Web Proxy
Table of Contents
11.0 (EoL)
Expand all | Collapse all
End-of-Life (EoL)
Web Proxy
If your network uses a proxy device, learn how to configure
a web proxy as either an explicit proxy or a transparent proxy to
route authentication traffic.
If your network uses a proxy device for security,
you can now leverage the same level of protection using the on-premises
web proxy capability with PAN-OS 11.0. The web proxy features enables additional
options for migrating from an existing web proxy architecture to
a simple unified management console. Using the web proxy feature
with Prisma Access provides
a seamless method for migrating, deploying, and maintaining secure
web gateway (SWG) configurations from an easy to use and simplified
interface. Web proxy helps during the transition from on-premises
to the cloud with no loss to security or efficiency.
The
web proxy supports two methods for routing traffic:
- For the explicit proxy
method, the request contains the destination IP address of the configured proxy
and the client browser sends requests to the proxy directly. You can use one of
following methods to authenticate users with the explicit proxy:
- Kerberos, which requires a web proxy license.
- SAML 2.0, which requires Panorama, a Prisma Access license, the Cloud Services 3.2.1 plugin (and later versions), and the add-on web proxy license.
- Cloud Identity Engine, which requires Panorama, a Prisma Access license, the Cloud Services 3.2.1 plugin (and later versions), and the add-on web proxy license.
- For the transparent proxy method, the request contains the destination IP address of the web server and the proxy transparently intercepts the client request (either by being in-line or by traffic steering). There is no client configuration and Panorama is optional. Transparent proxy requires a loopback interface, User-ID configuration in the proxy zone, and specific Destination NAT (DNAT) rules. Transparent proxy does not support X-Authenticated Users (XAU) or Web Cache Communications Protocol (WCCP).
The
following platforms support web proxy:
- PA-1400
- PA-3400
- VM Series (with a minimum of four vCPUs)
- Panorama using PAN-OS 11.0
- Cloud services plugin 3.2.1 (and later versions) for Explicit Proxy using SAML authentication
Web proxy supports
IPv4.
- Configure Explicit ProxyThe explicit proxy method allows you to troubleshoot issues more easily, since the client browser is aware of the existence of the proxy.
- If you have not already done so, activate
the license for web proxy. You must activate the web proxy license for the PA-1400 Series, PA-3400 Series, and VM-Series. Learn how to activate your subscription licenses for the PA-1400 Series and PA-3400 Series or activate the web proxy license for the VM-Series in the following step.
- Log in to the Customer Service Portal (CSP).
- Edit the deployment profile.
- Select Web Proxy (Promotional Offer).
![]()
- Click Update Deployment Profile.
- On the firewall, retrieve the license keys from the
server. If the license key retrieval is not successful, restart the firewall and repeat this step before proceeding.
- Set up the necessary interfaces and zones. As a best practice, use Layer 3 (L3) for the three interfaces the web proxy uses and configure a separate zone for each interface within the same virtual routers and the same virtual systems.
- Configure an interface for the client traffic. Be sure to carefully copy the IP address for this interface and save it in a secure location because you must enter it as the Proxy IP address when you configure the web proxy.
- Configure an interface for the outgoing traffic to the internet.
- Configure a loopback interface for the proxy. All incoming traffic is routed through this interface to the proxy.
- Configure an interface for the client traffic.
- Set up the DNS proxy for Explicit Proxy.
- Configure a DNS proxy object for the proxy connection.
- Configure a DNS Server profile with
both primary and secondary DNS servers.You must configure both a primary and a secondary DNS server for web proxy.
- Specify the interface for the proxy
connection.Specify either the traffic ingress interface or a loopback interface.
- To enable decryption for MITM detection, create a self-signed root CA certificate or import a certificate signed by your enterprise certificate authority (CA). For more information, refer to the best practices for administrative access.
- Ensure you have completed the pre-deployment steps for the authentication method you want to configure. Select only one of the following authentication methods.
- If you have a DNS security subscription, integrate the web proxy
firewall with Explicit Proxy to sinkhole any requests that match
the DNS security categories that you specify.
- Select PanoramaCloud ServicesConfigurationOn-Prem Proxy.
- Edit the settings then select the Device
Group you want the web proxy firewall to use or Add a
new device group. To integrate the web proxy firewall with Prisma Access, you must configure the web proxy firewall in a separate device group that contains no other firewalls or virtual systems. If the firewall is already a member of a device group, create a child device group as a sub-group and move the firewall to the child device group.
![]()
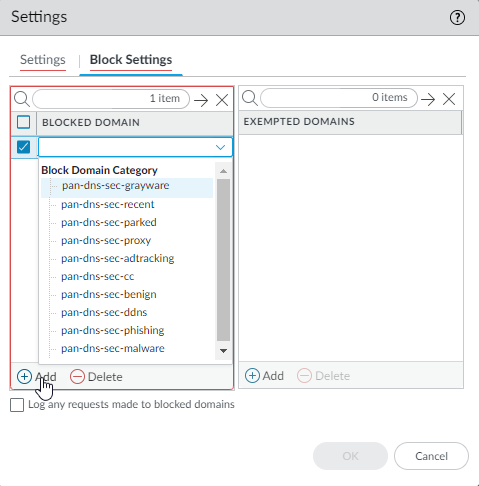
- (Optional) Select Block Settings to Add a
Blocked Domain or any domains that
are Exempted Domains because they are
sinkholed due to matching one or more of the DNS Security
categories.
![]()
- (Optional) Select whether you want to Log any requests made to blocked domains.
- Click OK.
- Set up the Explicit Proxy.
- On the firewall, select NetworkProxy then Edit the Proxy Enablement settings.
- Select Explicit Proxy as the Proxy
Type then click OK to confirm
the changes. If the only available option is None, verify that you have an active license for the web proxy feature.
![]()
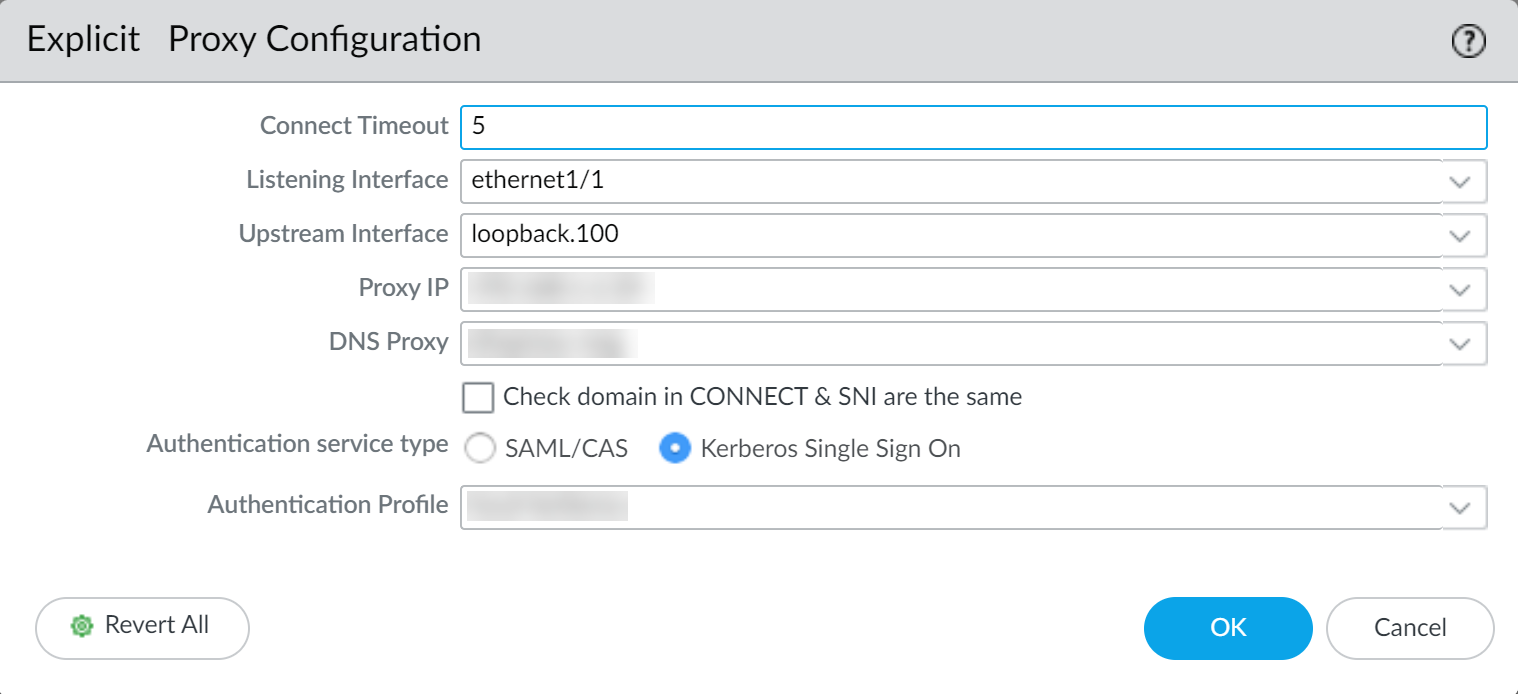
- Edit the Explicit Proxy Configuration.
![]()
- Specify the Connect Timeout to define (in seconds) how long the proxy waits for a response from the web server. If there is no response after the specified amount of time has elapsed, the proxy closes the connection.
- Select the Listening Interface that contains
the firewall where you want to enable the web proxy.Specify the ingress interface for the client traffic.
- Select the Upstream Interface that contains
the interface with the web proxy that reroutes the traffic to the
server.If you are using a loopback interface, specify that interface as the Upstream Interface.
- Specify the IP address of the listening interface as the Proxy IP.
Enter the IP address of the interface you created in Step 2.a.
- Specify the DNS Proxy object you created in Step 3.a.
- Select Check domain in CONNECT & SNI are the same to prevent domain fronting attacks by specifying different domains between the CONNECT request and the Server Name Indication (SNI) field in the HTTP header.
- Select the Authentication service type you want to use (either
SAML/CAS or Kerberos
Single Sign On). Be sure to complete all necessary pre-deployment and configuration steps for the authentication method you select. Select only one of the following authentication methods:
- Click OK to confirm the changes
- Configure the necessary security policy rules to decrypt traffic
and reroute applicable traffic to the proxy. You will need to create the following types of rules:
- Source NAT (if applicable)
- Decryption
- Security
- Configure a decryption
policy to decrypt the traffic so
it can be rerouted if necessary. To avoid decrypting traffic twice, select the zone that contains the upstream interface as the source zone for the decryption policy.
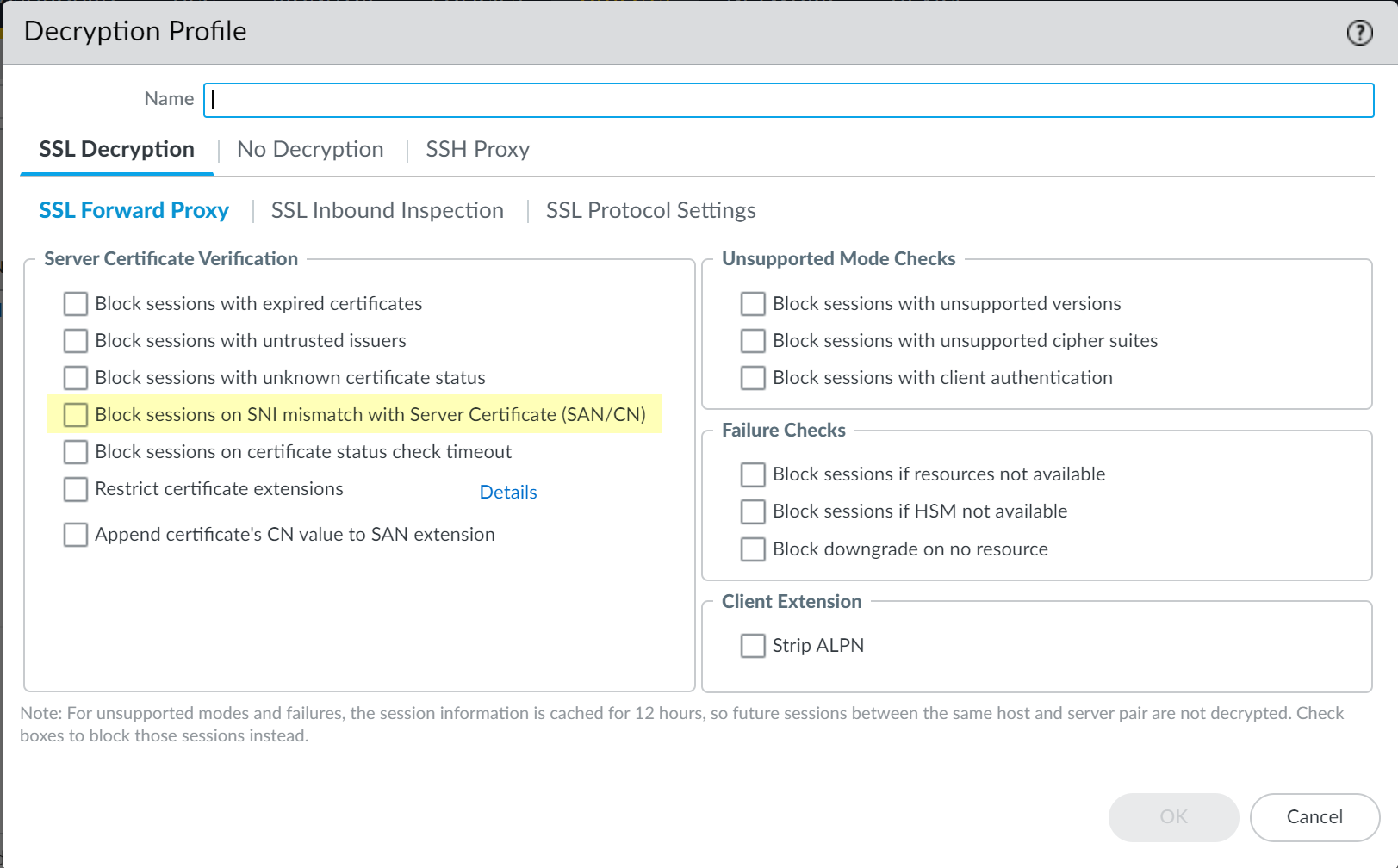
- (Optional but recommended) Select ObjectsDecryption Profile and select Block
sessions on SNI mismatch with Server Certificate (SAN/CN) to
automatically deny any sessions where the Server Name Indication
(SNI) does not match the server certificate.
![]()
- Configure the necessary security policy rules.
- Create a security policy rule to allow traffic from the client to the interface you selected as the listening interface.
- Configure a security policy rule to allow traffic from the zone that contains the upstream interface to the internet.
- Configure a security policy rule to allow traffic from the DNS proxy zone to the internet.
- Configure a security policy rule using the authentication profile you configured in Step 5 to route traffic to the proxy as appropriate.
Configure Transparent ProxyWith transparent proxy, the client browser is not aware of the proxy. Transparent proxy supports inline mode deployment and does not support web cache communication protocol (WCCP). Transparent proxy is transparent to the user without requiring additional authentication.- If you have not already done so, activate the license for web
proxy. This step is required for the PA-1400, PA-3400, and VM Series. The following steps are for the VM series; for the PA-1400 and PA-3400, follow the steps to activate subscription licenses.
- Log in to the Customer Service Portal (CSP).
- Edit the deployment profile.
- Select Web Proxy (Promotional Offer).
![]()
- Click Update Deployment Profile.
- On the firewall, retrieve the license keys from the
server. If the license key retrieval is not successful, restart the firewall and repeat this step before proceeding.
- Set up zones and interfaces. As a best practice, use Layer 3 (L3) for all interfaces and configure a separate zone for each interface within the same virtual routers and the same virtual systems.
- Configure an interface for the client.
- Configure an interface for the outgoing traffic to the internet.
- Configure a loopback interface for the proxy. All incoming traffic is routed through this interface to the proxy. Be sure to carefully copy the IP address for this interface and save it in a secure location because you must enter it as the Proxy IP address when you configure the web proxy.
- Set up the DNS proxy for Transparent Proxy.
- Configure a DNS proxy object for the proxy connection.
- Configure a DNS Server profile with
both primary and secondary DNS servers.You must configure both a primary and a secondary DNS server for web proxy.
- Specify the loopback interface for the proxy connection.
- To enable decryption for MITM detection, create a self-signed root CA certificate or import a certificate signed by your enterprise certificate authority (CA). For more information, refer to the best practices for administrative access.
- Set up the Transparent Proxy.
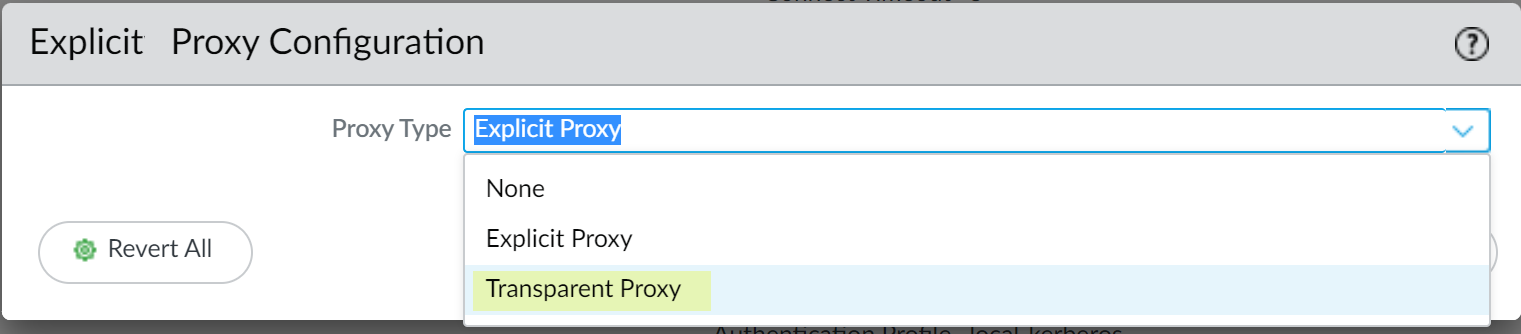
- On the firewall, select NetworkProxy then Edit the Proxy Enablement settings.
- Select Transparent Proxy as the Proxy
Type then click OK to confirm
the changes.If the only available option is None, verify that you have an active license for the web proxy feature.
![]()
- Edit the Transparent Proxy
Configuration.
![]()
- Specify the Connect Timeout to define (in seconds) how long the proxy waits for a TCP response from the web server. If there is no response after the specified amount of time has elapsed, the proxy closes the connection.
- Select the Upstream Interface.The upstream interface must be a loopback interface that is not associated with any other subnets.
- Specify the IP address of the loopback interface as the Proxy
IP. Enter the IP address of the interface you configured in Step 2.3.
- Specify the DNS Proxy object you created
in Step 3.Specify the loopback interface as the Upstream Interface.
- Click OK to confirm the changes.
- Configure the destination network address translation (DNAT)
policy. You must configure the DNAT policy rule exactly as described in the following steps for the firewall to successfully use the web proxy to route traffic. Be sure to configure the DNAT policy rule so that it precedes the source network address translation (SNAT) policy rule.
- Select PoliciesNAT and Add a NAT policy rule.
- Enter a unique Name and verify that Group
Rules by Tag is None then select
the NAT Type.
![]()
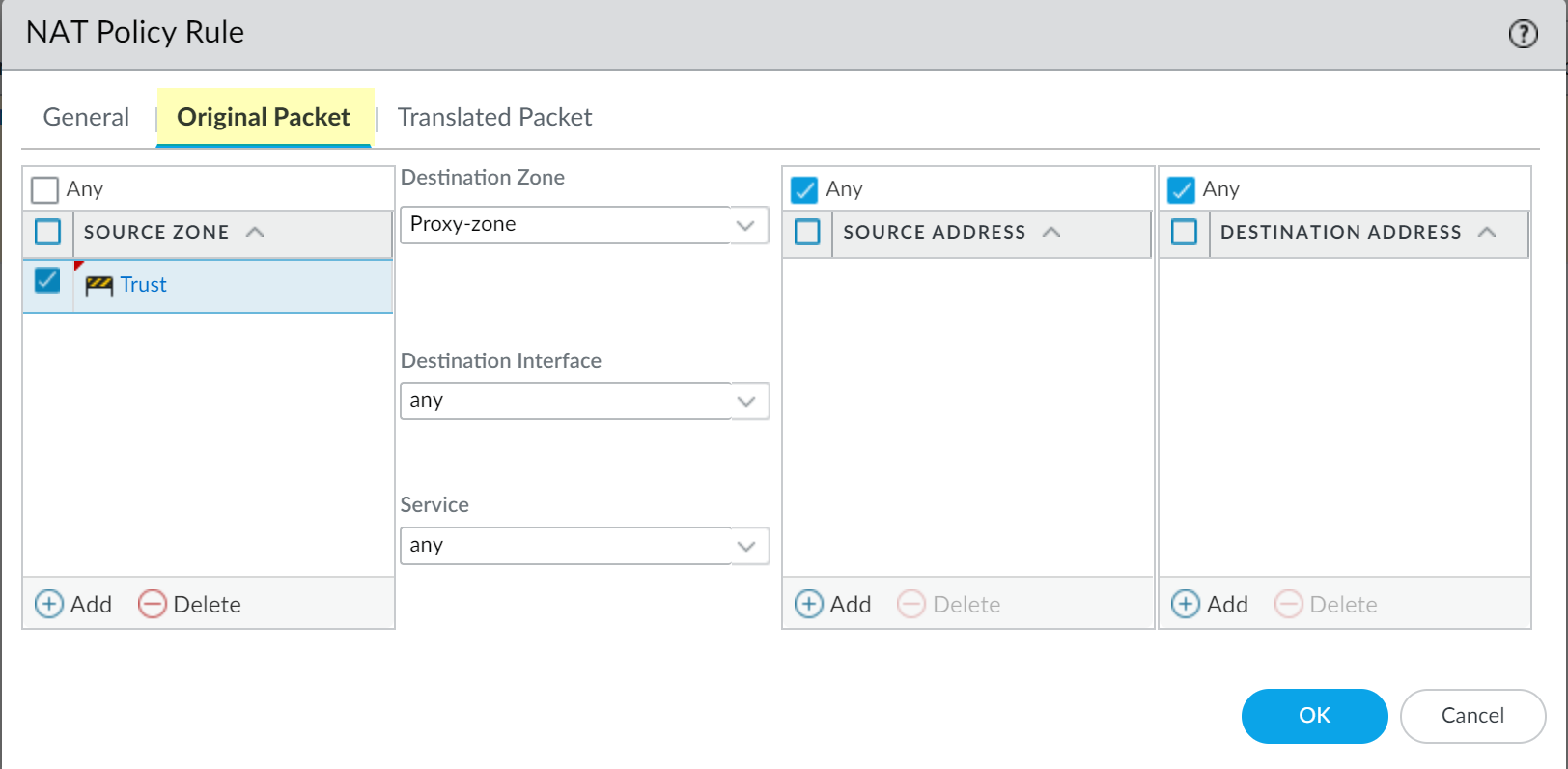
- Select Original Packet and Add a
trusted zone as the Source Zone and the Destination
Zone as the interface that contains the web proxy.
![]()
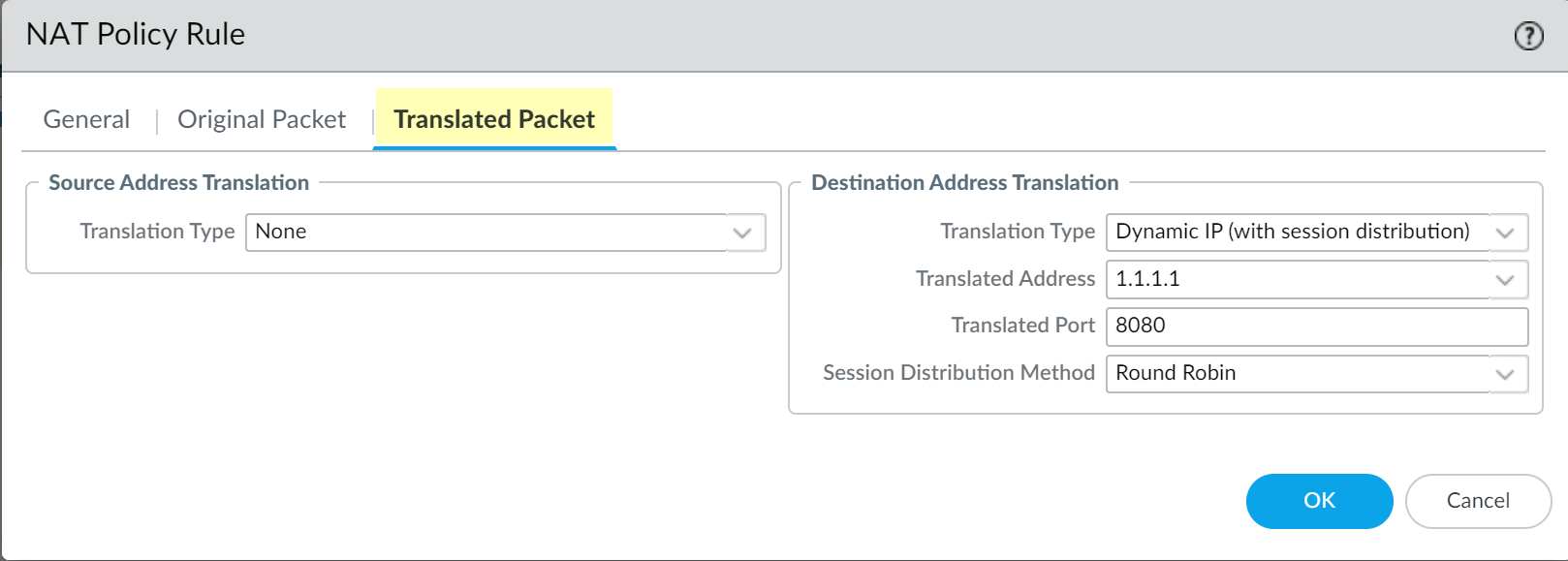
- Select Translated Packet and verify that Translation
Type for Source Address Translation is None.
![]()
- Select Dynamic IP (with session distribution) as the Translation Type for the Destination Address Translation.
- Enter the IP address of the web proxy as the Translated
Address. Enter the same IP address as the Proxy IP address specified in Step 2.3 and Step 5.6.
- Enter 8080 as the Translated Port.
- Select a Session Distribution Method (for
example, Round Robin). The session distribution method is not applicable for web proxy.
- Click OK and Commit the changes.
- Configure a security policy to allow and route the proxy traffic.
- Configure a source network address translation (SNAT) policy rule after the DNAT rule.
- Configure a decryption policy to decrypt traffic. Select the zone that contains the proxy interface as the source zone.
- (Optional but recommended) Select ObjectsDecryption Profile and select Block sessions on SNI
mismatch with Server Certificate (SAN/CN) to
automatically deny any sessions where the Server Name Indication
(SNI) does not match the server certificate.
![]()
- Configure policy rules to allow access to the DNS proxy servers for both the client and the proxy.
- Configure a policy rule to allow traffic from the client to the proxy.
- Configure a policy rule to allow traffic from the proxy to the internet.
- If you have not already done so, activate
the license for web proxy.