Prisma Access
GlobalProtect Pre-Logon
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
GlobalProtect Pre-Logon
Enable the pre-logon connect method for GlobalProtect mobile users.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Pre-logon is a connect method that establishes a VPN tunnel before a user
logs in. The purpose of pre-logon is to authenticate the endpoint, not the user, and
enable domain scripts or other tasks to run as soon as the endpoint powers on. Machine
certificates enable the endpoint to establish a VPN tunnel to the GlobalProtect gateway.
A common practice for IT administrators is to install the machine certificate while
staging the endpoint for the user. A pre-logon VPN tunnel uses a generic pre-logon
username because the user has not logged in. To allow endpoints to access resources, you
must create security policy rules that match the pre-logon user. These policy rules
should allow access to only the basic services for starting up the system; for example,
DHCP, DNS, specific Active Directory services, antivirus, or other update services.
After the user authenticates to the gateway, the GlobalProtect app reassigns the VPN
tunnel to that user. The IP address mapping on Prisma Access changes from the
pre-logon endpoint to the authenticated user.
The certificate used for pre-logon authentication resides in the endpoint’s personal
certificate store. Use a trusted third-party CA, self-signed CA, or an internal PKI CA
to issue a machine certificate. You need to configure a machine certificate as an
authentication method to establish a tunnel from an endpoint before logging in to Prisma
Access, and then create a certificate profile that includes the pre-logon CA
certificate.
GlobalProtect Pre-Logon (Strata Cloud Manager)
Learn how to enable the pre-logon connect method for GlobalProtect mobile
users.
Import a Third-Party Root CA Certificate
Use a machine certificate as an authentication method to establish a tunnel from an endpoint
before logging in to Prisma Access.
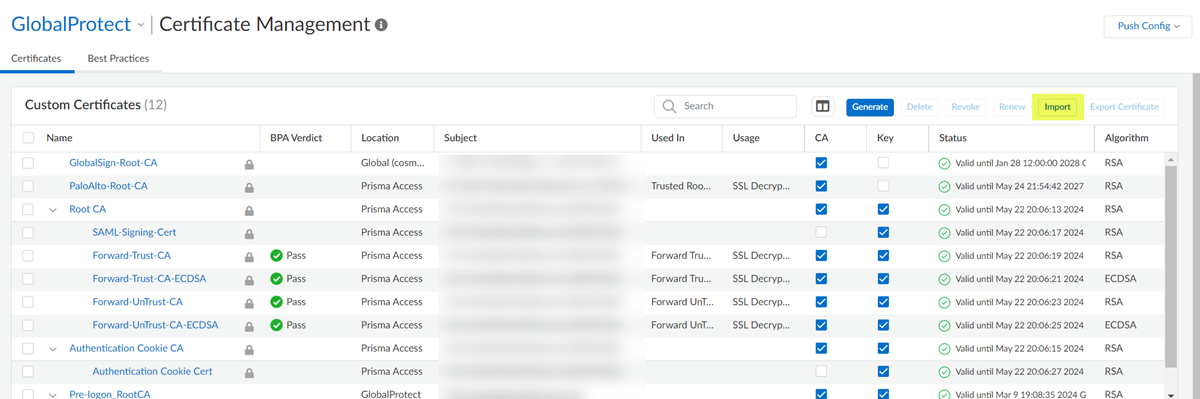
- Select ConfigurationNGFW and Prisma AccessObjectsCertificate Management. Select the Prisma Access configuration scope.Ensure that you're importing the certificate for GlobalProtect mobile users.Import a custom certificate.
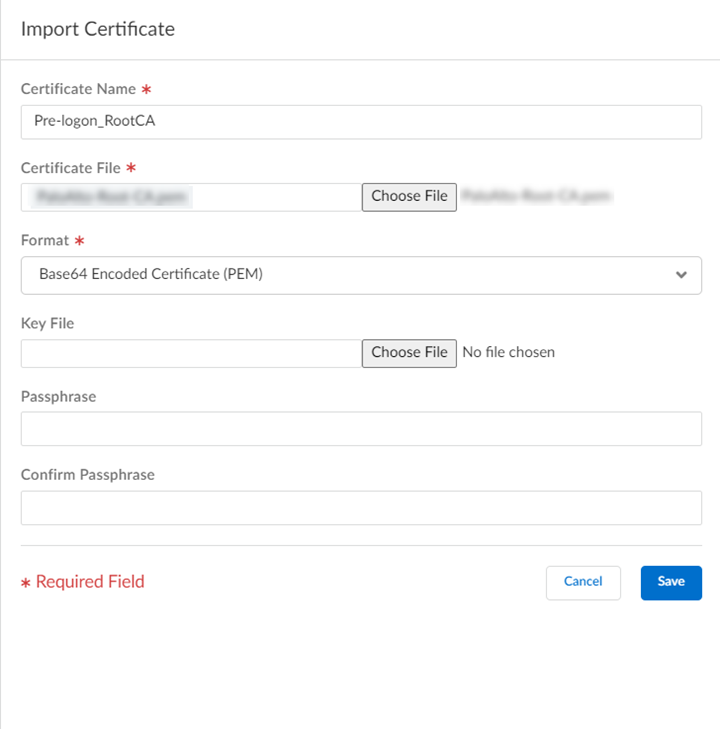
![]() Enter values, and Save the certificate settings.
Enter values, and Save the certificate settings.![]()
Create a Pre-Logon Certificate Profile
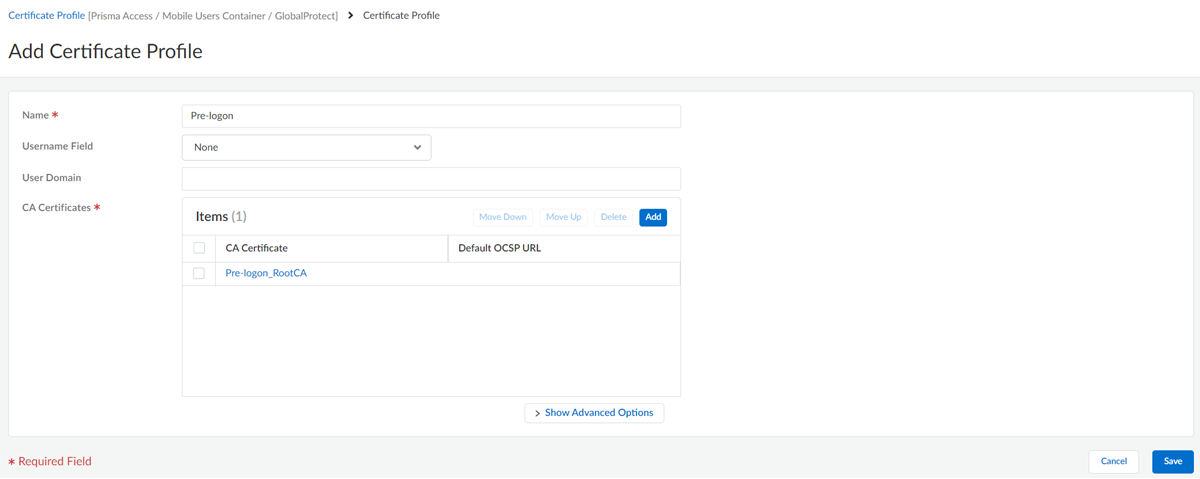
Create a certificate profile and include the self-signed root CA. This CA validates the machine certificate by the GlobalProtect mobile user during pre-logon.- Select ConfigurationNGFW and Prisma AccessObjectsCertificate Management. Select the Prisma Access configuration scope.Add Profile.Enter values.
- Ensure the Username Field is None to prevent the certificate mapping to a user.Username Field can't be None if you authenticate your certificate by any authentication method OR client certificate as mentioned in step 2.Add the root pre-logon CA certificate you imported in step 1.Save the certificate profile settings.
![]()
Configure the GlobalProtect Portal for Pre-Logon
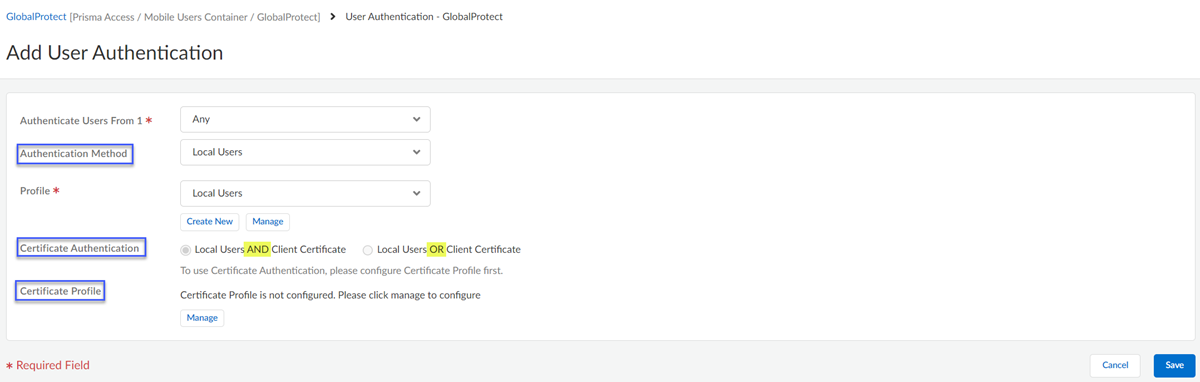
Configure the GlobalProtect portal to authenticate connections with a machine certificate.- Select Configuration NGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectInfrastructure.Edit the user authentication configuration settings.Select an authentication method that GlobalProtect supports, the pre-logon certificate profile you created, and the certificate authentication.Choose any certificate authentication that GlobalProtect supports.
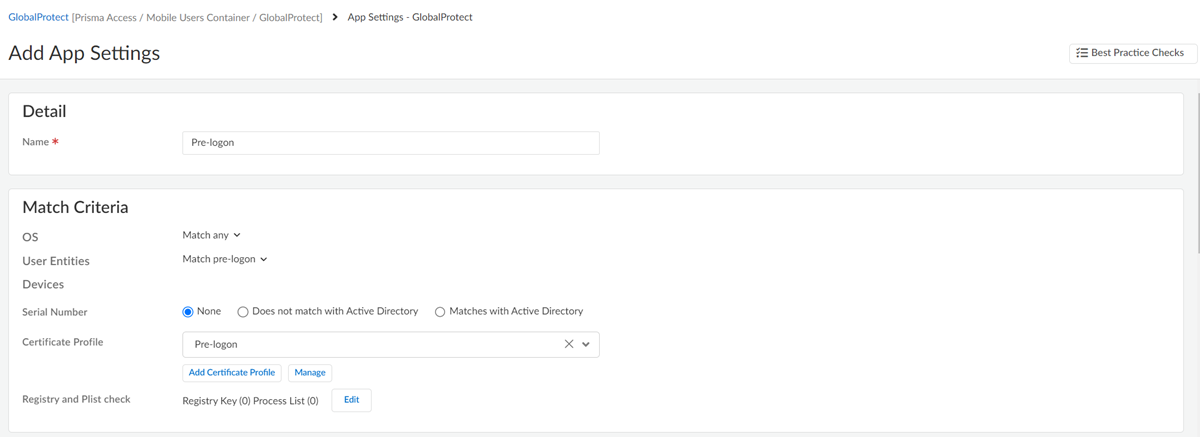
![]() Configure the GlobalProtect app settings to match the pre-logon criteria.
Configure the GlobalProtect app settings to match the pre-logon criteria.- Navigate to the GlobalProtect App tab.Add App Settings.When you enter values, ensure to Match pre-logon user entities and the pre-logon certificate profile.
![]()
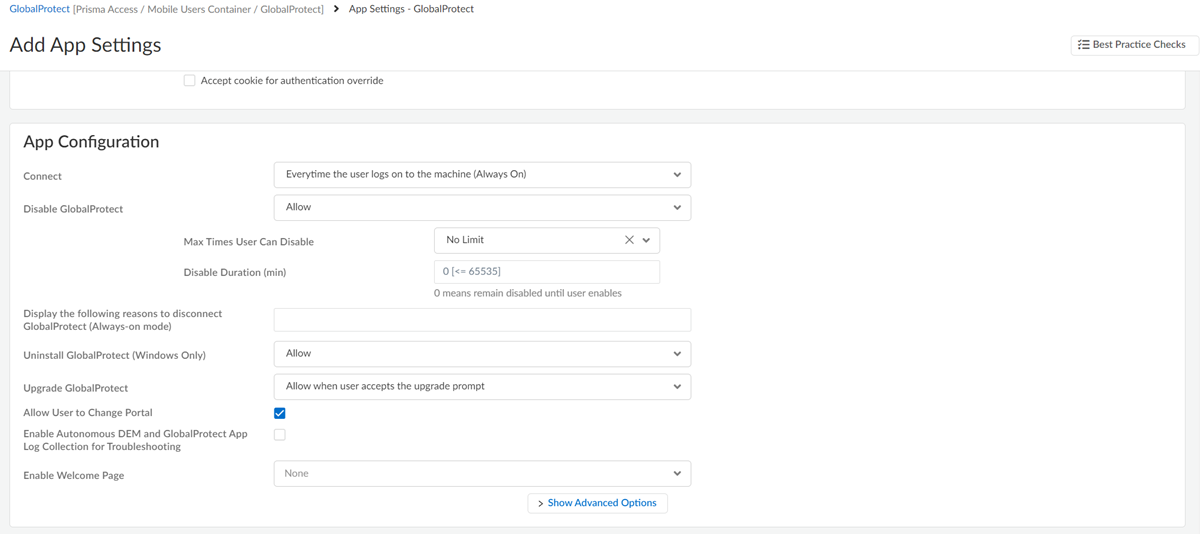
- Select a pre-logon connect method.
![]()
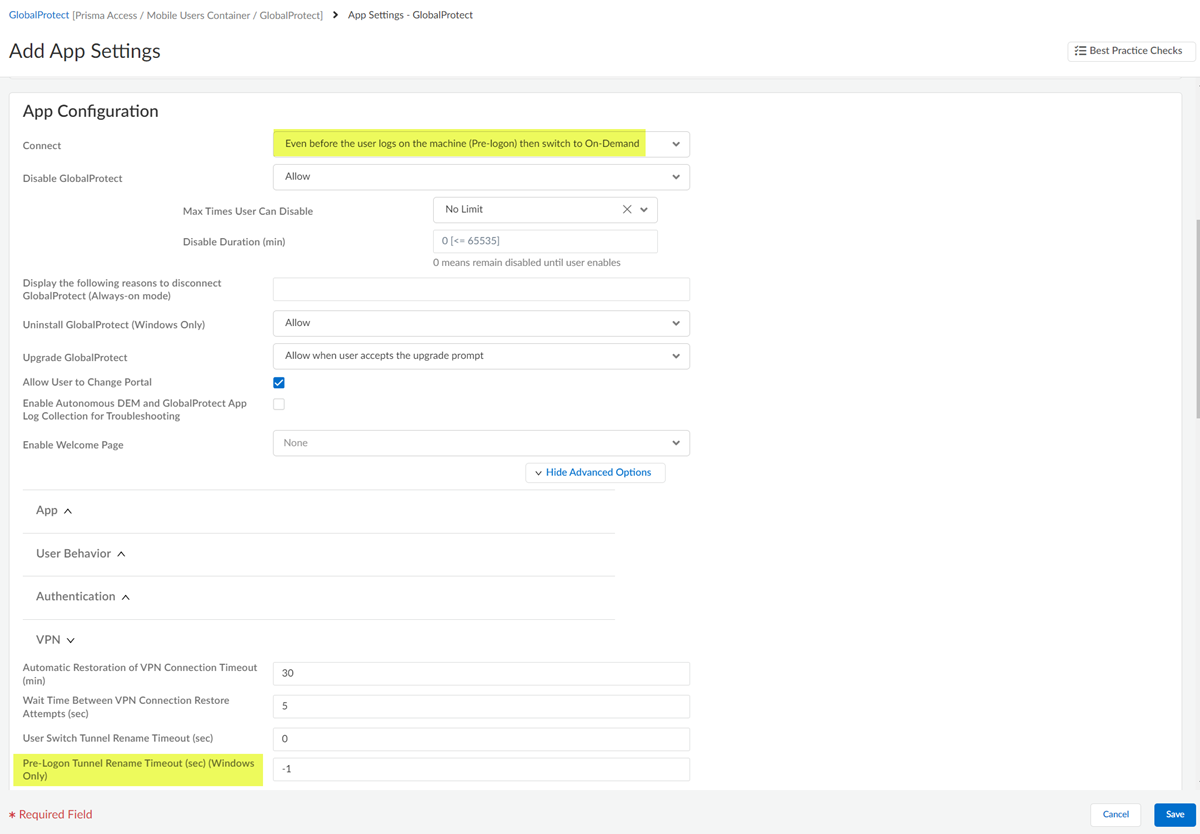
- If you select Even before the user logs on the
machine (Pre-logon) then switch to
On-Demand, set the value of Pre-logon
Tunnel Rename Timeout to –1. View the VPN
advanced options to edit this field.
![]()
Move the pre-logon app setting above other app settings.Edit all other app settings for authenticated users.Update the connect method and the certificate profile.Push the changes to Prisma Access.Install a Machine Certificate—Windows
Install the machine certificate at the endpoint, which is used for authentication.- Export the self-signed root CA certificate from your PKI in Binary Encoded Certificate (DER) format.Transfer the certificate files to a Windows machine.Install the root pre-logon CA certificate in the Trusted Root Certification Authorities store of your local machine.Install the pre-logon machine certificate in the local machine store location.Proceed with the installation, enter the passphrase when prompted, and complete the installation.Connect to the GlobalProtect portal, and delete all cookies from the host.(Optional) Sign out of your machine and view the GlobalProtect logs to verify the pre-logon connection.
GlobalProtect Pre-Logon (Panorama)
Learn how to enable the pre-logon connect method for GlobalProtect mobile users.Configure Pre-Logon Certificate and Profile
Configure a machine certificate as an authentication method to establish a tunnel from an endpoint before logging in to Prisma Access, and then create a certificate profile that includes the pre-logon CA certificate.- Configure a self-signed CA, and use it to generate a machine certificate in the Mobile User template. Go to DeviceCertificate ManagementCertificates.Be sure that you're in the Mobile_User_Template and the Location is set to Shared.
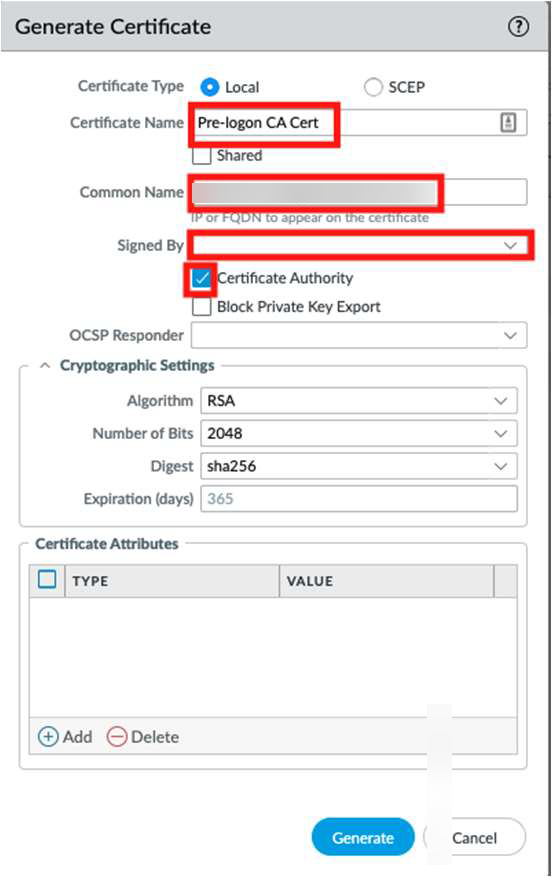
- Name the certificate; for example, Pre-logon CA Cert.Enter a Common Name.The Common Name (CN) is the domain name, such as www.yourdomainname.com, you want to secure with your certificate.Leave the Signed By field blank, and click the Certificate Authority check box.Generate the certificate for use in Pre-logon connections.
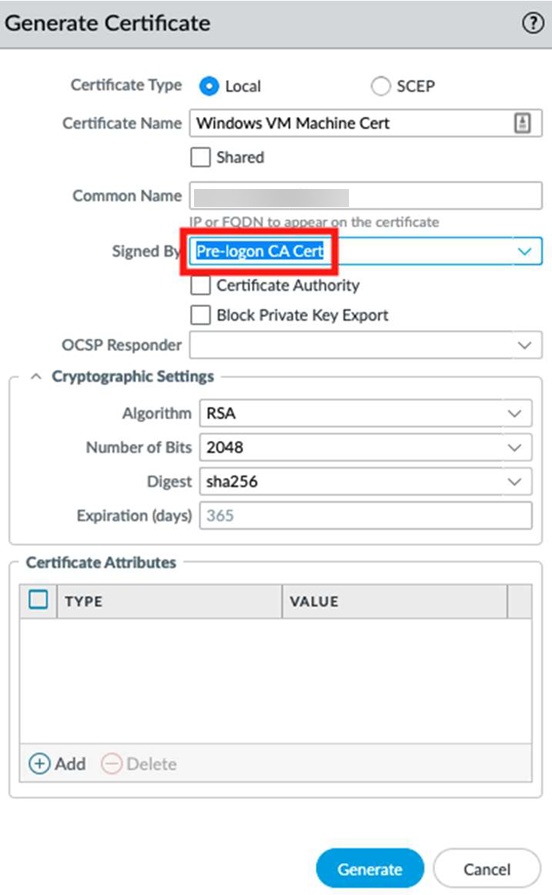
![]() After you configure the self-signed CA, generate the machine certificate.
After you configure the self-signed CA, generate the machine certificate.- Enter a Certificate Name and a Common Name.In the Signed By drop-down, select the Pre-logon CA Cert that you created in step 1.Generate the Windows VM Machine Certificate that you later install on a Windows machine.This certificate is a child of the Pre-logon CA.
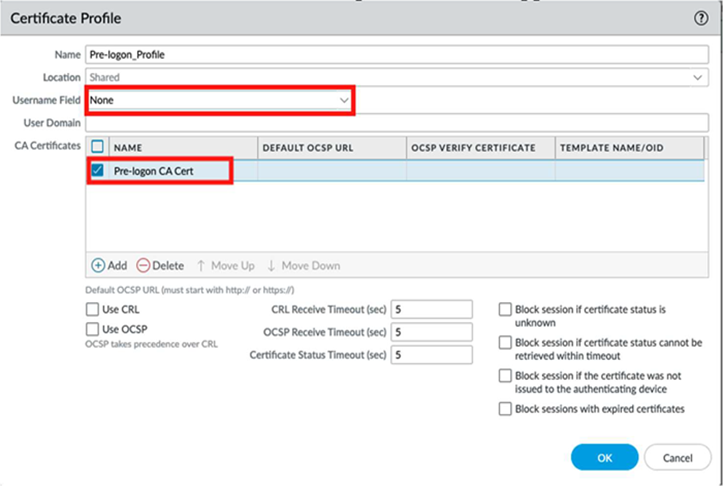
![]() To create a certificate profile that includes the pre-logon CA certificate, go to DeviceCertificate ManagementCertificate Profile.Use this CA to validate the machine certificate presented by the GlobalProtect client during the pre-logon tunnel initialization.Create and name the profile. Ensure that the Username Field is None to prevent the certificate mapping to a user.
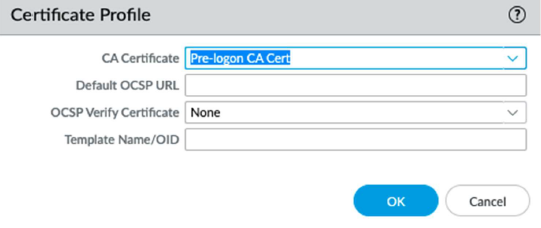
To create a certificate profile that includes the pre-logon CA certificate, go to DeviceCertificate ManagementCertificate Profile.Use this CA to validate the machine certificate presented by the GlobalProtect client during the pre-logon tunnel initialization.Create and name the profile. Ensure that the Username Field is None to prevent the certificate mapping to a user.![]() Under CA Certificates, select Add and select Pre-logon CA Cert from the drop-down.
Under CA Certificates, select Add and select Pre-logon CA Cert from the drop-down.![]() Select OK, and then select OK again.
Select OK, and then select OK again.Configure the GlobalProtect Portal for Pre-Logon
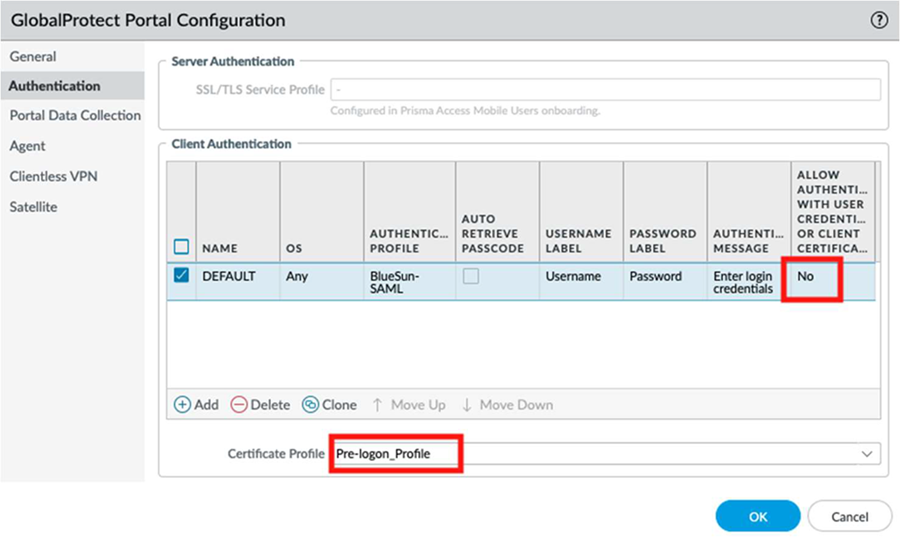
Configure the GlobalProtect portal to authenticate connections with a machine certificate.- Go to NetworkGlobalProtectPortalsGlobalProtect_PortalAuthentication.Under Allow Authentication with User Credentials OR Client Certificate, select No to enforce certificate-based authentication only.For Certificate Profile, select the Pre-logon_Profile you created, and click OK.
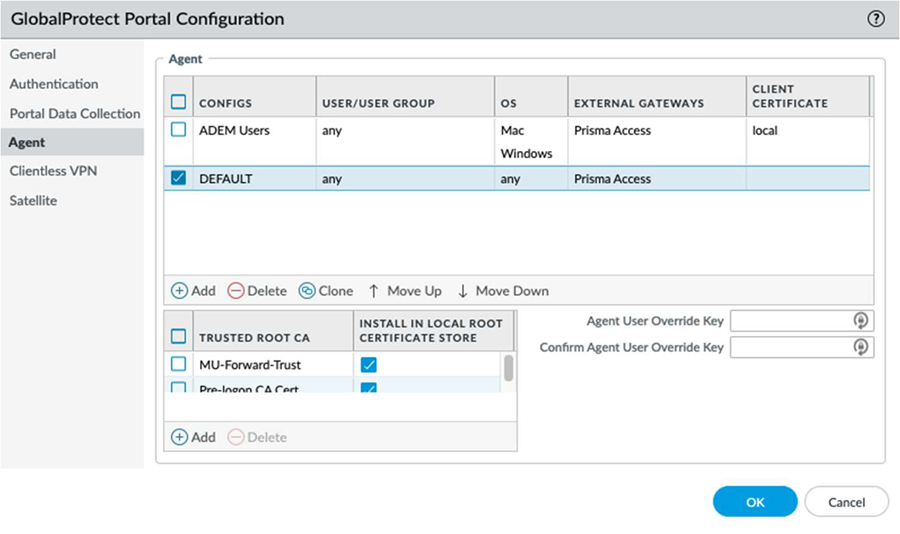
![]() Select Agent and open the Agent configuration for authenticated users.
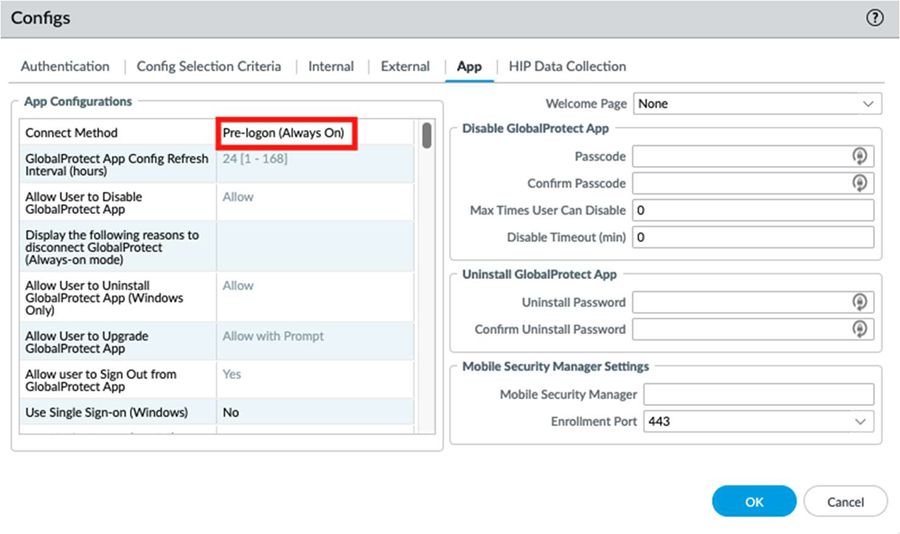
Select Agent and open the Agent configuration for authenticated users.![]() Select the App tab.Select Pre-logon (Always On), and select OK to return to the Agent area.
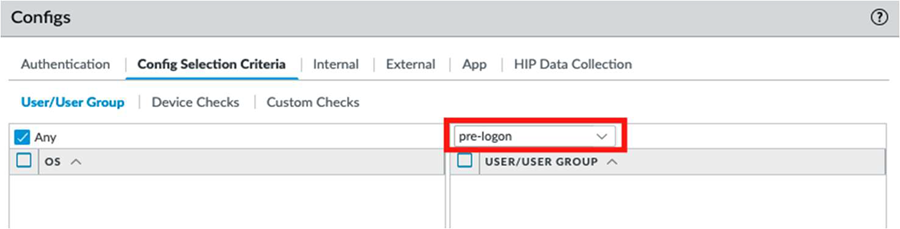
Select the App tab.Select Pre-logon (Always On), and select OK to return to the Agent area.![]() In the Agent area, Clone the default configuration. Change the configuration name to Pre-logon to match the connect method for machine certificate authentication.Select the newly cloned agent configuration.Select Config Selection Criteria. Under the User/User Group configuration, select pre-logon from the drop-down above the USER/USER Group configuration box, and ensure that the configuration is set to Any.
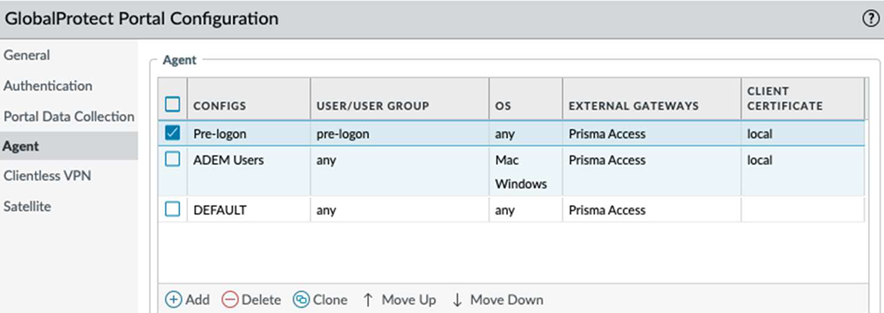
In the Agent area, Clone the default configuration. Change the configuration name to Pre-logon to match the connect method for machine certificate authentication.Select the newly cloned agent configuration.Select Config Selection Criteria. Under the User/User Group configuration, select pre-logon from the drop-down above the USER/USER Group configuration box, and ensure that the configuration is set to Any.![]() Configure the App settings as needed and select OK. Ensure that you select a pre-logon connect method for both the pre-logon and current configuration.Move the pre-logon agent configuration to the top of the CONFIGS list to ensure it matches first with the pre-logon condition.
Configure the App settings as needed and select OK. Ensure that you select a pre-logon connect method for both the pre-logon and current configuration.Move the pre-logon agent configuration to the top of the CONFIGS list to ensure it matches first with the pre-logon condition.![]() Click OK to save the portal configuration.
Click OK to save the portal configuration.Configure the Prisma Access GlobalProtect Gateways
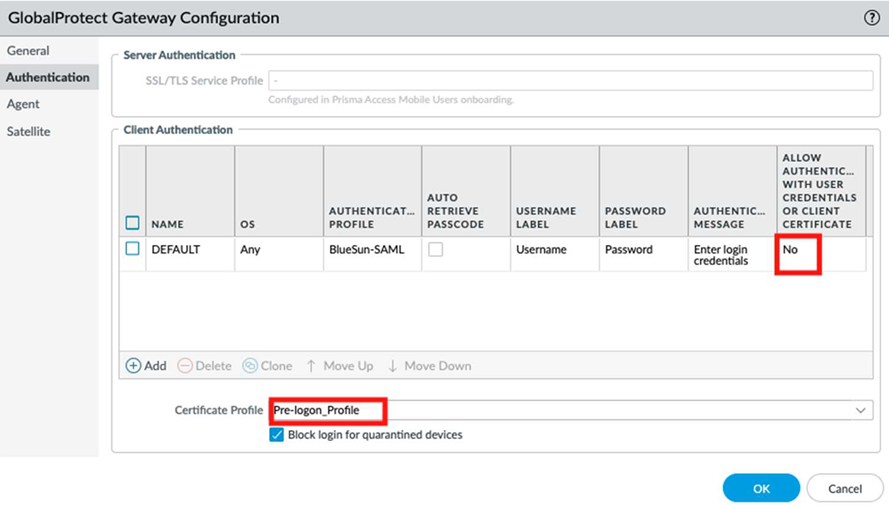
Configure the GlobalProtect gateways in Panorama Managed Prisma Access. This configuration enforces certificate-based authentication only.- Go to NetworkGlobalProtectGatewaysGlobalProtect_External_GatewayAuthentication.Select the Default authentication method.If you already have a client authentication (such as SAML) configured, select it instead of Default.Under Allow Authentication with User Credentials or Client Certificate, select No, and then select OK to save the configuration.
![]()
Install a Machine Certificate—Windows
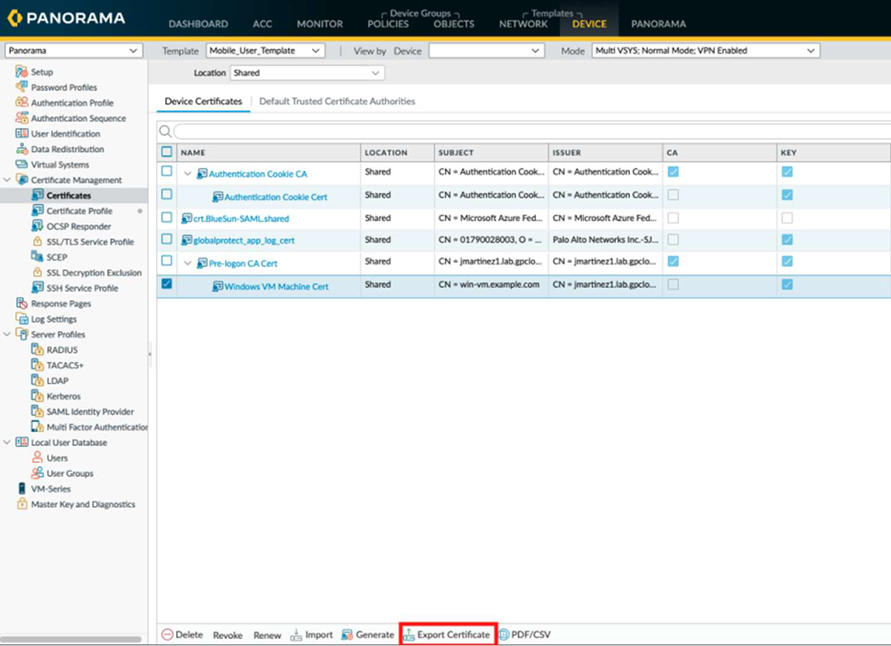
Install the machine certificate at the mobile users' endpoints, which are used for authentication.- Go to DeviceCertificate ManagementCertificates.Be sure that you're still in the Mobile_User_Template. Select the Windows VM Machine Cert that you created previously, and select Export Certificate to download it as a PKCS12 file with a passphrase.
![]() Export the pre-logon CA cert as a base64 encoded certificate.Transfer the certificate files to a Windows machine.Install the root pre-logon CA certificate in the Trusted Root Certification Authorities store of your local machine.
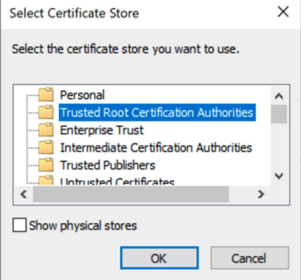
Export the pre-logon CA cert as a base64 encoded certificate.Transfer the certificate files to a Windows machine.Install the root pre-logon CA certificate in the Trusted Root Certification Authorities store of your local machine.![]() Install the pre-logon machine certificate in the local machine store location. Complete the permissions, and select Next to proceed with the installation.Validate the filename to the certificate, and select Next.Enter the password, which is the passphrase you used during the certificate export from Panorama, and select Next.In the Certificate Store dialog, select Place all certificates in the following store, and select Browse.Select the Personal folder where you want to install the machine certificate, and select OK.Select Next to proceed with installation.Connect to the GlobalProtect portal, and delete all cookies from the host.(Optional) Sign out of your machine and view the GlobalProtect logs to verify the pre-logon connection.
Install the pre-logon machine certificate in the local machine store location. Complete the permissions, and select Next to proceed with the installation.Validate the filename to the certificate, and select Next.Enter the password, which is the passphrase you used during the certificate export from Panorama, and select Next.In the Certificate Store dialog, select Place all certificates in the following store, and select Browse.Select the Personal folder where you want to install the machine certificate, and select OK.Select Next to proceed with installation.Connect to the GlobalProtect portal, and delete all cookies from the host.(Optional) Sign out of your machine and view the GlobalProtect logs to verify the pre-logon connection.