Prisma Access
Integrate Prisma Access with Cisco Catalyst SD-WAN
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Integrate Prisma Access with Cisco Catalyst SD-WAN
Learn how to integrate Prisma Access automatically with Cisco Catalyst
SD-WAN.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can onboard a remote network using IPSec tunnels between Cisco Catalyst SD-WAN, formerly known as
Viptela SD-WAN, and Prisma Access automatically or manually. When you enable a
Cisco Catalyst SD-WAN for the integration, Prisma Access creates remote networks for
devices, based on the topology you configure, using IPSec tunnels. Prisma Access
identifies eligible interfaces on the Cisco Catalyst SD-WAN devices, and you can
select the interface to onboard the remote network using the tunnel.
To onboard the Cisco Catalyst SD-WAN networks manually, see Integrate Prisma Access with Catalyst
SD-WAN (Manual Integration).
Ensure you meet the following requirements before you integrate Prisma Access with
Cisco Catalyst SD-WAN:
| Product | Requirement |
|---|---|
|
Prisma Access
|
|
|
Cisco Catalyst SD-WAN
|
|
Cisco Catalyst SD-WAN supports the following deployment architectures for use with
Prisma Access.
| Use Case | Architecture |
|---|---|
| Securing traffic from each branch site with 1 WAN link (Type 1) |

|
| Securing branch and HQ sites with active/backup SD-WAN connections |
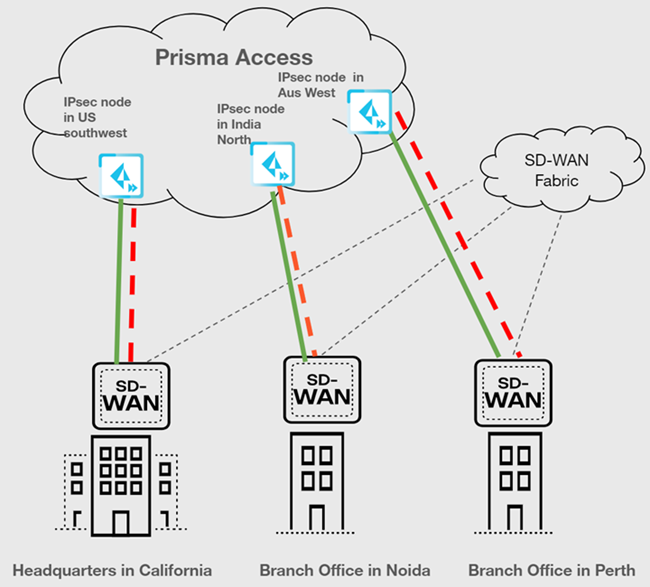
|
| Securing branch and HQ sites with active/active SD-WAN connections |
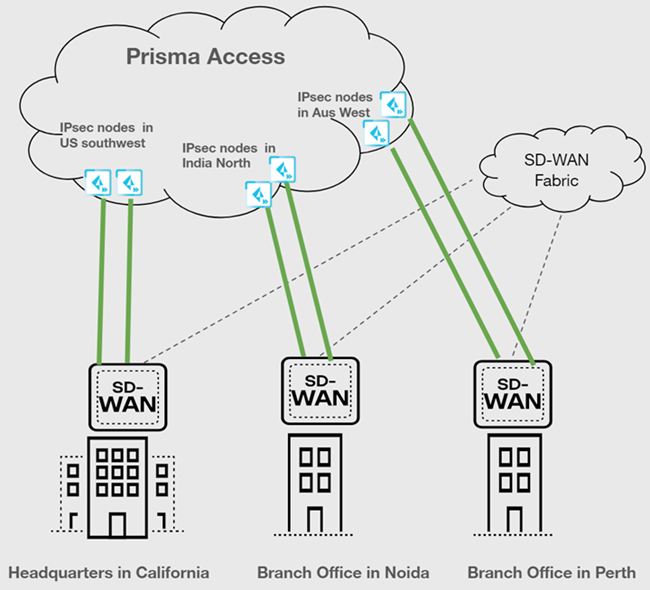
|
| Securing branch and HQ sites with SD-WAN edge devices in HA mode |
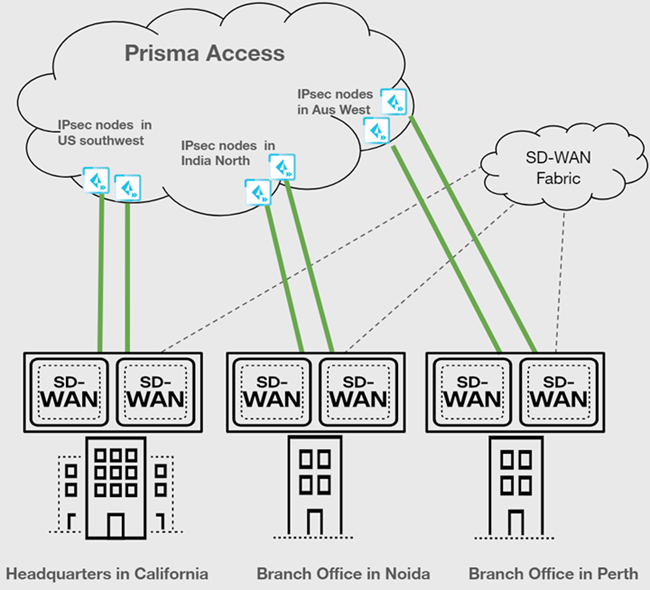
|
| Securing traffic from one device using active/active WAN links, that is, 2 WAN links from the device, both will be active on different compute regions |
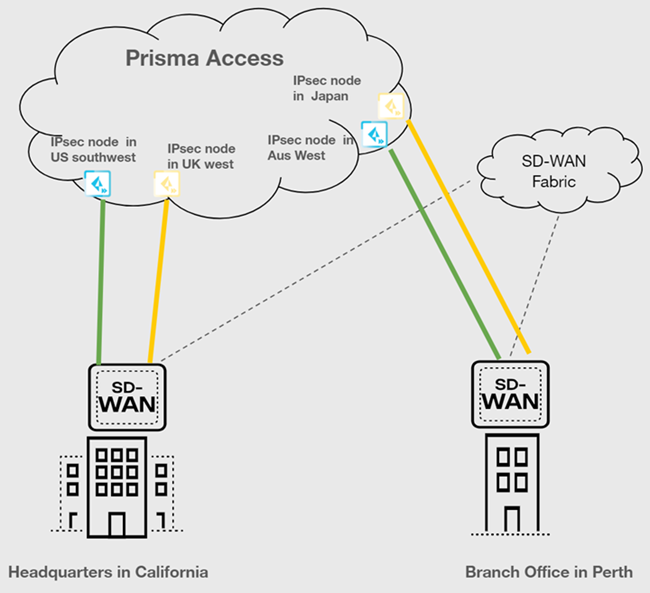
|
For any other deployment architectures, use the manual integration
workflow.
Before you begin, ensure you configure the Cisco Catalyst SD-WAN devices based on the
requirements mentioned above. To secure a Cisco Catalyst SD-WAN with Prisma Access,
complete the following steps.
- In the Cisco vManage dashboard, go to ConfigurationTemplatesDevice Templates.Update the template descriptions of your devices based on the type of redundancy.
Topology Devices WAN Links (VPN 0) Tunnel Type Device Template Description Updates Single WAN Single Device 1 WAN Link 1 Tunnel to single Prisma Access region/IPSec Termination NodeNo changes Active/active tunnels Single Device 1 WAN Link 2 Tunnels (on the same WAN) to 2 different Prisma Access Regions/IPSec Termination NodesAppend PA-AA to the description 2 WAN Links Different Prisma Access regions or different IPSec Termination Node in the same region Append PA-AA to the description Active/backup tunnels Single Device 2 WAN Links Primary/Secondary on Prisma Access to same remote network Append PA-AB to the description 2 WAN Links Different regions/IPSec Termination Nodes in Prisma Access Append PA-AB to the description In Prisma Access, if you have not already, allocate bandwidth for Prisma Access locations.- Go to SettingsPrisma Access SetupRemote NetworksBandwidth Management.Edit the Assigned Bandwidth for the remote network’s compute location.Push the changes.Go to Cisco Catalyst SD-WAN Integration with Prisma Access settings.
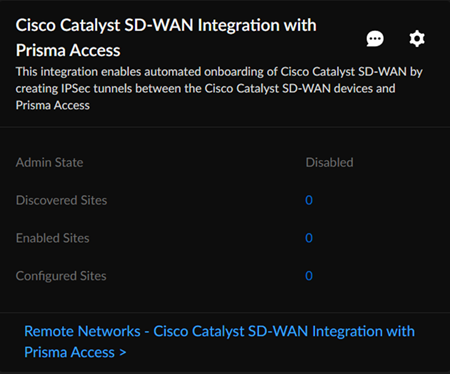
- Select System SettingsIntegrations.Locate Cisco Catalyst SD-WAN Integration with Prisma Access.
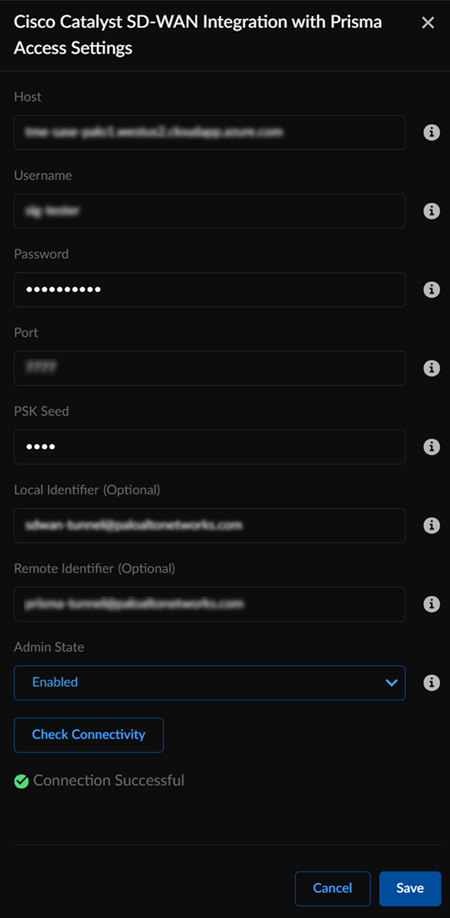
![]() Enter the information needed to check the connectivity between Prisma Access and Cisco Catalyst SD-WAN by editing the Settings.
Enter the information needed to check the connectivity between Prisma Access and Cisco Catalyst SD-WAN by editing the Settings.- Enter the hostname, username, and the password.Enter the PSK Seed, which is a string used to derive pre-shared keys (PSKs) per tunnel.(Optional) Enter an FQDN IKE identifier as the Local Identifier in the following syntax: name@domain.comThis identifier acts as a template to generate a unique ID per tunnel.(Optional) Enter an FQDN IKE identifier different from the local identifier as the Remote Identifier in the following syntax: name@domain.comSet the Admin State as Enabled.You can set Admin State in the following modes:
- Enabled: Enables the integration to discover new devices on Cisco Catalyst SD-WAN that are eligible for tunnel formation with Prisma Access. Additionally, this verifies current configurations.
- Disabled: Disable the integration to remove all configurations created in Prisma Access as well as in Cisco Catalyst SD-WAN, when a connection was set up between them.
- Paused: When you pause the integration, you can no longer add new devices or remove any unconfigured devices. However, the current configurations don't change.
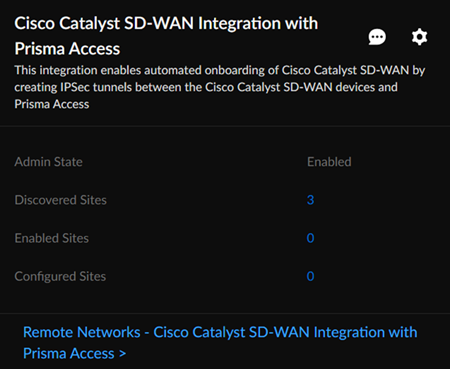
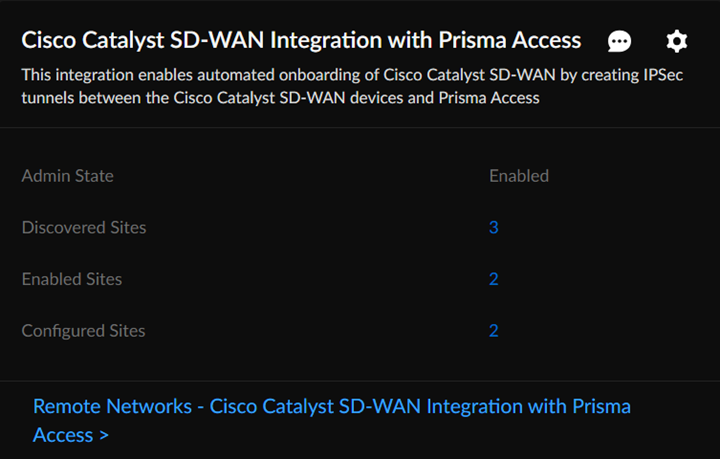
Check Connectivity to verify the connection.![]() Save the changes.You can Save changes only after you Check Connectivity every time you change settings or configurations.After you save the changes, you can see the Cisco Catalyst SD-WAN networks eligible for tunnel formation with Prisma Access in Discovered Sites. Cisco Catalyst SD-WAN networks are displayed as sites here. It might take some time to view the discovered sites.
Save the changes.You can Save changes only after you Check Connectivity every time you change settings or configurations.After you save the changes, you can see the Cisco Catalyst SD-WAN networks eligible for tunnel formation with Prisma Access in Discovered Sites. Cisco Catalyst SD-WAN networks are displayed as sites here. It might take some time to view the discovered sites.![]() Establish the tunnel setup between Prisma Access and Cisco Catalyst SD-WAN devices.
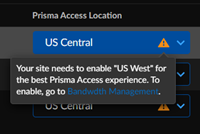
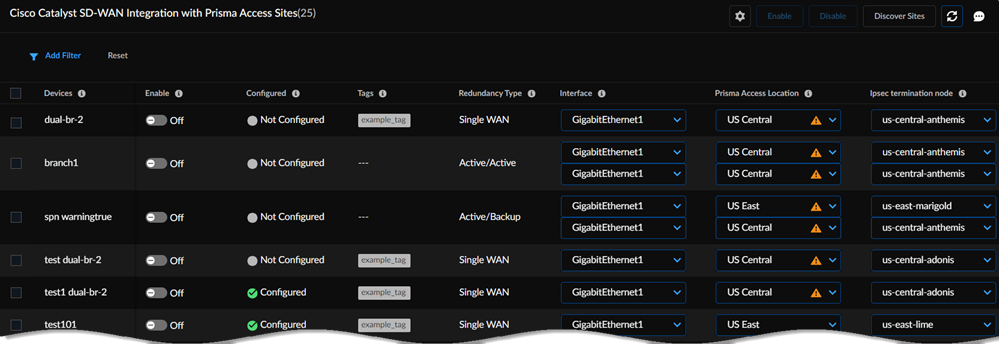
Establish the tunnel setup between Prisma Access and Cisco Catalyst SD-WAN devices.- View the discovered Cisco Catalyst SD-WAN networks and their information by clicking the site count.The integration checks for new Cisco Catalyst SD-WAN networks regularly. You can also initiate an on-demand site discovery.Select the InterfaceBy default, Prisma Access scans for devices and identifies interfaces from the Cisco Catalyst devices that are eligible to form tunnels with Prisma Access.(Optional) Select the nearest Prisma Access Location for the networks.(Optional) Select IPSec Termination Node for each site.If you select the same Prisma Access location for multiple networks, ensure to allocate the bandwidth equally by selecting different IPSec termination nodes for the networks sharing the same Prisma Access location.Based on the type of topology redundancy type, you see the following options to select the location and IPSec termination node.The integration assigns Prisma Access location and IPSec termination nodes automatically. However, you can choose other Prisma Access locations or IPSec termination nodes if needed.
![]()
Redundancy Type Number of Interfaces Number of Prisma Access Locations to Select Number of IPSec Termination Nodes to Select Single WAN 1 11 Active/active tunnels 222After you enable the device, Prisma Access creates 2 remote networks. Select the same IPSec termination nodes for both locations. These conditions are valid for HA deployments as well.Active/backup tunnels 2 (Primary/Secondary on Prisma Access to same remote network)The interface at the top is the primary tunnel.22After you enable the device, Prisma Access creates 1 remote network. This configuration provides redundancy at internet circuit level.2 (Different regions/IPSec Termination Nodes in Prisma Access)The interface at the top is the primary tunnel. The feature template you configure Cisco Catalyst SD-WAN devices assigns the interface as active or backup.2 2When the primary tunnel has connectivity issues, Prisma Access establishes a connection with the failover path, which is the secondary or backup tunnel.Select the Cisco Catalyst SD-WAN device and toggle the Enable option to establish a tunnel formation with Prisma Access.![]() Update the changes.You can view all the Enabled Sites and Configured Sites in Cisco Catalyst SD-WAN Integration with Prisma Access.
Update the changes.You can view all the Enabled Sites and Configured Sites in Cisco Catalyst SD-WAN Integration with Prisma Access.![]() When you click a site count, the hyperlink takes you to a filtered list of sites based on the site count you click. For example, if you click the site count of enabled sites, the list shows only the sites that are enabled and not all discovered sites.Verify the changes in Prisma Access.
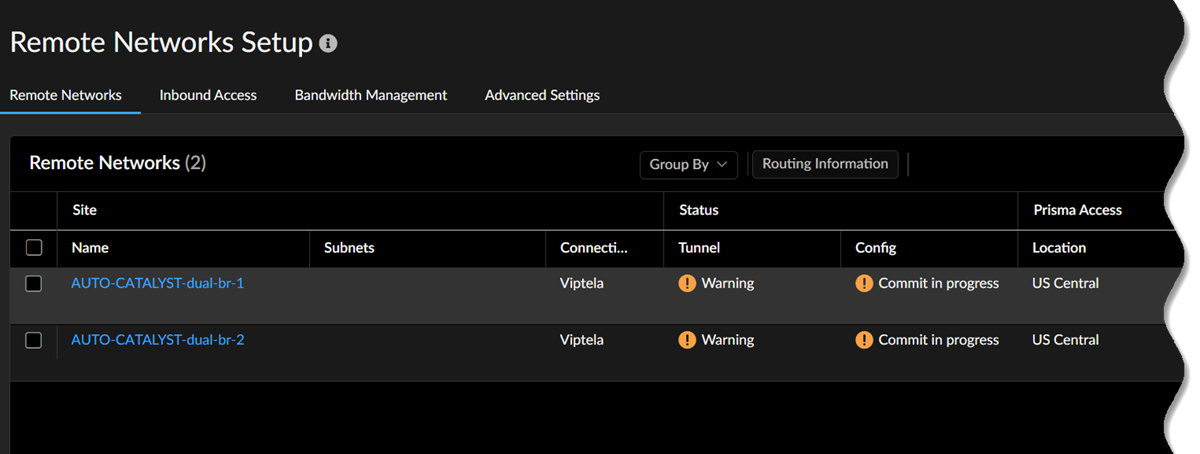
When you click a site count, the hyperlink takes you to a filtered list of sites based on the site count you click. For example, if you click the site count of enabled sites, the list shows only the sites that are enabled and not all discovered sites.Verify the changes in Prisma Access.- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote Networks.Alternatively, you can click Remote Networks - Cisco Catalyst SD-WAN Integration with Prisma Access.Verify the tunnel status. The integration creates remote networks automatically. Such remote networks have names in the following syntax: AUTO-CATALYST-Device_Name
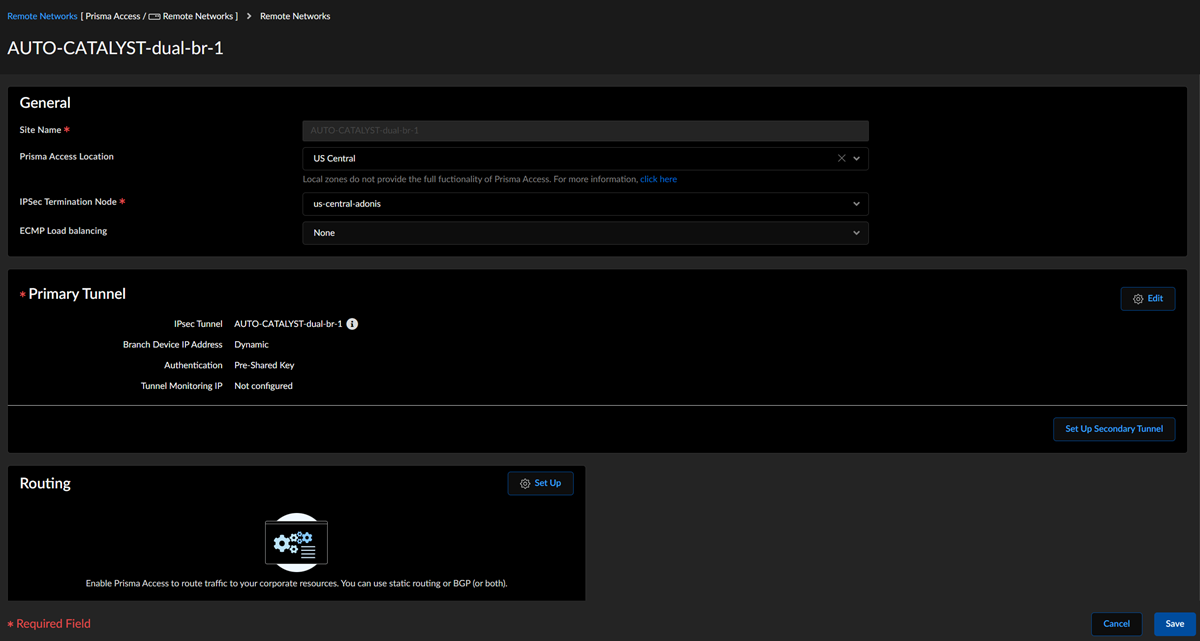
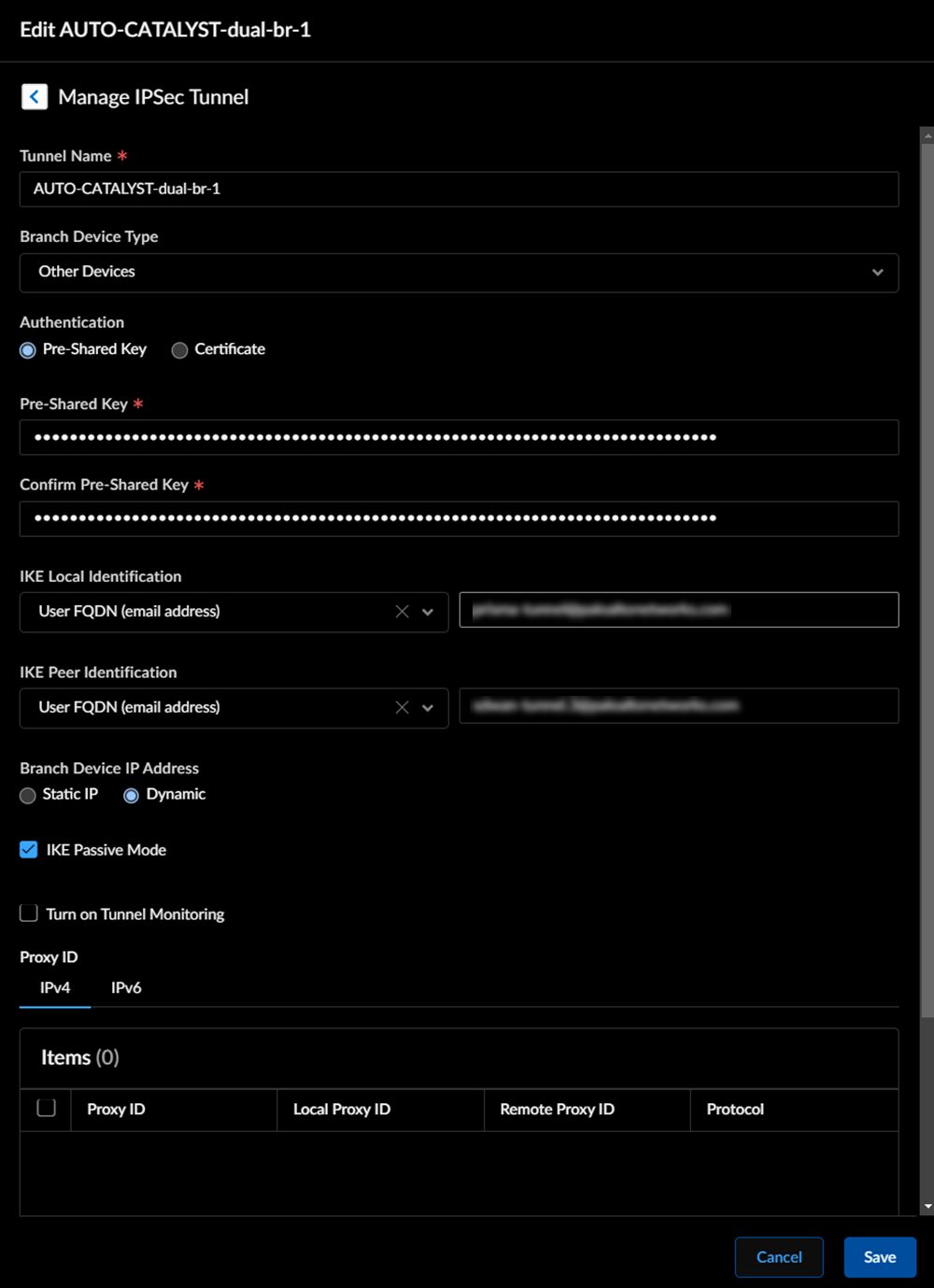
![]() The configuration status of Cisco Catalyst SD-WAN devices takes some time to be In sync.View the IPSec Tunnel, IKE gateway, IKE Crypto profile, and IPSec Crypto profile details.Select the remote network site to view these details.
The configuration status of Cisco Catalyst SD-WAN devices takes some time to be In sync.View the IPSec Tunnel, IKE gateway, IKE Crypto profile, and IPSec Crypto profile details.Select the remote network site to view these details.![]() IPSec Tunnel details:
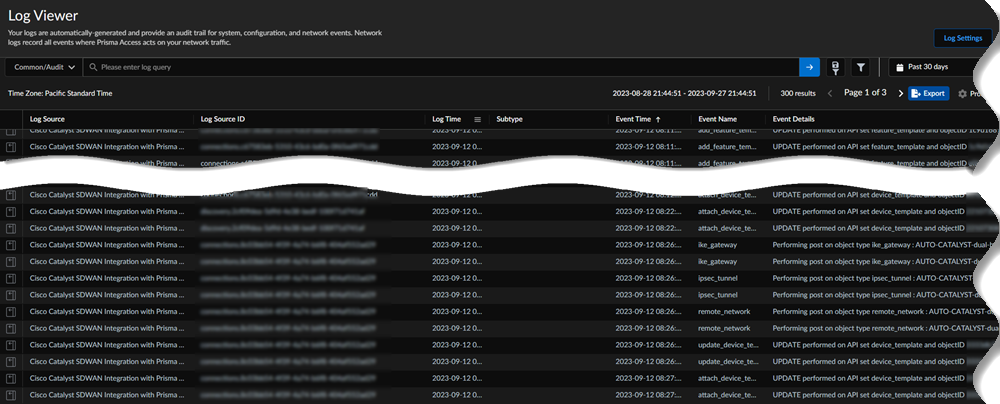
IPSec Tunnel details:![]() Select Log ViewerCommonAudit to view Cisco Catalyst SD-WAN Integration with Prisma Access logs.The logs specify if the changes were made in Prisma Access or in the Cisco Catalyst SD-WAN.
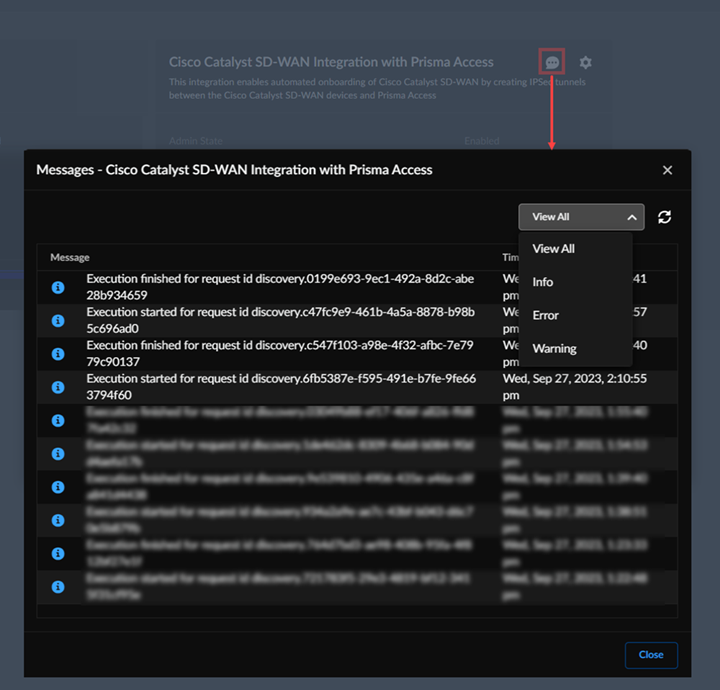
Select Log ViewerCommonAudit to view Cisco Catalyst SD-WAN Integration with Prisma Access logs.The logs specify if the changes were made in Prisma Access or in the Cisco Catalyst SD-WAN.![]() (Optional) In the Cisco Catalyst SD-WAN integration app, view information, errors, or warnings in Messages.
(Optional) In the Cisco Catalyst SD-WAN integration app, view information, errors, or warnings in Messages.![]() See Troubleshoot Integration Errors to troubleshoot more errors.Verify the Cisco Catalyst SD-WAN configurations in Cisco vManage.
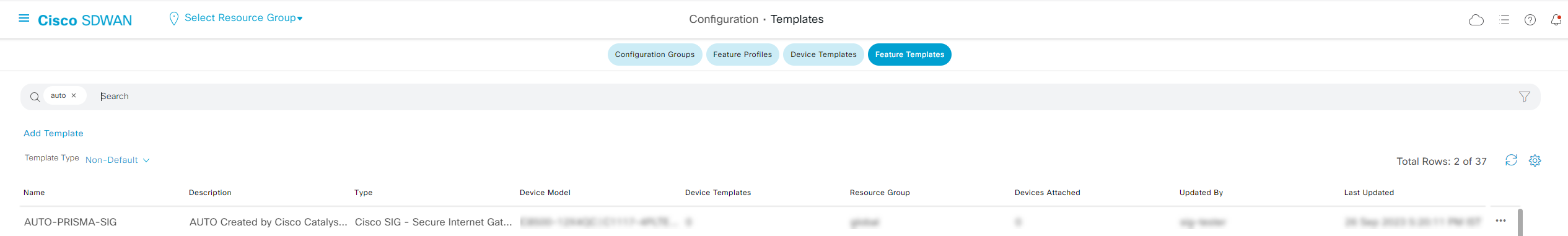
See Troubleshoot Integration Errors to troubleshoot more errors.Verify the Cisco Catalyst SD-WAN configurations in Cisco vManage.- Log in to the Cisco SD-WAN dashboard, and select MonitorDevices.Select ConfigurationTemplatesFeature Templates.The integration creates secure internet gateway (SIG) templates. The SIG template stores details of the IPSec tunnel and IKE values. Don't update these SIG templates manually.
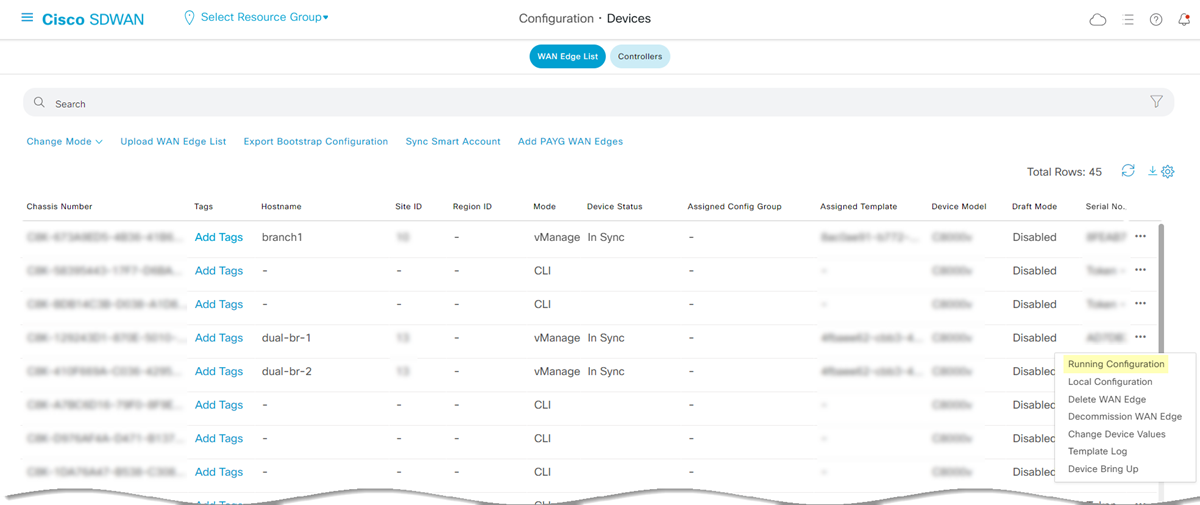
![]() If there are multiple devices that are part of a device template, configure all devices for tunnel formation with Prisma Access.Check the running configuration for the interfaces.In Cisco vManage, select Configuration Devices WAN Edge List.
If there are multiple devices that are part of a device template, configure all devices for tunnel formation with Prisma Access.Check the running configuration for the interfaces.In Cisco vManage, select Configuration Devices WAN Edge List.![]() View the Running Configuration of the corresponding devices.
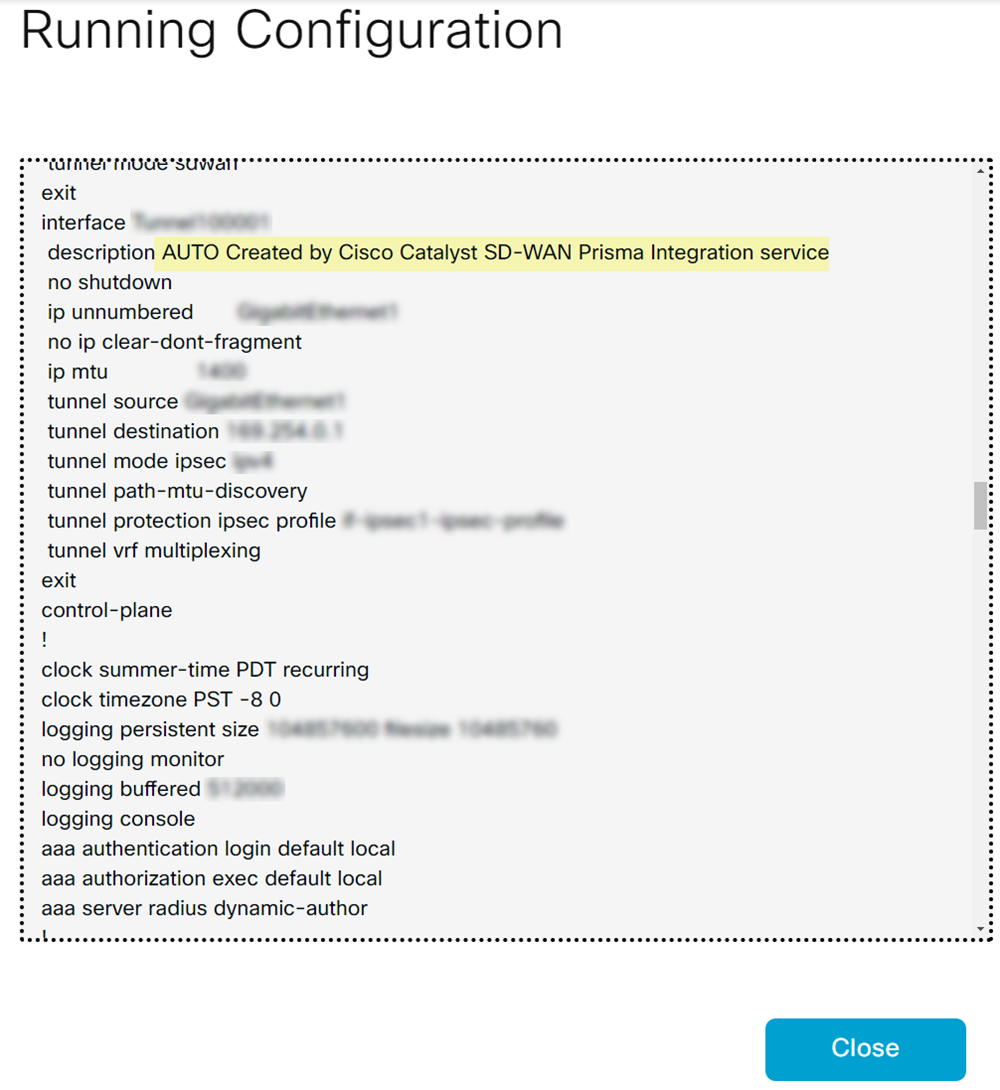
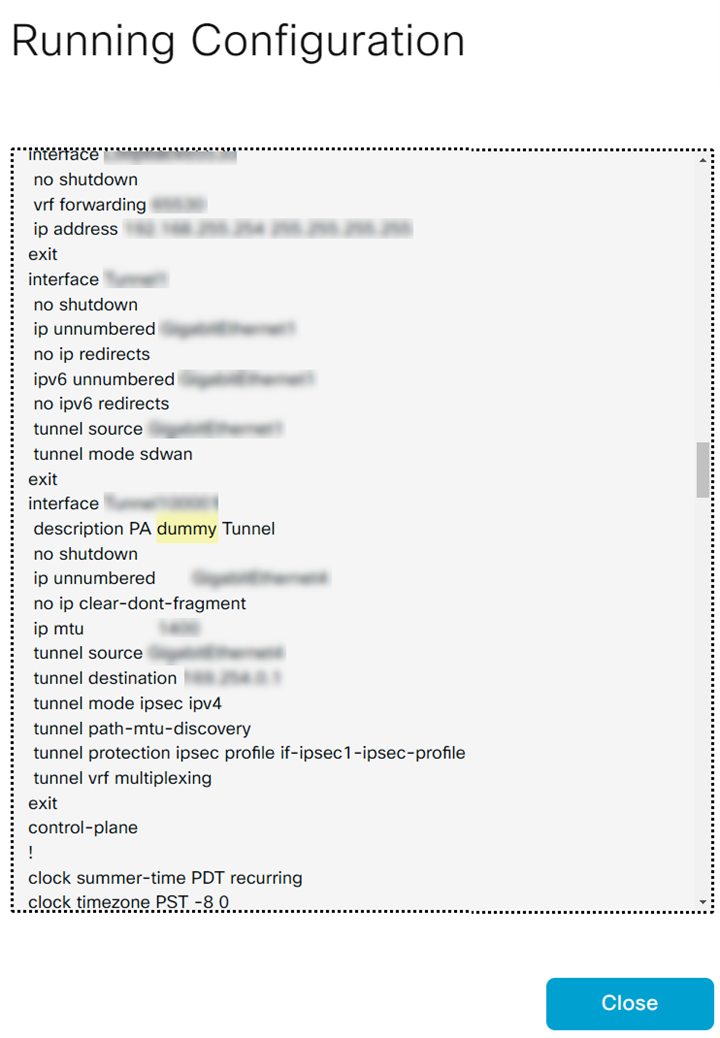
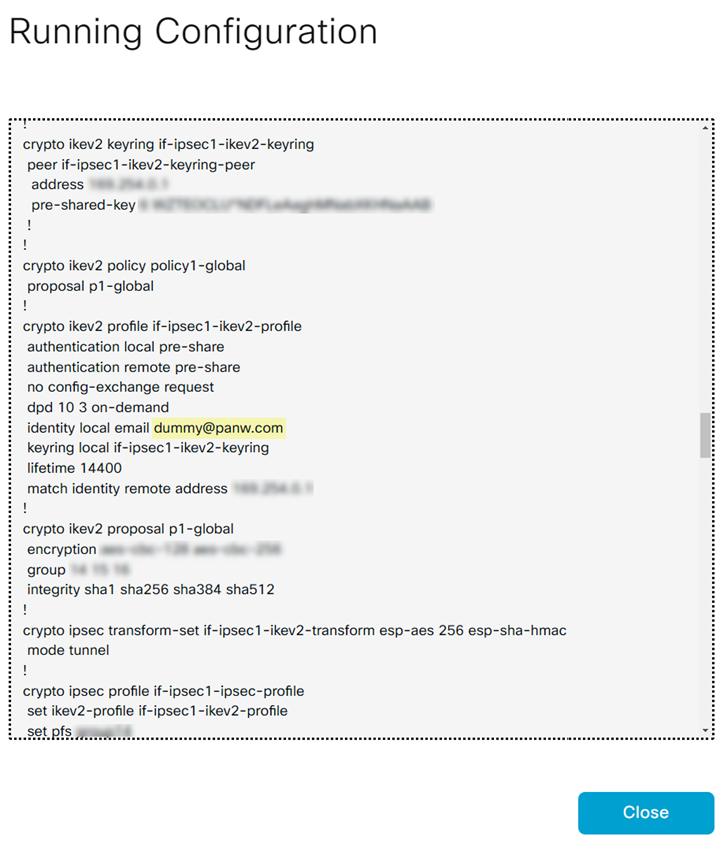
View the Running Configuration of the corresponding devices.![]() When you have multiple devices under a device template, devices that are not enabled will have dummy values.
When you have multiple devices under a device template, devices that are not enabled will have dummy values.![]()
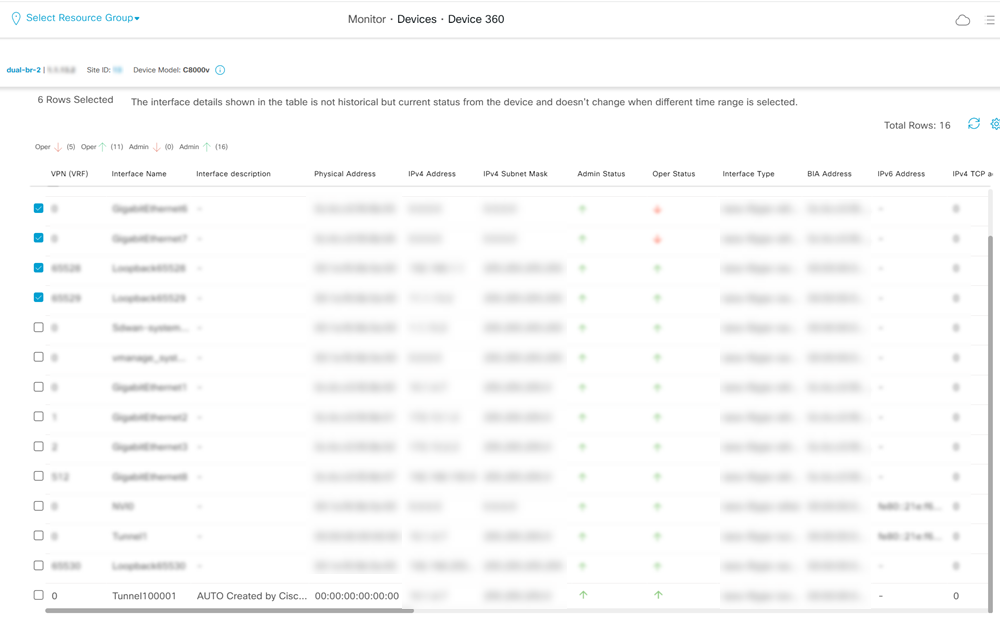
![]() To avoid dummy values on other devices, move the devices, for those you want to enable connectivity, to a separate device template and enable the connectivity for each device in this device template. If you enable devices with dummy values, Prisma Access overwrites those dummy values with the tunnel configuration values. Prisma Access populates dummy values for the description, tunnel source interface, tunnel destination, pre-shared secret, and IKE local ID.If you add a new device to the device template that has a SIG, configure a few dummy values and attach the device to the device template. After the integration discovers this device, enable it.Verify the tunnel status in Cisco Catalyst SD-WAN Manager.Log in to the Cisco SD-WAN dashboard, and select MonitorDevices. Select the device and view the Interface. Verify the admin status and operational status of the tunnel that was auto created for this device.
To avoid dummy values on other devices, move the devices, for those you want to enable connectivity, to a separate device template and enable the connectivity for each device in this device template. If you enable devices with dummy values, Prisma Access overwrites those dummy values with the tunnel configuration values. Prisma Access populates dummy values for the description, tunnel source interface, tunnel destination, pre-shared secret, and IKE local ID.If you add a new device to the device template that has a SIG, configure a few dummy values and attach the device to the device template. After the integration discovers this device, enable it.Verify the tunnel status in Cisco Catalyst SD-WAN Manager.Log in to the Cisco SD-WAN dashboard, and select MonitorDevices. Select the device and view the Interface. Verify the admin status and operational status of the tunnel that was auto created for this device.![]()
On-Demand Site Discovery
You can initiate network discoveries anytime to view new networks added in the Cisco vManage dashboard. You can also initiate network discoveries to resolve any misconfiguration in the integration-created objects. To initiate on-demand network discovery, perform the following steps:- Select WorkflowsIntegrationsPrisma Access.Locate Cisco Catalyst SD-WAN Integration with Prisma Access.View the discovered Cisco Catalyst SD-WAN networks and their information by clicking the site count.Discover Sites to identify new eligible Cisco Catalyst SD-WAN networks when required.
Troubleshoot Integration Errors
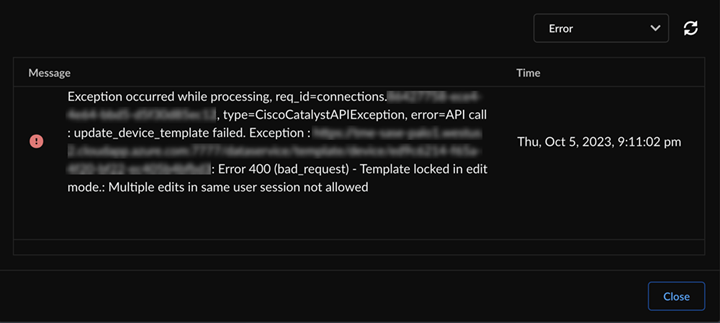
Audit logs provide records of administrators' configuration changes in the integration. You can use these logs for the compliance and troubleshooting purposes. You can also view the Messages in the integration settings for information, errors, and warnings. - If Cisco Catalyst SD-WAN locks a template, don't perform any manual operations on the integration-created objects to avoid template lock due to multiple sessions.
- If your template is locked in edit mode while editing, relog in after
sometime and try to edit the template. If the issue persists, contact Cisco
Systems support.
![]()
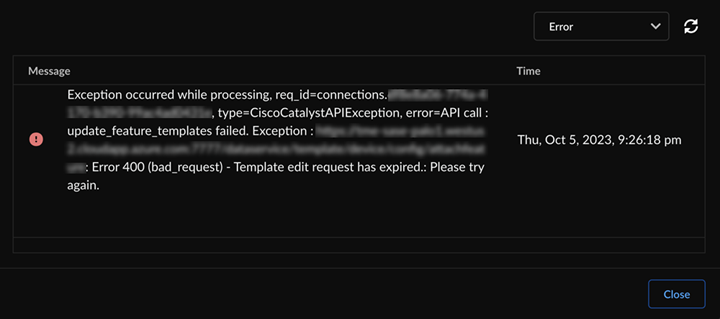
- If your template edit request session expires, re-log in after sometime and
try to edit the template. If the issue persists, contact Cisco Systems
support.
![]()
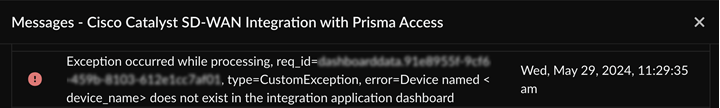
- If your device does not exist in Cisco Catalyst SD-WAN Manager, try discovering the missing device.
![]()