Prisma Access
Configure Privileged Remote Access Settings
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure Privileged Remote Access Settings
Learn how to set up general Privileged Remote Access settings such as enabling PRA and selecting the Cloud Identity Engine directory and authentication
profile.
To begin to onboard your users for Privileged Remote Access (PRA), you need to configure
general PRA settings such as enabling PRA
and selecting the Cloud Identity Engine directory and authentication profile to use
with PRA.
Before you configure the PRA settings, be sure to complete the
following prerequisites:
- Create your first tenant and activate the Cloud Identity Engine.
- Review the Cloud Identity Engine directory and authentication profile settings. You can use existing Cloud Identity Engine configurations for directory and authentication profiles. PRA supports only SAML 2.0 authentication with the Cloud Identity Engine. Local directory for Cloud Identity Engine isn’t supported.
- Make sure that you have a DNS server accessible via the Service Connection that can resolve the hostnames of the RDP, SSH, and VNC apps.
- Configure at least one GlobalProtect Mobile User connection method, and select at least one Prisma Access location to support mobile users.
- Activate the add-on license for PRA by clicking the activation link in the email you received from Palo Alto Networks.
To configure PRA settings:
- Navigate to the PRA Overview page.
- For Prisma Access (Managed by Strata Cloud Manager):
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationPrivileged Remote AccessOverview.
- For Prisma Access (Managed by Panorama):
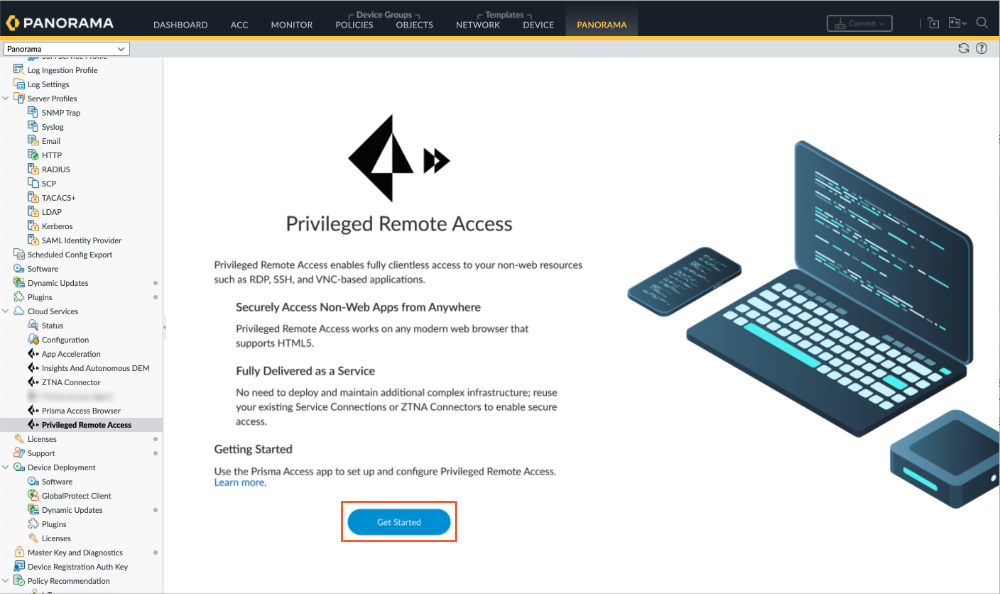
- Launch Privileged Remote Access from the Cloud Services plugin on Panorama by selecting PanoramaCloud ServicesPrivileged Remote Access.
- Click Get Started.
![]()
- Select ConfigurationPrivileged Remote AccessOverview.
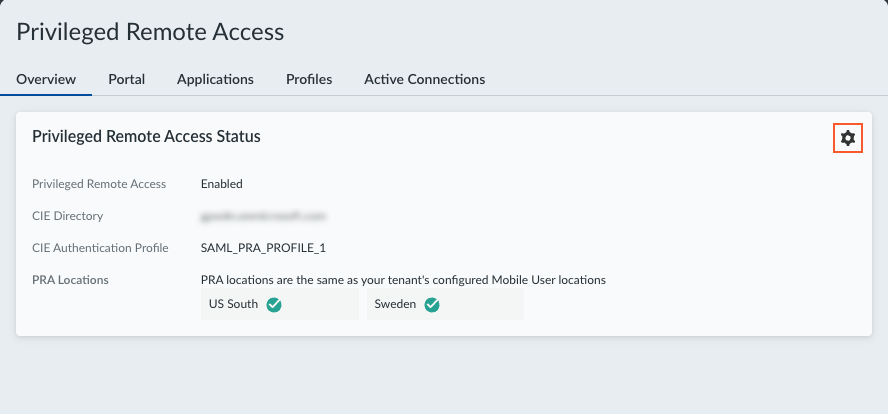
Edit the PRA settings.The PRA Overview page shows the status of your PRA deployment, such as the Cloud Identity Engine directory and authentication profile settings, and the locations where PRA will be deployed.![]() Enable PRA by enabling Enable/Disable Privileged Remote Access.
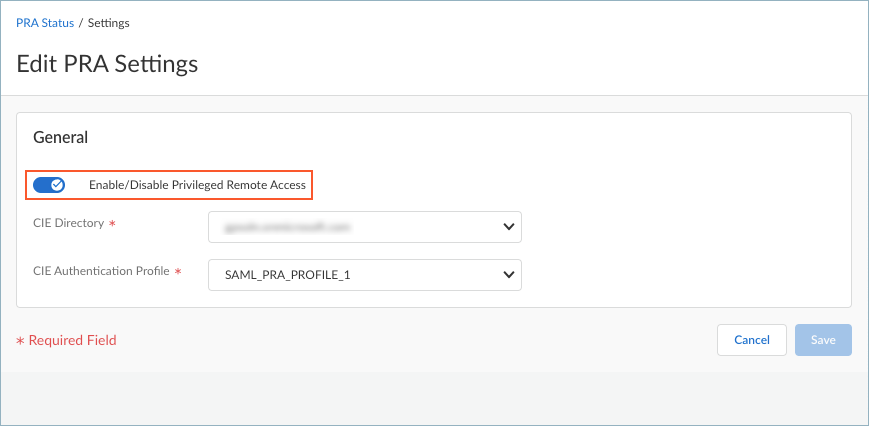
Enable PRA by enabling Enable/Disable Privileged Remote Access.![]() Set up user authentication for Privileged Remote Access (PRA) so that only authorized users can remotely log in to the PRA to access their apps. PRA works with the Cloud Identity Engine to authenticate users using identity providers like the Active Directory (AD) service and to retrieve the user-group mapping from the AD service.
Set up user authentication for Privileged Remote Access (PRA) so that only authorized users can remotely log in to the PRA to access their apps. PRA works with the Cloud Identity Engine to authenticate users using identity providers like the Active Directory (AD) service and to retrieve the user-group mapping from the AD service.- Select the CIE Directory from which to retrieve the user-group mapping.Select a CIE Authentication Profile, which is the SAML authentication profile that validates the login credentials of end users who access PRA.Save your settings.
- For Prisma Access (Managed by Strata Cloud Manager):