SaaS Security
Configure WildFire Analysis
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Configure WildFire Analysis
Learn how to configure WildFire analysis on which WildFire Report depends.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
Data Security leverages a WildFire service to detect known and unknown malware for
supported file types. To provide you the visibility you need, Data Security
integrates with WildFire by using a predefined data pattern. This process is
known as WildFire analysis.
To
enable WildFire analysis:
- Enable file types.
- Enable contextual information.
- Configure policies for Wildfire analysis.
- Monitor malware scanning.
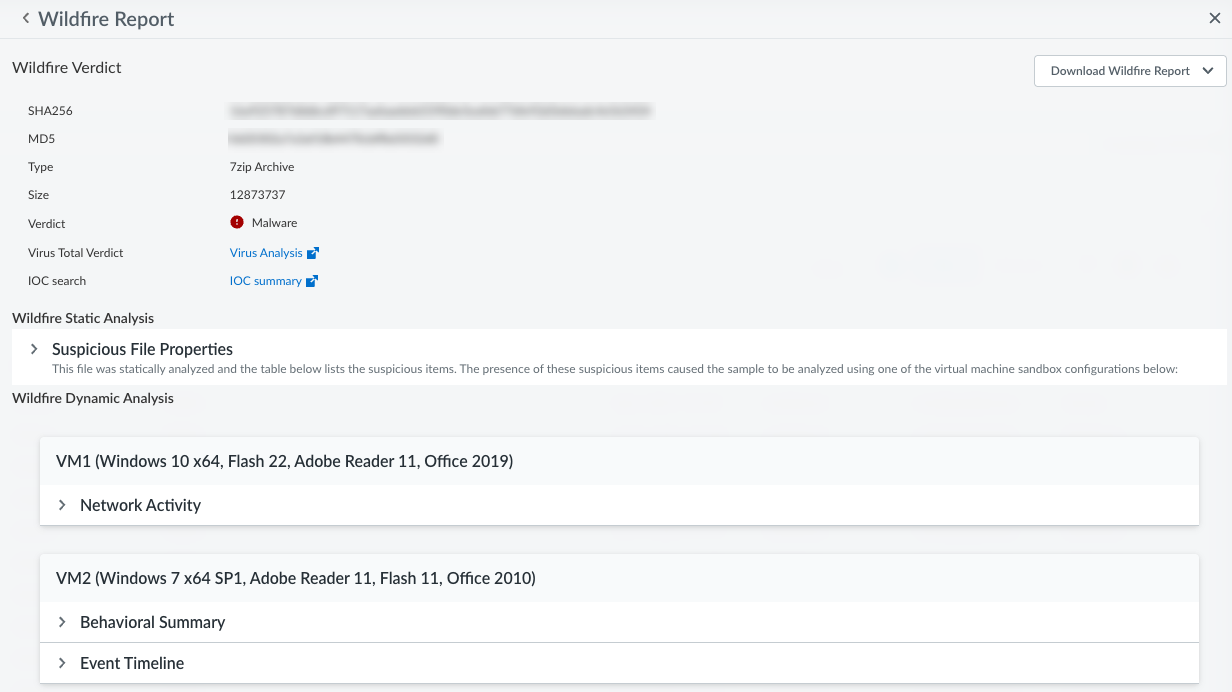
After you configure WildFire analysis, if WildFire detects malware on an asset, WildFire informs
Data Security and it flag the asset as a risk. From there, you can
track down threats using the WildFire Report on Data Security. Simply configure WildFire analysis to send files to
WildFire, then analyze the report.
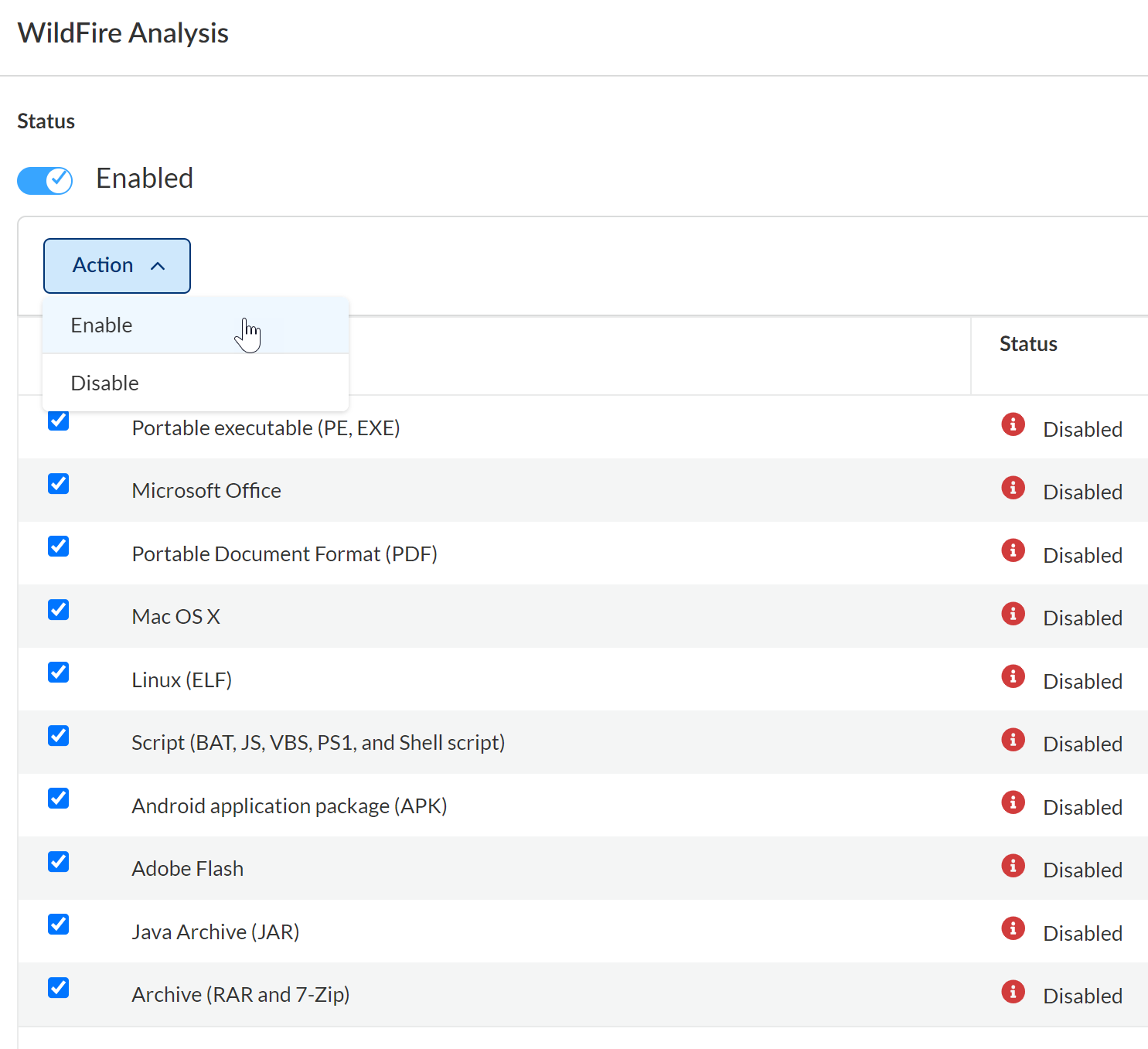
Enable File Types
Data Security enables you to submit files of specific file type categories to WildFire
for analysis, classification, and reporting. However, by default, Data Security does not submit any files for processing: you control
which file type categories apply to the WildFire service.
If you have privacy concerns with sharing specific file type categories, don’t select that file
category in Data Security. Data Security supports specific
file type categories, and the file types listed in parenthesis in the SaaS
Security web interface are examples.
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecuritySettingsScan SettingsWildFire Analysis.Locate the WildFire Analysis toggle and verify that WildFire is enabled.By default, Data Security enables WildFire analysis data pattern, but it’s possible that your organization disabled it previously.If any of your policies use the WildFire data pattern, you must remove the data pattern from those policies before you can disable WildFire analysis.Select the Files to Submit.
![]() After selecting the files, select ActionEnable.Data Security logs any changes to file type changes in the audit logs. If you want your changes to apply retroactively, initiate a rescan.
After selecting the files, select ActionEnable.Data Security logs any changes to file type changes in the audit logs. If you want your changes to apply retroactively, initiate a rescan.![]() Next step: Enable Contextual Information.
Next step: Enable Contextual Information.Enable Contextual Information
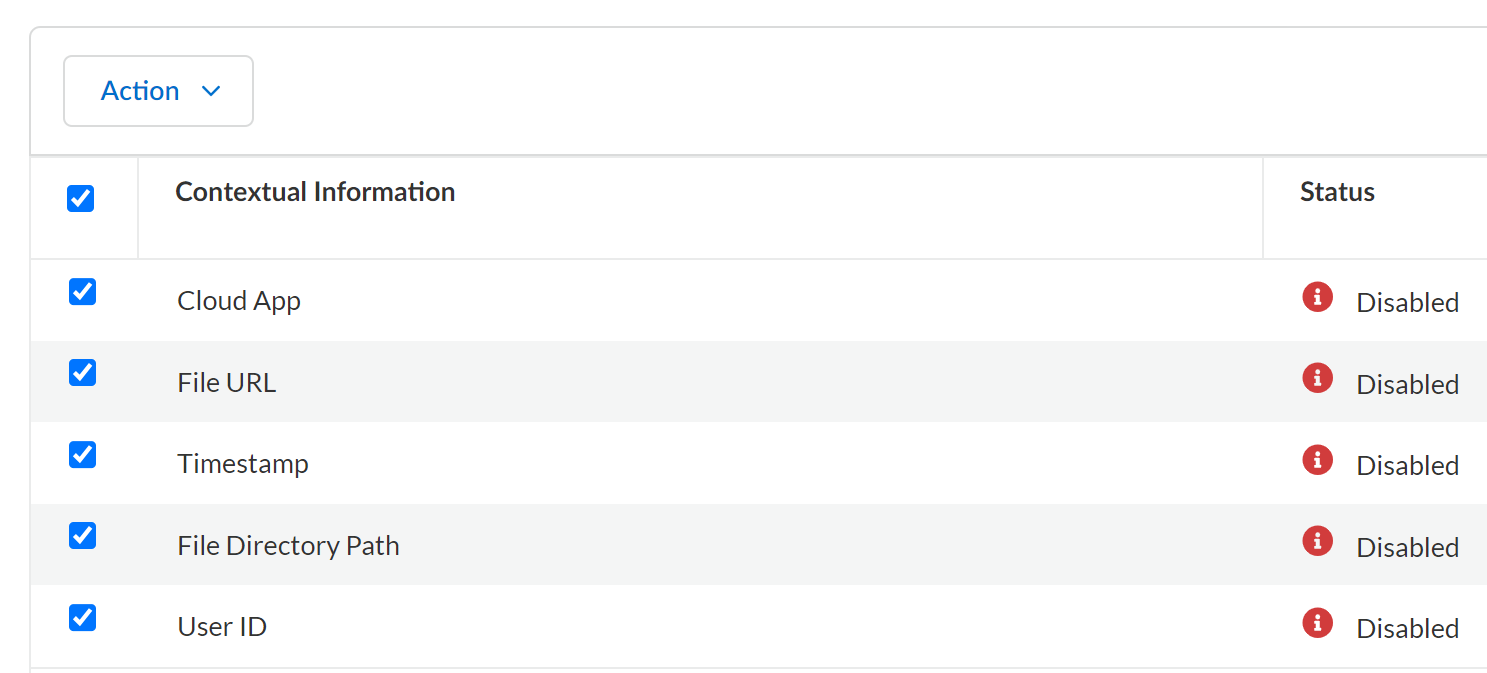
In addition to sending files to WildFire, Data Security enables you to send contextual information with the file so that your global administrator has the necessary context to the WildFire verdict, to determine and investigate threats. By default, Data Security does not send contextual information to WildFire.Palo Alto Networks recommends that you enable all contextual information. Data Security enables you to send your files to WildFire with contextual information.- Before you begin: Enable File Types.Log in to Strata Cloud Manager.Select ConfigurationSaaS SecuritySettingsScan SettingsWildFire Analysis.Specify the Contextual Information.
- Cloud App—Name of the SaaS application that you specified at the time of onboarding the app. For example, Box - HR or Box - HQ.
- File URL—the file path in Data Security.
- Timestamp—the latest update time on the file.
- File Directory Path—parent folder level.
- User ID—email address or username of file creator.
![]() After selecting the files, select ActionEnable.Data Security logs any changes to contextual information in the audit logs. If you want your changes to apply retroactively, initiate a rescan.Next step: Configure Policies for WildFire Analysis.
After selecting the files, select ActionEnable.Data Security logs any changes to contextual information in the audit logs. If you want your changes to apply retroactively, initiate a rescan.Next step: Configure Policies for WildFire Analysis.Configure Policies for WildFire Analysis
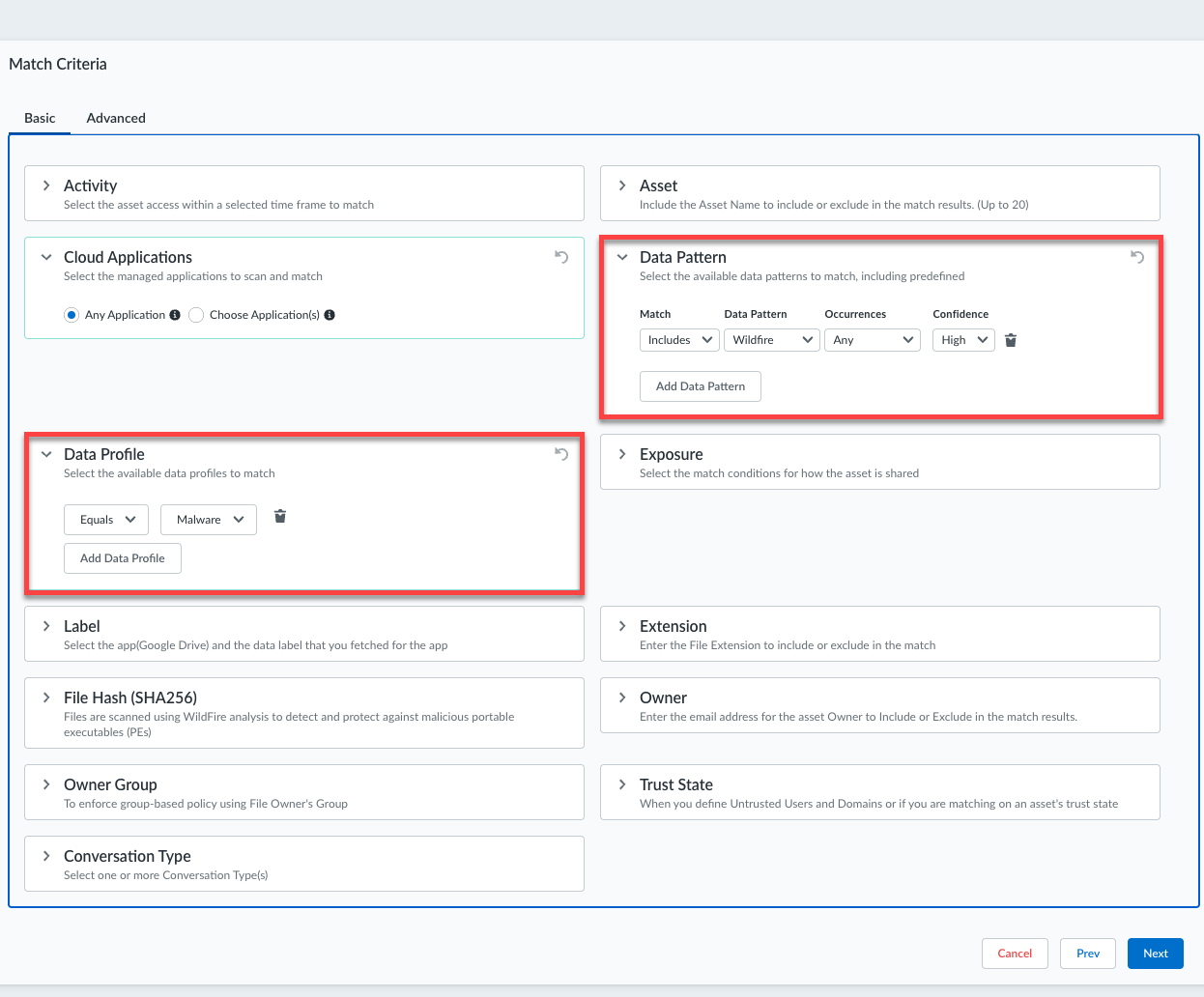
Data Security integrates with WildFire by using a predefined data pattern and predefined policy rule (WildFire).- Before you begin: Enable Contextual Information.Specify the WildFire Data Pattern or Malware Data Profile as match criteria in your policies.If you forget to specify the data pattern or data profile, your match results will not be accurate—they will include a large number of false positives.
![]() Next step: Monitor Malware Scanning.
Next step: Monitor Malware Scanning.Monitor Malware Scanning
Data Security enables you to track malware scanning for all file types configured for WildFire analysis. When you View Asset Details for such files, Data Security displays a malware scan status. - Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityIncidents.Select the data asset you want to monitor. It is now displayed under the Data Assets tab.Select the asset you want to monitor. Observe the Malware Verdict in the Details pane.
- Observe the Malware Verdict.
- Pending Analysis—Data Security is waiting for WildFire to analyze the file and return a verdict.
- Analyzed—WildFire analyzed the file and returned a verdict.
- Not Analyzed—WildFire did not analyze the file and an information icon next to the status displays an explanation. The most common reason for Not Analyzed is the file type is within an unsupported file type category for WildFire analysis.
- File Unavailable—File unavailable to Data Security. For example, when a file is quarantined by the cloud app.
![]() If WildFire detected malware, Track Down Threats with WildFire Report.
If WildFire detected malware, Track Down Threats with WildFire Report.