SaaS Agent Security
Enable Role Based Access to SaaS Agent Security
Table of Contents
Expand All
|
Collapse All
SaaS Agent Security Docs
Enable Role Based Access to SaaS Agent Security
Enable role-based access to SaaS Agent Security.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the SaaS Agent Security license:
|
Role-Based Access Control (RBAC) is a security mechanism that restricts system access
to authorized users based on their roles within an organization. For the SaaS Agent Security feature, RBAC is implemented to ensure a clear and
secure method for granting user access, aligning with domain-specific
responsibilities without requiring global super administrator privileges. This
approach leverages existing predefined roles within the Strata Cloud Manager,
avoiding the need to create new and custom roles.
Configure role-based access to SaaS Agent Security by assigning a
predefined role to your security administrators. The predefined roles you assign to
your security administrators define which parts of SaaS Agent Security
they have full or partial read and write access privileges. Review the table below
to understand the predefined roles that grant role-based access to SaaS Agent Security. This information pertains only to access privileges
specific to SaaS Agent Security. For detailed information about all
predefined roles and what other access privileges they grant, review the Roles and Permissions.
Add Predefined Role Based Access to SaaS Agent Security
- Use one of the various ways to access Identity & Access.(New admins only) Add Access to your tenant where SaaS Agent Security is active.This step is required only if the user for which you’re granting SaaS Agent Security access isn't already registered with the Palo Alto Networks Customer Support Portal (CSP).Assign any of the following predefined role-based access to SaaS Agent Security users.Predefined RolePermissions
- Superuser
- Data Security Administrator
- Posture Security Administrator
- MSP Superuser
- SOC Analyst
View Only AdministratorAdd Custom Role Based Access to SaaS Agent Security
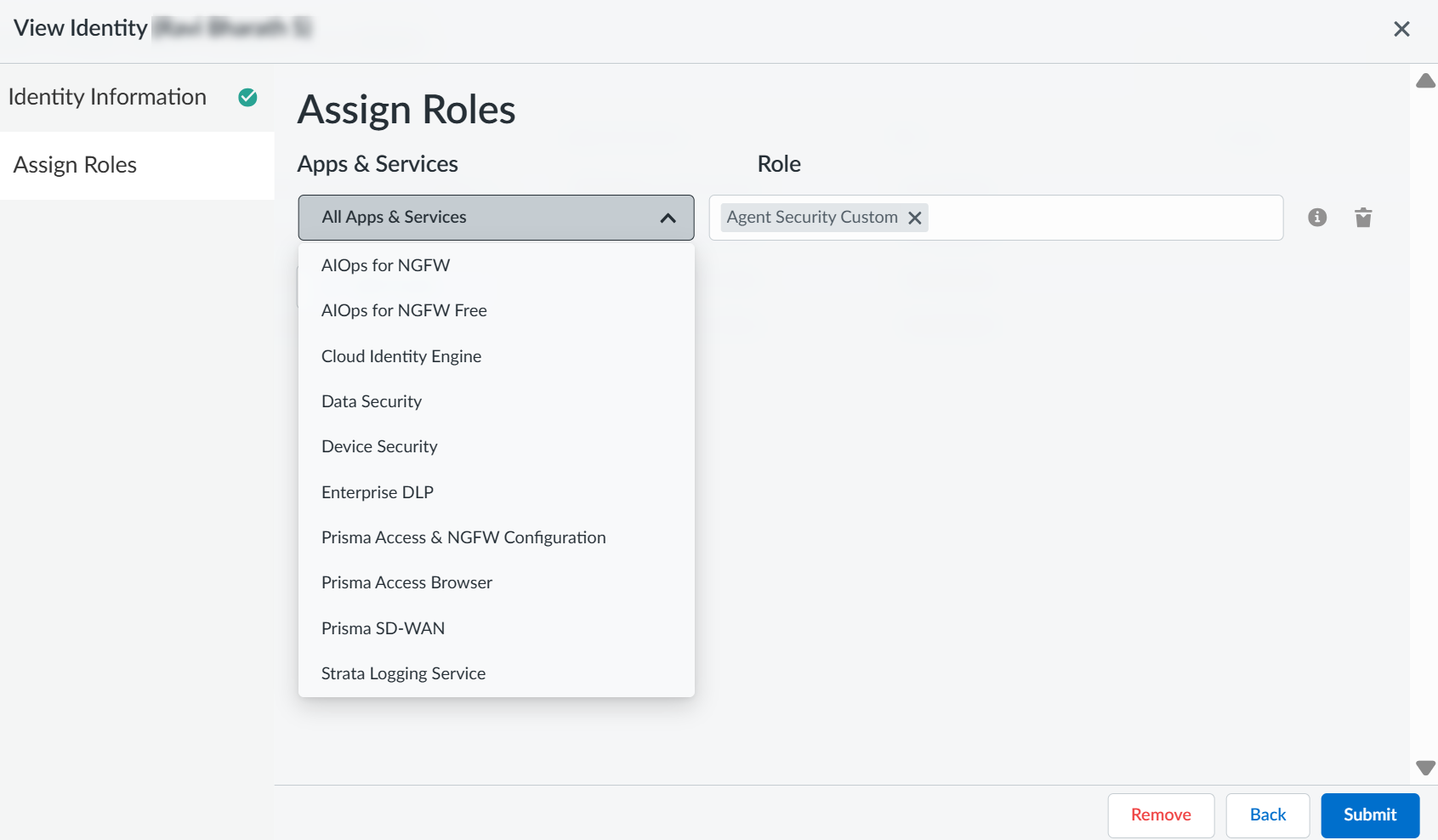
- Use one of the various ways to access Identity & Access.(New admins only) Add Access to your tenant where SaaS Agent Security is active.This step is required only if the user for which you’re granting SaaS Agent Security access isn't already registered with the Palo Alto Networks Customer Support Portal (CSP).Select RolesCustom Roles and add a custom role.
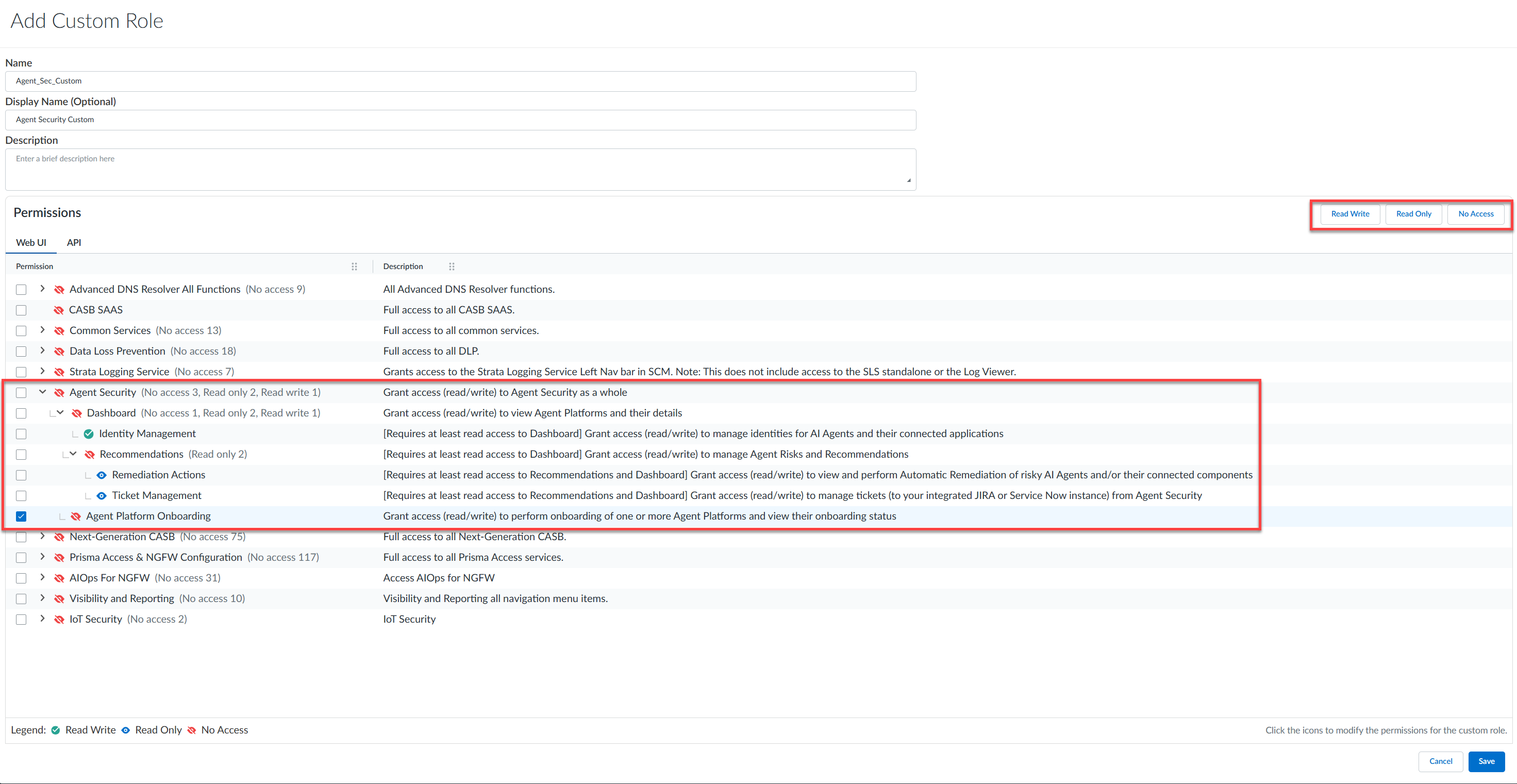
![]() For SaaS Agent Security, the permissions and their corresponding descriptions are given in the following table:PermissionsDescription
For SaaS Agent Security, the permissions and their corresponding descriptions are given in the following table:PermissionsDescriptionAgent Security Grant access (read/write) to Agent Security as a whole.Dashboard Grant access (read/write) to view Agent Platforms and their details.Identity Management Requires at least read access to DashboardGrant access (read/write) to manage identities for AI Agents and their connected apps.Recommendations Requires at least read access to DashboardGrant access (read/write) to manage Agent Risks and Recommendations.Remediation Actions Requires at least read access to Recommendations and DashboardGrant access (read/write) to view and perform Automatic Remediation of risky AI Agents and/or their connected components.Ticket Management Requires at least read access to Recommendations and DashboardGrant access (read/write) to manage tickets (to your integrated JIRA or Service Now instance) from Agent Security.Agent Platform Onboarding Grant access (read/write) to perform onboarding of one or more Agent Platforms and view their onboarding status.Assign the custom role you created to specific SaaS Agent Security users as per your need and Submit.![]()