Multiple Certificate Support for SSL Inbound Inspection
Table of Contents
10.2
Expand all | Collapse all
-
- CN-Series Firewall as a Kubernetes CNF
- High Availability Support for CN-Series Firewall as a Kubernetes CNF
- High Availability Support for CN-Series Firewall on AWS EKS
- DPDK Support for CN-Series Firewall
- Daemonset(vWire) IPv6 Support
- Panorama Plugin for Kubernetes 3.0.0
- L3 IPV4 Support for CN-Series
- 47 Dataplane Cores Support for VM-Series and CN-Series Firewalls
- Memory Scaling of the VM-Series Firewall
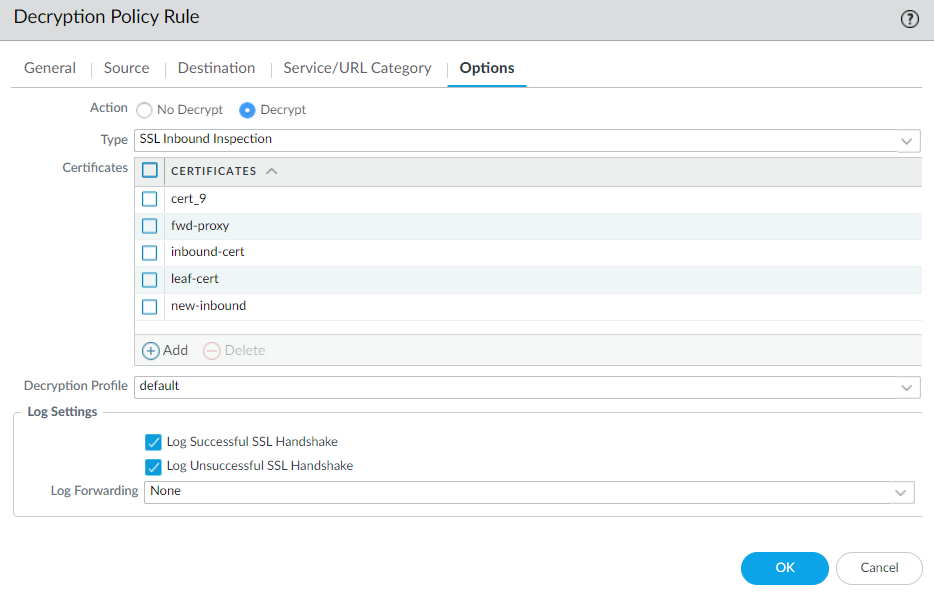
Multiple Certificate Support for SSL Inbound Inspection
You can add a new certificate to your SSL Inbound Inspection
decryption rule while an old certificate is still valid.
You can now configure SSL Inbound Inspection policy
rules with up to 12 server certificates. Newly added support for multiple
certificates enables you to update certificates on your protected
servers without decryption downtime. You can also configure rules
to decrypt and inspect traffic to servers that host multiple domains,
each with a different certificate.
To ensure a valid certificate
is always available, import the new server certificate and key on
your firewall and add it to your Decryption policy rule before updating
your web server. The firewall uses the old but valid server certificate
to proxy the connection between the client and your internal server
to decrypt and inspect inbound SSL/TLS traffic. After you install
the new certificate on your server, the firewall will use it for
new SSL/TLS connections as long as the certificate in your SSL Inbound
Inspection policy rule matches the server certificate. If a certificate mismatch
occurs, the session ends, and the Decryption log entry reports the session-end
reason as a firewall and server certificate mismatch.
(Panorama ™)
Support for multiple certificates in SSL Inbound Inspection policy
rules is unavailable in PAN-OS versions earlier than 10.2. If you
push an SSL Inbound Inspection policy rule with multiple certificates
from a Panorama management server running PAN-OS ® 10.2
to a firewall running an earlier version, only one certificate is
preserved in the policy rule on the firewall.
Before pushing
your Decryption policy rule from Panorama, we recommend you set
up different templates or device groups for firewalls running
PAN-OS 10.1 and earlier to ensure you push the correct policy rule and
certificate to the appropriate firewalls.
Perform
the following steps to update your firewall and SSL Inbound Inspection rule
with a newly issued server certificate.
- Import the new certificate and private key for the internal server whose inbound SSL traffic you want to decrypt and inspect to the firewall.Depending on the TLS version in use, you may need to upload the end-entity (leaf) certificate as part of a certificate bundle (single file) to the firewall to prevent server certificate validation errors.Add the certificate to your Decryption policy rule, then click OK.Upon clicking OK, the firewall automatically sorts the certificates alphabetically.
![]() Commit your changes.When you are ready...
Commit your changes.When you are ready...- Load your web server with the new certificate.(Best Practice) Remove expired or otherwise invalid certificates from your Decryption policy rule and the firewall.