Upgrade a Standalone Firewall
Table of Contents
11.1 & Later
Expand all | Collapse all
-
-
- Upgrade Panorama with an Internet Connection
- Upgrade Panorama Without an Internet Connection
- Install Content Updates Automatically for Panorama without an Internet Connection
- Upgrade Panorama in an HA Configuration
- Migrate Panorama Logs to the New Log Format
- Upgrade Panorama for Increased Device Management Capacity
- Upgrade Panorama and Managed Devices in FIPS-CC Mode
- Downgrade from Panorama 11.1
- Troubleshoot Your Panorama Upgrade
-
- What Updates Can Panorama Push to Other Devices?
- Schedule a Content Update Using Panorama
- Panorama, Log Collector, Firewall, and WildFire Version Compatibility
- Upgrade Log Collectors When Panorama Is Internet-Connected
- Upgrade Log Collectors When Panorama Is Not Internet-Connected
- Upgrade a WildFire Cluster from Panorama with an Internet Connection
- Upgrade a WildFire Cluster from Panorama without an Internet Connection
- Upgrade Firewalls When Panorama Is Internet-Connected
- Upgrade Firewalls When Panorama Is Not Internet-Connected
- Upgrade a ZTP Firewall
- Revert Content Updates from Panorama
-
Upgrade a Standalone Firewall
Follow these steps to upgrade a standalone firewall to PAN-OS 11.1.
Review the PAN-OS 11.1 Release Notes and then use the
following procedure to upgrade a firewall that is not in an HA configuration to
PAN-OS 11.1.
If your firewalls
are configured to forward samples to a WildFire appliance for analysis,
you must upgrade the WildFire appliance before upgrading
the forwarding firewalls.
To avoid
impacting traffic, plan to upgrade within the outage window. Ensure
the firewall is connected to a reliable power source. A loss of
power during an upgrade can make the firewall unusable.
- Save a backup of the current configuration file.Although the firewall automatically creates a configuration backup, it is a best practice to create and externally store a backup before you upgrade.
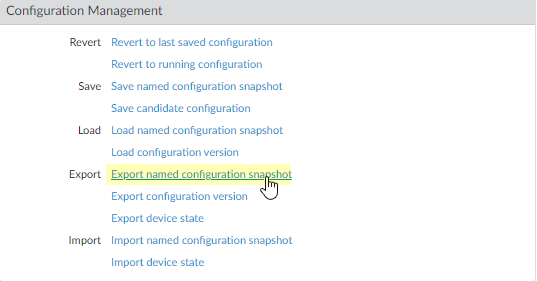
- Select DeviceSetupOperations and click Export named configuration snapshot.
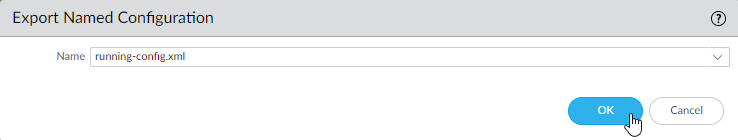
![]() Select the XML file that contains your running configuration (for example, running-config.xml) and click OK to export the configuration file.
Select the XML file that contains your running configuration (for example, running-config.xml) and click OK to export the configuration file.![]() Save the exported file to a location external to the firewall. You can use this backup to restore the configuration if you have problems with the upgrade.(Optional) If you have enabled User-ID, after you upgrade, the firewall clears the current IP address-to-username and group mappings so that they can be repopulated with the attributes from the User-ID sources. To estimate the time required for your environment to repopulate the mappings, run the following CLI commands on the firewall.
Save the exported file to a location external to the firewall. You can use this backup to restore the configuration if you have problems with the upgrade.(Optional) If you have enabled User-ID, after you upgrade, the firewall clears the current IP address-to-username and group mappings so that they can be repopulated with the attributes from the User-ID sources. To estimate the time required for your environment to repopulate the mappings, run the following CLI commands on the firewall.- For IP address-to-username mappings:
- show user user-id-agent state all
- show user server-monitor state all
- For group mappings: show user group-mapping statistics
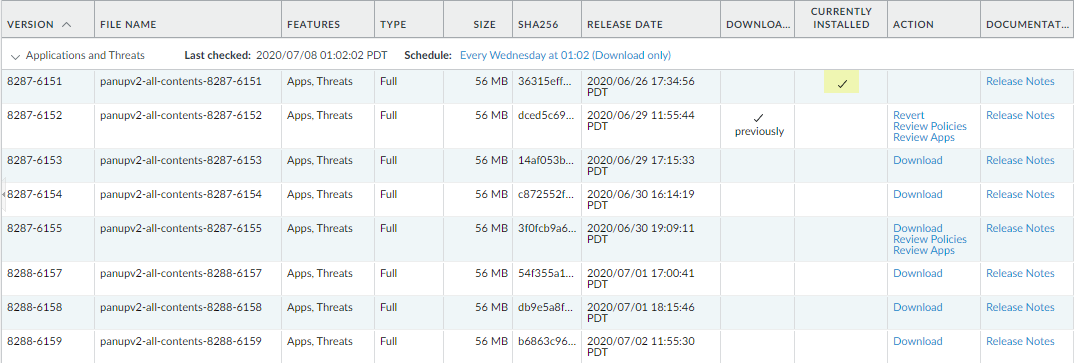
Ensure that the firewall is running the latest content release version.Refer to the Release Notes for the minimum content release version you must install for a PAN-OS 11.1 release. Make sure to follow the Best Practices for Applications and Threats Content Updates.- Select DeviceDynamic Updates and see which Applications or Applications and Threats content release version is Currently Installed.
![]() If the firewall is not running the minimum required content release version or a later version required for PAN-OS 11.1, Check Now to retrieve a list of available updates.Locate and Download the desired content release version.After you successfully download a content update file, the link in the Action column changes from Download to Install for that content release version.Install the update.Determine the Upgrade Path to PAN-OS 11.1 and later releasesReview PAN-OS Upgrade Checklist, the known issues and changes to default behavior in the Release Notes and Upgrade/Downgrade Considerations for each release through which you pass as part of your upgrade path.(Best Practices) If you are leveraging Strata Logging Service, install the device certificate.The firewall automatically switches to using the device certificate for authentication with Strata Logging Service ingestion and query endpoints on upgrade to PAN-OS 11.1.If you do not install the device certificate prior to upgrade to PAN-OS 11.1, the firewall continues to use the existing logging service certificates for authentication.Upgrade to PAN-OS 11.1.If your firewall does not have internet access from the management port, you can download the software image from the Palo Alto Networks Customer Support Portal and then manually Upload it to your firewall.
If the firewall is not running the minimum required content release version or a later version required for PAN-OS 11.1, Check Now to retrieve a list of available updates.Locate and Download the desired content release version.After you successfully download a content update file, the link in the Action column changes from Download to Install for that content release version.Install the update.Determine the Upgrade Path to PAN-OS 11.1 and later releasesReview PAN-OS Upgrade Checklist, the known issues and changes to default behavior in the Release Notes and Upgrade/Downgrade Considerations for each release through which you pass as part of your upgrade path.(Best Practices) If you are leveraging Strata Logging Service, install the device certificate.The firewall automatically switches to using the device certificate for authentication with Strata Logging Service ingestion and query endpoints on upgrade to PAN-OS 11.1.If you do not install the device certificate prior to upgrade to PAN-OS 11.1, the firewall continues to use the existing logging service certificates for authentication.Upgrade to PAN-OS 11.1.If your firewall does not have internet access from the management port, you can download the software image from the Palo Alto Networks Customer Support Portal and then manually Upload it to your firewall.- Select DeviceSoftware and click Check Now to display the latest PAN-OS updates.Only the versions for the next available PAN-OS release are displayed. For example, if the PAN-OS 11.1 is installed on the firewall, then only PAN-OS 11.1 releases are displayed.(PAN-OS 11.1.3 and later releases) By default, the preferred releases and the corresponding base releases are displayed. To view the preferred releases only, disable (clear) the Base Releases checkbox.Select PanoramaDevice DeploymentSoftwareActionValidatePanoramaDevice DeploymentSoftwareActionValidate to view all intermediate software and content images required to upgrade to 11.1.0.Download the intermediate software and content images.After you download the image (or, for a manual upgrade, after you upload the image), Install the image.After the installation completes successfully, reboot using one of the following methods:
- If you are prompted to reboot, click Yes.
- If you are not prompted to reboot, select DeviceSetupOperations and click Reboot Device.
At this point, the firewall clears the User-ID mappings, then connects to the User-ID sources to repopulate the mappings.If you have enabled User-ID, use the following CLI commands to verify that the firewall has repopulated the IP address-to-username and group mappings before allowing traffic.- show user ip-user-mapping all
- show user group list
Regenerate or re-import all certificates to adhere to OpenSSL Security Level 2.On upgrade to PAN-OS 11.1, it is required that all certificates meet the following minimum requirements:- RSA 2048 bits or greater, or ECDSA 256 bits or greater
- Digest of SHA256 or greater
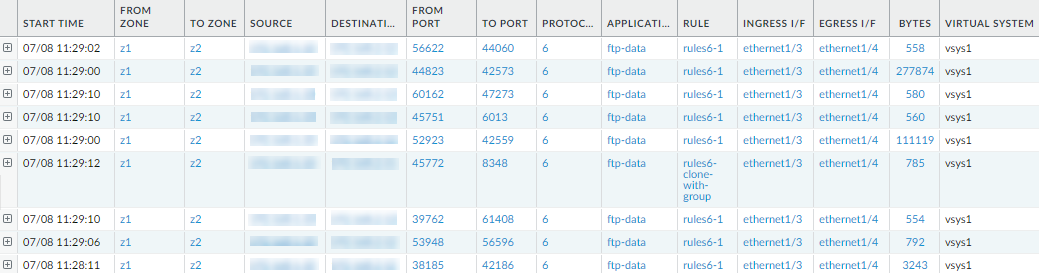
See the PAN-OS Administrator's Guide for more information on regenerating or re-importing your certificates.Verify that the firewall is passing traffic.Select MonitorSession Browser and verify that you are seeing new sessions.![]() View the software upgrade history on the firewall.
View the software upgrade history on the firewall.- Log in to the firewall interface.Go to DeviceSummarySoftware and click Device History.