proxy deployment.- Verify the information about your network connection on the GlobalProtect app Connections tab under Settings.
- Open the GlobalProtect app.
- Select Settings to open the GlobalProtect Settings panel, and then select Connections.
![]() View and collect the GlobalProtect logsView the PanGPS log to verify the proxy mode configuration on the GlobalProtect portal.You can verify fthat Proxy mode is configured by looking for the following event in the PanGPS log:OnProxyAgentMode: hybrid modeTo view GlobalProtect logs in Panorama, select Monitor Logs and:
View and collect the GlobalProtect logsView the PanGPS log to verify the proxy mode configuration on the GlobalProtect portal.You can verify fthat Proxy mode is configured by looking for the following event in the PanGPS log:OnProxyAgentMode: hybrid modeTo view GlobalProtect logs in Panorama, select Monitor Logs and:- GlobalProtect, for authentication logs
- Traffic and Decryption for user access logs
Disconnect and Disable Tunnel and Proxy Mode with Always-On Connect MethodStarting from GlobalProtect version 6.3.1, when you configure Tunnel and Proxy mode for the GlobalProtect app along with Always-On mode as the connect method and you want to disconnect the tunnel and proxy mode, you must perform the following steps:- Disconnect the GlobalProtect app to disconnect the tunnel (VPN) connection. When you disconnect the app, the tunnel (VPN) connection gets disconnected and the app will still be connected through the proxy mode.
- Disable the GlobalProtect app to disconnect both the tunnel and proxy mode. When you disable the app, both the tunnel and proxy mode will be disconnected and the app will not be connected anymore.
To disconnect and disable the GlobalProtect app configured with Tunnel and Proxy (hybrid mode) and Always-On connect method, you must:- Disconnect the GlobalProtect app using the
Disconnect option from the hamburger
menu. When you disconnect the app, the tunnel (VPN) connection gets
disconnected.
![]() After you disconnect the app, the VPN connection gets disconnected but the proxy mode is enabled. The app will still be connected through the proxy mode and the app displays the status as Enabled.If you want to reconnect the tunnel (VPN) connection, you can use the Connect option from the hamburger menu.
After you disconnect the app, the VPN connection gets disconnected but the proxy mode is enabled. The app will still be connected through the proxy mode and the app displays the status as Enabled.If you want to reconnect the tunnel (VPN) connection, you can use the Connect option from the hamburger menu.![]()
- Disable the app GlobalProtect app using the
Disable option from the hamburger menu.
After you disable the app, both the tunnel and proxy connection gets
disconnected.
![]()
The app will be disabled and it displays the status as Disabled.![]()