5G Equipment ID and Subscriber ID Security
Table of Contents
11.1 & Later
Expand all | Collapse all
-
- Intelligent Security and the UEIP Database
- Intelligent Security with PFCP for User Equipment to IP Address Correlation
- Configure Intelligent Security using PFCP for User Equipment to IP Address Correlation
- Configure Intelligent Security Using RADIUS for User Equipment to IP Address Correlation
- Configure Intelligent Security Using GTP for User Equipment to IP Address Correlation
5G Equipment ID and Subscriber ID Security
Information about 5G equipment ID and subscriber ID security.
5G is the next-generation mobile technology. New use cases, services, and applications in 5G are
in the areas of enhanced Mobile Broadband (eMBB), Ultra-Reliable and Low Latency
Communications (URLLC), and massive IoT (MIoT). High-value assets and critical processes
run on 5G networks. Early adopters of 5G technology are enterprises focused on smart
manufacturing, transport and logistics, critical infrastructure, oil, gas, and mining.
5G will accelerate the evolution of IoT as more devices become connected.
The attack surface increases in 5G. One major concern is a greater
number of devices connected to 5G networks, which increases the
number of opportunities for attackers to exploit the vulnerability
of a device. For example, the increased number of devices connected
to 5G networks makes it easier to launch a DDoS attack. Most of
these devices likely lack robust security and software update mechanisms. Compromised
devices can also impact service of the 5G network.
Security is one of the top concerns of organizations planning
to adopt 5G. Network security capabilities are required, with the
ability to identify and prevent the attack with the granularity
of device or equipment identifier and subscriber or user identifier.
Detection of these threats in 5G mobile networks requires identification of compromised
equipment, devices, subscribers, and users. Prevention requires the ability to apply
network security based on equipment ID, which is a Permanent Equipment Identifier (PEI).
This includes International Mobile Equipment Identity (IMEI), and subscriber ID, which
is Subscriber Permanent Identifier (SUPI), including International Mobile Subscriber
Identity (IMSI).
To extract IMSI and IMEI information, position the firewall on one of the following
interfaces:
- N4 interface between SMF and UPF along with the User Plane (N3) interface
- N11 interface between AMF and SMF along with the User Plane (N3) interface
The N4 interface is typically available from service providers who split the Control
Plane and User Plane functions or in private 5G deployments where the UPF is located
on-premises.
In the following private 5G network deployment scenario, only the User Plane Function (UPF) is
located on-premises. The 5G Core is located remotely in a central core site or public
cloud. To enforce Security policy for user and control traffic, the firewall must be
positioned on the 5G interfaces, including the User Plane (N3) and Control Plane (N4).
The second firewall in
the diagram is positioned on the perimeter (the N6 interface connected to the internet
and the enterprise IT data center).
For complete subscriber-level and equipment-level visibility
and Security policy control for network traffic threats, enable GTP Security.
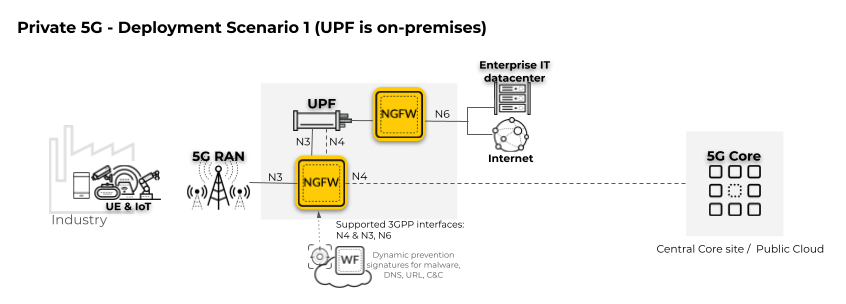
In the following private 5G network deployment scenario, the 5G Core, including the User Plane
Function (UPF), is located on-premises. The 5G Core includes network functions (NFs)
such as Session Management (SMF) and Access and Mobility Management Function (AMF), as
well as others. To enforce Security policy for user and control traffic, the firewall
must be positioned on the 5G interfaces, including the User Plane (N3) and the Control
Plane (N4).
The second firewall
in the diagram is positioned on the perimeter (the N6 interface connected to the
internet and the enterprise IT data center).
For complete subscriber-level and equipment-level
visibility and Security policy control for network traffic threats, enable GTP Security. Apply Security policy to the
Control Plane (N2) between the 5G RAN and the 5G Core for signaling protection by
enabling SCTP Security.

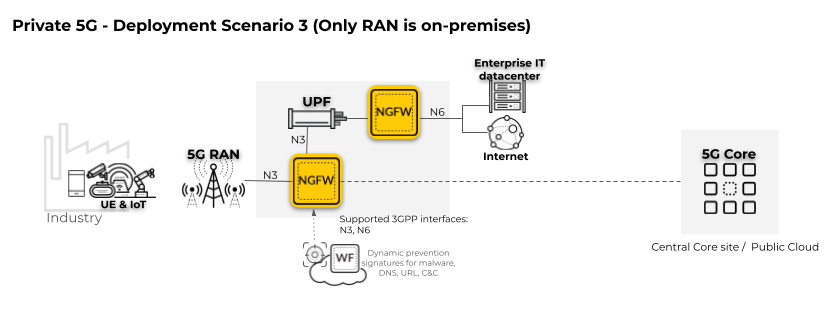
In the following private 5G network deployment scenario, only the radio access network (RAN) is
located on-premises.
The
firewall must be positioned on the 5G interface for the User Plane (N3).
To apply the Security policy to user traffic,
enable Tunnel Content Inspection.
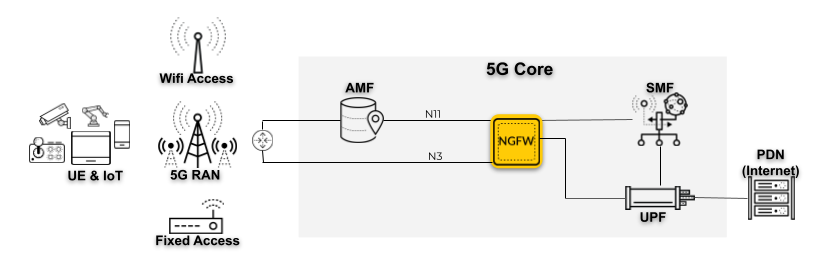
5G network functions communicate with each other using the HTTP/2 protocol; HTTP/2
messages carry various mobile network identifiers, such as PEI. Traffic from IoT devices
is carried in GTP-U tunnels in the 5G network. The firewall is positioned in N3 and N11
interfaces to inspect both HTTP/2 and GTP-U traffic, and it correlates the mobile
network identifier information with the IP traffic inside the GTP-U tunnels in a 5G
network.
PAN-OS supports the following HTTP/2 control messages on an N11 interface. From these messages,
the firewall extracts the identifiers (such as Equipment ID, Subscriber ID, and Network
Slice SST) to correlate traffic to a specific user at the N3 interface and to match the
identifiers to Security policy rules.
- Nsmf_PDUSession_CreateSMContext Request
- Nsmf_PDUSession_CreateSMContext Response
- Nsmf_PDUSession_UpdateSMContext Request
- Nsmf_PDUSession_UpdateSMContext Response
- Nsmf_PDUSession_ReleaseSMContext Request
- Nsmf_PDUSession_ReleaseSMContext Response
- Namf_Communication_N1N2MessageTransfer Request
- Namf_Communication_N1N2MessageTransfer Response
You can apply network security based on the equipment identity of any device or equipment or the
subscriber identity of any subscriber or user who is trying to access your 5G
network.
You can investigate a security event related to a piece of equipment in a 5G network when you
have the PEI including IMEI, or a security event related to a subscriber when you have
the SUPI including IMSI. You can look at the traffic, threat, URL filtering, and
WildFire® logs and reports.
You can apply the following per equipment ID or subscriber ID: application control, Antivirus,
antispyware, URL filtering, intrusion prevention, and Advanced Threat Prevention with
WildFire based on an IMEI, IMSI, or a group of IMEIs or IMSIs.
For more information, refer to the External Dynamic List documentation.
5G equipment ID and subscriber ID security support an additional
Radio Access Technology (RAT) not supported in 4G, and that is New
Radio (NR).
When deciding which firewall model to purchase, consider the total number of 3G, 4G, and 5G
network identifiers (Subscriber IDs and Equipment IDs) you need to include as external
dynamic list entries or static entries.
For platform support
and capacity information, see the Compatibility Matrix.
*You can use Software NGFW credits to fund a license for
your VM-Series firewall based on the maximum memory limits (tiers) that you require
in your network.
