Analysis Artifacts
Table of Contents
Expand all | Collapse all
Analysis Artifacts
Analysis artifacts make up the WildFire dynamic and
static analysis of a sample. WildFire Dynamic Analysis information
consist of properties, activities, and behaviors that WildFire detects
in the sample when it was executed in an analysis environment. WildFire
Static Analysis information consist of artifacts that WildFire can observe
from the sample without executing it in an analysis environment.
To get an idea of the artifacts that appear
in a WildFire analysis section, start a search with an analysis
artifact and for the operator, select has any value.
View the file analysis details of the search results, expanding
the section you searched for to view the artifacts that WildFire
found for it.
Artifact Type | Search with this Artifact Type to Find... |
|---|---|
Connection
Activity | Processes that accessed other hosts on the
network when the sample was executed in the WildFire analysis environment.
Artifacts listed for each connection activity include the process
that accessed other hosts on the network, the port through which
the process connected, the protocol used for the connection, and
the IP address and country of the host. |
DNS
Activity | DNS activity observed when the sample was
executed in the WildFire analysis environment. Artifacts listed
for each DNS activity include the hostname that was translated (Query
column) the resolved domain name or IP address (Response column),
and the Type of DNS resource record (Type column) used to resolve
the DNS query. |
File
Activity | Files that showed activity as a result of
the sample being executed in the WildFire analysis environment.
Artifacts listed for each file activity include the parent process
that showed activity, the action the parent process performed, and
the file that was altered (created, modified, duplicated, or deleted). |
HTTP
Activity | HTTP requests made when the sample was executed
in the WildFire analysis environment. Artifacts listed for each
HTTP activity include the destination domain of the HTTP request,
the HTTP method that the host used, the URL for the requested resource,
and the string originating the request (User Agent column). The domain (Host column) and URL values together
are the URL for the request. For example, the full URL for the first
artifact is althawry.org/images/xs.jpg?8b96=71468. |
Java API Activity | Java runtime activity seen when the sample
was executed in the WildFire analysis environment. |
Observed
Behavior | Behaviors seen for the sample in the WildFire
analysis environment, such as whether the sample created or modified
files, started a process, spawned new processes, modified the registry,
or installed browser help objects (BHOs). Each behavior is also
assigned a risk level of high, medium, low, or informational. On
the File Analysis tab within the sample details, alternate between operating
system columns to see the list of behaviors observed for each virtual
machine in which the sample was executed. 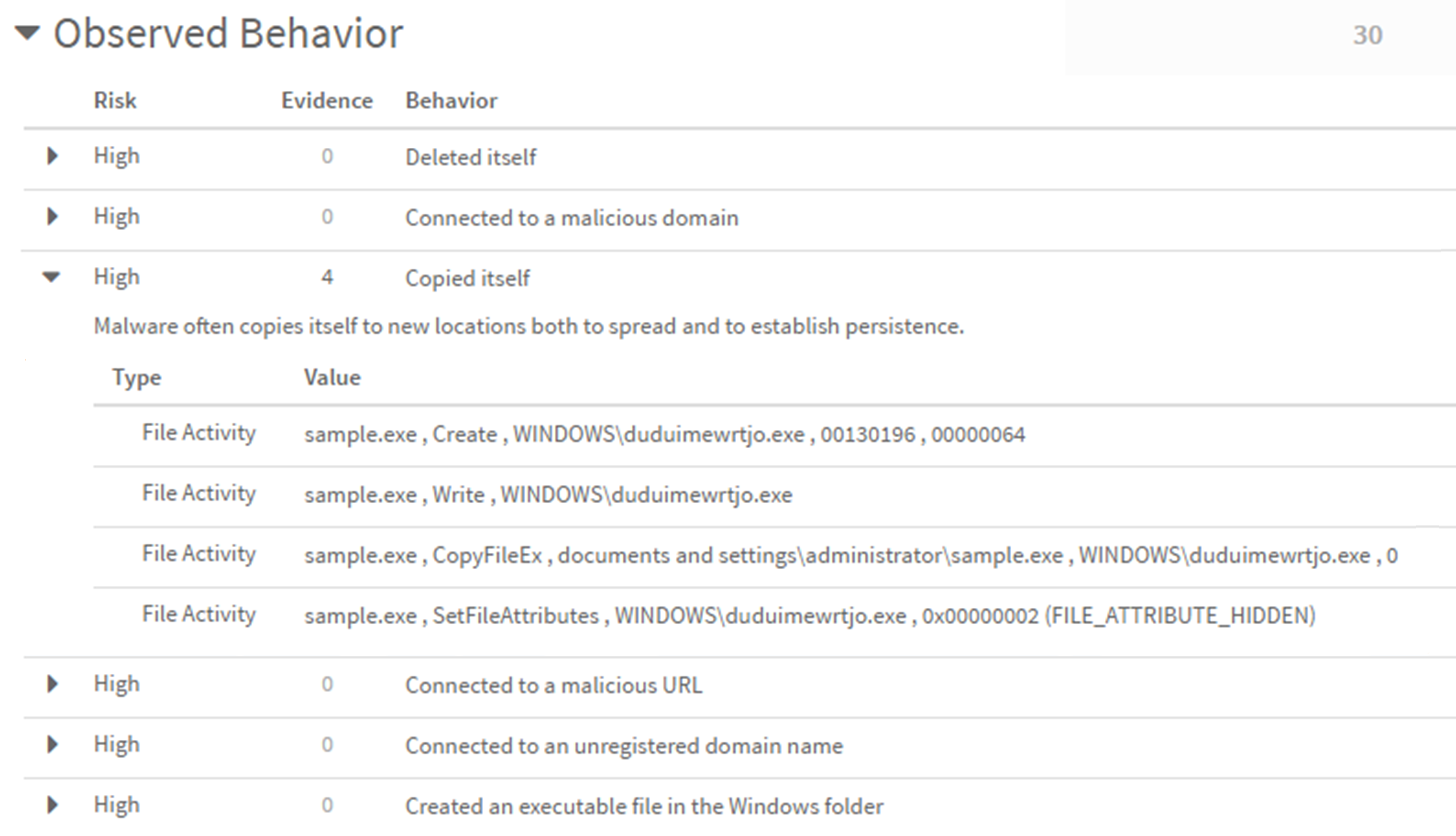
The Evidence
column lists the total number of sample activities that are evidence
of each behavior, and expand a single behavior for the list of matching
activities. For each activity listed, the Type column indicates
the WildFire analysis section and the Value column includes artifacts
that WildFire found for the section. The artifacts displayed might
vary depending on the activity category. In the example above, the
File Activity artifacts provided include the parent process that
showed activity, the action the process performed, and the file
that was altered. The artifact type Observed Behavior also
refers to properties that WildFire observed in a sample during static
analysis. These properties appear under the WildFire Static Analysis
category Suspicious File Properties. |
Other API Activity | Non-Java API activity seen in the WildFire
analysis environment when the sample was executed. Artifacts listed
include the parent process that was active, the API calls made by
the parent process, and the process that was modified. |
PE Metadata | Portable Executable (PE) file metadata details extracted during WildFire analysis. Artifacts listed for each file include the name, virtual address, virtual size, and raw size. |
Process Activity | Processes that showed activity when the
sample was executed. Artifacts listed for each process activity
include the parent process that was active, the action that the
parent process performed, and the process that was modified. |
Service Activity | Services that showed activity as a result
of the sample being executed in the WildFire analysis environment.
Artifacts listed for each service activity include the process that
was active, the action the process performed, and the service that
was created, modified, or deleted. |
User
Agent Fragments | The user agent header for HTTP requests
sent when the sample was executed in the WildFire analysis environment. |
