Prisma Access
Prisma Access Dataplane Upgrades
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Prisma Access Dataplane Upgrades
Learn the steps you perform to upgrade the Prisma Access (Panorama managed)
dataplane.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma Access performs dataplane upgrades to help protect your organization’s end-users,
business assets, and security posture. Here are the reasons for a dataplane upgrade:
- Hotfixes or emergency bug fixes (for example, a fix for a zero-day threat).
- Fixes made as the result of a Common Vulnerabilities and Exposures
(CVE) or Product Security Incident Response Team
(PSIRT) issue.If the fix is for a CVE or PSIRT issue, it's considered an urgent scheduled upgrade and follows a different schedule.
- Changes made to support a new feature or features.
When a new version of Prisma Access requires a dataplane upgrade, you should
understand how the upgrade process works and have the required prerequisites in place
before upgrading.
Some releases might offer an optional dataplane upgrade in addition to the required
dataplane upgrades to support Prisma Access features that require it.
Dataplane Upgrade Overview
Prisma Access upgrades your dataplane in two phases, and keeps you informed about
the upgrade using email notifications sent from Strata Cloud Manager. On a high
level, Prisma Access performs these steps during the upgrade process.
- Prisma Access sends you an email notifying you of the scheduled upgrade.Prisma Access upgrades your deployment in two phases. The upgrade happens in two windows on the second and fourth weekend of a given month. In July, November, and December, a holiday moratorium is in effect and Prisma Access does not perform any upgrades except for urgent scheduled dataplane upgrades.After you choose a month, Prisma Access performs the upgrade using one of these schedules:
- Phase #1 occurs on the second weekend of the month and Phase #2 occurs on the fourth weekend of the same month.
- Phase #1 occurs on the fourth weekend of the month and Phase #2 occurs on the second weekend of the following month.
Each upgrade has a window of 4 hours, and Prisma Access performs the upgrade starting at 10:00 p.m. of the time zone of the compute region of the location that's being upgraded. You can request an exception to the upgrade up to 48 hours before the maintenance window begins. To request an exception, reach out to your Palo Alto Networks account representative, who will contact the Site Reliability Engineering (SRE) team and submit a request.- Phase #1 upgrades a location or locations you select on either the second or fourth weekend of the selected month. Select the location or locations to upgrade using upgrade preferences in Strata Cloud Manager. If you don't select a location, Prisma Access selects it for you.If you need to make changes, Prisma Access emails you with a confirmation of the changes. It can take up to 30 minutes for the changes you made to display in the Upgrade Dashboard in Strata Cloud Manager.Palo Alto Networks strongly suggests that you select a Phase #1 location that reflects your entire deployment. For example, if you have a mobile user, service connection, and remote network deployment, select a location or locations that have all deployment types.If the selected upgrade locations have any combination of Mobile Users—GlobalProtect™, Mobile Users—Explicit Proxy, Service Connections, or Remote Networks, the dataplane for each deployment will be upgraded to the required dataplane version, as described later in this section.Strata Cloud Manager sends you an email notification when Phase #1 completes. Palo Alto Networks recommends that you monitor the service for any new issues that occur immediately after the dataplane upgrade.In the unlikely occurrence where you see a new issue, report the issue to Palo Alto Networks technical support. The technical support team investigates the issue and takes corrective actions that might also include rolling the dataplane back to its previous version. This decision will be communicated to you via a technical support case.
- Phase #2 upgrades the remainder of your locations on either the fourth weekend of the selected month or the second weekend of the following month. After the dataplane upgrade completes, you will be notified via an email alert.
(Prisma Access (Managed by Panorama) Deployments Only) If a plugin upgrade is required after the dataplane upgrade, Palo Alto Networks recommends that you upgrade the plugin after the dataplane upgrade completes.
Palo Alto Networks might make last-minute upgrade changes due to:
- Finding commit errors in your Prisma Access deployment
- Not having sufficient Mobile Users—GlobalProtect IP addresses added to your network's allow lists
In addition, the Palo Alto Networks upgrade team reserves the right to change upgrade
times based on:
- Determining that an issue in the new image or environment might potentially put your network at risk
- Finding any infrastructure issues that are beyond the control of Palo Alto Networks
Here's the timeline for the upgrade.

Urgent Scheduled Dataplane Upgrades
Dataplane upgrades to address a CVE or PSIRT issue are classified as an emergency
upgrade to patch a vulnerability. Palo Alto Networks will make every effort to give
you 48 hours’ notice before an urgent scheduled dataplane upgrade; however, on
occasion, you might receive a shorter notice for an urgent scheduled upgrade. If
you're notified via an email that an urgent scheduled dataplane upgrade is
required, make sure that you have sufficient Mobile Users—GlobalProtect IP addresses
added to your network's allow lists.
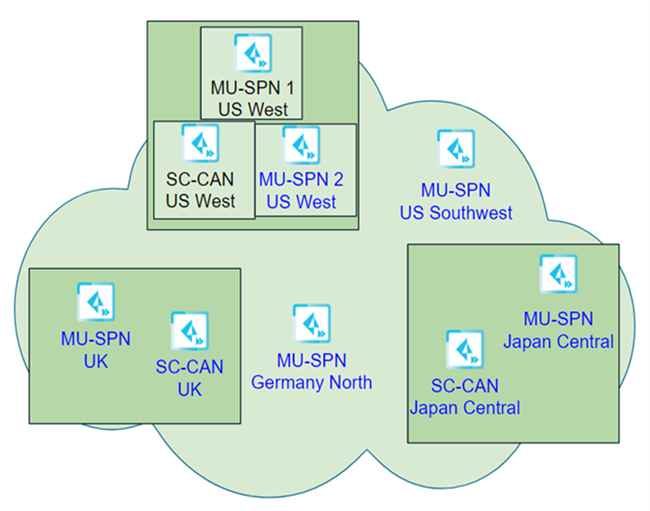
Dataplane Upgrade Example
The following example shows a sample dataplane upgrade procedure for a Mobile Users
deployment with five security processing nodes (MU-SPNs) and three service
connection Corporate Access Nodes (SC-CANs). The US West location has two MU-SPNs as
the result of an autoscale event (an extra MU-SPN was added after a large number of
mobile users logged in to that location).
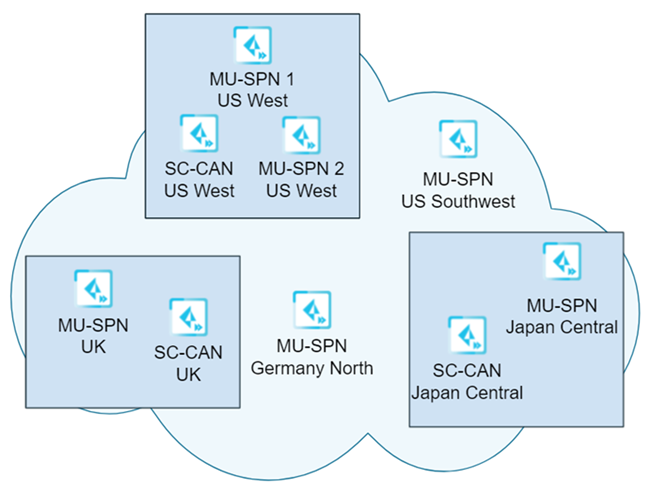
In this example, you selected a single location (US West) to upgrade first. This
upgrade occurs during the second weekend of the month at 10 p.m. Pacific Time.
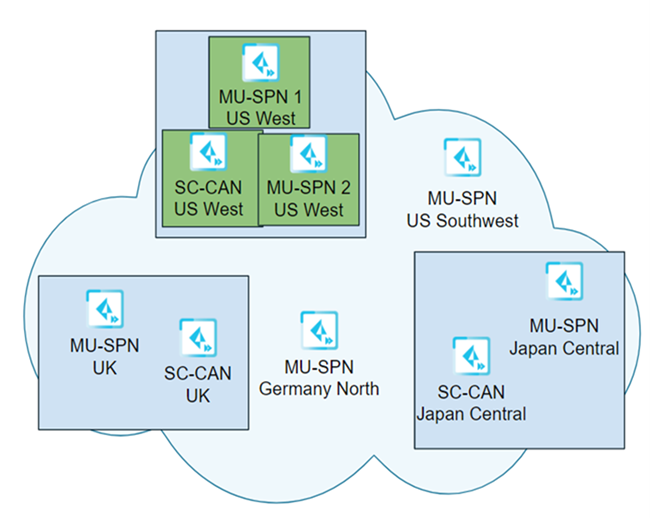
Palo Alto Networks upgrades the remaining components (Phase #2) on the fourth weekend
of the month at 10 p.m.
In this example, Prisma Access uses the following time zone information when
upgrading the dataplane:
- The Japan Central MU-SPN and SC-CAN are upgraded using the local time in Japan.
- The UK MU-SPN and SC-CAN are upgraded using the local time in the UK.
- The US Southwest MU-SPN is upgraded using Pacific Time.