Advanced DNS Security Powered by Precision AI®
Manage Connection Sources
Table of Contents
Manage Connection Sources
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Connection sources are egress IP addresses in your branch/campus/datacenter that are
subject to the security policies dictated by the Advanced DNS Security Resolver policies. This
includes secure connections that are managed by Prisma Access Agent. Add and
configure connection sources to your Advanced DNS Security Resolver configuration.
Select from the connection source options below:
Manage Connection Sources (Advanced DNS Security Resolver)
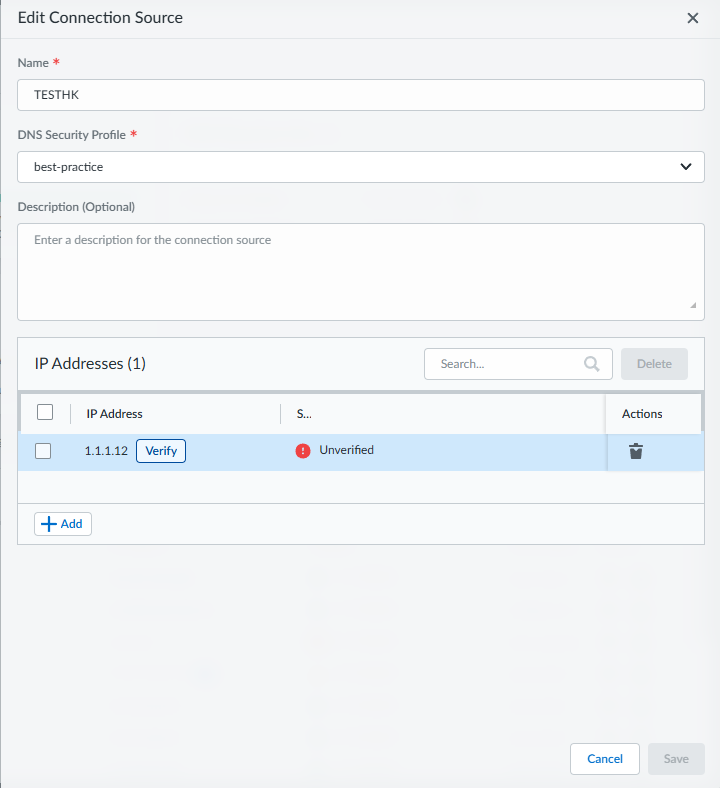
- Log in to the Strata Cloud Manager on the hub.Select ManageConfigurationADNS Resolver and view currently available Connection Sources. This provides an overview of all configured connection sources.Click Create Connection Source and provide a Name and optional Description.Select a DNS Security Profile with the appropriately configured security policies for the connection source.
![]() Add IP addresses or subnets for the connection source. If you do not provide any at this time, a popup will notify you to add IP address(es) to your new connection.
Add IP addresses or subnets for the connection source. If you do not provide any at this time, a popup will notify you to add IP address(es) to your new connection.- From the IP Addresses panel, + Add or delete entries (using the icon) to modify the IP Addresses list entries as necessary. You can only add valid IPv4 IP addresses or a /28 subnet.
- Click Save when finished. An icon appears next to new unverified connection sources.
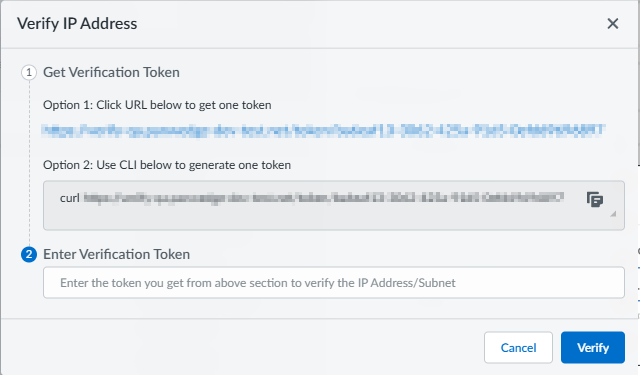
To Verify the IP address, you must download the token using the supplied link (option 1) or generate one by using the curl command (option 2). After you receive the token, you must then Enter Verification Token in the provided field.The client device used for verification (the accessing URL) must be within the specified subnet or IP range for successful IP/Subnet verification.![]() Click Verify to continue.Repeat as necessary for additional IP addresses.If you are verifying a subnet, it is only necessary to verify a single IP address in the subnet IP range; all other IP addresses in that subnet are automatically verified.
Click Verify to continue.Repeat as necessary for additional IP addresses.If you are verifying a subnet, it is only necessary to verify a single IP address in the subnet IP range; all other IP addresses in that subnet are automatically verified.Manage Connection Sources (Prisma Access Agent)
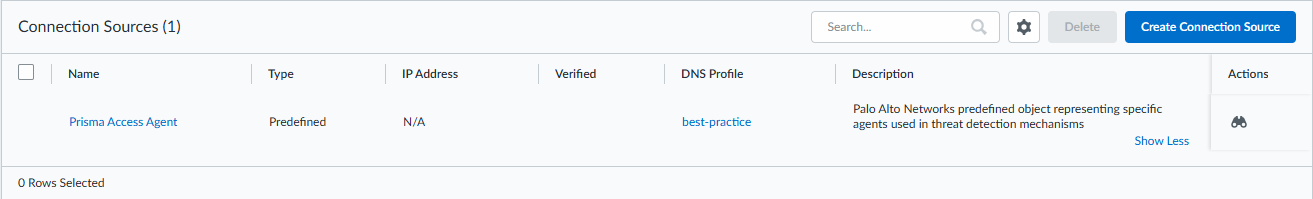
If your Prisma Access deployment provides secure access to your organization's network resources for remote users through Prisma Access Agent, a predefined connection source named Prisma Access Agent is present in the connection sources list. This connection source cannot be modified or removed, with the exception of the redefining the associated DNS Security profile. Additionally, Prisma Access Agent connections do not need to be verified, as identification and authentication are managed internally through Strata Cloud Manager.Prisma Access Agent support for Advanced DNS Security Resolver operates as a fall-back option when the tunnel connection that provides secure access for mobile users fails or is not available. This allows you to retain DNS resolution and query and response inspection from the Advanced DNS Security Resolver service, regardless of your connection status.Unlike connection sources that are managed directly through the Advanced DNS Security Resolver, Prisma Access Agent users and user groups that you want fallback support for are defined within the Prisma Access Agent > Agent Settings > Match Criteria. Keep in mind, this is part of a larger configuration process to Configure.- Log in to the Strata Cloud Manager on the hub.Select ConfigurationADNS Resolver and select Prisma Access Agent.
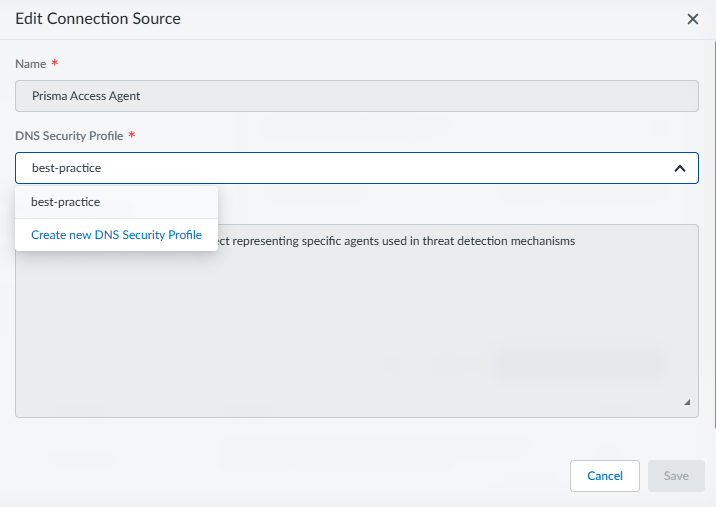
![]() Select a DNS Security Profile with the appropriately configured security policies for the connection source.
Select a DNS Security Profile with the appropriately configured security policies for the connection source.![]() Click Save when finished.Configure the Prisma Access Agent Connectivity Method located in your Forwarding Profile to enable ADNS cloud-based DNS resolution and real-time inspection. For more information, refer to step 2 of: Configure for Prisma Access Agent.The ADNS connection option can only be enabled when Tunnel is enabled first.
Click Save when finished.Configure the Prisma Access Agent Connectivity Method located in your Forwarding Profile to enable ADNS cloud-based DNS resolution and real-time inspection. For more information, refer to step 2 of: Configure for Prisma Access Agent.The ADNS connection option can only be enabled when Tunnel is enabled first.