Prisma Access
Onboarding Workflow for Prisma Access ZTNA Connector
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Onboarding Workflow for Prisma Access ZTNA Connector
Learn how to set up a Prisma Access ZTNA Connector for the first time.
Zero Trust Network Access (ZTNA) Connector helps connect Prisma
Access to your organization's private apps quickly and securely. It gives
mobile users and branch users access to private apps using an automated secure
tunnel, so you don't have to manually configure IPSec tunnels or routing to your
data center, public cloud environments, or partner networks.
When you deploy ZTNA Connector VMs, they automatically connect to the nearest Prisma Access location to ensure optimal latency. Each
Connector supports up to 2 Gbps of bandwidth per Connector.
Prisma Access blocks all traffic by default. As an
administrator, you must create policy rules that explicitly allow access to private
apps using User-ID, App-ID, and Device-ID. This approach reduces your attack surface
and improves security.
After you allow a connection, Prisma Access:
- Continuously verifies the trust of the connection
- Inspects traffic for threats
- Scans for data leakage
ZTNA Connector also hides the private IP addresses of your apps, adding another layer
of protection.
To secure private apps using ZTNA Connector, complete the following task.
Before you begin, configure the Application block and Connector IP
address block and Push Config to save the
configuration.
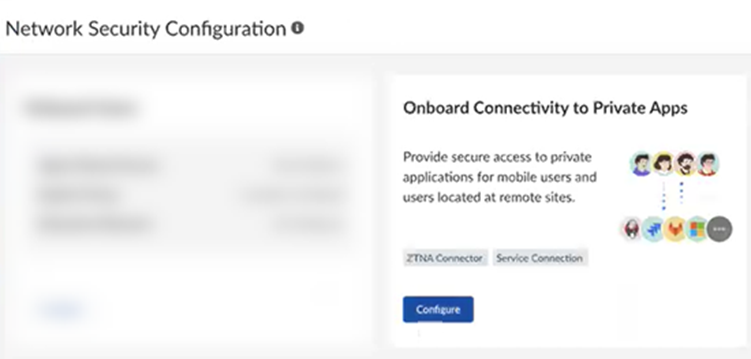
- Go to ConfigurationOnboarding.Configure connectivity to private apps.
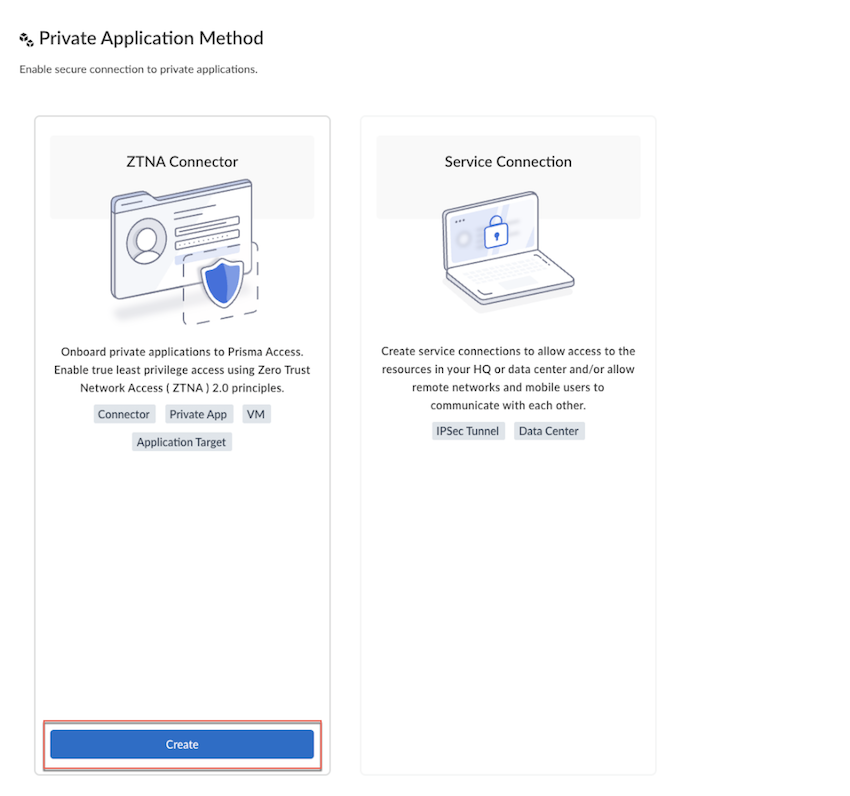
![]() Create a ZTNA Connector.
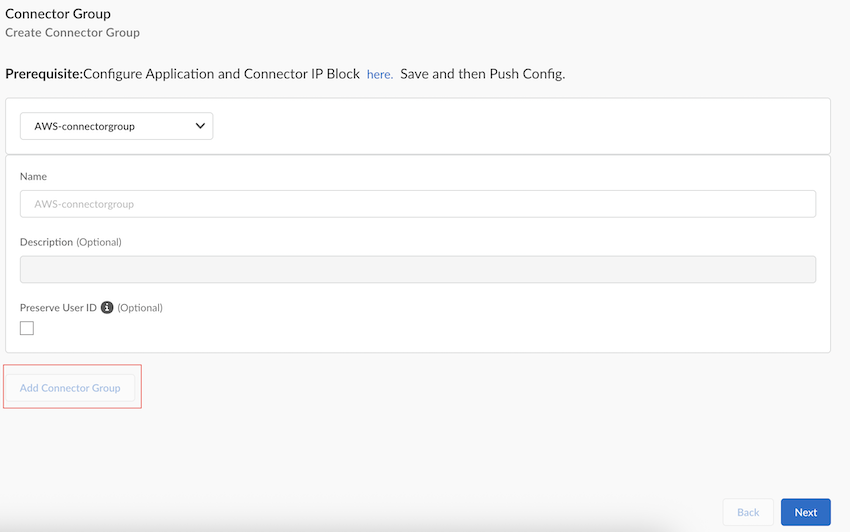
Create a ZTNA Connector.![]() Create a Connector Group.
Create a Connector Group.- Add Connector Group, give the Connector Group a unique Name, and select the Group Type as ZTNA Connector.(Optional) Add a Description and enable Preserve User ID, if required.Create to add the Connector Group, and then select Next.
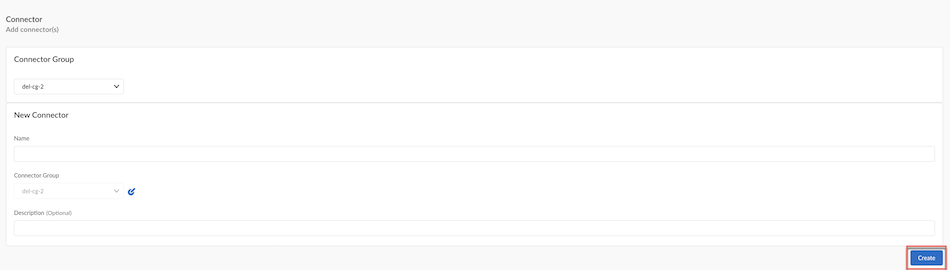
![]() Create a Connector.
Create a Connector.- Give the Connector a unique Name.Select the Connector Group and optionally add a Description for the Connector, and then select Next.
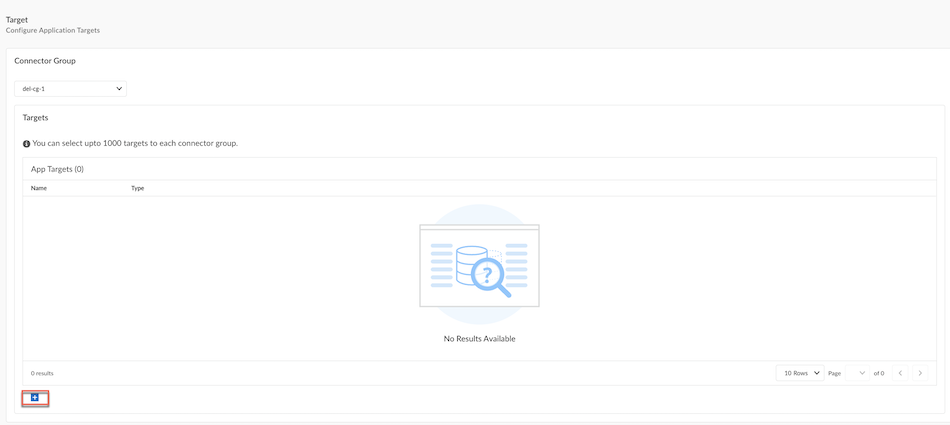
![]() Configure Application Targets.
Configure Application Targets.- Select the add icon to add a FQDN Target or a Wildcard Target.
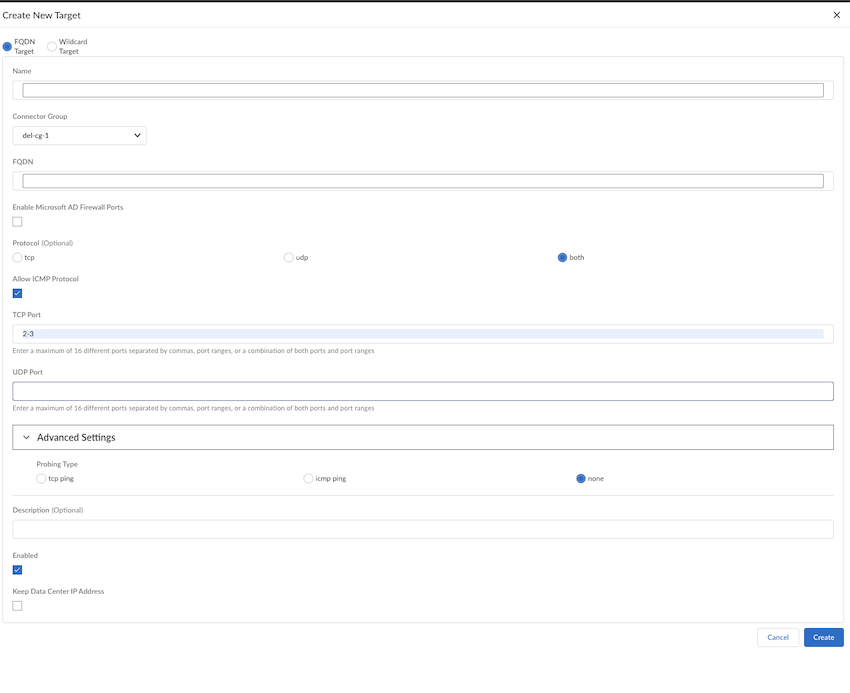
![]() Configure an FQDN Target:
Configure an FQDN Target:- Add a unique Name for the target and assign a Connector Group to associate with the target. The Group must be a type of FQDN/Wildcard.
- Add the FQDN to use with the target.
- Enable Microsoft AD Firewall Ports, if you want to enable all TCP and UDP ports required for Microsoft Active Directory Domain Services.
- Select the Protocol (tcp, udp or both).
- (Optional) To enable ICMP protocol from a GlobalProtect user to a ZTNA Connector data center Allow ICMP Protocol.
- Select the Port to use for the app.Enter ports in one or more of these formats:
- A single port
- Multiple ports using commas between the ports
- A range of ports using dashes
- A range of ports using commas and dashes
If you have selected both under Protocol, add ports to TCP Port and UDP Port.When you enter a range in the TCP Port field, under Advanced Settings, icmp ping and Probing Type of none are activated. - Enter a Probing Type of tcp
ping, icmp ping, or
none, depending on the protocol you
select.If you select tcp ping, select a Probing Port, and enter a single port. The port does not have to be in the range of ports you entered in the Port and Protocol area. ZTNA Connector determines the reachability of the app by performing a TCP ping from the probing port to the FQDN's resolved IP address. If the ping is successful, the app is considered Up.You can also edit the probing port, which you have added during application onboarding. When the probe port is updated, ZTNA Connector starts a TCP probing application on the updated port and the application status is updated accordingly.If you select icmp ping, ZTNA Connector performs an ICMP ping to the FQDN's resolved IP address. When a response is received to the ICMP ping, the app is considered Up. If you select none, no probing is performed and the application is always marked as Up.
- Select Enabled to create the target.
- (Optional) Enable Keep Data Center IP
Address.Normally, FQDN targets are allocated an IP address from the ZTNA Connector IP Blocks and DNS Proxies. However, Microsoft Active Directory DS applications won't function properly with DNS Proxy NAT. FQDN targets with Keep Data Center IP Address keep the data center IP address resolved at the ZTNA Connector DNS Server. DNS Resolution must be consistent with no overlapping IP addresses.
- Create to add the required FQDN target.
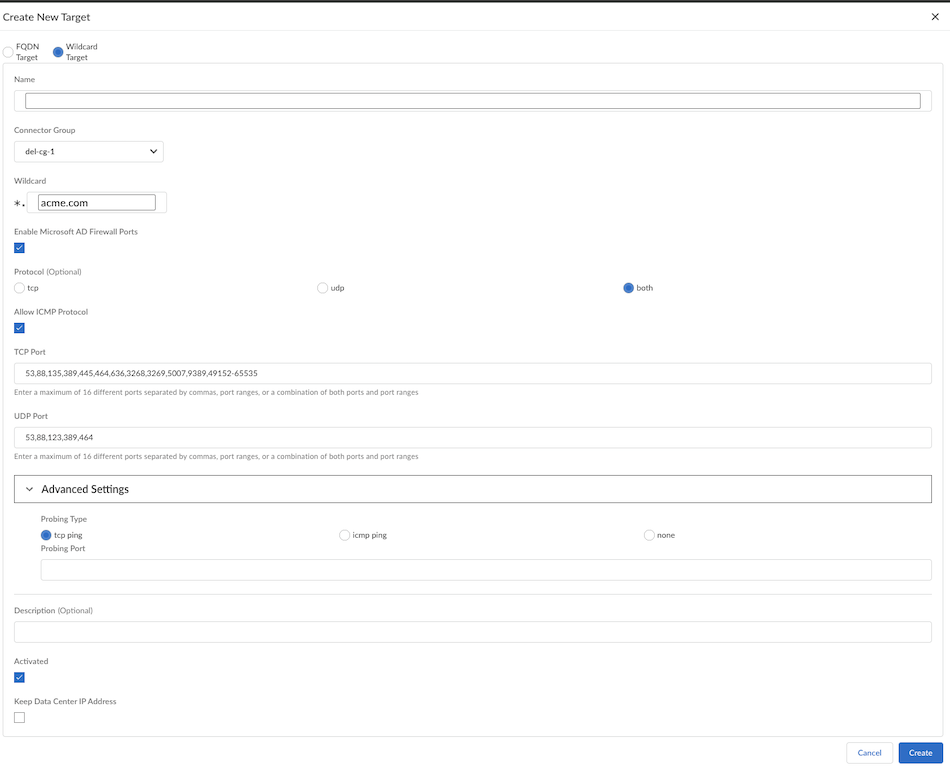
![]() Configure a Wildcard Target:
Configure a Wildcard Target:- Add a unique Name for the target and assign a Connector Group to associate with the target. The Group must be a type of FQDN/Wildcard.
- Add the Wildcard to use with the
target.Enter it in the format of .example.com or .my.example.com (the UI implicitly adds the asterisk to the front of the wildcard). Don't allow all sites by specifying a wildcard of *.*, example.*.com, or *.com.
- Enable Microsoft AD Firewall Ports, if you want to enable all TCP and UDP ports required for Microsoft Active Directory Domain Services.
- Select the Protocol (tcp, udp or both).
- (Optional) To enable ICMP protocol from a GlobalProtect user to a ZTNA Connector data center Allow ICMP Protocol.
- Select the Port to use for the app.Enter ports in one or more of these formats:
- A single port
- Multiple ports using commas between the ports
- A range of ports using dashes
- A range of ports using commas and dashes
If you have selected both under Protocol, you have to add ports to TCP Port and UDP Port.When you enter a range in the TCP Port field, under Advanced Settings, icmp ping and Probing Type of none are activated. - Enter a Probing Type of tcp
ping, icmp ping, or
none, depending on the protocol you
select.If you select tcp ping, select a Probing Port, and enter a single port. The port does not have to be in the range of ports you entered in the Port and Protocol area. ZTNA Connector determines the reachability of the app by performing a TCP ping from the probing port to the FQDN's resolved IP address. If the ping is successful, the app is considered Up.You can also edit the probing port, which you have added during application onboarding. When the probe port is updated, ZTNA Connector starts a TCP probing application on the updated port and the application status is updated accordingly.If you select icmp ping, ZTNA Connector performs an ICMP ping to the FQDN's resolved IP address. When a response is received to the ICMP ping, the app is considered Up. If you select none, no probing is performed and the application is always marked as Up.
- Select Activated to create the target.
- (Optional) Enable Keep Data Center IP
Address.Normally, FQDN targets are allocated an IP address from the ZTNA Connector IP Blocks and DNS Proxies. However, Microsoft Active Directory DS applications won't function properly with DNS Proxy NAT. FQDN targets with Keep Data Center IP Address keep the data center IP address resolved at the ZTNA Connector DNS Server. DNS Resolution must be consistent with no overlapping IP addresses.
- Create to add the required Wildcard target and select Next.
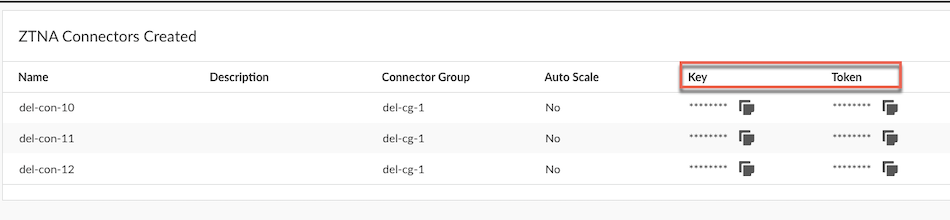
![]() Retrieve the key and token to set up and activate and authenticate the connectors. For advanced monitoring and troubleshooting, navigate to ConfigurationZTNA ConnectorConnectors.
Retrieve the key and token to set up and activate and authenticate the connectors. For advanced monitoring and troubleshooting, navigate to ConfigurationZTNA ConnectorConnectors.![]() Complete the setup by deploying your ZTNA Connector VMs in your data center.Navigate to ConfigurationNGFW and Prisma Access to create a Security policy under the Prisma Access configuration scope to control user access to the applications that ZTNA Connector discovers.Create security policy rules to allow users access to the apps in the connectors.Finish to complete the onboarding process.Push Config to push your configuration changes.(Optional) View Monitor: Data Centers ZTNA Connectors to see how your ZTNA connectors and connector groups are performing.(Optional) If you encounter issues with accessing private apps using ZTNA Connector, use the ping, traceroute, and nslookup diagnostic tools to check app reachability.
Complete the setup by deploying your ZTNA Connector VMs in your data center.Navigate to ConfigurationNGFW and Prisma Access to create a Security policy under the Prisma Access configuration scope to control user access to the applications that ZTNA Connector discovers.Create security policy rules to allow users access to the apps in the connectors.Finish to complete the onboarding process.Push Config to push your configuration changes.(Optional) View Monitor: Data Centers ZTNA Connectors to see how your ZTNA connectors and connector groups are performing.(Optional) If you encounter issues with accessing private apps using ZTNA Connector, use the ping, traceroute, and nslookup diagnostic tools to check app reachability.