Advanced DNS Security Powered by Precision AI®
Configure DNS Security Over TLS
Table of Contents
Configure DNS Security Over TLS
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can get visibility and control into DNS Security over TLS requests by decrypting the DNS
payload contained within the encrypted DNS request. The decrypted DNS payload can
then be processed using the security profile configuration containing your DNS
policy settings. DNS requests that have been determined to have originated from TLS
sources have a source port of 853 in the threat logs.
Configure DNS Security Over TLS (Strata Cloud Manager)
- Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager application on the hub.Enable DNS Security is configured to inspect DNS requests. You can use your existing security profile if you want to use the same DNS Policies settings for DNS Security over TLS traffic.Create a decryption policy rule with an action to decrypt HTTPS traffic on port 853, which includes DNS Security over TLS traffic (refer to the Decryption Best Practices for more information). When DNS Security over TLS traffic is decrypted, the resulting DNS requests in the logs appear as conventional dns-base applications.(Optional) Search for activity on the firewall for decrypted TLS-encrypted DNS queries that have been processed using DNS Security.
- Select Log Viewer and use the drop down to filter the logs based on the Threat log type. Use the query builder to filter based on the application using dns-base and port 853 (which is exclusively used for DNS Security over TLS transactions), for example, app = 'dns-base' AND source_port = 853.Select a log entry to view the details of the detected DNS threat.The Application should display dns-base in the General pane and the Port in the Source pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding tabs.
Configure DNS Security Over TLS (NGFW (Managed by PAN-OS or Panorama))
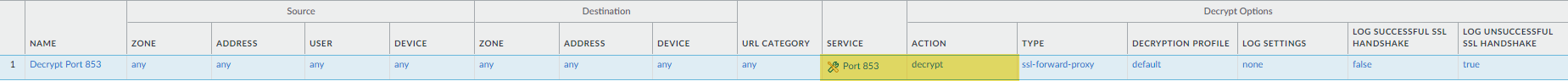
- Log in to the NGFW.Enable DNS Security is configured to inspect DNS requests. You can use your existing security profile if you want to use the same DNS Policies settings for DNS Security over TLS traffic.Create a decryption policy rule (similar to the example below) with an action to decrypt HTTPS traffic on port 853, which includes DNS Security over TLS traffic (refer to the Decryption Best Practices for more information). When DNS Security over TLS traffic is decrypted, the resulting DNS requests in the logs appear as conventional dns-base applications.
![]() (Optional) Search for activity on the firewall for decrypted TLS-encrypted DNS queries that have been processed using DNS Security.
(Optional) Search for activity on the firewall for decrypted TLS-encrypted DNS queries that have been processed using DNS Security.- Select MonitorLogsTraffic and filter based on the application using dns-base and port 853 (which is exclusively used for DNS Security over TLS transactions), for example, ( app eq dns-base ) and ( port.src eq 853 ).Select a log entry to view the details of a detected DNS threat.The Application should display dns-base in the General pane and the Port in the Source pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.