Prisma Access
Manage Prisma SASE 5G
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Manage Prisma SASE 5G
Learn how to secure 5G traffic with Prisma Access.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
To activate this functionality, reach out to your Palo Alto
Networks account representative.
|
The Prisma SASE 5G solution extends Prisma Access security capabilities to 5G
networks, enabling service providers to offer comprehensive AI-powered security for
enterprises’ 5G-connected users and devices. To integrate security with 5G core
networks, SASE 5G uses Prisma Access to provide Agentless
Security services for 5G-connected devices.
The Prisma SASE 5G solution integrates with 5G network authentication and
authorization mechanisms, enabling Service Providers to orchestrate Security policy
rules based on the International Mobile Equipment Identity (IMEI), International
Mobile Subscriber Identity (IMSI), or Access Point Name (APN) corresponding to the
5G endpoint's SIM identity. This integration allows for seamless security
enforcement across 5G networks, (including roaming scenarios) and wireline networks.
Prisma Access secures 5G traffic using a Security Processing Node (SPN). Prisma Access identifies the traffic based on IMEI, IMSI, and APN, synchronizes
the mobile users' identity using the Cloud Identity Engine, and authenticates
the users' 5G devices using RADIUS. Using Palo Alto Networks Security policy rules,
you can write policy rules based on users and user groups to allow and deny traffic
for both private and public apps. You can also use Advanced Threat Prevention, Advanced URL Filtering, Advanced WildFire, and other advanced security
capabilities that integrate with Prisma Access to make sure that access to your
private and public apps are secure.

Prisma SASE 5G separates traffic into a control plane and a data plane.
- The Data Plane uses the backbone to establish
connectivity between the 5G network and Prisma Access. This backbone enables
egress traffic forwarding to Prisma Access, where you can use Security policy
rules to enforce security before egressing the traffic to public and private
apps. You can use either your service provider's backbone (interconnect) or specify traffic to use either your interconnect or the Prisma Access backbone in a hybrid backbone deployment. You select the egress method when you configure Prisma SASE 5G in the Prisma Access web interface.
- The Control Plane manages authentication and authorization from the 5G Network, using RADIUS authentication based on IMEI, IMSI, and APN credentials from the 5G Network
Configure Prisma SASE 5G
Before you begin, make sure that you have:
- Accessed the Strata Multitenant Cloud Manager and Created a top-level, root, parent tenant.
- Added tenants as children of the root-level tenant.
Also note the following caveats for Prisma SASE 5G:
- GCP partner (not dedicated) interconnects are supported.
- Access the Strata Multitenant Cloud Manager and make sure that you're in the topmost, root-level, parent tenant of your multitenant hierarchy.Add a service provider backbone through the Strata Multitenant Cloud Manager.You manage a SASE 5G backbone the same as you manage a Service Provider backbone.Set up a GCP partner interconnect; any other interconnect types are not supported.Add a service provider connection through the Strata Multitenant Cloud Manager.Configure IP address pools using Strata Multitenant Cloud Manager.
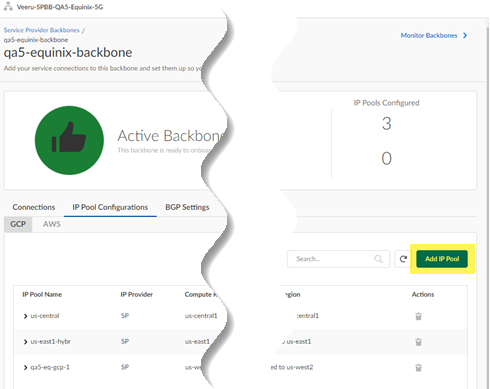
- From the root-level, parent tenant, go to ManageService Provider Backbones and Manage Connections.Select IP Pool Configurations and select GCP.
![]() Add IP Pool.
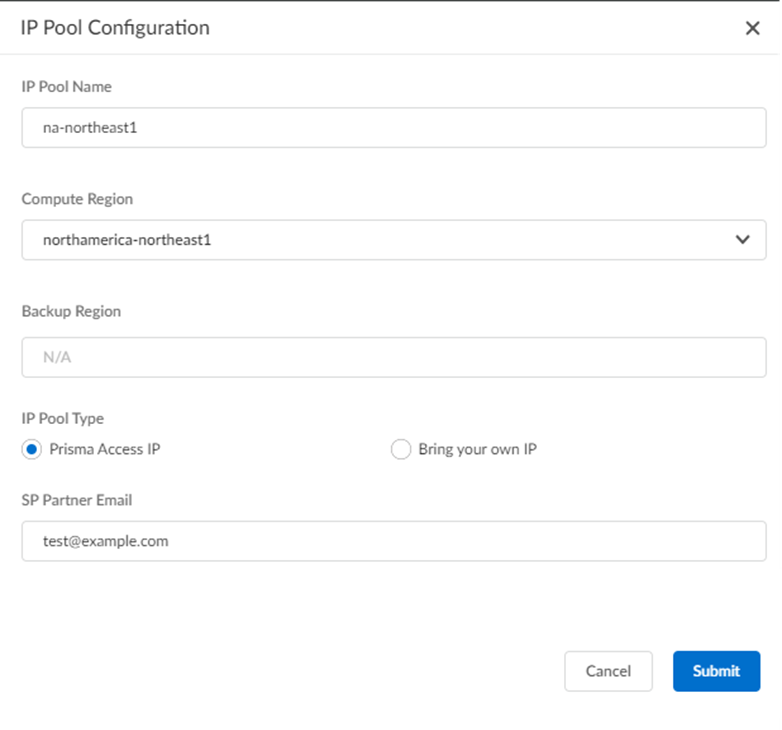
Add IP Pool.![]() Enter an IP address pool configuration.
Enter an IP address pool configuration.- Enter an IP Pool Name.
- Select a Compute Region.
- Select a Backup Region.
- Choose an IP Pool Type of
Prisma Access IP or
Bring your own IP and complete
based on the steps that follow for your scenario.
- To use a Prisma Access IP,
enter an SP Partner Email
address.Palo Alto Networks assigns these IP addresses to you, and a Palo Alto Networks SRE will provide you in an email with the IP addresses that you have been assigned.
- To Bring your own IP, select
a Location and enter an
IP Pool.Enter multiple values separated by commas (no spaces) or enter an address with a subnet mask with a mask between /24 and /29 inclusive.You can optionally add multiple IP addresses by, after submitting your changes, selecting Add/Edit IP Pool in the IP address pool configuration you created and adding another subnet. The maximum number of subnets you can assign is 10, and after the IP subnet is consumed, you can't change it.
![]()
- To use a Prisma Access IP,
enter an SP Partner Email
address.
Submit your changes.(Optional) Configure BGP Settings.![]() Configure the Control Plane component of Prisma SASE 5G.
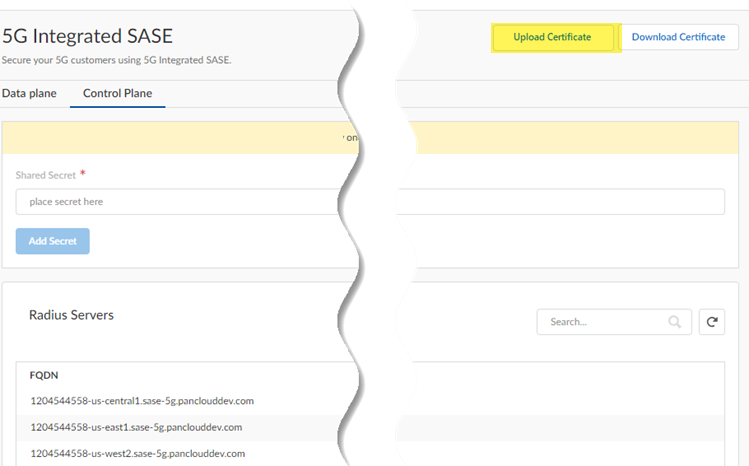
Configure the Control Plane component of Prisma SASE 5G.- Log in to the root-level, parent tenant.From Strata Multitenant Cloud Manager, go to Manage5G Integrated SASEService ProviderControl Plane.Download Certificate and save it locally.
![]() This certificate is a mutual TLS (mTLS) certificate, used when both the RADIUS server and Prisma Access require a certificate for authentication.Prisma SASE 5G integrates with the 5G authentication system using RADIUS. For secure communications, Prisma SASE 5G uses a Mutual TLS authentication. For successful authentication, you download the root certificate of the Prisma SASE RADIUS server.On each of your RADIUS proxies, install this root certificate in your certificate authority store.To upload the certificate from the RADIUS server, download the RADIUS server's certificate; then, and select it.Import the root certificate with public key signing the RADIUS proxy client certificate and Upload Certificate to Strata Multitenant Cloud Manager.You use this certificate to authenticate the RADIUS proxy server's identity. After you upload it and you enable the connection, you can't change it.
This certificate is a mutual TLS (mTLS) certificate, used when both the RADIUS server and Prisma Access require a certificate for authentication.Prisma SASE 5G integrates with the 5G authentication system using RADIUS. For secure communications, Prisma SASE 5G uses a Mutual TLS authentication. For successful authentication, you download the root certificate of the Prisma SASE RADIUS server.On each of your RADIUS proxies, install this root certificate in your certificate authority store.To upload the certificate from the RADIUS server, download the RADIUS server's certificate; then, and select it.Import the root certificate with public key signing the RADIUS proxy client certificate and Upload Certificate to Strata Multitenant Cloud Manager.You use this certificate to authenticate the RADIUS proxy server's identity. After you upload it and you enable the connection, you can't change it.![]() Prisma SASE 5G relies on specific RADIUS attributes to uniquely identify user equipment and enforce security policies. Ensure that the required attributes are correctly configured in the RADIUS messages to enable proper health monitoring and policy enforcement.Add a proxy server connection.
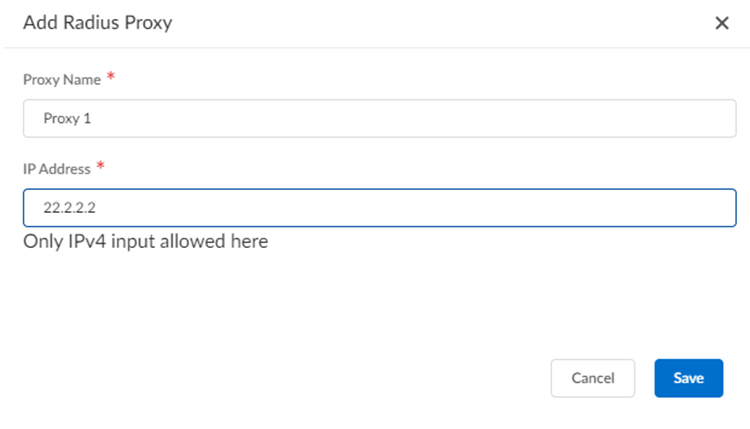
Prisma SASE 5G relies on specific RADIUS attributes to uniquely identify user equipment and enforce security policies. Ensure that the required attributes are correctly configured in the RADIUS messages to enable proper health monitoring and policy enforcement.Add a proxy server connection.- Go to Manage5G Integrated SASEService ProviderControl Plane and Add Proxy.
![]() Enter a unique Proxy Name for the RADIUS proxy and the IP address used for the proxy and Save your changes when complete.
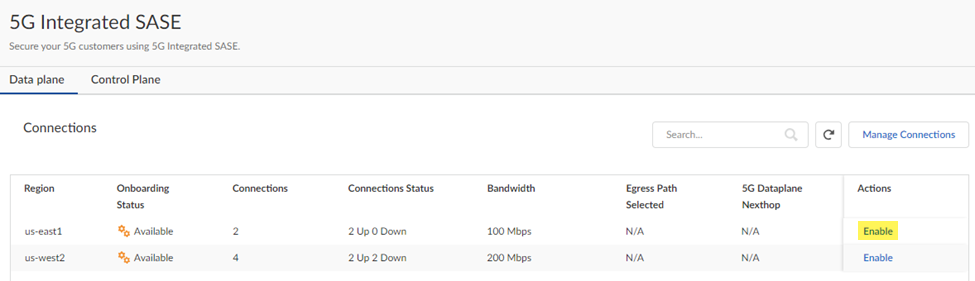
Enter a unique Proxy Name for the RADIUS proxy and the IP address used for the proxy and Save your changes when complete.![]() From the Data Plane tab, select the connection you created and configured and Enable the connection.Don't enable your connection until you have all Prisma SASE 5G configuration is complete, or the connection can't successfully initiate.
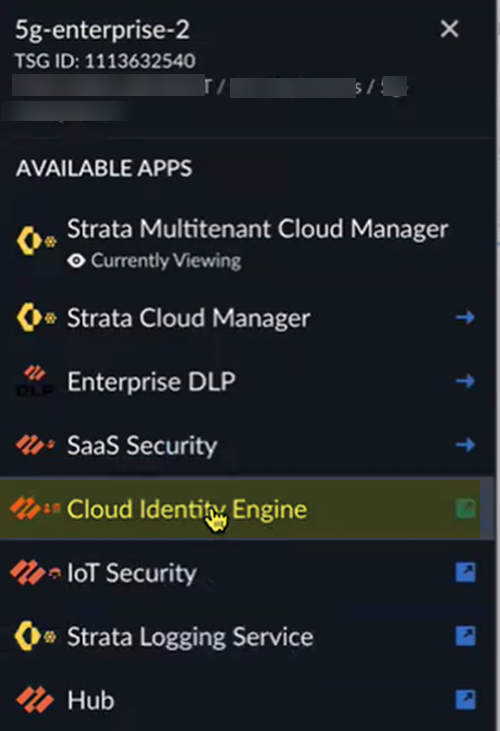
From the Data Plane tab, select the connection you created and configured and Enable the connection.Don't enable your connection until you have all Prisma SASE 5G configuration is complete, or the connection can't successfully initiate.![]() Set up the Cloud Identity Engine for your child tenant.You set up the Cloud Identity Engine before you add identities and identity groups. Configuring the Cloud Identity Engine allows Prisma SASE 5G to populate the 5G identities you configure throughout Strata Cloud Manager.
Set up the Cloud Identity Engine for your child tenant.You set up the Cloud Identity Engine before you add identities and identity groups. Configuring the Cloud Identity Engine allows Prisma SASE 5G to populate the 5G identities you configure throughout Strata Cloud Manager.- From the child tenant of the root-level tenant, go to Cloud Identity Engine.
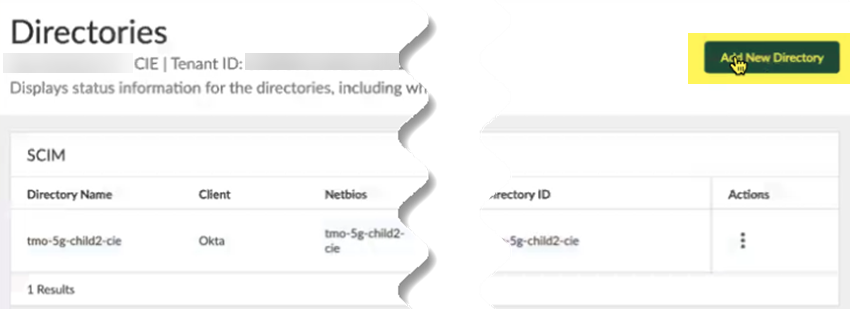
![]() Add New Directory.
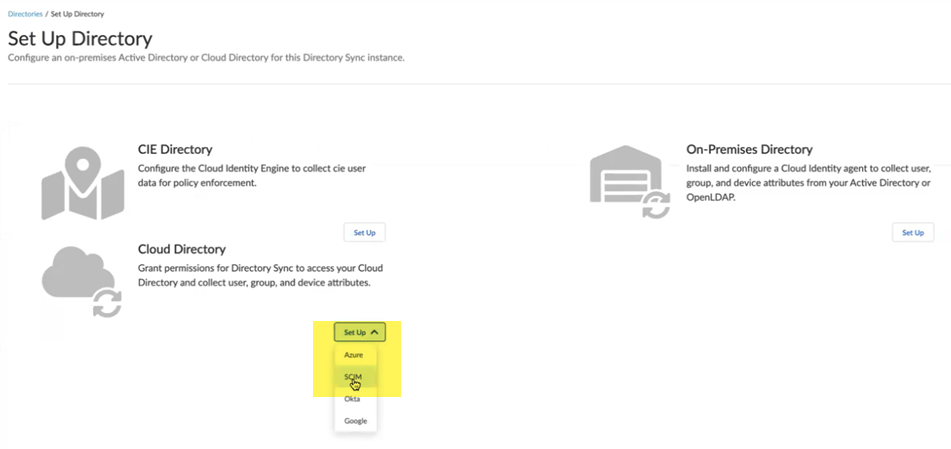
Add New Directory.![]() Create a new SCIM directory by selecting Cloud DirectorySCIM.
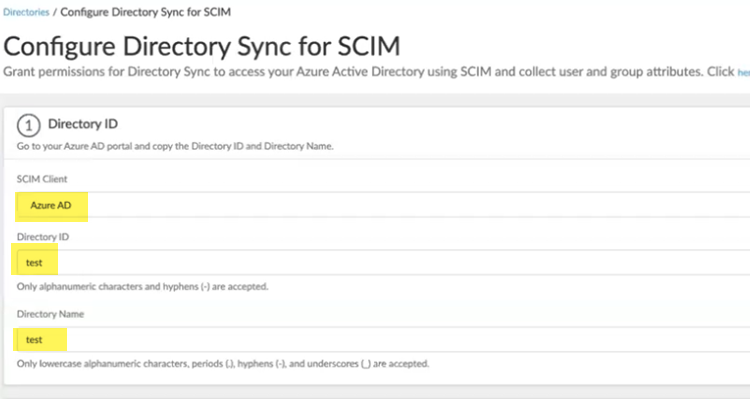
Create a new SCIM directory by selecting Cloud DirectorySCIM.![]() Choose a SCIM Client and enter a unique Directory ID and Directory Name.
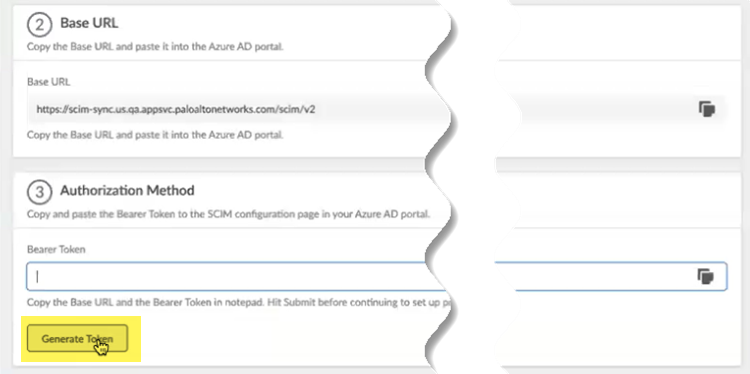
Choose a SCIM Client and enter a unique Directory ID and Directory Name.![]() Make a note of the Directory Name and the BASE URL.You use this URL to configure the Cloud Identity Engine in Strata Multitenant Cloud Manager.Generate Token.
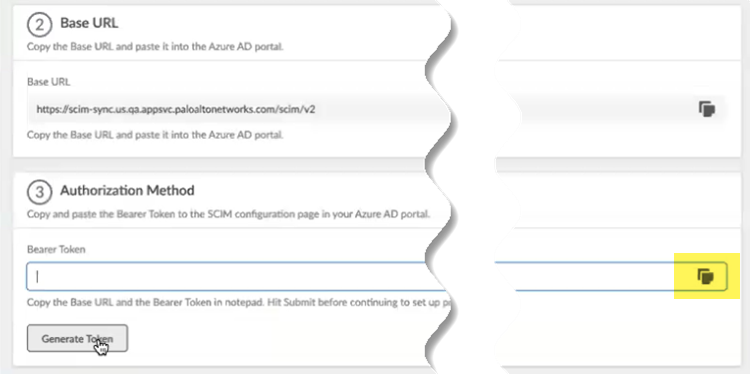
Make a note of the Directory Name and the BASE URL.You use this URL to configure the Cloud Identity Engine in Strata Multitenant Cloud Manager.Generate Token.![]() Copy the token by clicking the copy icon on the right.
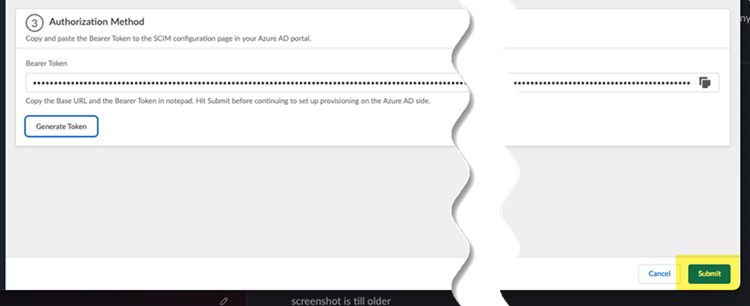
Copy the token by clicking the copy icon on the right.![]() Submit the token to apply the changes to the Cloud Identity Engine.
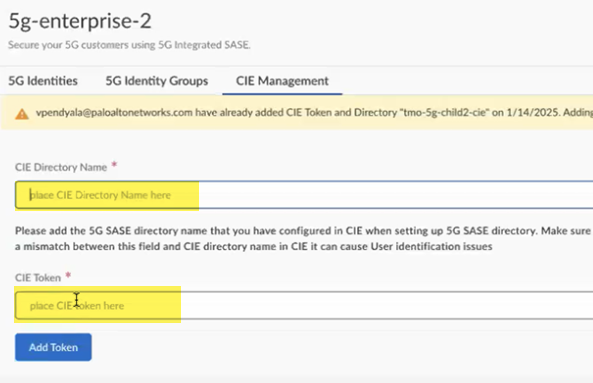
Submit the token to apply the changes to the Cloud Identity Engine.![]() Return to the Strata Multitenant Cloud Manager select Manage5G Integrated SASEService ProviderTenantNameCIE Management.Enter the CIE Directory Name, using the same name you configured in the Cloud Identity Engine, and paste in the CIE Token you copied during Cloud Identity Engine setup.
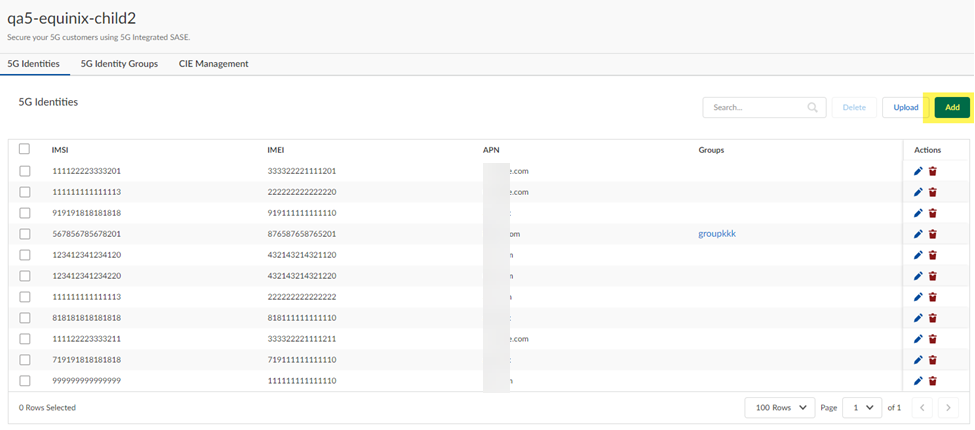
Return to the Strata Multitenant Cloud Manager select Manage5G Integrated SASEService ProviderTenantNameCIE Management.Enter the CIE Directory Name, using the same name you configured in the Cloud Identity Engine, and paste in the CIE Token you copied during Cloud Identity Engine setup.![]() Add your mobile user identities by going to Manage5G Integrated SASEService ProviderTenantName5G Identities, where TenantName is a child tenant under the parent, root-level tenant, and Add user identities.You can either upload identities one at a time in the web interface, or in bulk using a .csv file. If you use a .csv file:
Add your mobile user identities by going to Manage5G Integrated SASEService ProviderTenantName5G Identities, where TenantName is a child tenant under the parent, root-level tenant, and Add user identities.You can either upload identities one at a time in the web interface, or in bulk using a .csv file. If you use a .csv file:- A maximum of 500 records are supported for each .csv file.
- You can upload multiple .csv files; however upload the .csv files one at a time and wait until you get a message that the records have been successfully added before uploading the next file.
- Make sure that the records are in this order:
- IMEI
- IMSI
- APN
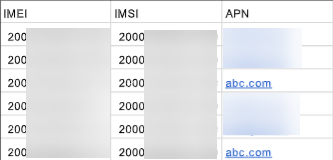
All three fields are required. The following is a sample .csv file.![]()
- If the upload fails, a message displays that indicates the line that failed.
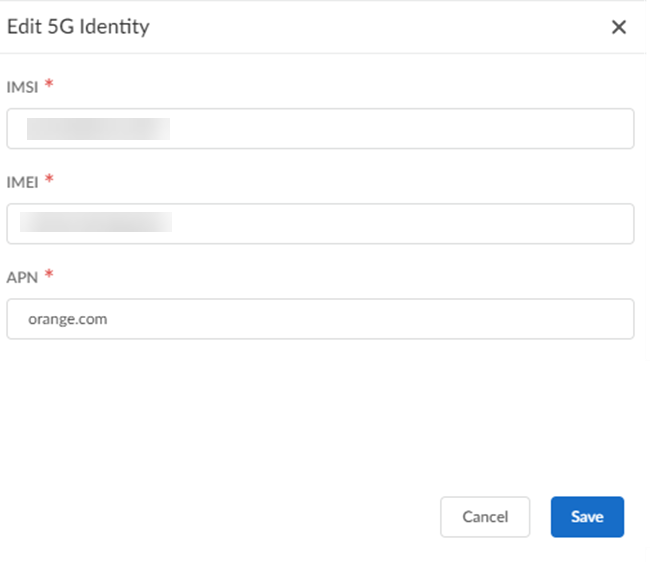
- To add identities one at a time:
- Add the identities.
![]()
- Add the IMSI, IMEI, and APN numbers.
- Save your changes or, to add more
identities, Save, and Add More.
![]()
- Add the identities.
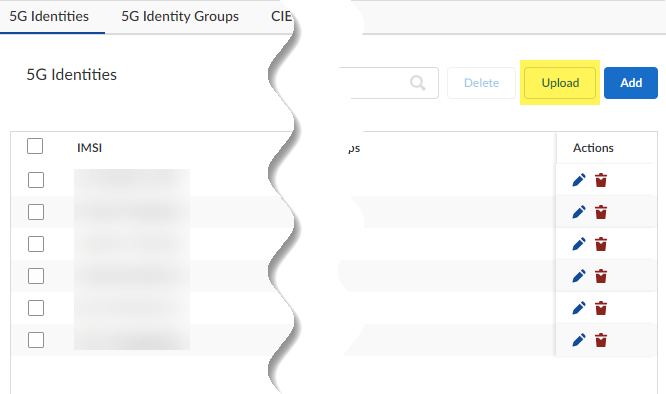
- To add identities from a .csv file:
- Upload the .csv file that has the 5G
identities.
![]()
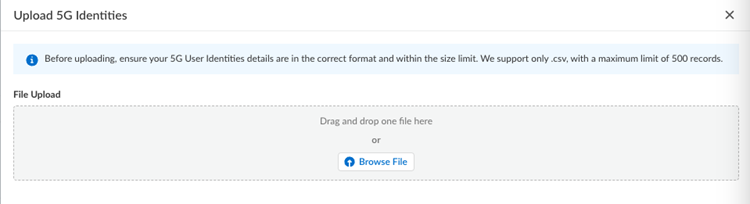
- Drag and drop the file, or Browse File,
and Upload the file.
![]()
- Upload the .csv file that has the 5G
identities.
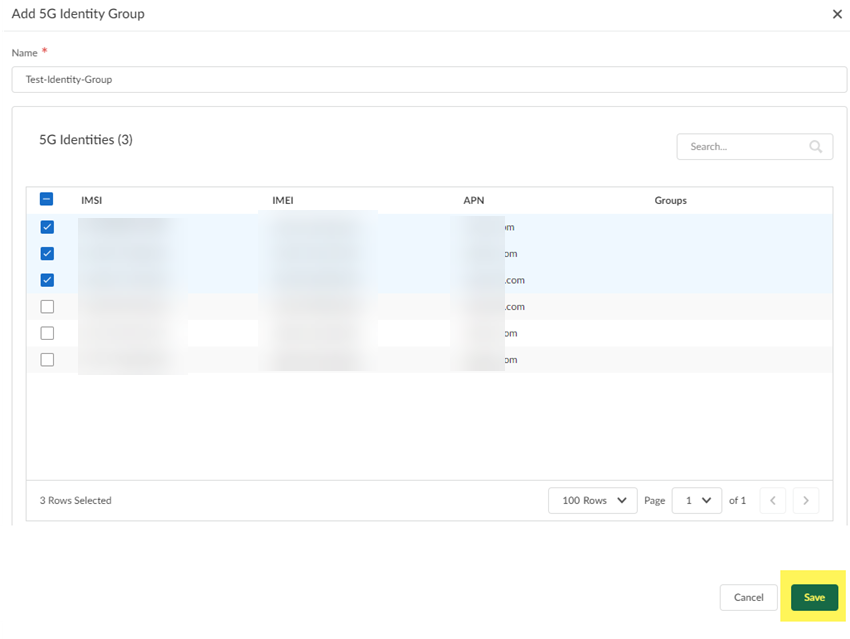
Add 5G identity groups.Use these groups in Security policy rules to allow or block the access of public and private apps.- Go to Manage5G Integrated SASEService ProviderTenantName5G Identity Groups, where TenantName is a tenant under the root-level tenant, and Add the identity groups.Specify a unique Name for the group.Select the 5G identities to add to the group and Save your changes.
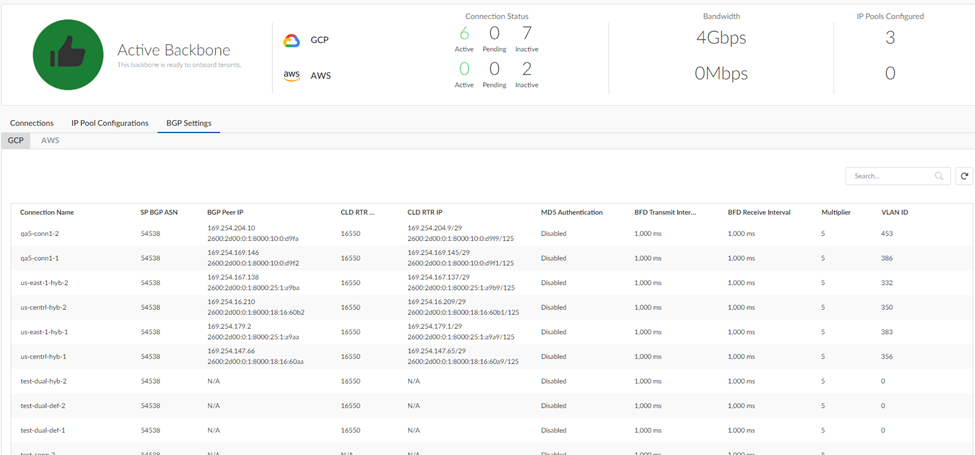
![]() View and monitor the statistics for Prisma SASE 5G.
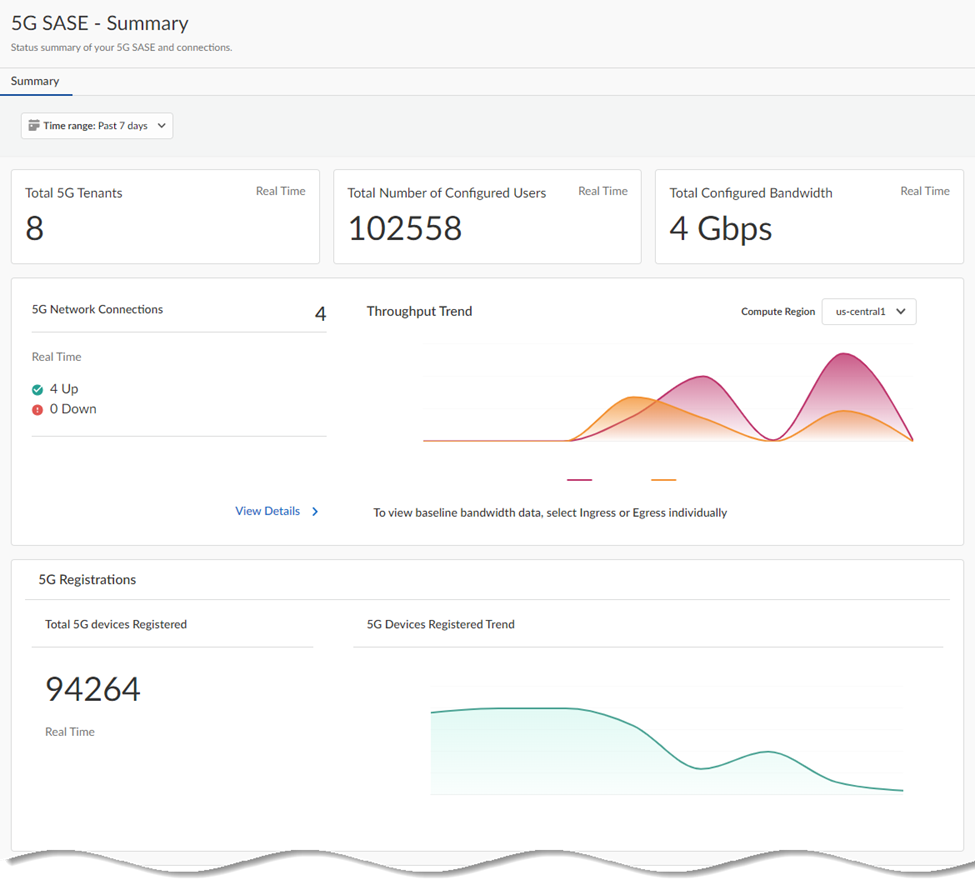
View and monitor the statistics for Prisma SASE 5G.- From the root-level tenant, go to Monitor5G Summary.View the information in the fields.
- Total 5G Tenants—The number of tenants under the root-level tenant.
- Total Number of Configured Users—The number of users in the deployment.
- Total Configured Bandwidth—The total bandwidth you have configured.
- 5G Network Connections—The number of 5G network connections.
- Throughput Trend
- 5G Registrations
![]()
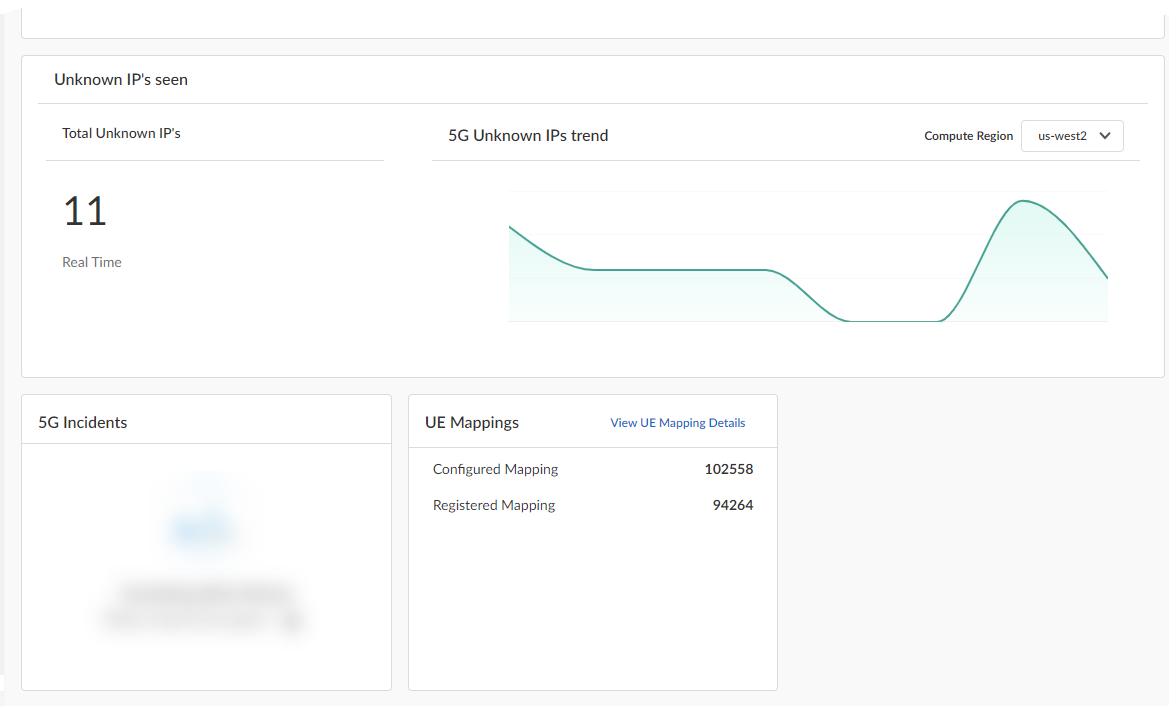
- Unknown IP's Seen
- 5G Incidents
- UE Mappings
![]()