Prisma Access
Configure Remote Network and Service Connection Connected with a WAN Link
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure Remote Network and Service Connection Connected with a WAN Link
Remote network and service connection connected with a WAN link.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
If you have a deployment where a remote network location(s) and an HQ or data center
with a service connection are directly connected over a WAN link, to ensure optimal
routing (with eBGP) you must:
- Add a static route to the eBGP router address. In addition to the default route that sends all traffic to Prisma Access, you must add a static route locally on the IPSec-capable device or router at the remote network(s).
- Filter the routes that are advertised from the IPSec capable device or router at HQ to the eBGP peers at other directly connected locations. As a best practice, configure the BGP router at HQ to only advertise routes that you want to allow across the WAN link; you ensure that the eBGP router at HQ does not advertise the routes it learns from Prisma Access to other remote network location(s) secured by Prisma Access. In this example, the eBGP router at HQ only advertises routes that employees from the branch office will need to connect to the servers (subnets) at HQ.
The following illustration shows a retail business with two paths to the servers at
the HQ location. One path is a WAN link that provides direct connectivity for
employees accessing servers at HQ, and the other path secures traffic generated by
other users at this location. For example, traffic generated by customers accessing
the retailer’s website over Wifi or using the kiosk at the branch office to check
inventory. This traffic is sent through the tunnel to the remote network and on to
HQ.

To set up this configuration, create a remote network connection and create a service
connection to onboard the remote network and HQ locations. The details below show
how to set up the router configuration at each location to ensure optimal routing:
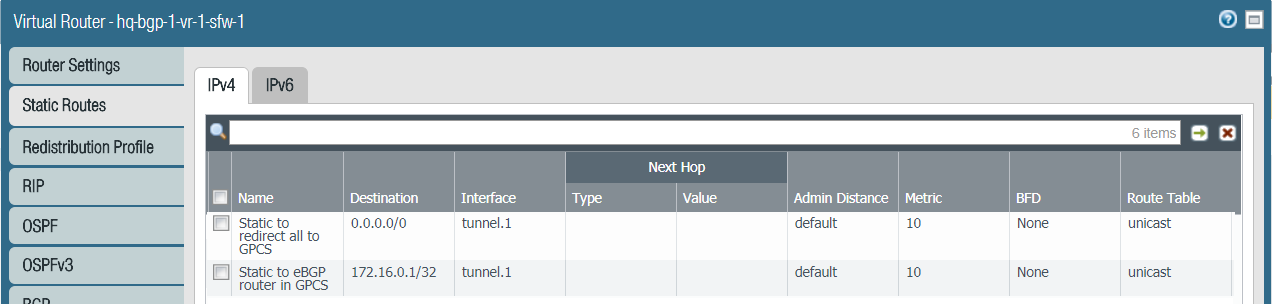
- Add the static routes on your router or on-premises IPSec capable device at the remote network location.If you have a Palo Alto Networks firewall at the edge of the WAN link, on NetworkVirtual RoutersStatic Routes, Add the static routes:
![]() Configure the routes that you want to advertise to another directly connected location over the WAN link.In this example, you need to configure this on the at HQ location. If you have an on-premises Palo Alto Networks firewall at the edge of the WAN link, you can set up route redistribution and configure which BGP routes to export on NetworkVirtual RoutersBGP.
Configure the routes that you want to advertise to another directly connected location over the WAN link.In this example, you need to configure this on the at HQ location. If you have an on-premises Palo Alto Networks firewall at the edge of the WAN link, you can set up route redistribution and configure which BGP routes to export on NetworkVirtual RoutersBGP.![]()