Download PDF
Onboarding External Load Balancer
Table of Contents
11.1 & Later
Expand all | Collapse all
-
- VM-Series Deployments
- VM-Series in High Availability
- IPv6 Support on Public Cloud
- Enable Jumbo Frames on the VM-Series Firewall
- Hypervisor Assigned MAC Addresses
- Custom PAN-OS Metrics Published for Monitoring
- Interface Used for Accessing External Services on the VM-Series Firewall
- PacketMMAP and DPDK Driver Support
- Enable NUMA Performance Optimization on the VM-Series
- Enable ZRAM on the VM-Series Firewall
- Additional XFF IP Logging
-
- Licensing and Prerequisites for Virtual Systems Support on VM-Series
- System Requirements for Virtual Systems Support on VM-Series
- Enable Multiple Virtual Systems Support on VM-Series Firewall
- Enable Multiple Virtual Systems Support on VM-Series in Panorama Console
- Enable Multiple Virtual Systems Support Using Bootstrap Method
-
- VM-Series Firewall Licensing
- Create a Support Account
- Serial Number and CPU ID Format for the VM-Series Firewall
- Use Panorama-Based Software Firewall License Management
-
- Activate Credits
- Create a Deployment Profile
- Activate the Deployment Profile
- Manage a Deployment Profile
- Register the VM-Series Firewall (Software NGFW Credits)
- Provision Panorama
- Migrate Panorama to a Software NGFW License
- Transfer Credits
- Renew Your Software NGFW Credits
- Deactivate License (Software NGFW Credits)
- Delicense Ungracefully Terminated Firewalls
- Set the Number of Licensed vCPUs
- Customize Dataplane Cores
- Migrate a Firewall to a Flexible VM-Series License
-
- Generate Your OAuth Client Credentials
- Manage Deployment Profiles Using the Licensing API
- Create a Deployment Profile Using the Licensing API
- Update a Deployment Profile Using the Licensing API
- Get Serial Numbers Associated with an Authcode Using the API
- Deactivate a VM-Series Firewall Using the API
- What Happens When Licenses Expire?
-
- Supported Deployments on VMware vSphere Hypervisor (ESXi)
-
- Plan the Interfaces for the VM-Series for ESXi
- Provision the VM-Series Firewall on an ESXi Server
- Perform Initial Configuration on the VM-Series on ESXi
- Add Additional Disk Space to the VM-Series Firewall
- Use VMware Tools on the VM-Series Firewall on ESXi and vCloud Air
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Use the VM-Series CLI to Swap the Management Interface on ESXi
- Configure Link Aggregation Control Protocol
- ESXi Simplified Onboarding
-
-
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (North-South)
- Components of the VM-Series Firewall on NSX-T (North-South)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Deploy the VM-Series Firewall
- Direct Traffic to the VM-Series Firewall
- Apply Security Policy to the VM-Series Firewall on NSX-T
- Use vMotion to Move the VM-Series Firewall Between Hosts
- Extend Security Policy from NSX-V to NSX-T
-
- Components of the VM-Series Firewall on NSX-T (East-West)
- VM-Series Firewall on NSX-T (East-West) Integration
- Supported Deployments of the VM-Series Firewall on VMware NSX-T (East-West)
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Add a Service Chain
- Direct Traffic to the VM-Series Firewall
- Apply Security Policies to the VM-Series Firewall on NSX-T (East-West)
- Use vMotion to Move the VM-Series Firewall Between Hosts
-
- Install the Panorama Plugin for VMware NSX
- Enable Communication Between NSX-T Manager and Panorama
- Create Template Stacks and Device Groups on Panorama
- Configure the Service Definition on Panorama
- Launch the VM-Series Firewall on NSX-T (East-West)
- Create Dynamic Address Groups
- Create Dynamic Address Group Membership Criteria
- Generate Steering Policy
- Generate Steering Rules
- Delete a Service Definition from Panorama
- Migrate from VM-Series on NSX-T Operation to Security Centric Deployment
- Extend Security Policy from NSX-V to NSX-T
- Use In-Place Migration to Move Your VM-Series from NSX-V to NSX-T
-
-
- Deployments Supported on AWS
-
- Planning Worksheet for the VM-Series in the AWS VPC
- Launch the VM-Series Firewall on AWS
- Launch the VM-Series Firewall on AWS Outpost
- Create a Custom Amazon Machine Image (AMI)
- Encrypt EBS Volume for the VM-Series Firewall on AWS
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable CloudWatch Monitoring on the VM-Series Firewall
- Publish ENA Network Performance Metrics to AWS CloudWatch
- VM-Series Firewall Startup and Health Logs on AWS
- Simplified Onboarding of VM-Series Firewall on AWS
- Use AWS Secrets Manager to Store VM-Series Certificates
- AWS Shared VPC Monitoring
- Use Case: Secure the EC2 Instances in the AWS Cloud
- Use Case: Use Dynamic Address Groups to Secure New EC2 Instances within the VPC
-
- Intelligent Traffic Offload
- Software Cut-through Based Offload
-
- Deployments Supported on Azure
- Deploy the VM-Series Firewall from the Azure Marketplace (Solution Template)
- Simplified Onboarding of VM-Series Firewall on Azure
- Deploy the VM-Series Firewall from the Azure China Marketplace (Solution Template)
- Deploy the VM-Series with the Azure Gateway Load Balancer
- Create a Custom VM-Series Image for Azure
- Deploy the VM-Series Firewall on Azure Stack
- Deploy the VM-Series Firewall on Azure Stack HCI
- Enable Azure Application Insights on the VM-Series Firewall
- Azure Health Monitoring
- Set up Active/Passive HA on Azure
- Use Azure Key Vault to Store VM-Series Certificates
- Use the ARM Template to Deploy the VM-Series Firewall
-
- About the VM-Series Firewall on Google Cloud Platform
- Supported Deployments on Google Cloud Platform
- Create a Custom VM-Series Firewall Image for Google Cloud Platform
- Prepare to Set Up VM-Series Firewalls on Google Public Cloud
-
- Deploy the VM-Series Firewall from Google Cloud Platform Marketplace
- Management Interface Swap for Google Cloud Platform Load Balancing
- Use the VM-Series Firewall CLI to Swap the Management Interface
- Enable Google Stackdriver Monitoring on the VM Series Firewall
- Enable VM Monitoring to Track VM Changes on Google Cloud Platform (GCP)
- Use Dynamic Address Groups to Secure Instances Within the VPC
- Use Custom Templates or the gcloud CLI to Deploy the VM-Series Firewall
- Enable Session Resiliency on VM-Series for GCP
- Google Cloud Network Security Integration (NSI) with VM-Series Firewalls
- Secure Boot Support for VM-Series on GCP
-
- Prepare Your ACI Environment for Integration
-
-
- Create a Virtual Router and Security Zone
- Configure the Network Interfaces
- Configure a Static Default Route
- Create Address Objects for the EPGs
- Create Security Policy Rules
- Create a VLAN Pool and Domain
- Configure an Interface Policy for LLDP and LACP for East-West Traffic
- Establish the Connection Between the Firewall and ACI Fabric
- Create a VRF and Bridge Domain
- Create an L4-L7 Device
- Create a Policy-Based Redirect
- Create and Apply a Service Graph Template
-
- Create a VLAN Pool and External Routed Domain
- Configure an Interface Policy for LLDP and LACP for North-South Traffic
- Create an External Routed Network
- Configure Subnets to Advertise to the External Firewall
- Create an Outbound Contract
- Create an Inbound Web Contract
- Apply Outbound and Inbound Contracts to the EPGs
- Create a Virtual Router and Security Zone for North-South Traffic
- Configure the Network Interfaces
- Configure Route Redistribution and OSPF
- Configure NAT for External Connections
-
-
- Choose a Bootstrap Method
- VM-Series Firewall Bootstrap Workflow
- Bootstrap Package
- Bootstrap Configuration Files
- Bootstrapping VM-Series in Virtual Metadata Collector Mode
- Generate the VM Auth Key on Panorama
- Create the bootstrap.xml File
- Prepare the Licenses for Bootstrapping
- Prepare the Bootstrap Package
- Bootstrap the VM-Series Firewall on AWS
- Bootstrap the VM-Series Firewall on Azure
- Bootstrap the VM-Series Firewall on Azure Stack HCI
- Bootstrap the VM-Series Firewall on Google Cloud Platform
- Verify Bootstrap Completion
- Bootstrap Errors
Onboarding External Load Balancer
The external TCP load balancer distributes TCP/UDP traffic from the internet to
the VM-Series firewall. Internal applications can be onboarded by creating a forwarding
rule for each application. Here, we will onboard two applications by allocating frontend
IPs to an external TCP load balancer.

Before you begin, you need the following:
- The IPs of the backend applications (i.e. app1: 10.1.0.10, app2: 10.2.0.10).
- If you do not have an environment, use this Terraform plan to build a test bed environment.
Following are the steps to onboard external TCP load balancer:
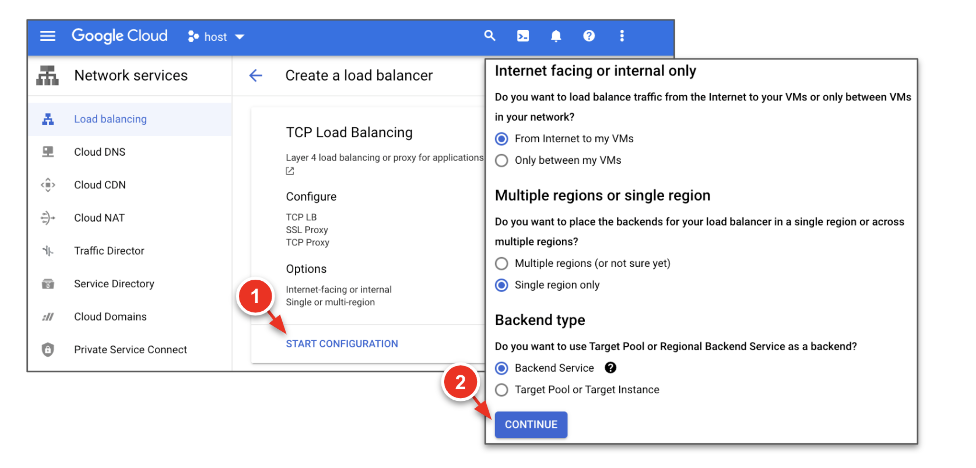
- Login to your GCP console and create the External TCP/UDP Load Balancer.
![]()
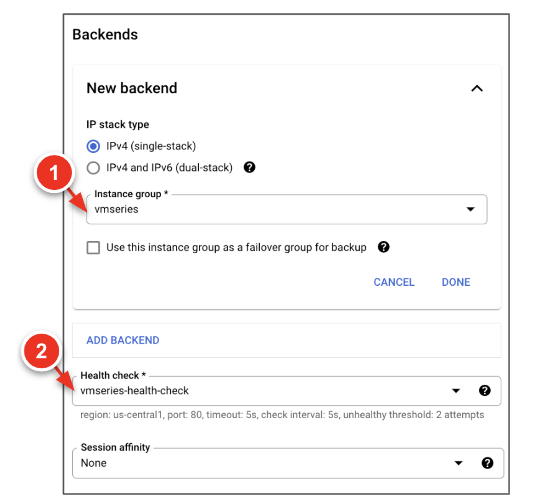
- Configure the backend service.
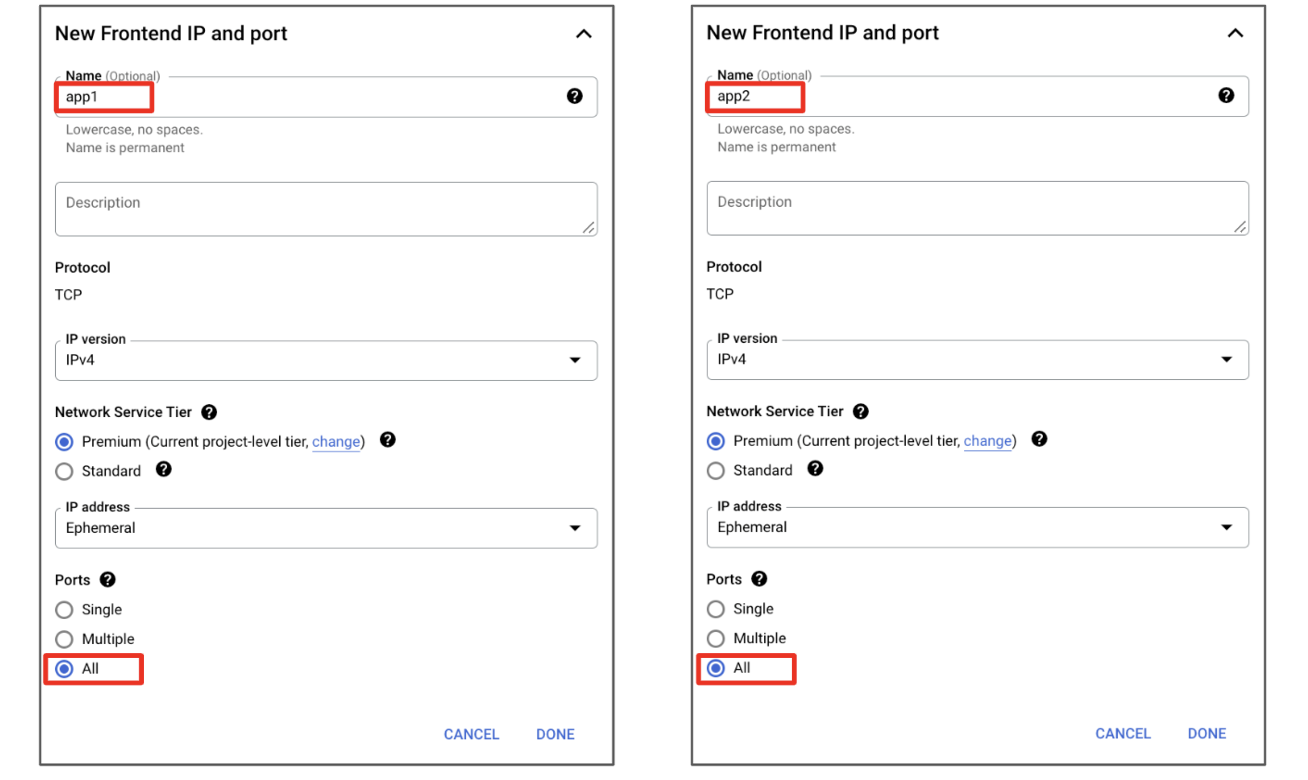
![]() Here is an example:gcloud compute health-checks create tcp vmseries-hc \ --request=/php/login.php \ --port=80 \ --region=us-central1 gcloud compute backend-services create vmseries-external-lb \ --load-balancing-scheme=EXTERNAL \ --protocol=TCP \ --health-checks=vmseries-hc \ --health-checks-region=us-central1 \ --region=us-central1 gcloud compute backend-services add-backend vmseries-external-lb \ --instance-group=vmseries-us-central1-a \ --instance-group-zone=us-central1-a \ --region=us-centrallCreate a forwarding rule for each application.
Here is an example:gcloud compute health-checks create tcp vmseries-hc \ --request=/php/login.php \ --port=80 \ --region=us-central1 gcloud compute backend-services create vmseries-external-lb \ --load-balancing-scheme=EXTERNAL \ --protocol=TCP \ --health-checks=vmseries-hc \ --health-checks-region=us-central1 \ --region=us-central1 gcloud compute backend-services add-backend vmseries-external-lb \ --instance-group=vmseries-us-central1-a \ --instance-group-zone=us-central1-a \ --region=us-centrallCreate a forwarding rule for each application.![]() gcloud compute forwarding-rules create app1 \ --load-balancing-scheme=EXTERNAL \ --region=us-central1 \ --ports=ALL \ --backend-service=vmseries-external-lb gcloud compute forwarding-rules create app2 \ --load-balancing-scheme=EXTERNAL \ --region=us-central1 \ --ports=ALL \ --backend-service=vmseries-external-lbClick Create.On your VM-Series firewall web interface, create two NAT policies to IP map the load balancer forwarding rule address to the correct internal application.
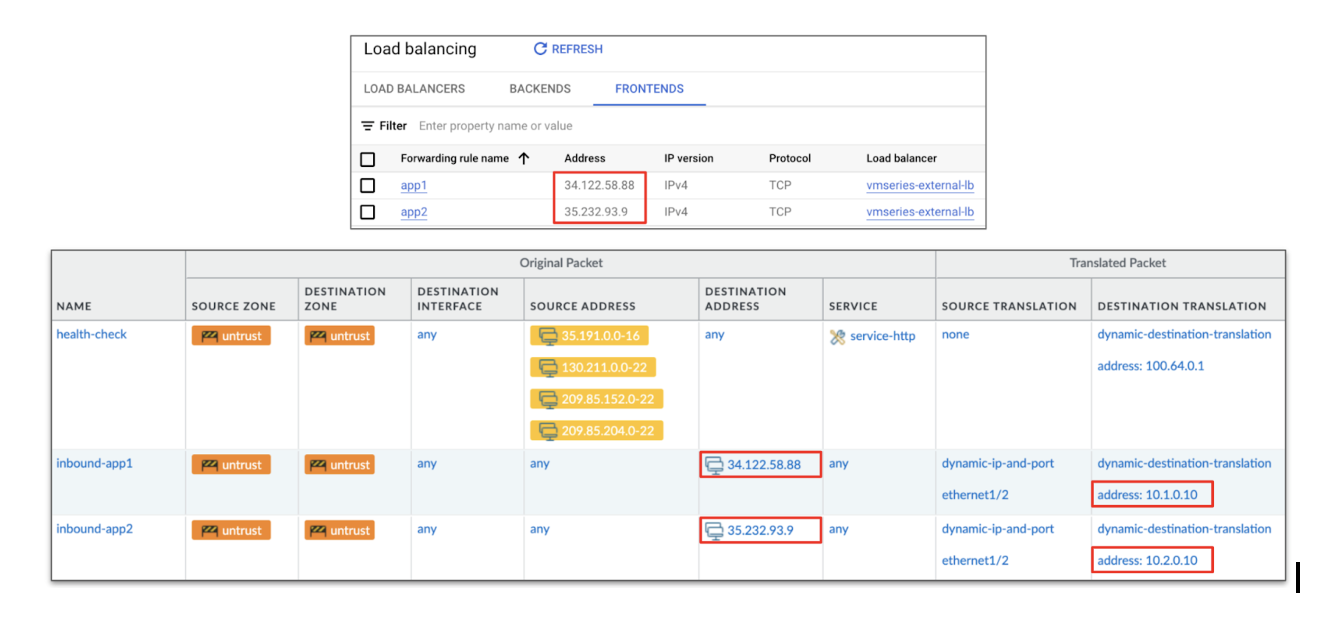
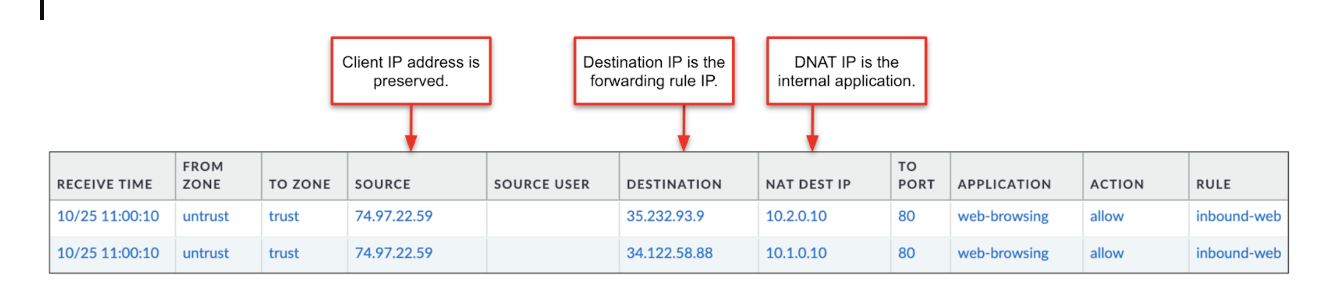
gcloud compute forwarding-rules create app1 \ --load-balancing-scheme=EXTERNAL \ --region=us-central1 \ --ports=ALL \ --backend-service=vmseries-external-lb gcloud compute forwarding-rules create app2 \ --load-balancing-scheme=EXTERNAL \ --region=us-central1 \ --ports=ALL \ --backend-service=vmseries-external-lbClick Create.On your VM-Series firewall web interface, create two NAT policies to IP map the load balancer forwarding rule address to the correct internal application.![]() You can see the following details in your traffic logs:
You can see the following details in your traffic logs:![]() Automation Example:Below is a Terraform code sample that automates the manual steps above.A forwarding rule is created on an existing external TCP load balancer. The forwarding rule address is used within the VM-Series NAT policy to map to a backend application.# Create GCP LB forwarding rule resource "google_compute_forwarding_rule" "default" { name = "my-forwarding-rule" target = var.target region = "us-central1" load_balancing_scheme = "EXTERNAL" all_ports = true } # Create VM-Series NAT policy resource "panos_nat_rule_group" "main" { provider = panos position_keyword = "bottom" rule { name = "my-nat-policy" original_packet { source_zones = ["untrust"] destination_zone = "untrust" destination_interface = "ethernet1/1" service = "any" source_addresses = ["any"] destination_addresses = ["${google_compute_forwarding_rule.default.ip_address}"] } translated_packet { source { dynamic_ip_and_port { interface_address { interface = "ethernet1/2" } } } destination { dynamic_translation { address = "<ip-address>" } } } }
Automation Example:Below is a Terraform code sample that automates the manual steps above.A forwarding rule is created on an existing external TCP load balancer. The forwarding rule address is used within the VM-Series NAT policy to map to a backend application.# Create GCP LB forwarding rule resource "google_compute_forwarding_rule" "default" { name = "my-forwarding-rule" target = var.target region = "us-central1" load_balancing_scheme = "EXTERNAL" all_ports = true } # Create VM-Series NAT policy resource "panos_nat_rule_group" "main" { provider = panos position_keyword = "bottom" rule { name = "my-nat-policy" original_packet { source_zones = ["untrust"] destination_zone = "untrust" destination_interface = "ethernet1/1" service = "any" source_addresses = ["any"] destination_addresses = ["${google_compute_forwarding_rule.default.ip_address}"] } translated_packet { source { dynamic_ip_and_port { interface_address { interface = "ethernet1/2" } } } destination { dynamic_translation { address = "<ip-address>" } } } }