Advanced DNS Security Powered by Precision AI®
Enable Advanced DNS Security
Table of Contents
Enable Advanced DNS Security
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Advanced DNS Security supplements your existing DNS Security configuration to provide
additional protection against DNS hijacking by inspecting changes to DNS responses. You
should have fully configured DNS Security settings before proceeding with this
step.
To enable Advanced DNS Security, you must create (or modify) an Anti-Spyware security
profile to access the Advanced DNS Security service, configure the log severity and
policy settings for the DNS signature category (or categories), and then attach the
profile to a security policy rule.
You can specify up to a maximum of 100 DNS Zone Misconfigurations entries.
Enable Advanced DNS Security (PAN-OS 11.2 and Later)
Palo Alto Networks recommends enabling your DNS Security functionality prior to
setting up Advanced DNS Security.
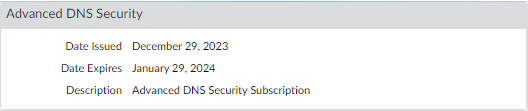
- Log in to the NGFW.Update the content release version to 8832 or later.To prevent access to known and unknown malicious domains using Advanced DNS Security, you must have an active Advanced DNS Security license. This should only be installed after upgrading to PAN-OS 11.2.Advanced DNS Security supports a licensing model that subsumes DNS Security functionality into the Advanced DNS Security license when installed on a previously unlicensed firewall. If you upgrade from a firewall with an existing DNS Security license, entries indicating the presence of separate DNS Security and Advanced DNS Security licenses are displayed. In this instance, the DNS Security license is a passive entry and all DNS Security and Advanced DNS Security functionality is conferred through the Advanced DNS License, including the relevant expiration date. Firewalls without a previously installed DNS Security license show an Advanced DNS Security license, however, it provides both DNS Security and Advanced DNS Security functionality.Consequently, if you downgrade from a PAN-OS release operating an Advanced DNS Security license to a release that does not support Advanced DNS Security, the firewall continues to display and confer DNS Security functionality through the Advanced DNS Security license, however, it is limited to base DNS Security features.To verify subscriptions for which you have currently-active licenses, select DeviceLicenses and verify that the appropriate licenses are available and have not expired.
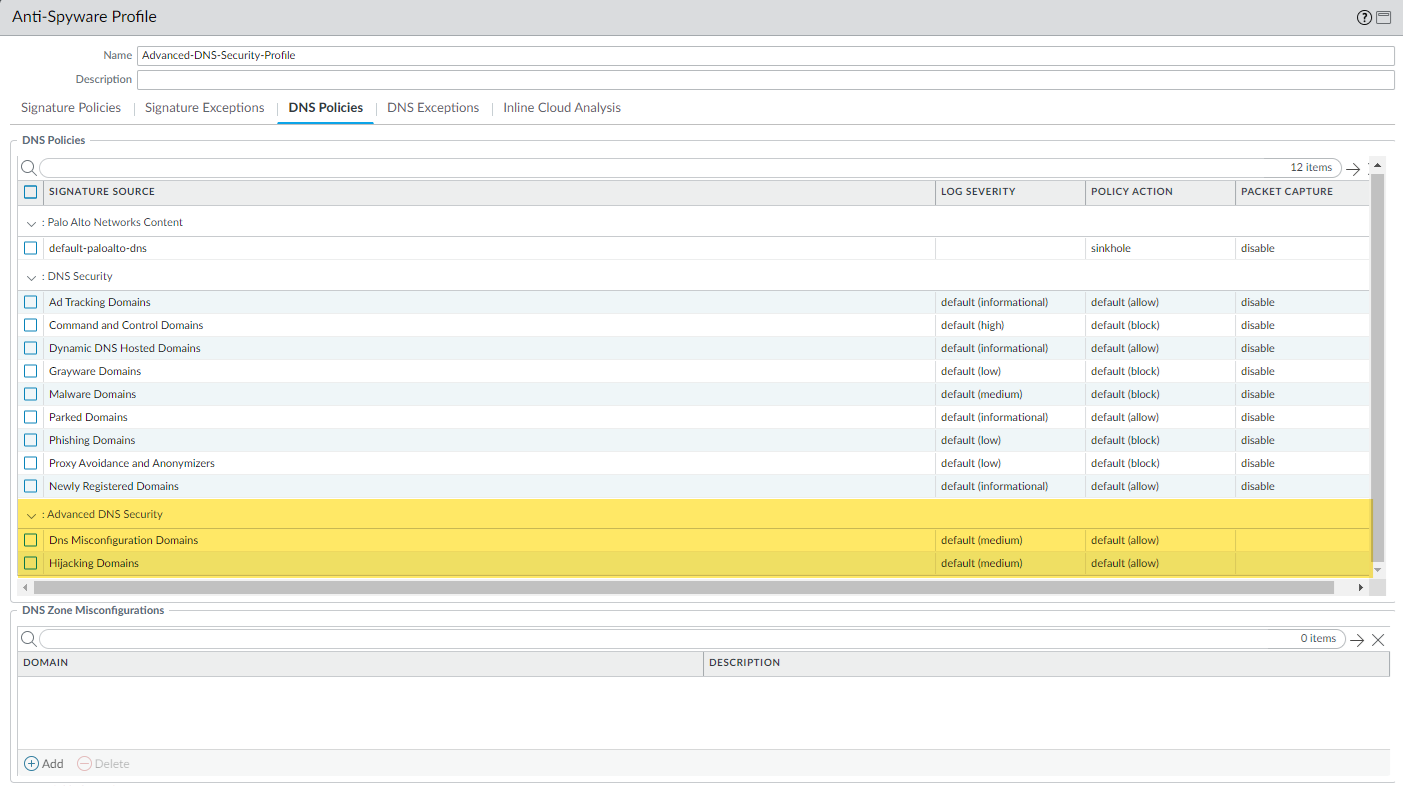
![]() Update or create a new Anti-Spyware Security profile to enable real-time Advanced DNS Security queries. Typically, this is your existing Anti-Spyware security profile used for the DNS Security configuration.
Update or create a new Anti-Spyware Security profile to enable real-time Advanced DNS Security queries. Typically, this is your existing Anti-Spyware security profile used for the DNS Security configuration.![]()
- Select an existing Anti-Spyware security profile or Add a new one (ObjectsSecurity ProfilesAnti-Spyware).
- Select your Anti-Spyware security profile and then go to DNS Policies.
- For each Advanced DNS Security domain category, specify a Log Severity and Policy Action to take when a domain type is detected using a corresponding analysis engine. There are currently two analysis engines available: DNS Misconfiguration Domains and Hijacking Domains.Policy Action Options:
- allow—The DNS query is allowed.You can configure the firewall to generate an alert when the applicable domain type is detected by setting the action to allow and the log severity to informational.
- block—The DNS query is blocked.
- sinkhole—Forges a DNS response for a DNS query targeting a detected malicious domain. This directs the resolution of the malicious domain name to a specific IP address (referred to as the Sinkhole IP), which is embedded as the response. The default Sinkhole IP address is set to access a Palo Alto Networks server. Palo Alto Networks can automatically refresh this IP address through content updates.
Log Severity Options:- none—The event does not have an associated log severity level.
- low—Warning-level threats that have very little impact on an organization's infrastructure. They usually require local or physical system access and may often result in victim privacy or DoS issues and information leakage.
- informational—Suspicious events that do not pose an immediate threat, but that are reported to call attention to deeper problems that could possibly exist.
- medium—Minor threats in which impact is minimized, such as DoS attacks that do not compromise the target or exploits that require an attacker to reside on the same LAN as the victim, affect only non-standard configurations or obscure applications, or provide very limited access.
- high—Threats that have the ability to become critical but have mitigating factors; for example, they may be difficult to exploit, do not result in elevated privileges, or do not have a large victim pool.
- critical—Serious threats, such as those that affect default installations of widely deployed software, result in root compromise of servers, and the exploit code is widely available to attackers. The attacker usually does not need any special authentication credentials or knowledge about the individual victims and the target does not need to be manipulated into performing any special functions.
- Click OK to exit the Anti-Spyware Security Profile configuration dialog and Commit your changes.
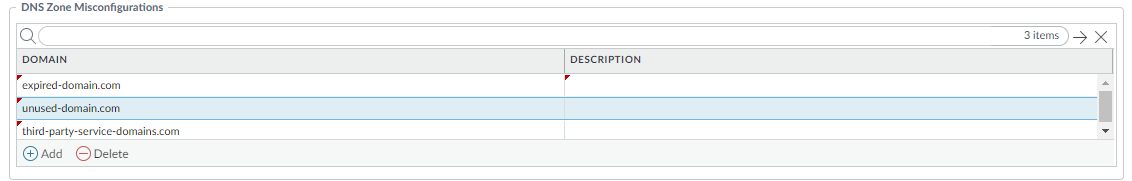
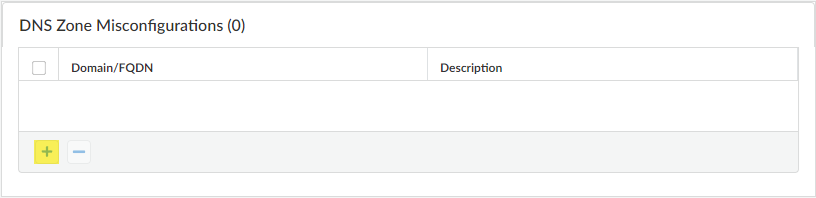
(Optional) Specify any public-facing parent domains within your organization that you want Advanced DNS Security to analyze and monitor for the presence of misconfigured domains. Misconfigured domains are inadvertently created by domain owners who point alias records to third party domains using CNAME, MX, NS record types, using entries that are no longer valid, allowing an attacker to take over the domain by registering the expired or unused domains.TLDs (top-level domains) and root level domains cannot be added to the DNS Zone Misconfigurations list.![]()
- Select an Anti-Spyware security profile (ObjectsSecurity ProfilesAnti-Spyware) and go to DNS Policies.
- In the DNS Zone Misconfigurations section, add public-facing parent domains with an optional description to assist you in identifying domain usage or ownership within your organization.Entries must have a "." contained in the domain using the following format (e.g. paloaltonetworks.com), otherwise it gets parsed as a hostname, which is considered a private domain.
- Click OK to exit the Anti-Spyware Security Profile configuration dialog and Commit your changes.
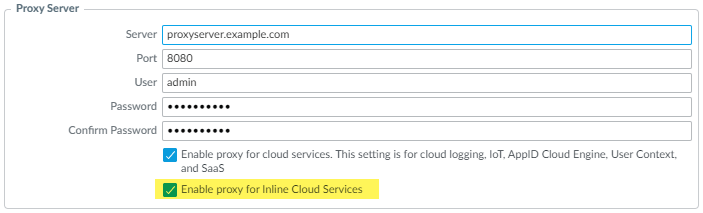
(Optional) Configure the maximum Advanced DNS signature lookup timeout setting. When this value is exceeded, the DNS response passes through without performing analysis using Advanced DNS Security.(Optional [If you do not have the latest device certificate]) Install an updated firewall device certificate used to authenticate to the Repeat for all firewalls enabled for inline cloud analysis.If you have already installed an updated firewall device certificate as part of your IoT Security, Device Telemetry, Advanced Threat Prevention, or Advanced URL Filtering onboarding process, this step is not necessary.(Required when the firewall is deployed with an explicit proxy server) Configure the proxy server used to access the servers that facilitate requests generated by all configured inline cloud analysis features. A single proxy server can be specified and applies to all Palo Alto Networks update services, including all configured inline cloud and logging services.- (PAN-OS 11.2.3 and later) Configure the proxy server through PAN-OS.
- Select Device Setup Services and edit the Services details.
- Specify the Proxy Server settings and Enable proxy for Inline Cloud Services. You can provide either an IP address or FQDN in the Server field.The proxy server password must contain a minimum of six characters.
![]()
- Click OK.
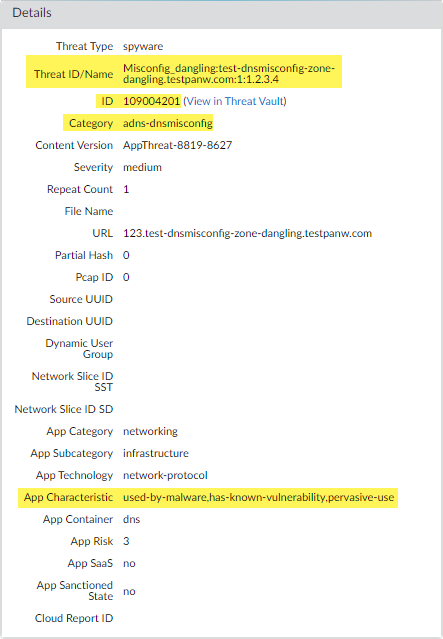
(Optional) Verify the status of your firewall connectivity to the(Optional) Monitor activity on the firewall for DNS queries that have been detected using Advanced DNS Security. DNS Security Categories analyzed using Advanced DNS Security real-time analysis of the DNS response packet have the prefix ‘adns’ followed by the category. For example, adns-dnsmisconfig, whereby ‘dnsmisconfig’ indicates the supported DNS category type. If the DNS domain category was determined by analyzing the DNS request packet, the specified category is displayed with the prefix ‘dns’ followed by the category. For example, ‘dns-grayware.’- Access theSelect MonitorLogsThreat. You can filter the logs based on the specific type of Advanced DNS Security domain category, for example ( category-of-threatid eq adns-hijacking ), whereby the variable adns-hijacking indicates DNS queries that have been categorized as a malicious DNS hijacking attempt by Advanced DNS Security. The following Advanced DNS Security threat categories available in the logs:Advanced DNS Security Categories
- DNS Hijacking—adns-hijackingDNS Hijacking domains have a threat ID of (UTID: 109,004,100).
- DNS
Misconfiguration—adns-dnsmisconfigDNS Misconfiguration domains have three threats IDs, which correspond to three variants of DNS misconfiguration domains types: dnsmisconfig_zone (UTID: 109,004,200), dnsmisconfig_zone_dangling (UTID: 109,004,201), and dnsmisconfig_claimable_nx (UTID: 109,004,202). You can constrain the search by cross-referencing a Threat-ID value that corresponds to a specific DNS misconfiguration domain type. For example, ( category-of-threatid eq adns-dnsmisconfig ) and (threatid eq 109004200), whereby 109004200 indicates the Threat ID of a DNS misconfiguration domain that does not route traffic to an active domain due to a DNS server configuration issue.
DNS Categories analyzed using Advanced DNS Security enhanced response analysis.You must operate a firewall running PAN-OS 11.2 and later to take advantage of enhanced Advanced DNS Security real-time analysis.- DNS —adns-benign
- Malware Domains —adns-malware
- Command and Control Domains—adns-c2
- Phishing Domains—adns-phishing
- Dynamic DNS Hosted Domains—adns-ddns
- Newly Registered Domains—adns-new-domain
- Grayware Domains—adns-grayware
- Parked Domains—adns-parked
- Proxy Avoidance and Anonymizers—adns-proxy
- Ad Tracking Domains—adns-adtracking
If the DNS query does not complete within the specified timeout period for Advanced DNS Security, the DNS Security categorization will be used, when possible. In those instances, the legacy notation for the category is used, for example, instead of adns-malware, it will be categorized as dns-malware, indicating that the DNS Security categorization value was used.Select a log entry to view the details of the DNS query.The DNS Category is displayed under the Details pane of the detailed log view. In addition, you can see other aspects of the threat, including the Threat ID, which includes the origin domain, the specific threat category, and other associated characteristics, as well as the associated Q type, and R data using the following format: hijacking:<FQDN>:<QTYPE>:<RDATA>, whereby <QTYPE> represents the DNS resource record type and <RDATA> represents the hijacked IP Address.![]() (Optional) Retrieve a list of misconfigured domains and hijacked domains detected by the Advanced DNS Security service. The misconfigured domains are based on the public-facing parent domain entries added to DNS Zone Misconfigurations.Misconfigured domain entries that are removed from your network are not immediately reflected in the Advanced DNS Security dashboard statistics.
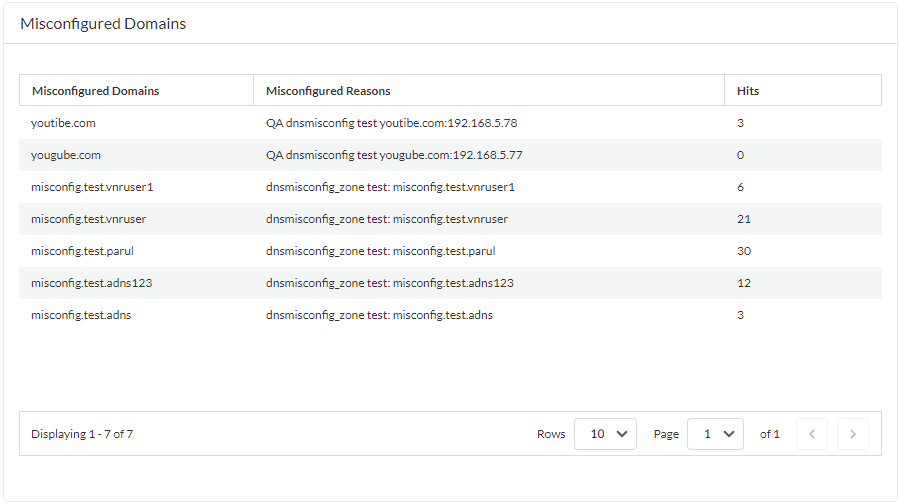
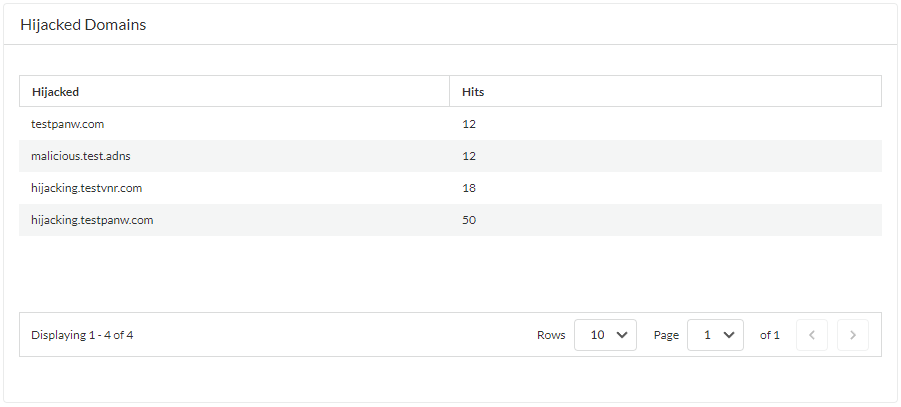
(Optional) Retrieve a list of misconfigured domains and hijacked domains detected by the Advanced DNS Security service. The misconfigured domains are based on the public-facing parent domain entries added to DNS Zone Misconfigurations.Misconfigured domain entries that are removed from your network are not immediately reflected in the Advanced DNS Security dashboard statistics.- Use the credentials associated with your Palo Alto Networks support account and log in to Strata Cloud Manager on the hub.Select DashboardsMore DashboardsDNS Security to open the DNS Security dashboard.From the DNS Security dashboard, refer to the following widgets:
- Misconfigured Domains—View a list of non-resolvable domains associated with the user-specified public-facing parent domain(s). For each entry, there is a misconfiguration reason and a traffic hit count based on the source IP.
![]()
- Hijacked Domains—View a list of hijacked domains as determined by Advanced DNS Security. For each entry, there is a categorization reason and a traffic hit count based on the source IP.
![]()
Enable Advanced DNS Security (Strata Cloud Manager)
- Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager on the hub.Verify that a DNS Security and a Threat Prevention license is active. Select ConfigurationNGFW and Prisma AccessOverview and click the license usage terms link in the License panel. You should see green check marks next to the following security services: Antivirus, Anti-Spyware, Vulnerability Protection, and DNS Security.Update or create a new DNS Security profile to enable real-time Advanced DNS Security queries. Typically, this is your existing DNS Security profile used for the DNS Security configuration.
- Select an existing DNS Security profile or Add a new one (ConfigurationNGFW and Prisma AccessSecurity ServicesDNS Security).
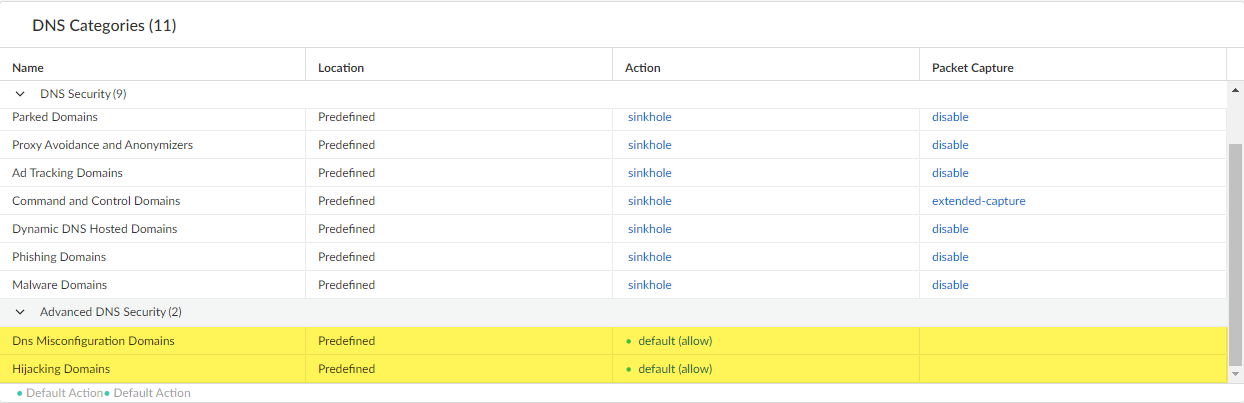
- Select your DNS Security profile and then go to DNS Categories.
![]()
- For each Advanced DNS Security domain category, specify a policy Action to take when a corresponding domain type is detected. There are currently two analysis engines available: DNS Misconfiguration Domains and Hijacking Domains.Policy Action Options:
- allow—The DNS query is allowed.You can configure Strata Cloud Manager to generate an alert when the applicable domain type is detected by setting the action to allow and the log severity to informational.
- block—The DNS query is blocked.
- sinkhole—Forges a DNS response for a DNS query targeting a detected malicious domain. This directs the resolution of the malicious domain name to a specific IP address (referred to as the Sinkhole IP), which is embedded as the response. The default Sinkhole IP address is set to access a Palo Alto Networks server. Palo Alto Networks can automatically refresh this IP address through content updates.
(Optional) Specify any public-facing parent domains within your organization that you want Advanced DNS Security to analyze and monitor for the presence of misconfigured domains. Misconfigured domains are inadvertently created by domain owners who point alias records to third party domains using CNAME, MX, NS record types, using entries that are no longer valid, allowing an attacker to take over the domain by registering the expired or unused domains.TLDs (top-level domains) and root level domains cannot be added to the DNS Zone Misconfigurations list.- Select a DNS Security profile (ConfigurationNGFW and Prisma AccessSecurity ServicesDNS Security) that contains an Advanced DNS Security configuration.
- In the DNS Zone Misconfigurations section, add public-facing parent domains with an optional description to assist you in identifying domain usage or ownership within your organization.Entries must have a "." contained in the domain using the following format (e.g. paloaltonetworks.com), otherwise it gets parsed as a hostname, which is considered a private domain.
![]()
- Click OK to exit and save the DNS Security security profile.
(Optional) Monitor activity on Strata Cloud Manager for DNS queries that have been detected using Advanced DNS Security. DNS Security Categories analyzed using Advanced DNS Security real-time analysis of the DNS response packet have the prefix ‘adns’ followed by the category. For example, adns-dnsmisconfig, whereby ‘dnsmisconfig’ indicates the supported DNS category type. If the DNS domain category was determined by analyzing the DNS request packet, the specified category is displayed with the prefix ‘dns’ followed by the category. For example, ‘dns-grayware.’- Access theSelect Log Viewer. You can filter the threat logs based on the specific type of Advanced DNS Security domain category, for example threat_category.value = 'adns-hijacking', whereby the variable adns-hijacking indicates DNS queries that have been categorized as a malicious DNS hijacking attempt by Advanced DNS Security. The following Advanced DNS Security threat categories available in the logs:Advanced DNS Security Categories
- DNS Hijacking—adns-hijackingDNS Hijacking domains have a threat ID of (UTID: 109,004,100).
- DNS
Misconfiguration—adns-dnsmisconfigDNS Misconfiguration domains have three threats IDs, which correspond to three variants of DNS misconfiguration domains types: dnsmisconfig_zone (UTID: 109,004,200), dnsmisconfig_zone_dangling (UTID: 109,004,201), and dnsmisconfig_claimable_nx (UTID: 109,004,202). You can constrain the search by cross-referencing a Threat-ID value that corresponds to a specific DNS misconfiguration domain type. For example, threat_category.value = 'adns-dnsmisconfig' and Threat ID = 109004200, whereby 109004200 indicates the Threat ID of a DNS misconfiguration domain that does not route traffic to an active domain due to a DNS server configuration issue.
DNS Categories analyzed using Advanced DNS Security enhanced response analysis.- DNS —adns-benign
- Malware Domains —adns-malware
- Command and Control Domains—adns-c2
- Phishing Domains—adns-phishing
- Dynamic DNS Hosted Domains—adns-ddns
- Newly Registered Domains—adns-new-domain
- Grayware Domains—adns-grayware
- Parked Domains—adns-parked
- Proxy Avoidance and Anonymizers—adns-proxy
- Ad Tracking Domains—adns-adtracking
If the DNS query does not complete within the specified timeout period for Advanced DNS Security, the DNS Security categorization will be used, when possible. In those instances, the legacy notation for the category is used, for example, instead of adns-malware, it will be categorized as dns-malware, indicating that the DNS Security categorization value was used.Select a log entry to view the details of the DNS query.The DNS Category is displayed under the General pane of the detailed log view. In addition, you can see other aspects if the threat, including the origin URL, the specific threat type, and associated characteristics.(Optional) Retrieve a list of misconfigured domains and hijacked domains detected by the Advanced DNS Security service. The misconfigured domains are based on the public-facing parent domain entries added to DNS Zone Misconfigurations. This is available as a request through AI Canvas.