Prisma Access
Access Your Data Center Using Explicit Proxy
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Access Your Data Center Using Explicit Proxy
This is how you use Explicit Proxy to access resources in your data
center.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can use service connections, ZTNA Connector, or colo-connect to access resources in your
data center, such as external dynamic lists or private and
partner apps, while still benefiting from an Explicit Proxy connection.
Following RFC 6598 IP addresses aren't supported for Private application access
through Explicit Proxy via service connections, Colo-Connect, or ZTNA
Connector:
- 100.64.0.0/15
- 100.88.0.0/15
- 100.72.0.0/15
The existing ZTNA Connectors using these IP addresses in ZTNA Connector
Application IP blocks or Connector IP blocks are disabled from using Prisma Access Browser or GlobalProtect Agent in Proxy Mode through Explicit Proxy. You must
Reach out to your Palo Alto Networks representative to migrate your IP addresses
to a different block.
Private app access is not supported when traffic is coming from the IP address
that is a part of Trusted source IP address list.
Skip auth-bypass is not supported for private application domains. Hence, the
custom URL used for authentication flows must not contain private application
FQDNs.
Access Your Data Center Using Explicit Proxy (Strata Cloud Manager)
This is how you access your data center using Prisma Access Explicit Proxy in Strata Cloud Manager.
- Configure a service connection, Colo-Connect or ZTNA Connector in Prisma Access based on your requirement.Configure DNS settings.Ensure that the DESTINATION Zones for internet-bound traffic is set to untrust instead of any.Failure to perform this step could result in unintended access to your data center.
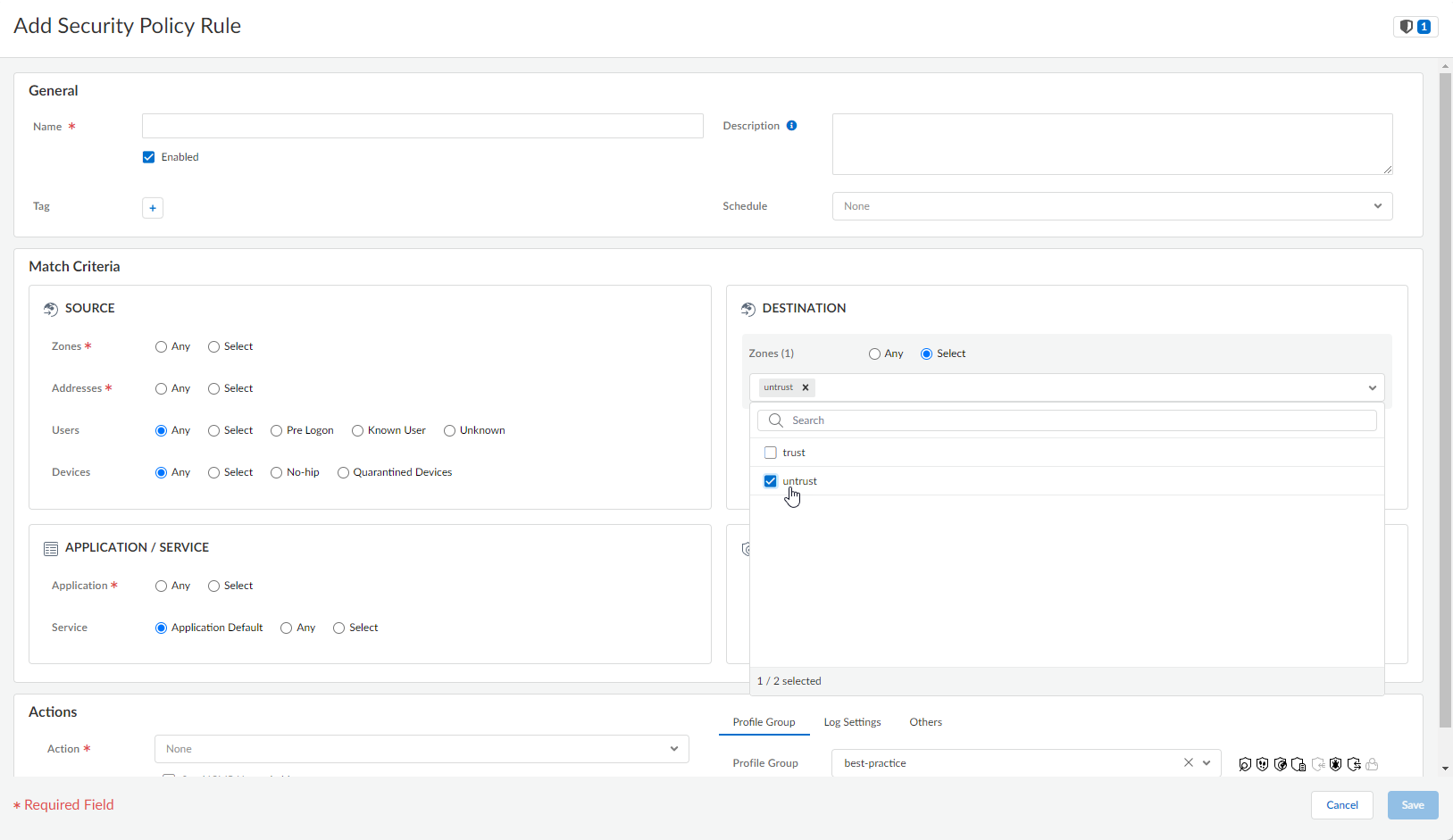
- Go to ConfigurationNGFW and Prisma Access, set the Configuration Scope to Prisma AccessMobile Users ContainerExplicit Proxy, then select Security PolicySecurity Services.Open a rule for internet-bound traffic.Ensure Zones under DESTINATION is set to untrust.
![]() Repeat for all of your internet-bound traffic rules.Enable private application access.
Repeat for all of your internet-bound traffic rules.Enable private application access.- Enable private application access using Prisma Browser.
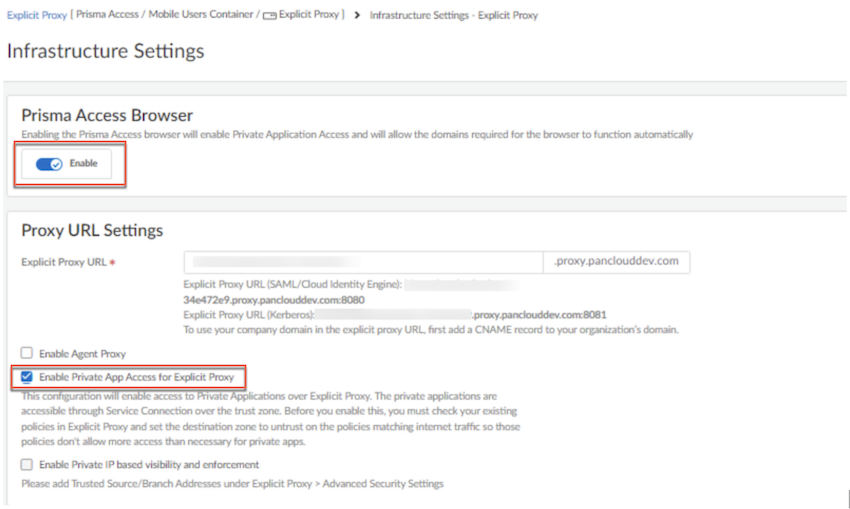
- Select ConfigurationPrisma Access SetupConfiguration ScopePrisma AccessExplicit Proxy Infrastructure Settings and Enable Prisma Browser. Under Proxy URL Settings, select Enable Private App Access for Explicit Proxy.
![]()
![]()
- Select ConfigurationPrisma Access SetupConfiguration ScopePrisma AccessExplicit Proxy Infrastructure Settings
- Enable private application access using a regular browser.
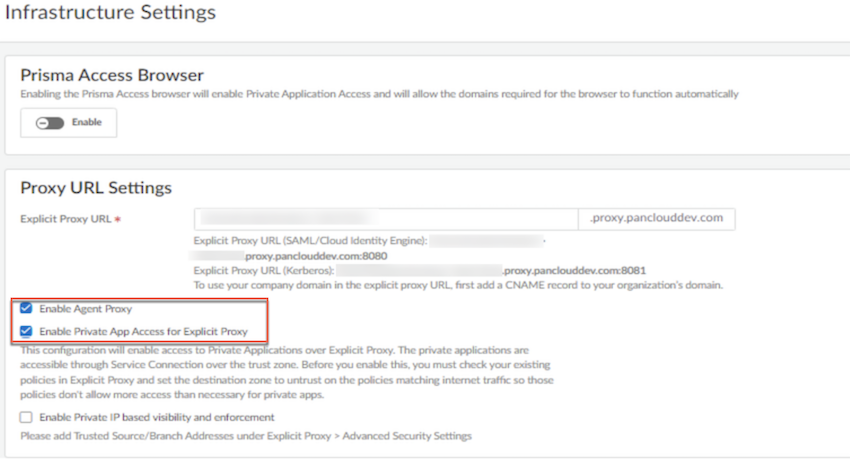
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeExplicit ProxyExplicit Proxy Infrastructure Settings Enable Agent ProxyEnable Private App Access for Explicit Proxy.
![]()
![]()
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeExplicit ProxyExplicit Proxy Infrastructure Settings
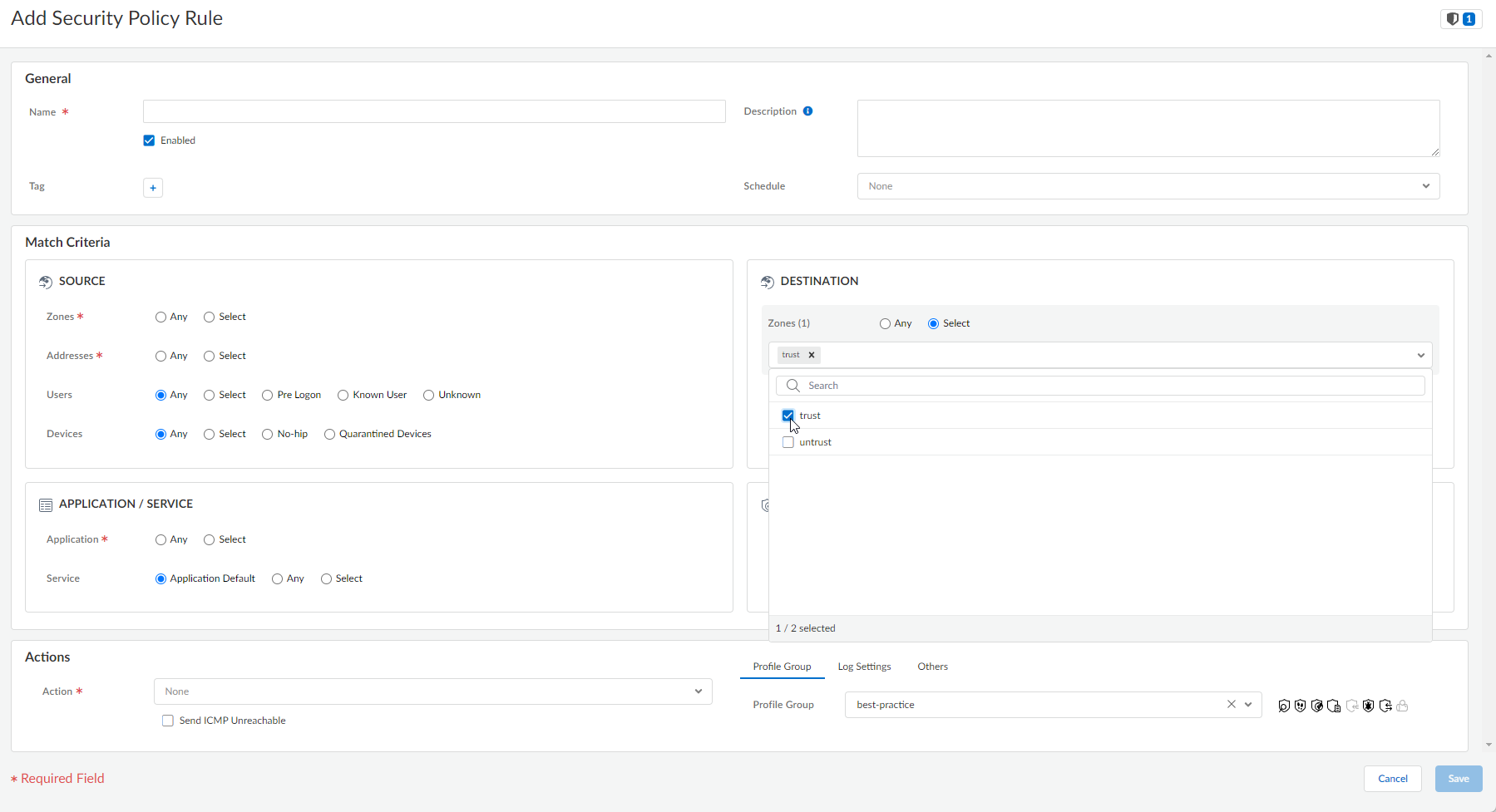
Create security policy rules for the data center resources you want to access.- Go to ConfigurationNGFW and Prisma Access, set the Configuration Scope to Prisma AccessMobile Users ContainerExplicit Proxy, then select Security PolicySecurity Services.Create security policy rules.In rules for data center access, ensure Zones under DESTINATION is set to trust.
![]() If you enable Private Application Access under Explicit Proxy, Push Config to save your configuration changes after onboarding the ZTNA Connector.
If you enable Private Application Access under Explicit Proxy, Push Config to save your configuration changes after onboarding the ZTNA Connector.
Access Your Data Center Using Explicit Proxy (Panorama)
Access resources hosted in your data center using Prisma Access Explicit Proxy.- Configure a service connection, Colo-Connect or ZTNA Connector in Prisma Access based on your requirement.Configure DNS settings.Configure zone mappings.
- Select PanoramaCloud ServicesConfigurationMobile Users - Explicit ProxyZone Mapping
![]() Add the zones that you will use to access your data center resources to Trusted Zones.Ensure that the Destination ZONE in policy rules for internet-bound traffic is set to an untrust zone instead of any.Failure to perform this step could result in unintended access to your data center.
Add the zones that you will use to access your data center resources to Trusted Zones.Ensure that the Destination ZONE in policy rules for internet-bound traffic is set to an untrust zone instead of any.Failure to perform this step could result in unintended access to your data center.- Select Policies.Set the Device Group to Explicit_Proxy_Device_Group.Change the Destination ZONE from any to one of the untrust zones you configured in an earlier step.Enable private application access.
- Enable private application access using Prisma Browser.
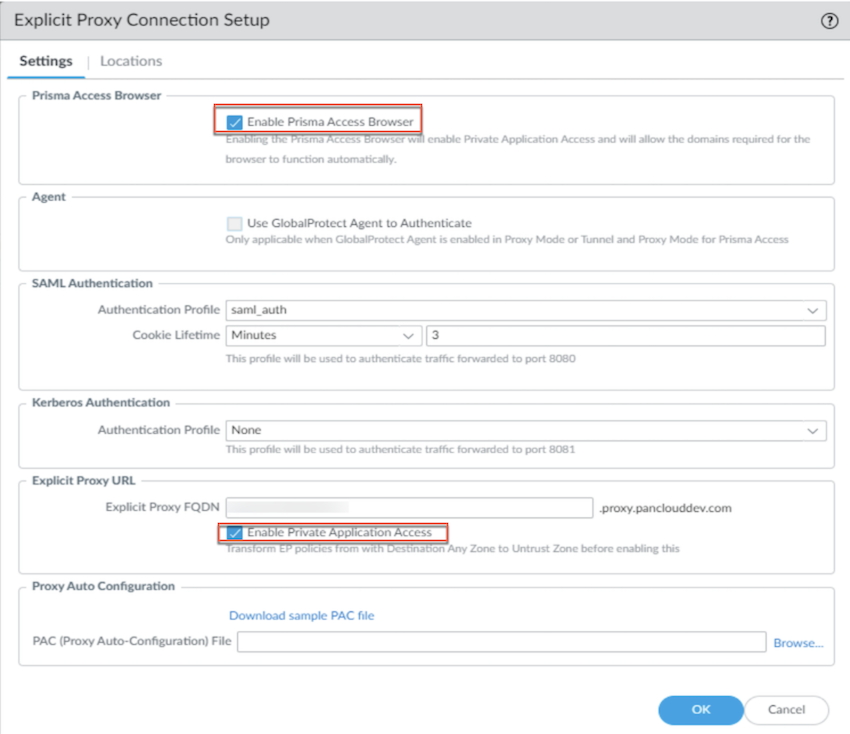
- Go to PanoramaCloud ServicesConfigurationMobile Users - Explicit ProxySettings AdvancedEnable Prisma Access BrowserEnable Private Application Access
![]()
![]()
- Go to PanoramaCloud ServicesConfigurationMobile Users - Explicit ProxySettings
- Enable private application access using a regular browser.
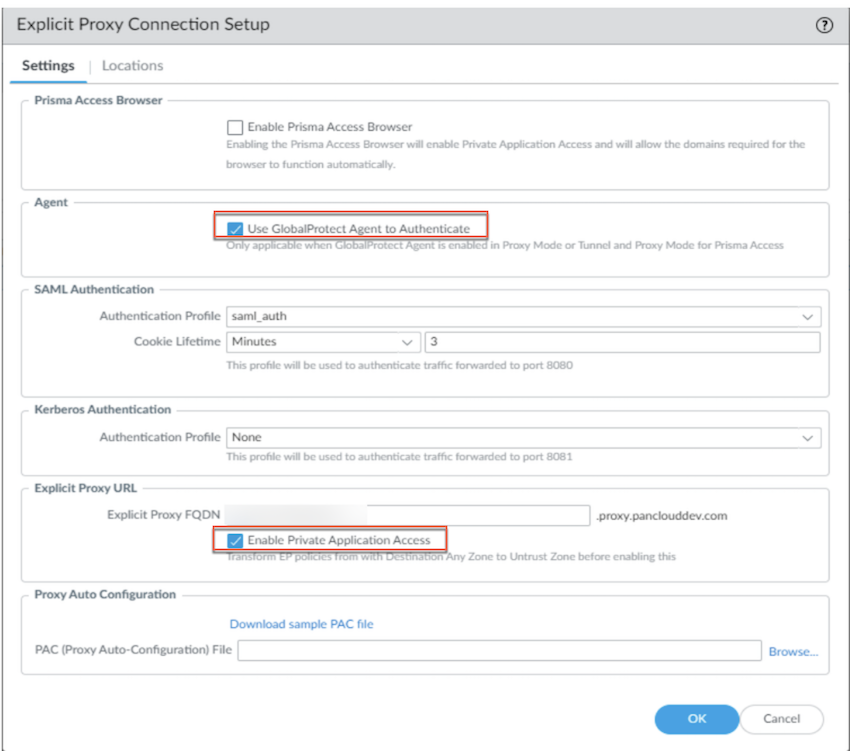
- Go to PanoramaCloud ServicesConfigurationMobile Users - Explicit ProxySettings AdvancedUse GlobalProtect Agent to AuthenticateEnable Private Application Access
![]()
![]()
- Go to PanoramaCloud ServicesConfigurationMobile Users - Explicit ProxySettings
Create security policy rules for the data center resources you want to access.- Select Policies.Set the Device Group to Explicit_Proxy_Device_Group.Create security policy rules.In rules for data center access, ensure that you use the Trusted zones you configured in an earlier step.