Advanced Threat Prevention Support for Zero-day Exploit Prevention
Table of Contents
11.0 (EoL)
Expand all | Collapse all
End-of-Life (EoL)
Advanced Threat Prevention Support for Zero-day Exploit Prevention
Palo Alto Networks now operates new inline
deep learning detection engines in the Advanced Threat Prevention
cloud to analyze traffic for command injection and SQL injection
vulnerabilities in real-time to protect users against zero-day threats.
By operating cloud-based detection engines, you can access a wide
array of detection mechanisms that are updated and deployed automatically
without requiring the user to download update packages or operate process
intensive, firewall-based analyzers which can sap resources. Inline
cloud analysis for your firewall Vulnerability Protection profile
supports two analysis engines: SQL injection and Command injection.
Additional analysis models are delivered through content updates,
however, enhancements to existing models are performed as a cloud-side
update, requiring no firewall update. Inline cloud analysis is enabled
and configured using the Vulnerability Protection profile and requires
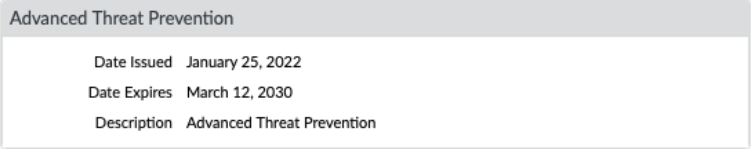
an active Advanced Threat Prevention license.
- Log in to the PAN-OS web interface.To take advantage of inline cloud analysis of vulnerability exploits, you must have an active Advanced Threat Prevention subscription.To verify subscriptions for which you have currently-active licenses, select DeviceLicenses and verify that the appropriate licenses are available and have not expired.
![]() Update or create a new Vulnerability Protection Security profile to enable inline cloud analysis.
Update or create a new Vulnerability Protection Security profile to enable inline cloud analysis.![]()
- Select an existing Vulnerability Protection security profile or Add a new one (ObjectsSecurity ProfilesVulnerability Protection).
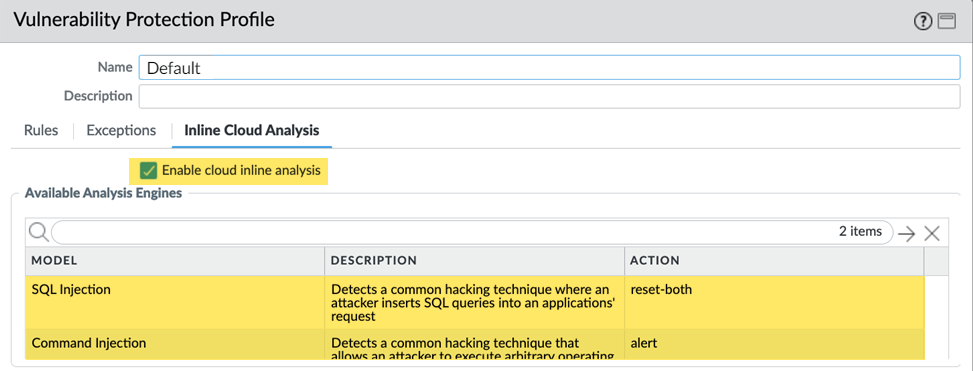
- Select your Vulnerability Protection profile and then go to Inline Cloud Analysis and Enable cloud inline analysis.
- Specify an Action to take when a vulnerability exploit is detected using a corresponding analysis engine. There are currently two analysis engines available: SQL Injection and Command Injection.
- Allow—The request is allowed and no log entry is generated.
- Alert—The request is allowed and a Threat log entry is generated.
- Reset-Client—Resets the client-side connection.
- Reset-Server—Resets the server-side connection.
- Reset-Both—Resets the connection on both the client and server ends.
- Click OK to exit the Vulnerability Protection Profile configuration dialog and Commit your changes.
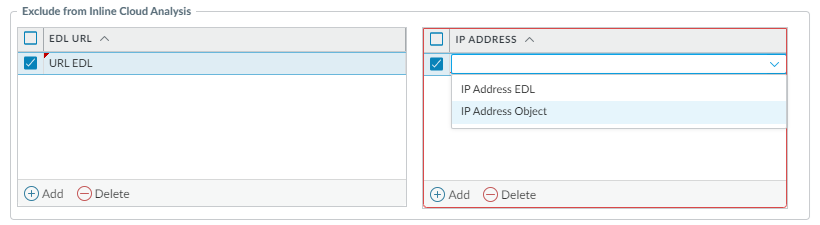
(Optional) Add URL and/or IP address exceptions to your Vulnerability Protection profile if Inline Cloud Analysis produces false-positives. You can add exceptions by specifying an external dynamic list (URL or IP address list types) or an Addresses object.- Add an External Dynamic Lists or [IP] Addresses object exception.
- Select Objects > Security Profiles > Vulnerability to return to your Vulnerability Protection profile.
- Select a Vulnerability profile for which you want to exclude specific URLs and/or IP addresses and then select Inline Cloud Analysis.
- Add an EDL URL or IP Address, depending on the type of exception you want to add, and then select a pre-existing URL or IP address external dynamic list. If none are available, create a new external dynamic list. For IP address exceptions, you can, optionally, select an Addresses object list.
![]()
- Click OK to save the Vulnerability Protection profile and Commit your changes.
Install an updated firewall device certificate used to authenticate to the Advanced Threat Prevention inline cloud analysis service. Repeat for all firewalls enabled for inline cloud analysis.If you have already installed an updated firewall device certificate as part of your IoT Security, Device Telemetry, Advanced Threat Prevention, or Advanced URL Filtering onboarding process, this step is not necessary.(Optional) Set the Cloud Content Fully Qualified Domain Name (FQDN) used by the firewall to handle inline cloud analysis service requests.(Optional) Verify the status of your firewall connectivity to the Advanced Threat Prevention cloud service.Use the following CLI command on the firewall to view the connection status.show ctd-agent status security-clientFor example:show ctd-agent status security-client ... Security Client AceMlc2(1) Current cloud server: hawkeye.services-edge.paloaltonetworks.com Cloud connection: connected ...
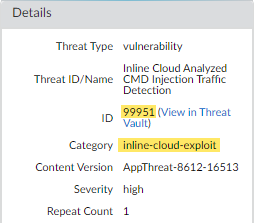
CLI output shortened for brevity.If you are unable to connect to the Advanced Threat Prevention cloud service, verify that the cloud content FQDN is not being blocked: hawkeye.services-edge.paloaltonetworks.com. If you specified a regional cloud content server in step 6, enter that FQDN instead.(Optional) Monitor activity on the firewall for vulnerability exploits that have been detected using inline cloud analysis.- Select MonitorLogsThreat and filter by ( category-of-threatid eq inline-cloud-exploit ) to view logs that have been analyzed using the inline cloud analysis mechanism of Advanced Threat Prevention. Inline exploit (SQL injection) threats have an ID of 99950 while inline exploit (command injection) threats have an ID of 99951.
![]() Select a log entry to view the details of a vulnerability exploit.The threat Category is displayed under the Details pane of the detailed log view. Vulnerability exploits that have been detected using inline cloud analysis have a threat category of inline-cloud-exploit.
Select a log entry to view the details of a vulnerability exploit.The threat Category is displayed under the Details pane of the detailed log view. Vulnerability exploits that have been detected using inline cloud analysis have a threat category of inline-cloud-exploit.![]()