Advanced DNS Security Powered by Precision AI®
Configure DNS Security Over DoH
Table of Contents
Configure DNS Security Over DoH
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can analyze and categorize the DNS payload contained within encrypted DNS traffic requests to
DNS hosts using HTTPS (DoH—[DNS-over-HTTPS]). If your organization currently blocks
all DoH requests as Palo Alto Networks recommends, you can transition away from that
policy as DNS Security now enables you extract the DNS hostname from the encrypted
request and apply your organization’s existing DNS Security policies. This allows
you to safely access more websites as support for DoH widens. DNS Security support
for DoH is enabled by configuring the firewall to decrypt the payload of DNS
requests originating from a user-specified list of DNS resolvers, providing support
for a range of server options. The decrypted DNS payload can then be processed using
the Anti-spyware profile configuration containing your DNS policy configuration. DNS
requests that have been determined to be DoH are labeled as
dns-over-https in the traffic logs.
Configure DNS Security Over DoH (Strata Cloud Manager)
- Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager on the hub.Create a Custom URL Category list that includes all DoH resolvers you want to enable traffic to/from (you will need the DNS server URL(s)).Create a Decryption Policy Rule that references the custom URL category list that you created in the previous step.Update or create a new anti-spyware security profile used to inspect DoH requests.Create or update a security policy rule and reference a DNS Security profile and a custom URL category list (ConfigurationPAN-OS and Prisma AccessSecurity ServicesURL Access Management) containing the approved list of DoH servers.Create a block policy to decrypt HTTPS traffic and block all remaining unsanctioned DoH traffic that is not explicitly allowed by the custom URL category list (referenced in step 5) by using the App-ID: dns-over-https and the following URL category: encrypted-dns.If you already have an existing block policy to block DoH traffic, verify that the rule is placed below the previous security policy rule used to match with specific DoH resolvers listed in a custom URL category list object.(Optional) Search for activity on the firewall for HTTPS-encrypted DNS queries that have been processed using DNS Security.
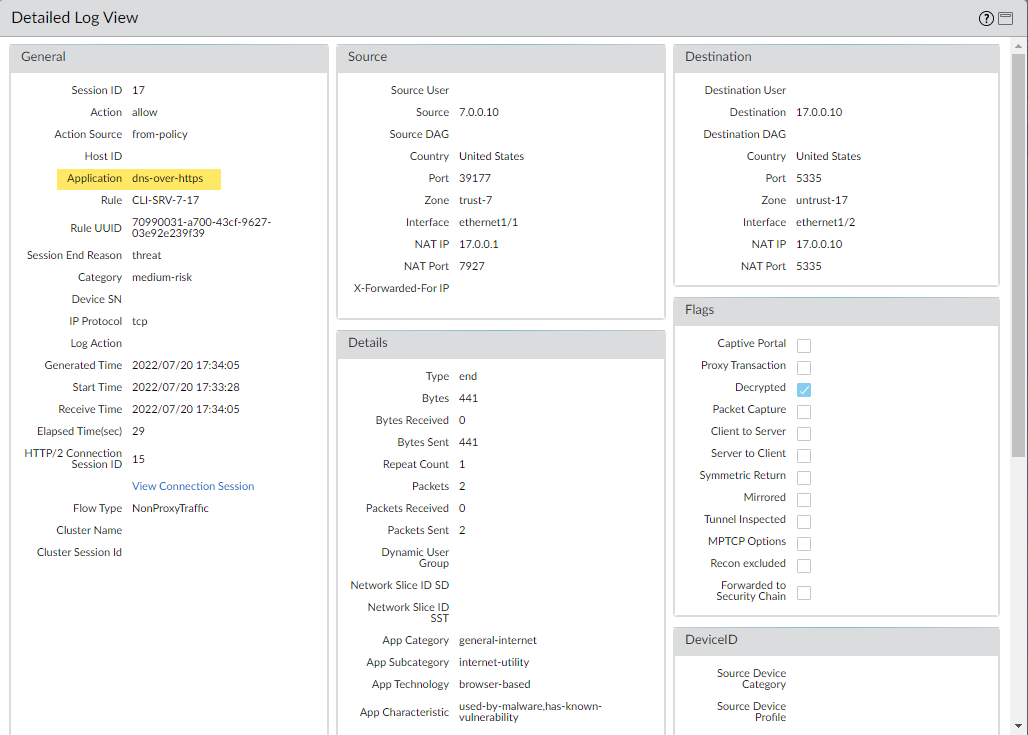
- Select Log Viewer and use the drop down to select the Threat log type.Submit a log query based on the application, using dns-over-https, for example, app = 'dns-over-https'.Select a log entry to view the details of a detected DNS threat that uses DoH.The threat Application is displayed in the General pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.
Configure DNS Security Over DoH (PAN-OS 11.0 and Later)
- Log in to theCreate a Custom URL Category list that includes all DoH resolvers you want to enable traffic to/from (you will need the DNS server URL(s)).Create a Decryption Policy Rule that references the custom URL category list that you created in the previous step.Update or create a new anti-spyware security profile used to inspect DoH requests.Create or update a security policy rule and reference an anti-spyware profile and a custom URL category list (ObjectsCustom ObjectsURL Category) containing the approved list of DoH servers.Create a block policy to decrypt HTTPS traffic and block all remaining unsanctioned DoH traffic that is not explicitly allowed by the custom URL category list (referenced in step 5) by using the App-ID: dns-over-https and the following URL category: encrypted-dns.If you already have an existing block policy to block DoH traffic, verify that the rule is placed below the previous security policy rule used to match with specific DoH resolvers listed in a custom URL category list object.(Optional) Search for activity on the firewall for HTTPS-encrypted DNS queries that have been processed using DNS Security.
- Select MonitorLogsTraffic and filter based on the application using dns-over-https, for example, ( app eq dns-over-https ).Select a log entry to view the details of a detected DNS threat.The Application should display dns-over-https in the General pane of the detailed log view, indicating that this is DoH traffic that has been processed using DNS Security. Other relevant details about the threat are displayed in their corresponding windows.
![]()