Prisma Access
Allow Listing GlobalProtect Mobile Users
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Allow Listing GlobalProtect Mobile Users
Learn how to enable the egress IP address allow lists for existing mobile
users.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To enable you to add the public (egress) IP addresses for your GlobalProtect™—Mobile
User deployment to any SaaS application allow lists you use within your organization,
Prisma Access provides the IP addresses and lets you verify that you have added
them to your allow list before using them in your environment. If you enable egress IP
address allow lists for existing Prisma Access deployments, Prisma Access
migrates all the egress IP addresses already allocated for your locations to the egress
IP allow lists. For new Prisma Access deployments, enable the egress IP allow list
while onboarding the GlobalProtect™ mobile users.
After you have added the egress IP addresses to your organization’s allow
lists, return to the Prisma Access UI, confirm the GlobalProtect egress IP addresses
as allow listed, and Push your changes. Prisma Access then
releases these egress IP addresses and adds them to your deployment. If Prisma Access adds more IP addresses after initial configuration as a result of an autoscale event,
you confirm the new egress IP addresses as having been added before Prisma Access
adds them to your deployment.
This method of egress IP address allocation has the following benefits:
- It ensures that Prisma Access only provisions IP addresses that you have allow listed.
- It prevents mobile users from attempting to connect to Prisma Access from an IP address that is blocked by your organization’s network. Prisma Access does not release IP addresses to your deployment until they have been confirmed by you as allow listed.
- It provides a way to retrieve your current egress IP addresses without using the API.
Prisma Access allocates egress IP addresses in the following situations:
- When you onboard your locations during mobile user onboarding.Prisma Access allocates two gateway IP addresses for each location you onboard.If you onboard a location, and other locations in the same compute location are experiencing an autoscale event, Prisma Access might allocate more than two IP addresses for the new location. In this situation, be sure that you add all these IP addresses to your allow lists and confirm all addresses as being Added to My Allow List.
- During a large scaling event.If the number of mobile users exceeds the capacity of the two pre-allocated IP addresses, Prisma Access allocates additional IP addresses.To keep informed of any IP addresses that Prisma Access adds as a result of an autoscale event, you can set up a URL where Prisma Access will notify you of IP address changes.
You're not required to enable this functionality; you choose whether or not to let Prisma Access release the IP addresses until you have confirmed them as being allow
listed in the UI.
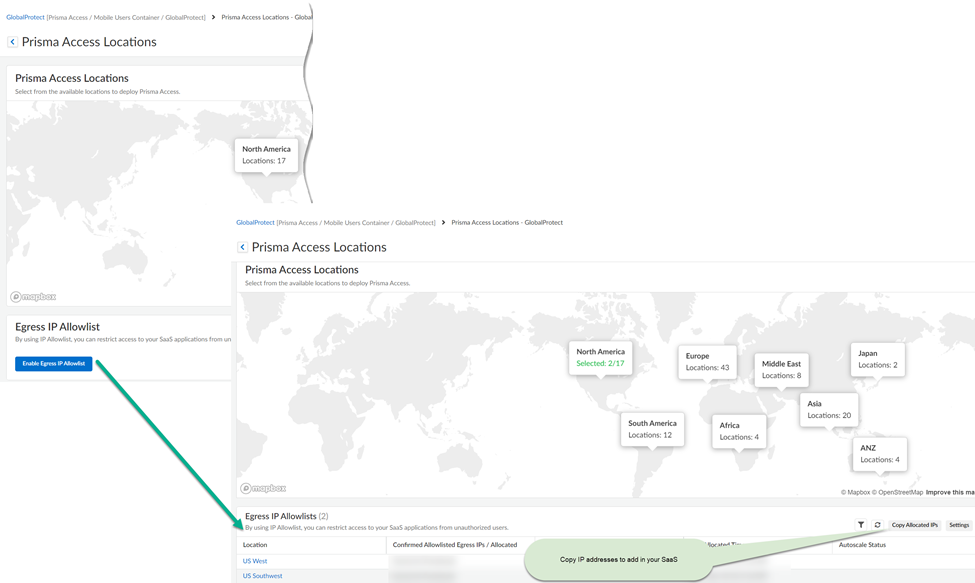
Once enabled, the Egress IP Allowlists table provides information on the IP addresses
that are confirmed or yet to be confirmed, as well as their provision status.
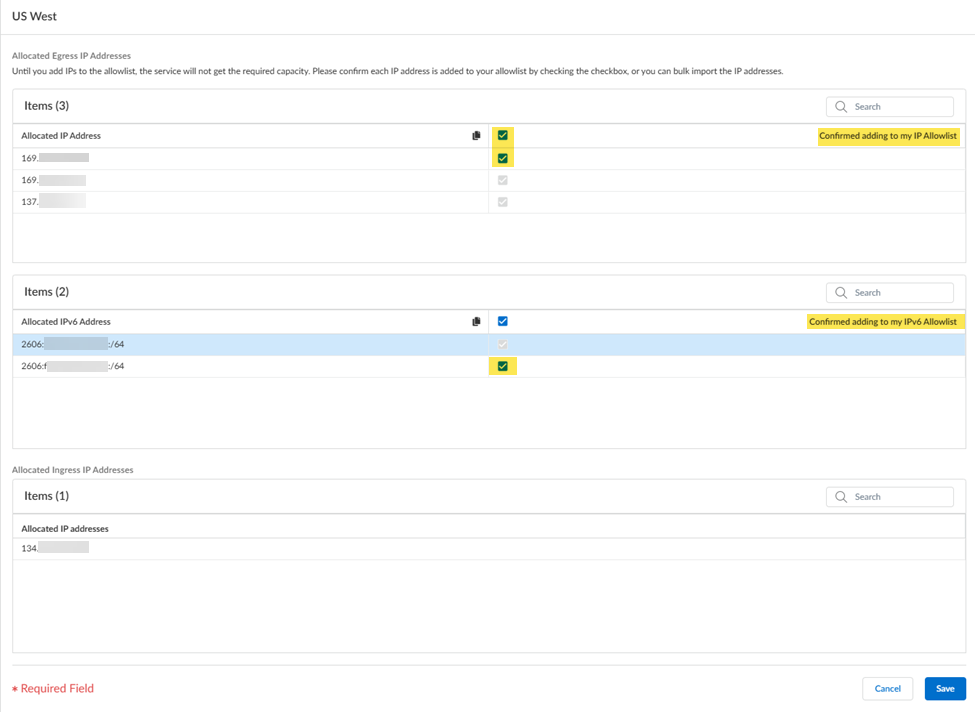
Prisma Access also provides you with the ingress IP addresses that are used in IP Optimization
deployments. Internet or SaaS apps don’t see these IP addresses but you might have to
add them to your allow lists in certain conditions.
Allow Listing for IPv6 Deployments
If you use IPv6 in allow lists, you must first enable IPv6 networking for your
Mobile Users—GlobalProtect deployment. In addition, make a note of the differences
between IPv4 and IPv6 addresses in allow lists:
| IPv4 Addressing | IPv6 Addressing |
|---|---|
| Prisma Access provides you with specific IPv4 addresses (for example, 35.1.2.3, 35.1.2.4, and 35.1.2.5). | Prisma Access provides you with an IPv6 prefix (for example, 2001:db8:3c4d:15::/64) |
| Each location can have multiple IPv4 addresses. Prisma Access can add IP addresses during an autoscale event (for example, if a large number of mobile users log in at the same time, Prisma Access adds a GlobalProtect gateway). | Prisma Access uses the prefix for all autoscale events and does not provide you with additional IPv6 addresses. |
| You don’t need to enable all IPv4 addresses in each enabled location. | If you don’t select the IPv6 address in the Confirmed adding to my IPv6 Allowlist field (for Prisma Access (Managed by Strata Cloud Manager) deployments) or IPv6 Address in the Allow Lists ( (for Prisma Access (Managed by Panorama) deployments), the commit process fails until you select that check box. |
Allow Listing GlobalProtect Mobile Users (Strata Cloud Manager)
Learn how to find the IP addresses that you need to add to your network's allow lists.
Enable Prisma Access to display the egress
IP addresses for Prisma Access traffic. Use these IP addresses in
the IP allow lists for your SaaS applications, where you’re restricting
usage to authorized users or sources.
Retrieving IP addresses for Mobile Users—GlobalProtect Deployments: If you
have a Mobile Users—GlobalProtect deployment:
- You can retrieve the public IP addresses using the Prisma Access UI instead of using the API.
- If you have IPv6 enabled for your deployment, Prisma Access allocates an IPv6 subnet and uses addresses in that subnet for autoscale events instead of specific IPv6 addresses.
- Go to Configuration NGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectInfrastructure and edit Prisma Access Locations settings.Display the IP addresses for Prisma Access locations.
- Enable egress IP allow listing to display the IP addresses for onboarded Prisma Access locations.Copy and add the allocated IP addresses to the allow lists of your SaaS applications.Migrate to confirm the IP addresses allocated for the onboarded locations in Prisma Access.
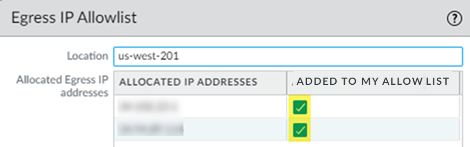
![]() Retrieve the IP addresses for a newly-onboarded location or during an auto-scaling event.You can also retrieve the public IP addresses using the Prisma Access UI instead of using the API.
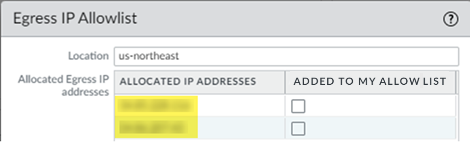
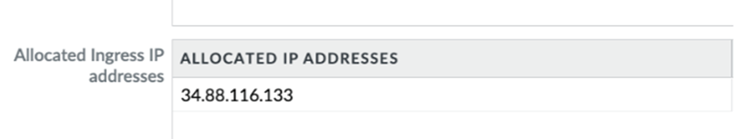
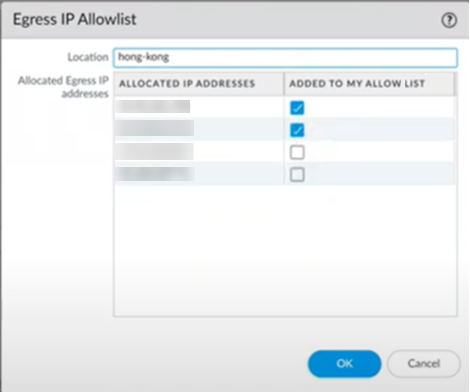
Retrieve the IP addresses for a newly-onboarded location or during an auto-scaling event.You can also retrieve the public IP addresses using the Prisma Access UI instead of using the API.- Select the Location name to find the new egress IP addresses allocated to the location.Select Confirmed adding to my IP Allowlist to add these IP addresses to the allow lists for your SaaS applications before you confirm them in Prisma Access.If you have IPv6 addresses, select Confirmed adding to my IPv6 Allowlist. Prisma Access provides you with an IPv6 subnet instead of specific IPv6 addresses.Any check boxes that are grayed out indicate IP addresses that are already being used and you cannot add or remove them. The Allocated ingress IP addresses are the ingress IP addresses you should add to your NGFW allow list or client endpoint policies.
![]() Push your changes to Prisma Access.
Push your changes to Prisma Access.Statuses of Allocated Egress IP Addresses
Field Description Status - Provisioned—You have added the egress IP addresses to the allow lists of your SaaS applications, confirmed the IP addresses in Prisma Access, and pushed your changes to fully provision them.
- Partially Provisioned—You have added the first set of egress IP addresses, confirmed them in the Prisma Access, and pushed your changes. However, Prisma Access has added another set of IP addresses as part of an autoscale event, and those IP addresses are not yet confirmed in Prisma Access.
- Not Provisioned—Prisma Access has allocated IP addresses for the location, and you have added the egress IP addresses to the allow lists of your SaaS applications and confirmed them in Prisma Access, but you have not yet onboarded this location.
- Can’t be Provisioned—You have onboarded this location, but have not yet confirmed in Prisma Access and pushed your changes.
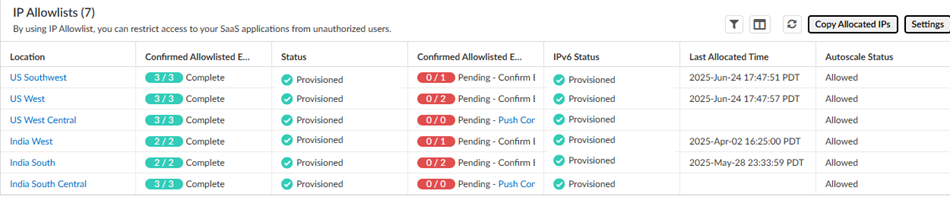
Autoscale Status - Allowed—You have specified IP addresses as being added to the allow lists in the Prisma Access UI.Autoscale events affect all the onboarded locations in a compute location. When an autoscale event occurs for a location and you have not yet confirmed the addresses as being added to your allow lists, all locations in that compute location will show an Autoscale Status of Not Allowed.to the allow lists.
- Not Allowed—You have not specified all IP addresses as being added to your allow lists in the Prisma Access UI, or you have not committed and pushed your changes after marking them as added. If Prisma Access triggers an autoscale event, Prisma Access won’t provision more IP addresses to add more capacity for the location.Every time that you add a location, or every time that Prisma Access adds IP addresses as a result of an autoscale event, you need to refresh the page that contains the Egress IP Allow List table, specify Added to My Allow List to mark the IP addresses as being added to your organization’s allow lists, and Commit and Push your changes.
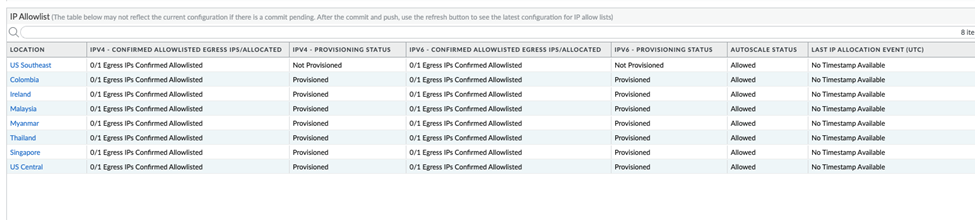
To keep informed of any IP addresses that Prisma Access adds as a result of an autoscale event, you should set up a URL where Prisma Access will notify you of IP address changes.The Egress IP Allowlists table also indicates the number of IP addresses that are confirmed and not yet confirmed in Prisma Access. For example, 1/2 means, one out of two IP addresses allocated for the location are confirmed in Prisma Access.![]()
Allow Listing GlobalProtect Mobile Users (Panorama)
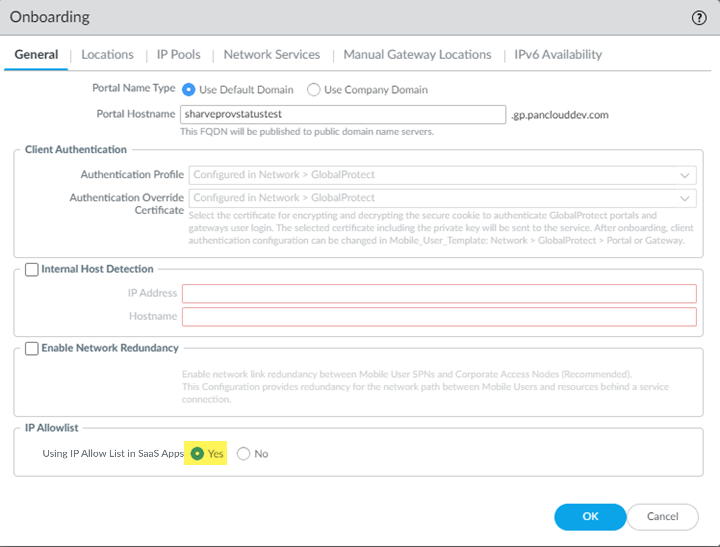
Learn how to enable the egress IP allow lists for existing Panorama managed mobile users.To prevent Prisma Access from provisioning public (egress) GlobalProtect IP addresses to your deployment until you have added them to your allow lists, specify Yes in the Using IP Allow List in SaaS Apps setting during Mobile Users—GlobalProtect onboarding. Confirm that you have added them in the Prisma Access UI by completing the following task.Retrieving IP addresses for Mobile Users—GlobalProtect Deployments: If you have a Mobile Users—GlobalProtect deployment:- You can retrieve the public IP addresses using the Prisma Access UI instead of using the API.
- If you have IPv6 enabled for your deployment, Prisma Access allocates an IPv6 subnet and uses addresses in that subnet for autoscale events instead of specific IPv6 addresses.
- Select PanoramaCloud ServicesConfigurationMobile Users—GlobalProtect.Select your Hostname and Configure it (for an existing deployment), or Configure your deployment for the first time (for a new deployment).Specify Using IP Allow List in SaaS Apps as Yes.
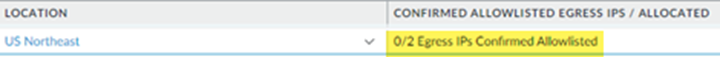
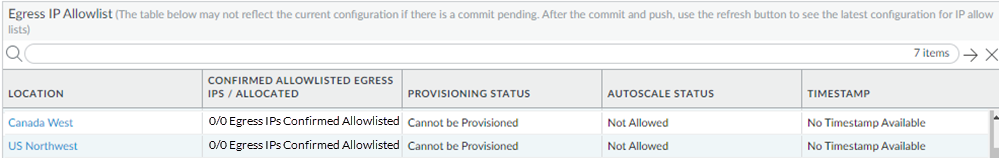
![]() Continue your Prisma Access onboarding, including selecting the locations to use in your mobile users—GlobalProtect deployment, and Commit and Push your changes.It might take up to a minute for the changes to be reflected in the UI. If you view the Egress IP Allow List before committing and pushing your changes, it shows a status of 0/0 Egress IPs Confirmed Allow Listed, because Prisma Access has not assigned any egress IP addresses to your deployment.View the Egress IP Allow List table, and make a note of the egress IP addresses that need to be added to your allow lists.You can view the egress IP addresses in the Confirmed Allow Listed Egress IPs/Allocated field of the Egress IP Allow List table. The first number indicates whether or not the IP address has been confirmed as being added to your allow lists.The following example shows the IP addresses for the US Northeast location. The description of 0/2 Egress IPs Confirmed Allow Listed indicates that none of the two egress IP addresses have been marked as being added to your allow lists, and you need to add them.
Continue your Prisma Access onboarding, including selecting the locations to use in your mobile users—GlobalProtect deployment, and Commit and Push your changes.It might take up to a minute for the changes to be reflected in the UI. If you view the Egress IP Allow List before committing and pushing your changes, it shows a status of 0/0 Egress IPs Confirmed Allow Listed, because Prisma Access has not assigned any egress IP addresses to your deployment.View the Egress IP Allow List table, and make a note of the egress IP addresses that need to be added to your allow lists.You can view the egress IP addresses in the Confirmed Allow Listed Egress IPs/Allocated field of the Egress IP Allow List table. The first number indicates whether or not the IP address has been confirmed as being added to your allow lists.The following example shows the IP addresses for the US Northeast location. The description of 0/2 Egress IPs Confirmed Allow Listed indicates that none of the two egress IP addresses have been marked as being added to your allow lists, and you need to add them.![]() If you have a new Prisma Access deployment, or if you have added locations or had an autoscale event, the table shows that none of the egress IP addresses have been added to your organization’s allow list.
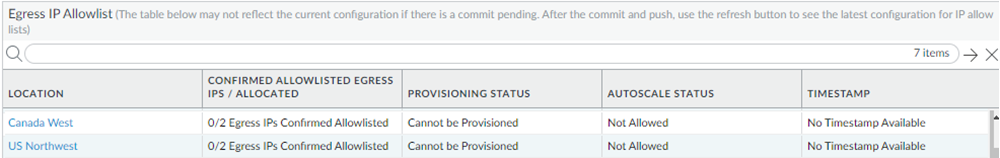
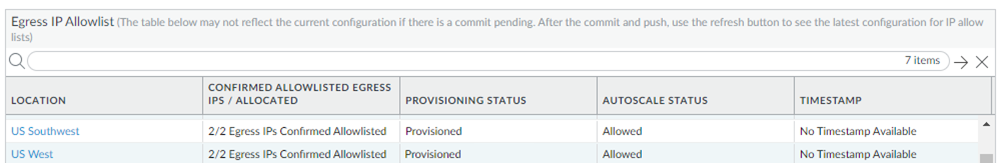
If you have a new Prisma Access deployment, or if you have added locations or had an autoscale event, the table shows that none of the egress IP addresses have been added to your organization’s allow list.![]() If you have an existing Prisma Access deployment, the table shows a Provisioning Status of Provisioned and an Autoscale Status of Allowed, which indicates that Prisma Access marked the egress IP addresses as added.
If you have an existing Prisma Access deployment, the table shows a Provisioning Status of Provisioned and an Autoscale Status of Allowed, which indicates that Prisma Access marked the egress IP addresses as added.![]() Prisma Access will allocate two addresses for each newly added location. If an existing location has previously had an autoscale event when a large number of mobile users logged in to a single location at the same time, Prisma Access allocates additional egress IP address in multiples of two, and an existing location could have four or more addresses.Find the new egress IP addresses that need to be added to your organization’s allow lists by selecting the Location name in the table.
Prisma Access will allocate two addresses for each newly added location. If an existing location has previously had an autoscale event when a large number of mobile users logged in to a single location at the same time, Prisma Access allocates additional egress IP address in multiples of two, and an existing location could have four or more addresses.Find the new egress IP addresses that need to be added to your organization’s allow lists by selecting the Location name in the table.![]() Prisma Access also provides you with the ingress IP addresses that are used in IP Optimization deployments. Internet or SaaS apps don’t see these IP addresses but you might have to add them to your allow lists in certain conditions.
Prisma Access also provides you with the ingress IP addresses that are used in IP Optimization deployments. Internet or SaaS apps don’t see these IP addresses but you might have to add them to your allow lists in certain conditions.![]() Add these egress IP addresses to your organization’s allow lists.After you have allow listed the egress IP address, return to the egress IP area and indicate that you have added them to your allow lists by selecting Added to My Allow List.
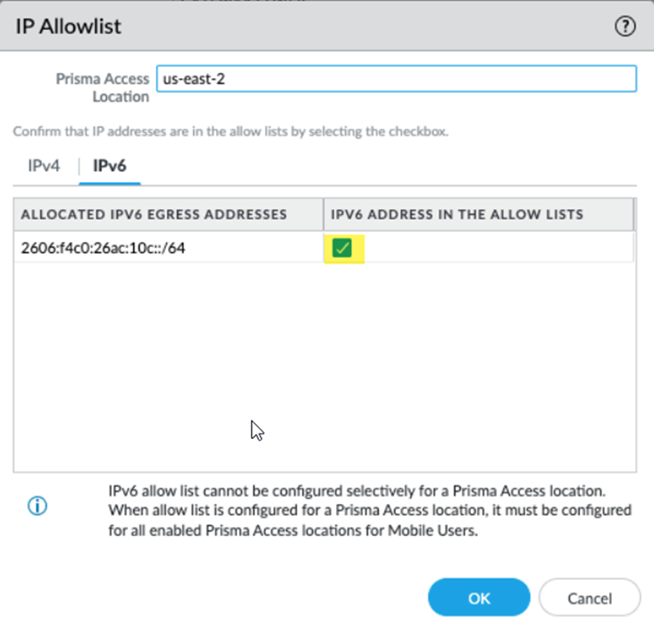
Add these egress IP addresses to your organization’s allow lists.After you have allow listed the egress IP address, return to the egress IP area and indicate that you have added them to your allow lists by selecting Added to My Allow List.![]() If you have IPv6 addresses, select IPv6 Address in the Allow Lists.Prisma Access provides you with an IPv6 subnet instead of specific addresses.
If you have IPv6 addresses, select IPv6 Address in the Allow Lists.Prisma Access provides you with an IPv6 subnet instead of specific addresses.![]() Commit and push your changes to make them active in Prisma Access.
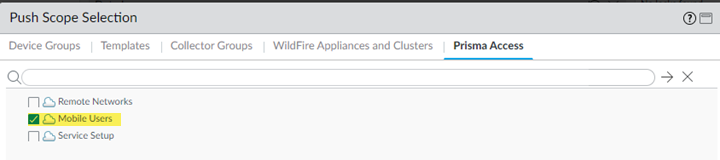
Commit and push your changes to make them active in Prisma Access.- Select CommitCommit and Push and Edit Selections in the Push Scope.Select Prisma Access, then make sure that Mobile Users is selected.
![]() Click OK to save your changes to the Push Scope.Commit and Push your changes.If you view the Egress IP Allow List table before committing and pushing your changes, the Confirmed column shows a status of 0/0 Egress IPs Confirmed Allow Listed because Prisma Access has not assigned any IP addresses to your deployment until you Commit and Push.
Click OK to save your changes to the Push Scope.Commit and Push your changes.If you view the Egress IP Allow List table before committing and pushing your changes, the Confirmed column shows a status of 0/0 Egress IPs Confirmed Allow Listed because Prisma Access has not assigned any IP addresses to your deployment until you Commit and Push.![]() The Egress IP Allow List table contains the following additional fields:
The Egress IP Allow List table contains the following additional fields:Field Description Location The onboarded mobile user location.Confirmed Allow Listed Egress IPs/Allocated The number of egress IP addresses that have been confirmed as being allow listed, and the number of egress IP addresses that have been allocated.Provisioning Status The allow listing status of the egress IP addresses.- Provisioned—You have added the egress IP addresses to your organization’s allow lists, have confirmed them as having been added in the Prisma Access UI by checking Added to My Allow List, and have committed and pushed your changes to fully provision the IP addresses.
- Not Provisioned—Prisma Access has allocated IP addresses for the location, and you have added the egress IP addresses to your organization’s allow lists and confirmed them as having been added in the Prisma Access UI, but you have not yet onboarded this location.
- Can’t Be Provisioned—You have onboarded this location, but have not yet checked Add to My Allow List and committed and pushed your changes.Until you specify in Prisma Access that you have added these egress IPs to your organization’s allow lists and Commit and Push your changes, Prisma Access won’t provision these IP addresses to your deployment.
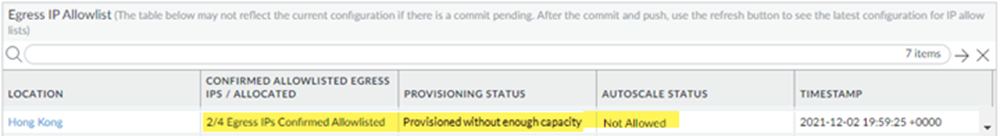
- Provisioned with partial capacity—You have added the first set of egress IP addresses, have confirmed them as having been added in the Prisma Access UI, and have Committed and Pushed your changes. However, Prisma Access has added another set of IP addresses as part of an autoscale event, and those IP addresses have not been specified as added to your allow lists in the Prisma Access UI.The following screenshot shows an example of a deployment that would be marked as Provisioned with partial capacity. Two IP addresses have been marked as Added to My Allow List; however, Prisma Access has added two more IP addresses to this location, and those locations have not been added in the UI.
![]()
Autoscale Status Shows the status of the autoscaling in Prisma Access.- Allowed—You have added IP addresses to the allow lists. If a large number of mobile users log in to a single location and trigger an autoscale event, Prisma Access will use the allow listed IP addresses for the autoscale event.
- Not Allowed—You have not specified all IP addresses as being added to your allow lists in the Prisma Access UI, or you have not committed and pushed your changes after marking them as added. If Prisma Access triggers an autoscale event, Prisma Access won’t provision more IP addresses to add more capacity for the location.Every time that you add a location, or every time that Prisma Access adds IP addresses as a result of an autoscale event, you need to refresh the page that contains the Egress IP Allow List table, specify Added to My Allow List to mark the IP addresses as being added to your organization’s allow lists, and Commit and Push your changes.
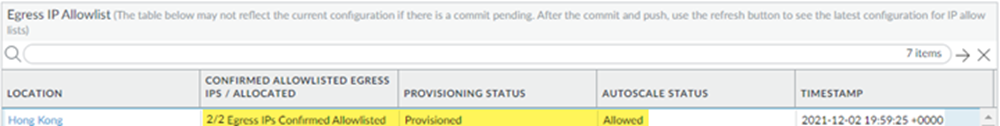
To keep informed of any IP addresses that Prisma Access adds as a result of an autoscale event, you should set up a URL where Prisma Access will notify you of IP address changes.Timestamp The last known time when an IP was allocated for this region in Coordinated Universal Time (UTC).After you Commit and Push, the Confirmed column will show a status of 0/2 Egress IPs Confirmed Allow Listed, because you have not yet confirmed the IP addresses as having been allow listed in the Prisma Access UI.When you onboard a mobile user location, Prisma Access provides you with two egress IP addresses - one active IP address and one address to use in case of an autoscale event. The following provides examples of how Prisma Access allocates and provisions egress IP addresses after an autoscale event.Autoscale Event—If a large number of mobile users log in to a mobile user location at the same time, that event might cause Prisma Access to allocate an additional set of two egress IP addresses to accommodate the large number of users. After you have allow listed the first two egress IP addresses, the status before an autoscale event shows the two egress IP addresses as being allow listed with a confirmed status of 2/2 Egress IPs Confirmed Allow Listed, a provisioning status of Provisioned, and an autoscale status of Allowed, as shown in the Hong Kong location in the following screenshot.![]() If a large number of mobile users log in to the Hong Kong location at the same time, Prisma Access makes the backup egress IP address active and allocates two more IP addresses and makes one of them active. When an autoscale event occurs, the egress IP addresses have been allocated but not provisioned, the confirmed status is 2/4 Egress IPs Confirmed Allow Listed, and the provisioning status shows Provisioned without enough capacity. In addition, the autoscale status shows Not Allowed, which means that Prisma Access won’t provision the extra egress IP address to your deployment if an autoscale event occurs.
If a large number of mobile users log in to the Hong Kong location at the same time, Prisma Access makes the backup egress IP address active and allocates two more IP addresses and makes one of them active. When an autoscale event occurs, the egress IP addresses have been allocated but not provisioned, the confirmed status is 2/4 Egress IPs Confirmed Allow Listed, and the provisioning status shows Provisioned without enough capacity. In addition, the autoscale status shows Not Allowed, which means that Prisma Access won’t provision the extra egress IP address to your deployment if an autoscale event occurs.![]() After you have added the new egress IP addresses to your allow lists, select the location name; then, select Added to My Allow List for the two IP addresses that were added and Commit and Push your changes.
After you have added the new egress IP addresses to your allow lists, select the location name; then, select Added to My Allow List for the two IP addresses that were added and Commit and Push your changes.![]() When complete, the Hong Kong location shows that all four egress IP addresses are confirmed and provisioned, and autoscaling is active.
When complete, the Hong Kong location shows that all four egress IP addresses are confirmed and provisioned, and autoscaling is active.![]()