Prisma Access
GlobalProtect — Customize App Settings
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
GlobalProtect — Customize App Settings
Customize how your end users interact with the GlobalProtect
app.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Customize how your end users interact with the
GlobalProtect app.
There are some settings that you can customize
globally. These global app settings apply
to the GlobalProtect app across all devices. Other GlobalProtect
app settings are set by default. You can then customize these options
and, based on match criteria, target them to specific users
and devices. The match criteria you define for app settings tells
Prisma Access the users, devices, or systems that should receive
the settings. For example, you could specify that a rule applies only
to devices with serial numbers that match Active Directory entries.
| GlobalProtect App Settings | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Explore and customize app settings here (Prisma Access examples are shown in the table) |
Prisma Access (Managed by Strata Cloud Manager): Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectGlobalProtect App.
You can
Add multiple app settings, or
Clone an existing app setting and
modify it. 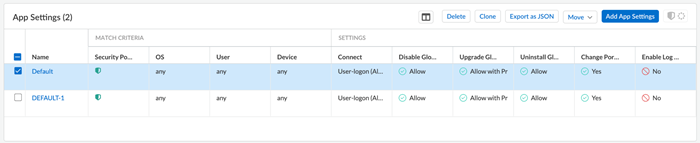
Prisma Access (Managed by Panorama): in the
Mobile_User_Template, go to NetworkGlobalProtectPortalsGlobalProtect_PortalAgentDefaultApp
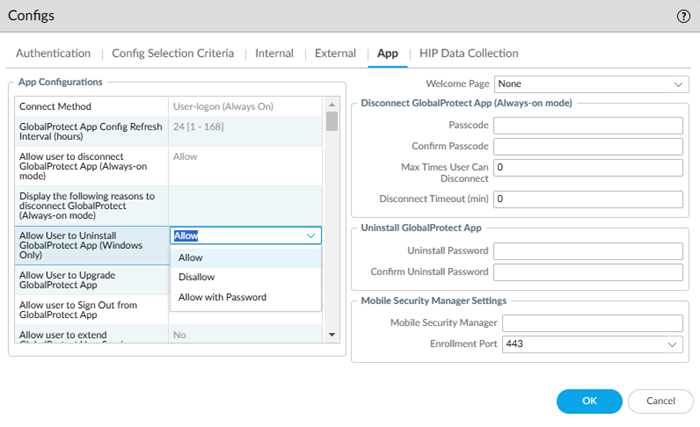
| ||||||||||
|
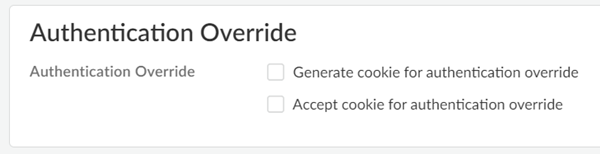
Authentication Override
|
Enable Prisma Access to generate and accept secure, encrypted
cookies for user authentication. Turning this on allows the user
to provide login credentials only once during the specified
period of time.
| ||||||||||
|
Connection Settings
|
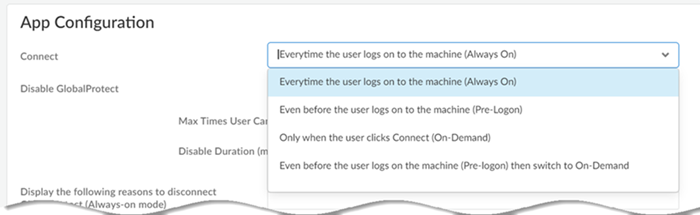
Specify the method that the GlobalProtect app uses to
Connect to Prisma Access.
| ||||||||||
|
GlobalProtect
|
Decide what GlobalProtect app settings the user can adjust:
| ||||||||||
| App Configuration -Advanced Options | |||||||||||
|
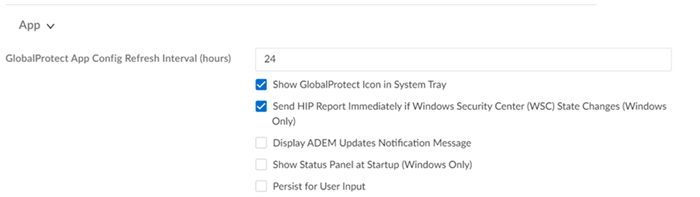
App Settings
|
| ||||||||||
|
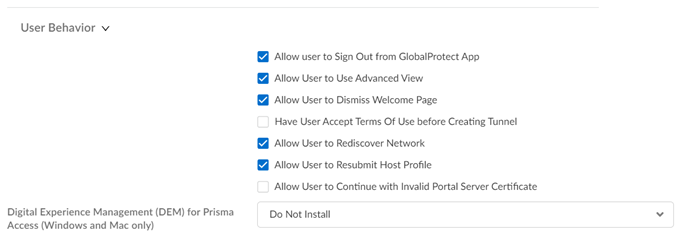
User Behavior Settings
|
User Behavior settings include:
| ||||||||||
|
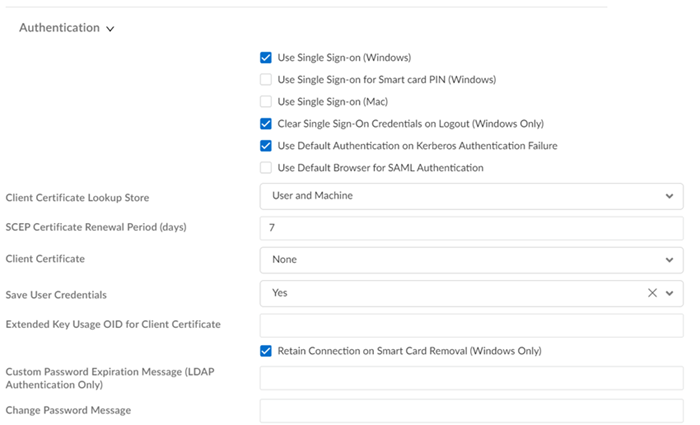
Authentication Settings
|
Authentication settings include:
| ||||||||||
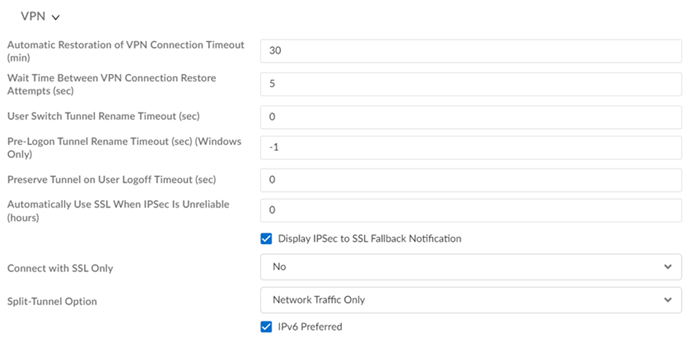
|
VPN Settings
|
Configure VPN timeout and tunnel settings:
| ||||||||||
|
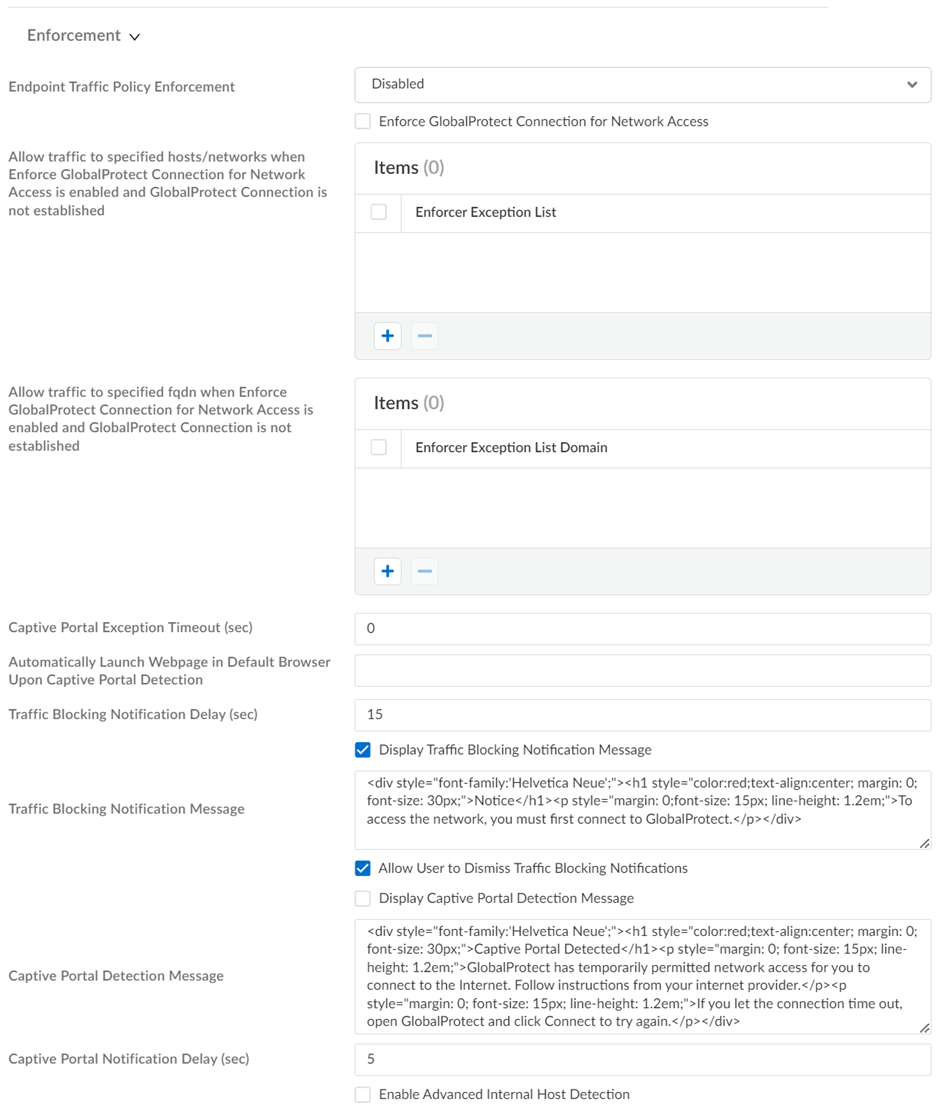
Enforcement Settings
|
Enforce settings for specified traffic:
| ||||||||||
|
Connection Behavior Settings
| Connection Behavior settings include: 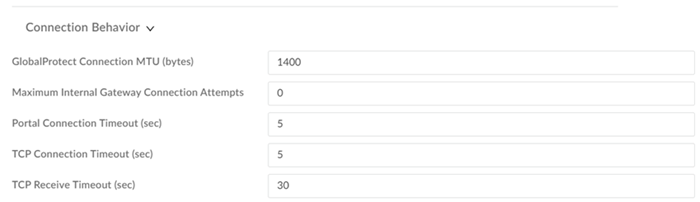
| ||||||||||
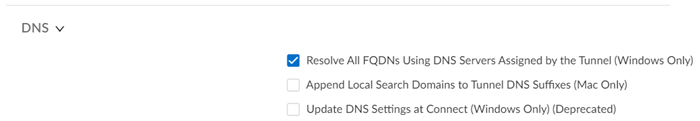
|
DNS Settings
|
DNS settings include:
| ||||||||||
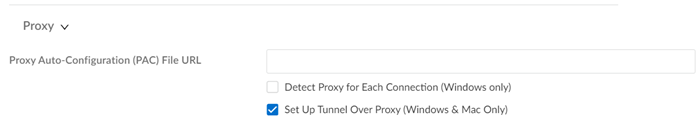
|
Proxy Settings
|
Specify the Proxy Auto-Configuration (PAC) File
URL that you want to push to the endpoint to
configure proxy settings. The maximum URL length is 256
characters. The following Proxy Auto-Configuration (PAC) File
URL methods are supported:
| ||||||||||
|
MFA Settings
|
MFA settings include:
| ||||||||||
|
Troubleshooting Settings
|
Troubleshooting settings include:
| ||||||||||
|
Device Quarantine Settings
|
Device Quarantine settings include:
| ||||||||||
|
Internal Host Detection
|
If you do not require your mobile users to connect to Prisma
Access when they are on the internal network, enable internal
host detection to enable the GlobalProtect app to determine if
it is on an internal or external network.
When a mobile user connects to Prisma Access, the GlobalProtect
app attempts to do a reverse DNS lookup on the specified
address. If the lookup fails, the GlobalProtect app determines
that it is on the external network and then initiates a
connection to Prisma Access.
| ||||||||||
|
Enable
Internal Host Detection
|
If you
want the GlobalProtect app will retry network discovery when an
internal gateway and internal host detection are configured
without an external gateway and internal host detection fails,
set the Enable Intelligent Internal Host
Detection parameter to yes.
| ||||||||||
|
Gateways
|
By default, all the gateways in your Prisma Access locations are
available to users. If you have additional GlobalProtect
gateways (internal or external) that you’d like your users to be
able to connect to, you can add those gateways here.
| ||||||||||
|
HIP Data Collection
|
Define custom host information profile (HIP) data that you want
the app to collect or exclude from collection. When this option
is enabled, the app collects data from devices running Windows,
Mac, or Linux operating systems.
For example, a custom check could enable you to know whether a
certain application is installed or running on an endpoint.The
data that you define to be collected in a custom check is
included in the raw host information data that the GlobalProtect
app collects and then submits to Prisma Access when the
appconnects.
To monitor the data collected with custom checks, create a HIP
object. You can then add the HIP object to a HIP profile to use
the collected data to match to endpoint traffic and enforce
security rules.
Go to ConfigurationNGFW and Prisma AccessObjectsHIP and HIP Objects or
HIP Profiles. Select the Prisma AccessMobile Users ContainerGlobalProtect configuration scope.
| ||||||||||
|
Timeout Settings
|
| ||||||||||
|
Source IP Address Enforcement for Authentication Cookies
|
Configure VPN connecting
setting and authentication cookie usage restrictions for an
enhanced security posture.
| ||||||||||