Prisma Access
INC_CERTIFICATE_EXPIRY
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
INC_CERTIFICATE_EXPIRY
Learn about the INC_CERTIFICATE_EXPIRY incident.
Synopsis
The system generates the INC_CERTIFICATE_EXPIRY incident before a
certificate's expiration date.
Incident Code—INC_CERTIFICATE_EXPIRY
Severity—Warning/Critical
For details about incident severity, see Incidents Distribution Over Time
in Incidents and Alerts Overview.
Supported Certificates
- ADEM/GP Log (also known as the ADEM certificate)
- GlobalProtect Portal
- SSL Decryption
The severity becomes Critical when the certificate is due to expire in seven days
or less.
Required License
Prisma Access
Details
| Feature | Raise Condition | Clear Condition |
|---|---|---|
|
ADEM/GP Log
|
The system raises the incident 30 days before the ADEM/GP Log
certificate expiration date.
|
The system clears the incident when the ADEM/GP Log certificate
is renewed.
|
|
GlobalProtect Portal
|
The system raises the incident 30 days before the GlobalProtect
Portal certificate expiration date.
|
The system clears the incident when the GlobalProtect Portal
certificate is renewed.
|
|
SSL Decryption
|
The system raises the incident 30 days before the SSL decryption
certificate expiration date.
|
The system clears the incident when the SSL decryption
certificate is renewed.
|
Correlated Alerts
AL_CERTIFICATE_EXPIRY
Remediation
Renew a GlobalProtect Portal certificate
Import the certificate provisioned for the custom domain portal address.
- Renew a GlobalProtect Portal certificate in Strata Cloud ManagerImport the certificate provisioned for the custom domain portal address.
- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectInfrastructure and edit Infrastructure Settings.
- Import the certificate you provisioned for your custom domain portal
address.
- Select the format for the certificate you're importing:
- Encrypted Private Key and Certificate (PKCS12)—The key and certificate are in a single container (Certificate File). Click Choose File and browse to the PKCS12 file to import.
- Base64 Encoded Certificate (PEM)—If you select this option, you must import the Key File separately from the certificate. To import the PEM certificate and Key File, click Choose File.
- Select the format for the certificate you're importing:
- Enter the Passphrase to encrypt the key, and Confirm Passphrase. Save your changes.
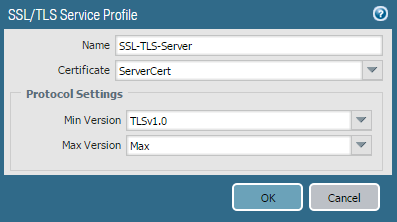
- Renew a GlobalProtect Portal certificate in Panorama
- Go to DeviceCertificate ManagementSSL/TLS Service Profile.
- Click Add at the bottom of the screen.
- Enter a Name for the profile.
- Select the server Certificate.
- Select the minimum and maximum SSL/TLS versions for the SSL transaction between client and server.
![]()
- Reference this SSL/TLS profile in the portal or gateway, as needed.
- Renew an ADEM/GP Log CertificatePrerequisites—Users in either a Strata Cloud Manager or Panorama environment must have an AI-Powered ADEM license.
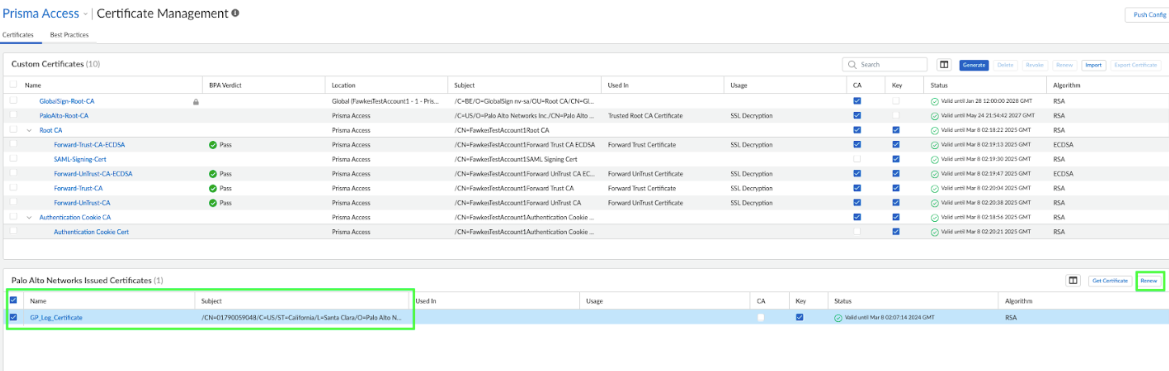
- Renew an ADEM/GP Log Certificate in Strata Cloud Manager
- In Strata Cloud Manager, ensure the scope is Prisma Access.
- Navigate to ConfigurationNGFW and Prisma Access.
- Select ObjectsCertificate Management.
- Under Palo Alto Networks Issued Certificates, select
the certificate, and click Renew.
![]()
- Push Config.
- Renew an ADEM/GP Log Certificate in Panorama
- Go to Mobile_User_TemplateDeviceCertificate ManagementCertificates, and delete the globalprotect_app_log_cert certificate.
- Go to the Panorama tab, and select Cloud ServicesConfiguration.
- In the GlobalProtect App Log Collection and Autonomous DEM section, click Renew Certificate for GlobalProtect App Log Collection and Autonomous DEM to renew the certificate.
- Commit and Push.
- Renew an SSL Decryption Certificate
- Renew an SSL Decryption Certificate in Strata Cloud Manager
- Renew a locally generated certificate
- Go to Configuration NGFW and Prisma Access.
- Click ObjectsCertificate Management.
- Under the Palo Alto Networks Certificate, select the certificate, and Renew.
- Push to Config.
- Generate a certificate signing request (CSR)
- Go to Configuration NGFW and Prisma Access.
- Click ObjectsCertificate Management, and select Generate.
- Enter the Certificate Name (be
sure to note this name for later use) and the
Common Name (usually the
FQDN). For Signed By, select
External Authority (CSR).Don't select Certificate Authority.
- Complete the remaining details, such as
Country and
Organization. Check with the Certificate Authority about their requirements for Certificate Attribute formatting and criteria.
- Click Generate to create the CSR.
- Push Config for the new certificate to take effect. The confirmation window appears when the CSR is generated.
- Import the signed certificate.
- Enter the name (this is the Certificate Name you entered previously) of the certificate to import.
- Click Import.
- Click Choose File to select the
signed certificate from the Certificate Authority, and
click OK.Don't click the Import Private Key check box, as the private key is already on the firewall.
- Depending on the Certificate Authority used, you may need to chain the intermediate certificate with the server certificate and import it before completing this step. For more information, see How to Install a Chained Certificate Signed by a Public CA.
- Click OK. The certificate now appears as valid, and the key check box is selected. Use the new third-party certificate for GlobalProtect or any other function.
- Renew a locally generated certificate
- Renew an SSL Decryption Certificate in Panorama
- Renew a locally generated certificate
- Select the certificate to be renewed under GUI: Device Certificate ManagementCertificates.
- Select Renew, enter the New Expiration Interval in days, and click OK. The system modifies the expiration date to reflect the change.
- Commit and Push your changes.
- Generate a CSR
- Go to DeviceCertificate ManagementCertificates.
- Click Generate at the bottom of the screen.
- Enter the Certificate Name (be
sure to note this name for later use) and the
Common Name (usually the
FQDN). For Signed By, select
External Authority (CSR).Don't select Certificate Authority.
- Complete the remaining details, such as
Country and
Organization. Check with the Certificate Authority about their requirements for Certificate Attribute formatting and criteria.
- Click Generate to create the CSR.
- Commit and Push again for the new certificate to take effect.
- You'll see the confirmation window when the CSR is generated.
- Import the signed certificate
- Enter the name (this is the Certificate Name you entered previously) of the certificate to import.
- Click Import at the bottom of the screen.
- Click Browse to select the signed
certificate received from the Certificate
Authority, and click
OK.Don't click the Import Private Key check box, as the private key is already on the firewall.
- Depending on the Certificate Authority used, you may need to chain the intermediate certificate with the server certificate and import it before completing this step. For more information, see How to Install a Chained Certificate Signed by a Public CA.
- Click OK. The certificate now appears as valid, and the key check box is selected. A new third-party certificate can now be used for GlobalProtect or any other function.
- Renew a locally generated certificate
- Renew an SSL Decryption Certificate in Strata Cloud Manager
Optional—For both Strata Cloud Manager and Panorama environments, you can
refer to Certificate Renewal for Autonomous Digital
Experience Management for additional details.