Network Security
Configure your Environment to Access an External Dynamic List from the EDL Hosting Service
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Configure your Environment to Access an External Dynamic List from the EDL Hosting Service
Configure an External Dynamic List (EDL) for Software-as-a-Service (SaaS)
applications.
Set up your configuration to access an external dynamic list (EDL) from
the EDL Hosting Service for Software-as-a-Service (SaaS) applications
Convert the GlobalSign Root R1 Certificate to PEM Format
You must convert the GlobalSign Root R1 certificate to
PEM format to create a certificate profile for
authenticating the EDL Hosting Service. Creating the certificate profile to
authenticate the EDL Hosting Service is a best practice when leveraging the EDL
Hosting Service when you configure your environment to access an external
dynamic list from the EDL Hosting Service.
Refer to the appropriate procedure based on operating system of the device where
you downloaded the GlobalSign Root R1 certificate.
- Download the GlobalSign Root R1 certificate if you have not already downloaded the certificate.Convert the certificate.
- Mac and Linux operating systems
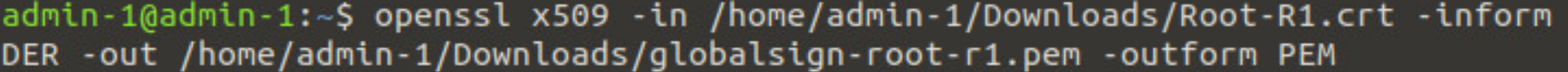
- Open the terminal and convert the GlobalSign Root R1 certificate you downloaded.admin: openssl x509 -in <certificate-path>.crt -inform DER -out <target-export-path>.pem -outform PEM
![]() If no target export path is specified, the converted certificate is created on the device desktop.
If no target export path is specified, the converted certificate is created on the device desktop.- Windows operating system
- Navigate to the location where you downloaded the GlobalSign Root1 certificate.
- Double click and Open the certificate.
- Click Details and Copy to File.Click Next when prompted to continue.
- Select Base-64 encoded x.509 (.CER) and click Next
- Click Browse to navigate to the location you want to copy the certificate and enter a name for the certificate that includes .pem appended to the end of file name. For example, globalsign-root-r1.pemSave the certificate. The File Name displayed shows the target export path and the certificate name you entered with .cer appended. Delete the appended.cer.
![]()
- Click Next and Finish exporting the certificate.
Create an External Dynamic List Using the EDL Hosting Service
Some Software-as-a-Service (SaaS) providers publish lists of IP addresses and URLs as destination endpoints for their SaaS applications. SaaS providers frequently update the SaaS applications destination endpoint lists as support grows and the service expands. This requires you to manually monitor the SaaS application endpoints for changes and manually update your policy configuration to ensure connectivity to these critical SaaS applications or set up an external tool to monitor and update your EDLs.Configure an EDL using the EDL Hosting Service maintained by Palo Alto Networks to ease the operational burden of maintaining an EDL for a SaaS application. The EDL Hosting Service provides publicly available Feed URLs for SaaS application endpoints published by the SaaS application provider. Leveraging a Feed URL as the source in an EDL allows for dynamic enforcement of SaaS application traffic without the need for you to host and maintain your own EDL source.Palo Alto Networks checks the application Feed URLs published by SaaS providers on a daily basis and optimizes the IP address information received from SaaS application providers in order to reduce the number of IP addresses that are published in each EDL. This optimization includes identifying and removing duplicate IP addresses and then aggregating the remaining IP addresses into a smaller number of contiguous address ranges.Microsoft updates all Microsoft 365 Feed URLs at the end of each calendar month and provides a 30 day advanced notice prior to update. See the official Microsoft 365 Web Services page for more information. Additionally, the endpoints for the Microsoft 365 Common and Office Online SaaS application are always added to every Feed URL in the EDL Hosting Service.The EDL Hosting Service availability status and updates are posted to the Palo Alto Networks Cloud Services Status page.Follow these steps to create an external dynamic list using the EDL Hosting Service.Create an External Dynamic List Using the EDL Hosting Service (Strata Cloud Manager)
Leveraging a Feed URL as the source in an EDL allows for dynamic enforcement of SaaS application traffic without the need for you to host and maintain your own EDL source.- Visit the EDL Hosting Service and identify the Feed URL for your SaaS application.Review the Microsoft 365 documentation for more information which Feed URL is best for your use case. Additionally, consider the SaaS application and location of users accessing the SaaS application when identifying a Feed URL to. For example, if you have a branch in Germany that only needs to access Exchange Online, select a Feed URL from the Service Area: Exchange Online for Germany.For a policy-based forwarding policy rule, use an IP-based Feed URL.(Best Practices) Create a certificate profile to authenticate the EDL Hosting Service.
- Download the GlobalSign Root R1 certificate.Convert the GlobalSign Root R1 Certificate to PEM Format.Import the GlobalSign Root R1 certificate.
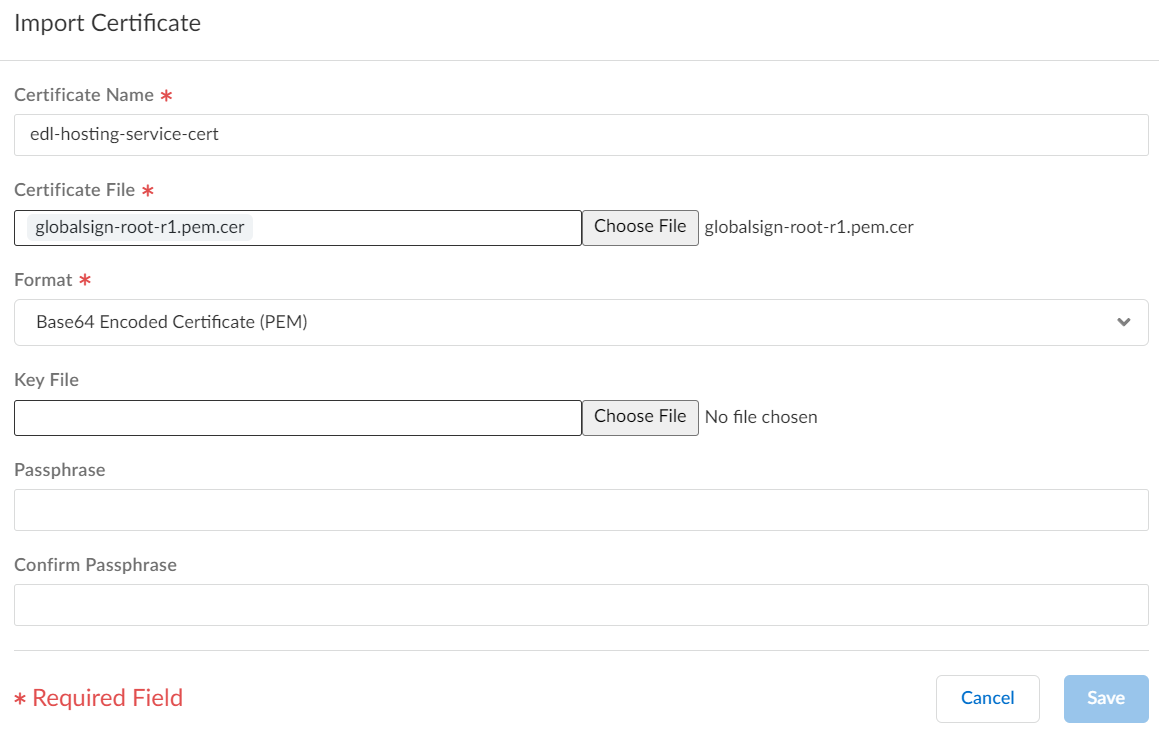
- Select ConfigurationNGFW and Prisma AccessObjectsCertificate ManagementCustom Certificates and Import a new custom certificate.
- Enter a descriptive Certificate Name.
- For the Certificate File, select Browse and select the certificate you converted in the previous step.
- For the Format, select Base64 Encoded Certificate (PEM).
- Select Save.
![]() Create a certificate authority (CA) certificate profile.
Create a certificate authority (CA) certificate profile.- Select ConfigurationNGFW and Prisma AccessObjectsCertificate ManagementCertificate Profiles and Add Profile.
- Enter a descriptive Name.
- For the CA Certificates, Add the certificate you imported in the previous step.
- Select Save.
![]() Select Push Config.Create an EDL using a Feed URL from the EDL Hosting Service.
Select Push Config.Create an EDL using a Feed URL from the EDL Hosting Service.- Select ConfigurationNGFW and Prisma AccessObjectsExternal Dynamic Lists and Add External Dynamic List.Enter a descriptive Name for the EDL.Select the EDL Type.
- For an IP-based EDL, select IP List.
- For a URL-based EDL, select URL List.
(Optional) Enter a Description for the EDLEnter the Feed URL as the EDL Source.Enforce all endpoints within a specific Feed URL. Adding an excluding a specific endpoint from a Feed URL can cause connectivity issues to the SaaS application.(Best Practices) Select the Certificate Profile you created in the previous step.Specify the frequency your environment should Check for updates to match the update frequency of the Feed URL.For example, if the Feed URL is updated daily by Palo Alto Networks then configure the EDL to check for updates Daily.Palo Alto Networks displays the update frequency for each Feed URL in the EDL Hosting Service. Feed URLs are automatically updated with any new endpoints.Select Save.![]() Enforce Policy on an External Dynamic List.When you enforce policy on an EDL from the EDL Hosting Service where the EDL is the source, be specific when configuring which users have access to the SaaS application to avoid over-provisioning access to the application.Leverage App-ID alongside EDLs in a security rule for additional strict enforcement of SaaS application traffic.
Enforce Policy on an External Dynamic List.When you enforce policy on an EDL from the EDL Hosting Service where the EDL is the source, be specific when configuring which users have access to the SaaS application to avoid over-provisioning access to the application.Leverage App-ID alongside EDLs in a security rule for additional strict enforcement of SaaS application traffic.Create an External Dynamic List Using the EDL Hosting Service (PAN-OS & Panorama)
Leveraging a Feed URL as the source in an EDL allows for dynamic enforcement of SaaS application traffic without the need for you to host and maintain your own EDL source.- Visit the EDL Hosting Service and identify the Feed URL for your SaaS application.Review the Microsoft 365 documentation for more information which Feed URL is best for your use case. Additionally, consider the SaaS application and location of users accessing the SaaS application when identifying a Feed URL to. For example, if you have a branch in Germany that only needs to access Exchange Online, select a Feed URL from the Service Area: Exchange Online for Germany.For a policy-based forwarding policy rule, use an IP-based Feed URL.(Best Practices) Create a certificate profile to authenticate the EDL Hosting Service.
- Download the GlobalSign Root R1 certificate.Convert the GlobalSign Root R1 Certificate to PEM Format.Launch the firewall web interface.Import the GlobalSign Root R1 certificate.
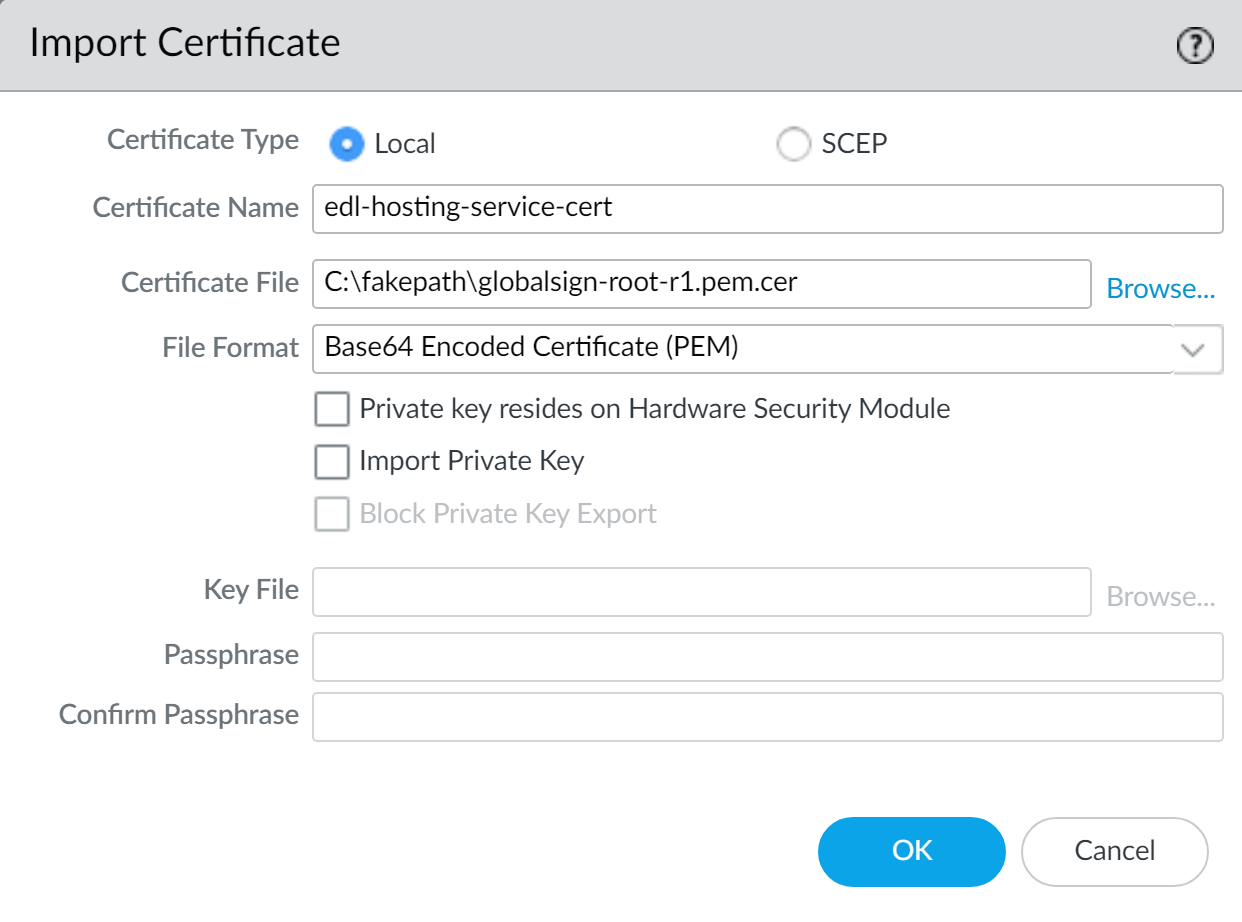
- Select DeviceCertificate ManagementCertificates and Import a new certificate.
- For Certificate Type, select Local.
- Enter a descriptive Certificate Name.
- For the Certificate File, select Browse and select the certificate you converted in the previous step.
- For the File Format, select Base64 Encoded Certificate (PEM).
- Click OK.
![]() Create a certificate authority (CA) certificate profile.
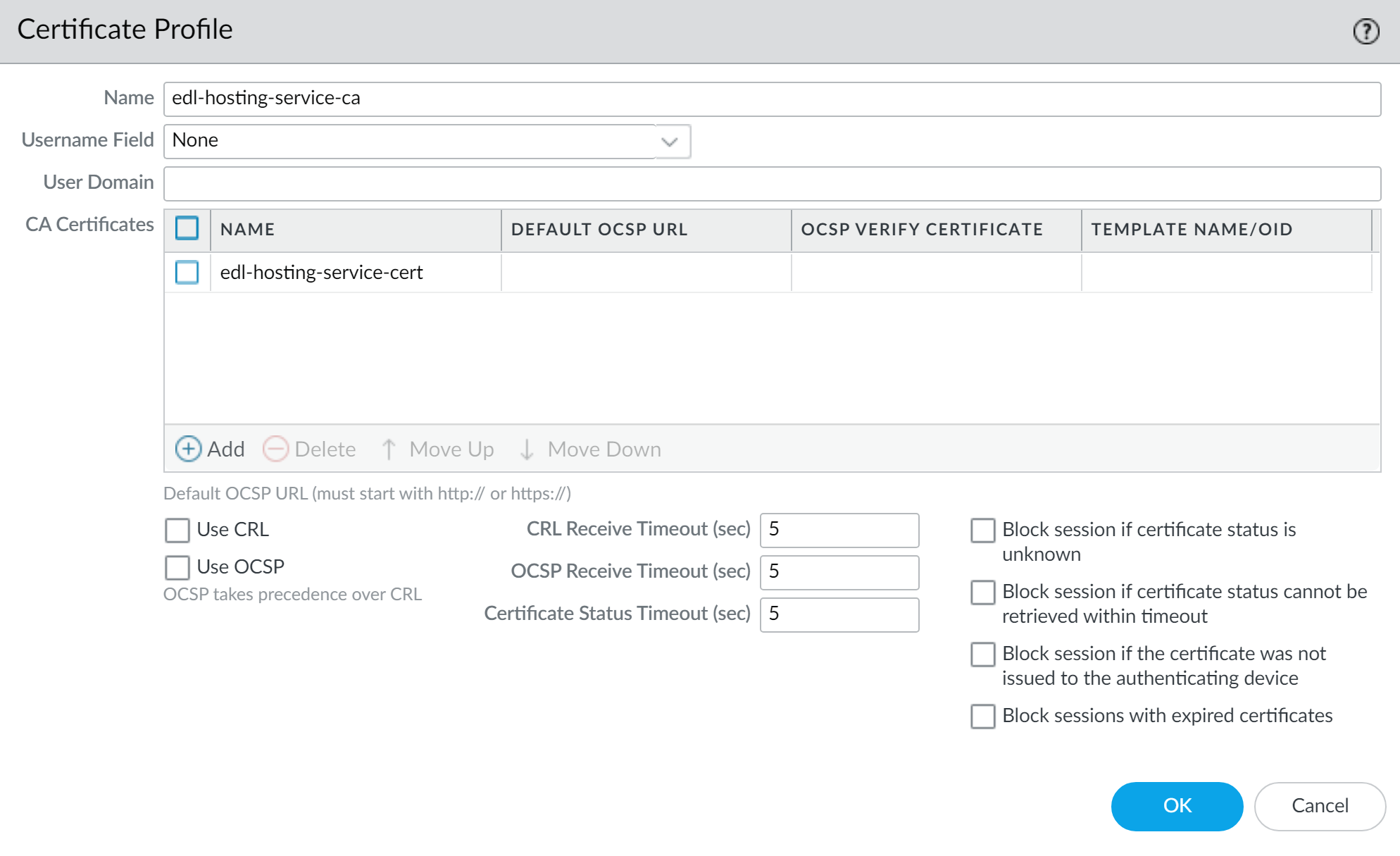
Create a certificate authority (CA) certificate profile.- Select DeviceCertificate ManagementCertificate Profile and Add a new certificate profile.
- Enter a descriptive Name.
- For the CA Certificates, Add the certificate you imported in the previous step.
- Click OK.
![]() Commit.Create an EDL using a Feed URL from the EDL Hosting Service.
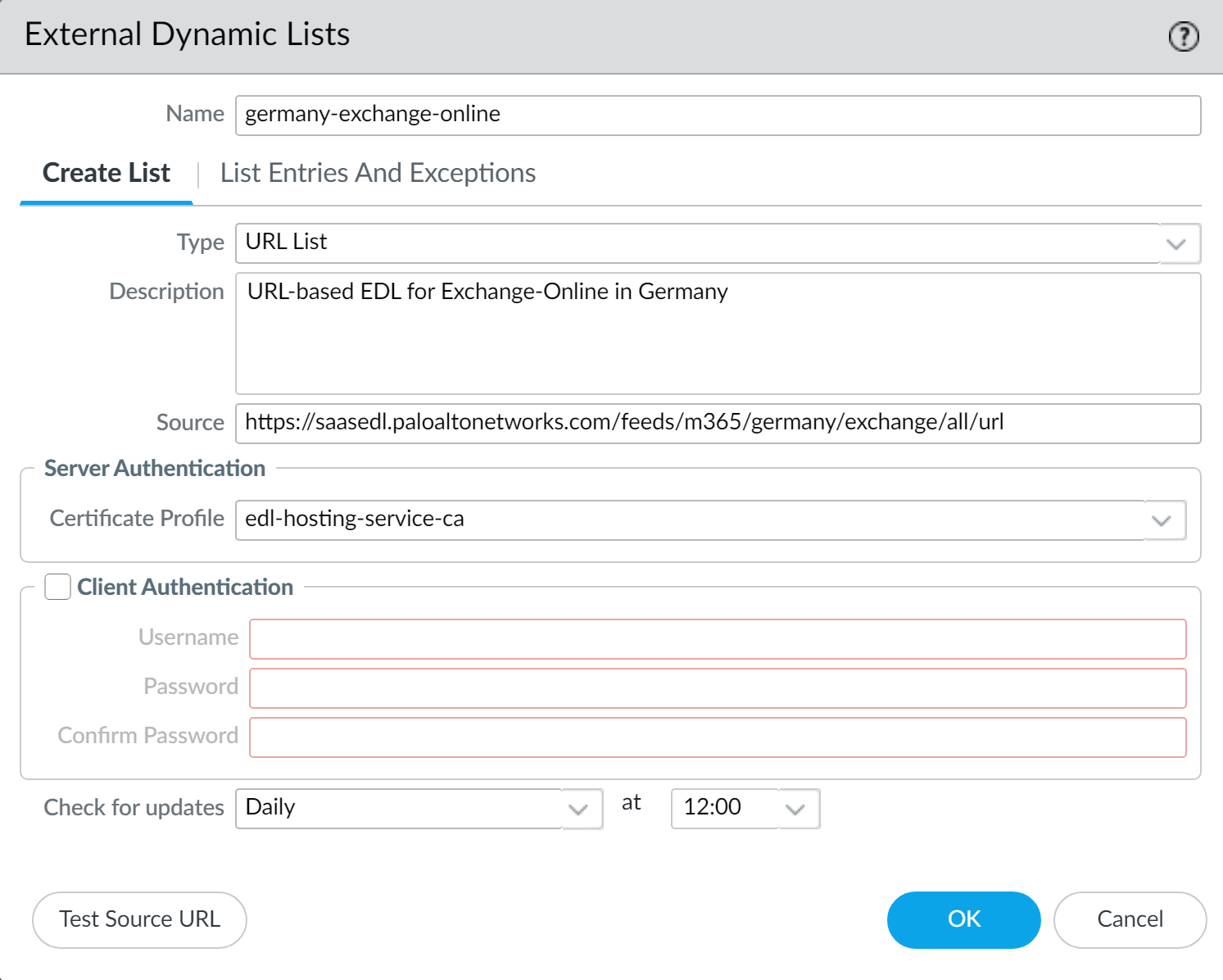
Commit.Create an EDL using a Feed URL from the EDL Hosting Service.- Select ObjectsExternal Dynamic Lists and Add a new EDL.Enter a descriptive Name for the EDL.Select the EDL Type.
- For an IP-based EDL, select IP List.
- For a URL-based EDL, select URL List.
(Optional) Enter a Description for the EDLEnter the Feed URL as the EDL Source.Enforce all endpoints within a specific Feed URL. Adding an excluding a specific endpoint from a Feed URL can cause connectivity issues to the SaaS application.(Best Practices) Select the Certificate Profile you created in the previous step.Specify the frequency the firewall should Check for updates to match the update frequency of the Feed URL.For example, if the Feed URL is updated daily by Palo Alto Networks then configure the EDL to check for updates Daily.Palo Alto Networks displays the update frequency for each Feed URL in the EDL Hosting Service. Feed URLs are automatically updated with any new endpoints.Click Test Source URL to verify that the firewall can access the Feed URL from the EDL Hosting Service.Click OK.![]() Enforce Policy on an External Dynamic List.When you enforce policy on an EDL from the EDL Hosting Service where the EDL is the source, be specific when configuring which users have access to the SaaS application to avoid over-provisioning access to the application.Leverage App-ID alongside EDLs in a security rule for additional strict enforcement of SaaS application traffic.
Enforce Policy on an External Dynamic List.When you enforce policy on an EDL from the EDL Hosting Service where the EDL is the source, be specific when configuring which users have access to the SaaS application to avoid over-provisioning access to the application.Leverage App-ID alongside EDLs in a security rule for additional strict enforcement of SaaS application traffic.