Prisma Access Agent
Configure Advanced DNS Security Resolver for Prisma Access Agent
Table of Contents
Configure Advanced DNS Security Resolver for Prisma Access Agent
Configure Advanced DNS Security Resolver to provide DNS security protection when
Prisma Access Agent cannot establish tunnel connections or when users disconnect from the
tunnel.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Advanced DNS Security Resolver provides DNS security for your mobile users when the
Prisma Access Agent tunnel is disconnected. This service maintains consistent threat
protection and content filtering by intercepting DNS queries and forwarding them to
Palo Alto Networks resolvers over encrypted HTTPS connections.
Advanced DNS Security Resolver applies DNS Security and enforces DNS policies
that you configured on the Advanced DNS Resolver page in
Strata Cloud Manager.
When to Use Advanced DNS Security Resolver
You should implement Advanced DNS Security Resolver if you want Always-On security
but your mobile users frequently encounter situations where maintaining full tunnel
connectivity is challenging or impractical. Common scenarios include users working
at customer sites where the use of Prisma Access Agent is blocked, experiencing
network performance issues that require tunnel disconnection, or accessing
sanctioned SaaS applications that perform better with direct connectivity.
How Advanced DNS Security Resolver Works
Advanced DNS Security Resolver operates by transparently intercepting DNS queries
from endpoints running Prisma Access Agent. When the tunnel is
disconnected,
the agent forwards these queries to Palo Alto Networks DNS resolvers using
DNS-over-HTTPS (DoH) protocol. The resolvers apply your DNS Security and enforces
your DNS policies before returning the DNS response to the endpoint.
Key Components
Forwarding Profiles define how the system routes DNS traffic. You configure
steering configuration within forwarding profiles to specify when domains should be
resolved by Advanced DNS Security Resolver and when they should use the local DNS
server. You can configure this on a per-application basis.
Authentication Tokens enable secure, authorized communication between Prisma
Access Agent and Advanced DNS Security Resolver. The system uses user access tokens
for policy enforcement and device tokens for longer-term authentication when users
do not actively log in.
DoH Connectivity establishes an encrypted communication channel between an
endpoint and the Palo Alto Networks DNS resolver. Advanced DNS Security Resolver
maintains primary and secondary resolvers for redundancy.
When you configure Advanced DNS Security Resolver, it provides seamless DNS security
that activates automatically based on your configuration and current endpoint
network conditions.
Before You Begin
- Ensure that you have administrator access to Strata Cloud Manager
- Identify internal domains that should bypass Advanced DNS Security Resolver resolution for use with the forwarding profile
- Configure Advanced DNS Security Resolver.
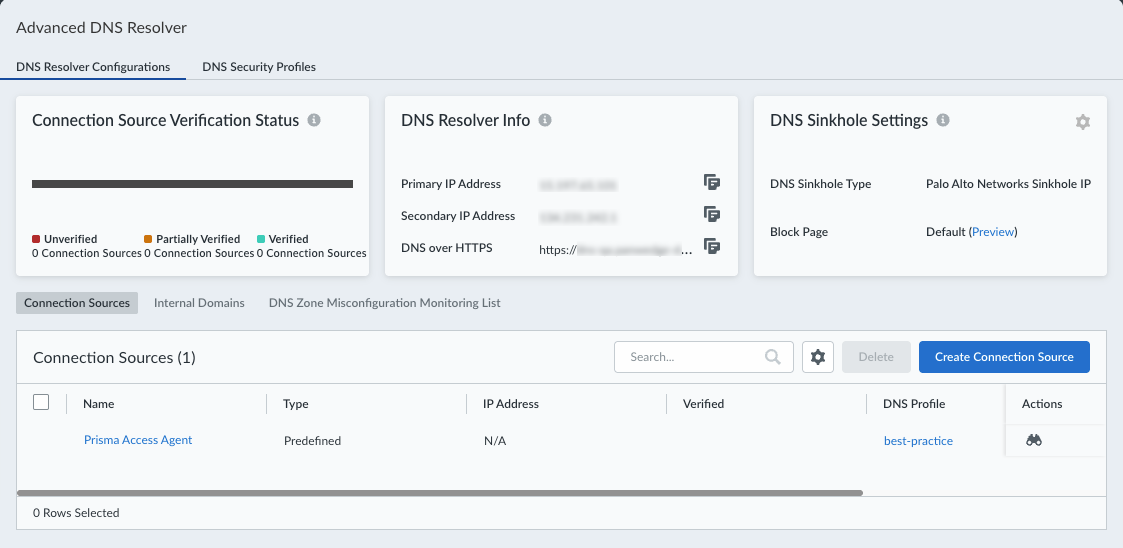
- Select ConfigurationADNS ResolverDNS Resolver Configurations.Use the predefined Prisma Access Agent connection source.The Prisma Access Agent connection source will appear only if you have the licenses for Prisma Access Agent and Advanced DNS Security Resolver.
![]() Use the predefined best-practice DNS security profile or create a DNS security profile to define categories that you want to allow, block, sinkhole, or alert users about.(Optional) Define domain overrides for custom FQDNs and EDL definitions.Configure forwarding profiles by selecting Configuration NGFW and Prisma Access Configuration ScopeMobile Users ContainerSetup.Edit the settings in the Forwarding Profiles Setup section.Set up a connectivity option for Advanced DNS Security Resolver.As a best practice, do not change the default Best Available connectivities.
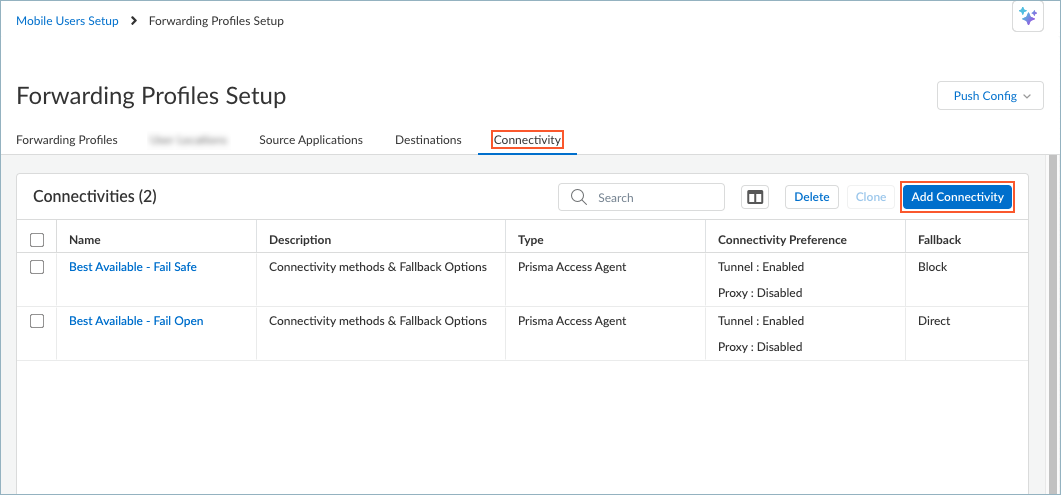
Use the predefined best-practice DNS security profile or create a DNS security profile to define categories that you want to allow, block, sinkhole, or alert users about.(Optional) Define domain overrides for custom FQDNs and EDL definitions.Configure forwarding profiles by selecting Configuration NGFW and Prisma Access Configuration ScopeMobile Users ContainerSetup.Edit the settings in the Forwarding Profiles Setup section.Set up a connectivity option for Advanced DNS Security Resolver.As a best practice, do not change the default Best Available connectivities.- In the Forwarding Profiles Setup page, select ConnectivityAdd Connectivity.
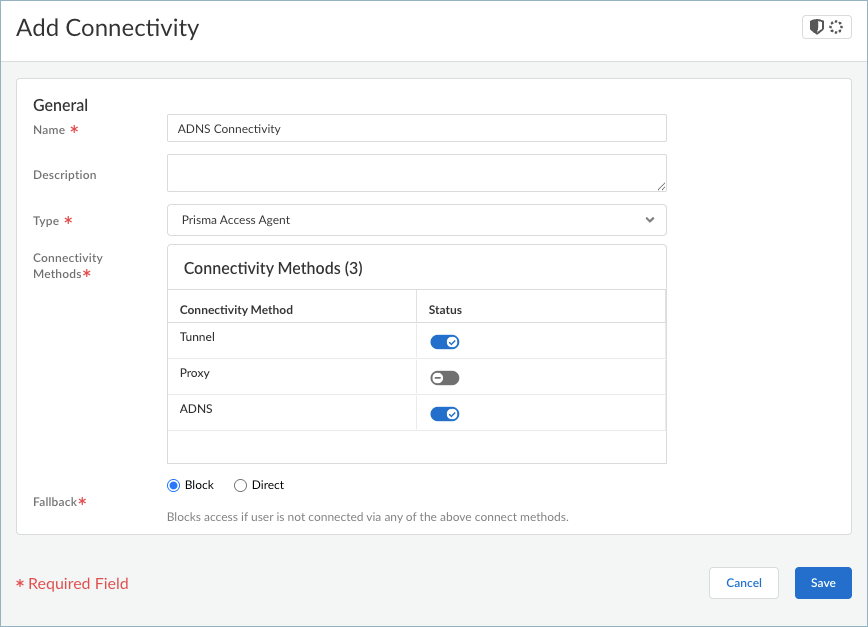
![]() Enter a Name for the connectivity option for Advanced DNS Security Resolver, such as ADNS Connectivity.Select TypePrisma Access Agent.Configure a connectivity method to direct traffic to Advanced DNS Security Resolver by enabling Tunnel and ADNS in the Connectivity Methods table.
Enter a Name for the connectivity option for Advanced DNS Security Resolver, such as ADNS Connectivity.Select TypePrisma Access Agent.Configure a connectivity method to direct traffic to Advanced DNS Security Resolver by enabling Tunnel and ADNS in the Connectivity Methods table.![]() Be sure to enable the Tunnel connectivity method. You can enable the ADNS method only when Tunnel is enabled.Select a Fallback behavior if the user is not connected using the specified connectivity methods. You can prevent access (Block) or allow access (Direct).Save your connectivity settings.Set up a Destination for the domains that you want to forward to Advanced DNS Security Resolver. Be sure to include all private destinations that users might need to access.Ensure that the Prisma Access Agent list of included or exclude domains are in sync with the domains for Advanced DNS Security Resolver on Strata Cloud Manager.
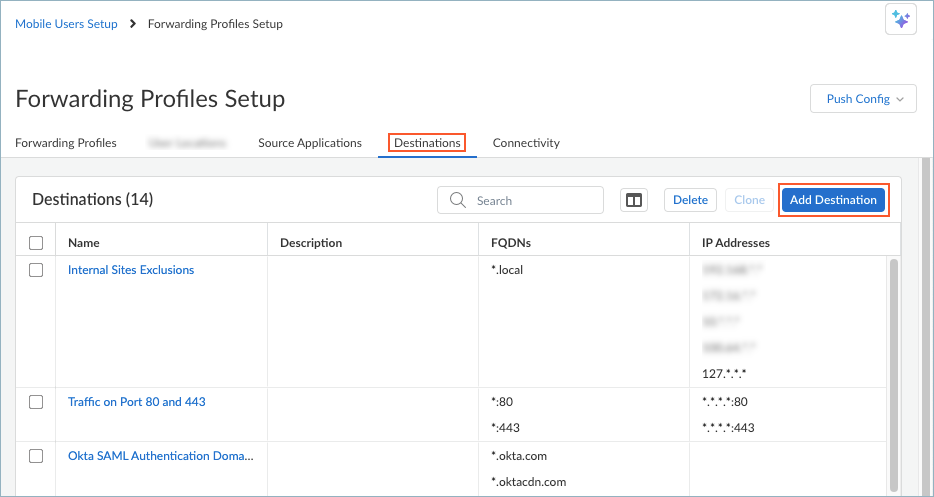
Be sure to enable the Tunnel connectivity method. You can enable the ADNS method only when Tunnel is enabled.Select a Fallback behavior if the user is not connected using the specified connectivity methods. You can prevent access (Block) or allow access (Direct).Save your connectivity settings.Set up a Destination for the domains that you want to forward to Advanced DNS Security Resolver. Be sure to include all private destinations that users might need to access.Ensure that the Prisma Access Agent list of included or exclude domains are in sync with the domains for Advanced DNS Security Resolver on Strata Cloud Manager.- In the Forwarding Profiles Setup page, select DestinationsAdd Destination.
![]() Enter a meaningful Name for the destination, such as adns-inclusions.In the FQDNs table, enter the domains to exclude, for example, *.example.com or internal.corp.Save the destinations.Set up a Destination for the domains that you don't want to forward to Advanced DNS Security Resolver. Be sure to include all private destinations that you don't want to forward to Advanced DNS Security Resolver.Ensure that the Prisma Access Agent list of included or exclude domains are in sync with the domains for Advanced DNS Security Resolver on Strata Cloud Manager.
Enter a meaningful Name for the destination, such as adns-inclusions.In the FQDNs table, enter the domains to exclude, for example, *.example.com or internal.corp.Save the destinations.Set up a Destination for the domains that you don't want to forward to Advanced DNS Security Resolver. Be sure to include all private destinations that you don't want to forward to Advanced DNS Security Resolver.Ensure that the Prisma Access Agent list of included or exclude domains are in sync with the domains for Advanced DNS Security Resolver on Strata Cloud Manager.- In the Forwarding Profiles Setup page, select DestinationsAdd Destination.Enter a meaningful Name for the destination, such as adns-exclusions.In the FQDNs table, enter the domains to exclude, for example, *.example.com or internal.corp.Save the destinations.Create a forwarding profile that allows or excludes traffic based on the source applications, destination, or connectivity options that you defined.
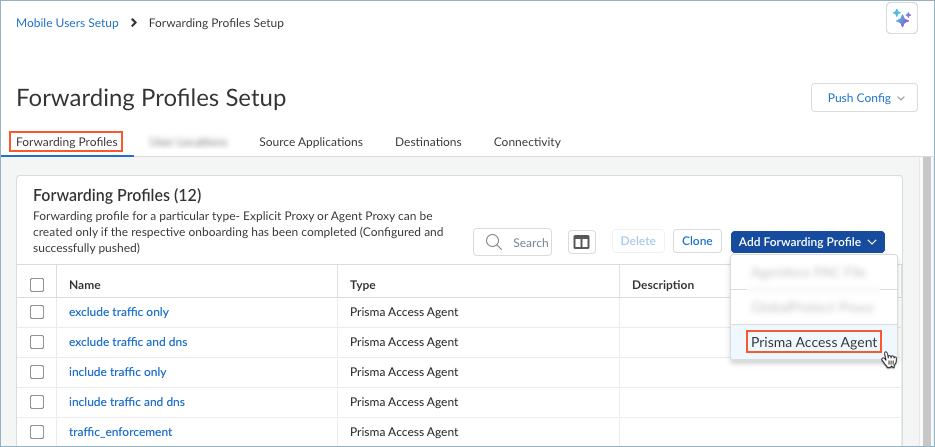
- In the Forwarding Profiles Setup page, choose an existing profile to modify or select Forwarding ProfilesAdd Forwarding ProfilePrisma Access Agent to create a new profile.
![]() For new profiles, enter a descriptive Name for the forwarding profile, for example, ADNS-Enabled-Profile.Modify the existing Default forwarding rule using ADNS connectivity.
For new profiles, enter a descriptive Name for the forwarding profile, for example, ADNS-Enabled-Profile.Modify the existing Default forwarding rule using ADNS connectivity.- Set Connectivity to the ADNS connectivity method that you created. For example, ADNS Connectivity.
- Update the forwarding rule.
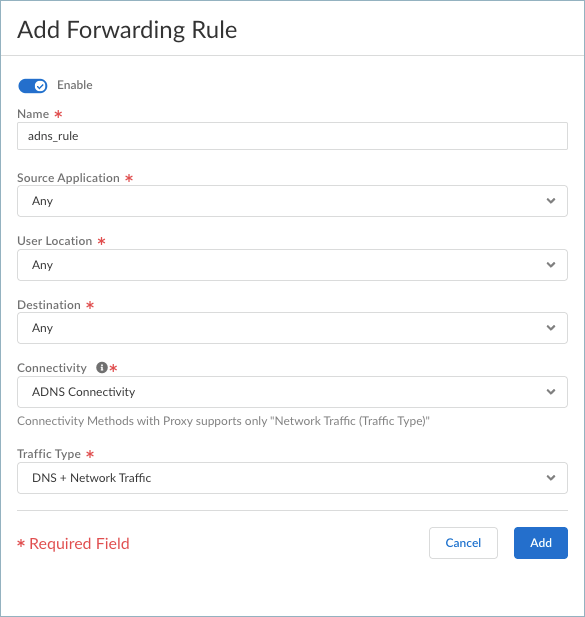
If you need to customize the domains that should be forwarded to Advanced DNS Security Resolver, Add an inclusion rule to forward the domains to Advanced DNS Security Resolver if the tunnel goes down.- Enter a meaningful Name for the rule, such as adns-rule.
- For Source Applications, select Any.
- For Destinations, select the adns-inclusions destination that you created.
- Set Connectivity to the ADNS connectivity method that you set up. For example, ADNS Connectivity
- For Traffic Type, select DNS or DNS + Network Traffic.If you select DNS + Network Traffic, DNS traffic routes to Advanced DNS Security Resolver while network traffic routes to the tunnel.
- Add the adns-rule forwarding rule.For example:
![]()
Add an exclusion rule to the forwarding profile for domains that should not be forwarded to Advanced DNS Security Resolver, and should be secured by the tunnel once the tunnel is up.- Enter a meaningful Name for the rule, such as local-resolver.
- For Source Applications, select Any.
- For Destinations, select the adns-exclusions destination that you created.
- Set Connectivity to any non-ADNS connectivity method, such as the Best Available connectivity objects or custom connectivity that you set up. This directs specified DNS queries to the endpoint's local DNS resolver.
- For Traffic Type, select DNS or DNS + Network Traffic.If you select DNS + Network Traffic, DNS traffic routes to Advanced DNS Security Resolver while network traffic routes to the tunnel.
- Add the local-resolver forwarding rule.
In the Forwarding Rules table of your forwarding profile, adjust the rule order to ensure exclusion rules are processed before the general adns_rule forwarding rule.Save your forwarding profile.Commit the changes to deploy the Advanced DNS Security Resolver forwarding profile configuration.- Select Push ConfigPush.Enter a Description for the job. This field is required.Select the GlobalPrisma AccessMobile UsersAccess Agent container and Push.Wait for the job to finish and Close the Jobs dialog.Verify the configuration.
- Confirm that Advanced DNS Security Resolver is functioning correctly after deployment. For example:
- Check agent connectivity status to verify Advanced DNS Security Resolver communication.
- Review DNS security logs to confirm that queries are routing through the Advanced DNS Security Resolver.
- Test DNS resolution for both allowed and blocked domains to verify policy enforcement.
- View DNS Security Logs and search for DNS queries submitted from Prisma Access Agent and processed by the Advanced DNS Resolver.