SaaS Security
View Asset Details
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
View Asset Details
Learn about how Data Security displays detailed information
about an asset violating a policy rule.
As Data Security scans your managed cloud apps and discovers content, you can view the
details on the console. Select Data SecurityData Assets. This page provides context into the findings so you can Assess Incidents and Monitor and Investigate User Activity across these applications.
The details for each incident vary depending on:
- Which cloud app retains the asset.
- Whether the asset is a file or a container (for example, a folder or a repository).
- The policy the asset violated.
- How the asset is shared.
- Whether users accessed the file or took other actions on the file.
Asset
Detail Description | ||
|---|---|---|
|
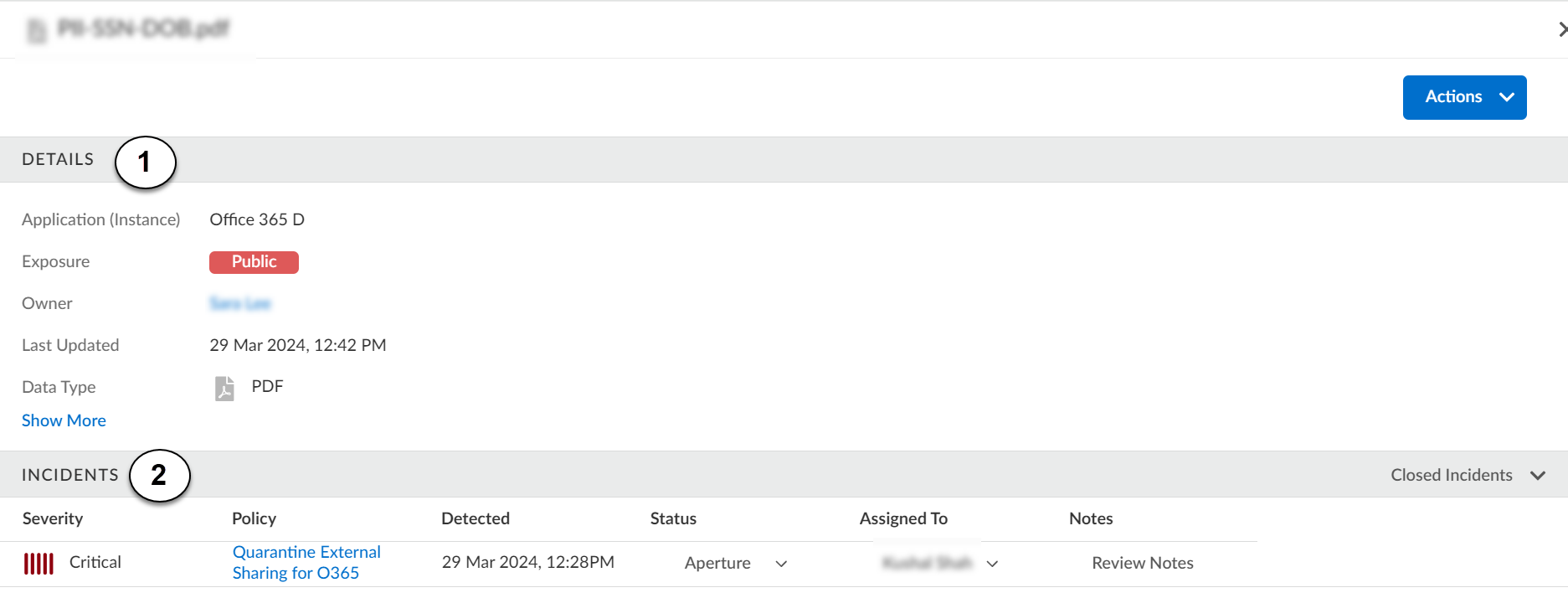
1
| Details | Summarizes asset file name, file type, exposure on cloud app, owner, and last updated
timestamp.
|
|
Actions
|
Lists available actions for an asset, depending on the cloud app and
admin role permissions:
| |
|
2
|
Incidents
|
Displays which data asset policy or policies that an asset violates,
the date Data Security identified the incident, the status
of the incident, and whether there have been previous incidents
associated with the asset. From here you can Assign Incidents to Another Administrator.
|
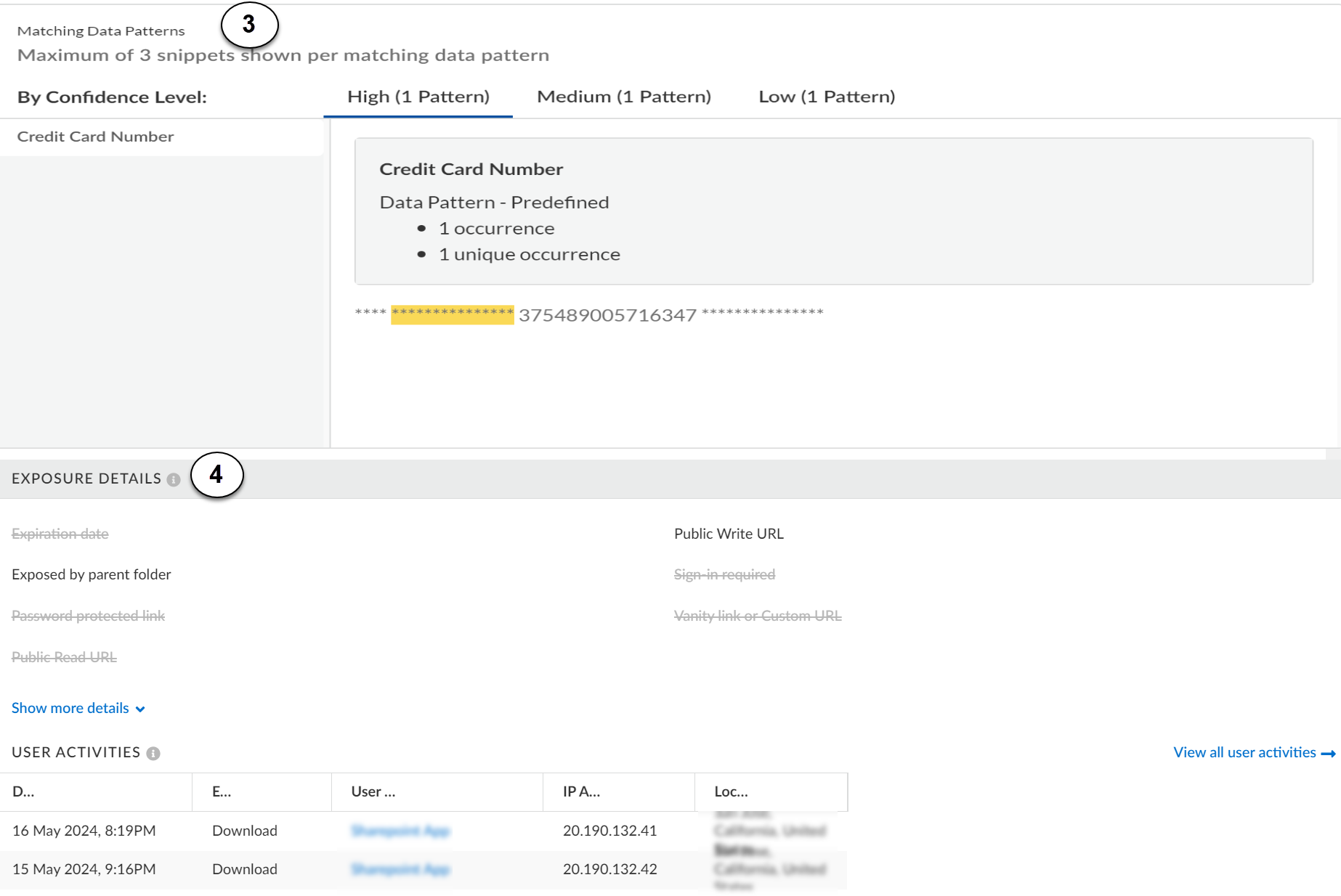
3 | Match Criteria |
Displays the data pattern that the asset matched, number of
occurrences, and date found. Administrators with Write
access for Request Snippets in
Common Services can view asset
snippets to view any available details about the asset
matching the data pattern.
For assets that match the WildFire Analysis rule, you can Use
the WildFire Report to Track Down Threats.
|
4 | Exposure Details |
Details how the asset is exposed (Published to the web, accessible by
a public URL, if sign-in is required, or the asset is exposed by a
parent folder). You can View Details to
access the asset URL, if available. Strike through text on
attributes denotes no exposure.
Lists information about the users who most recently interacted with
the file: Timestamp, event (for example, whether the user downloaded
the file), username, IP address, and location. You can
View all user activities to see details about this
event and all other events associated with this file.
Such information helps you investigate whether there is malicious or
inappropriate access to the file.
|
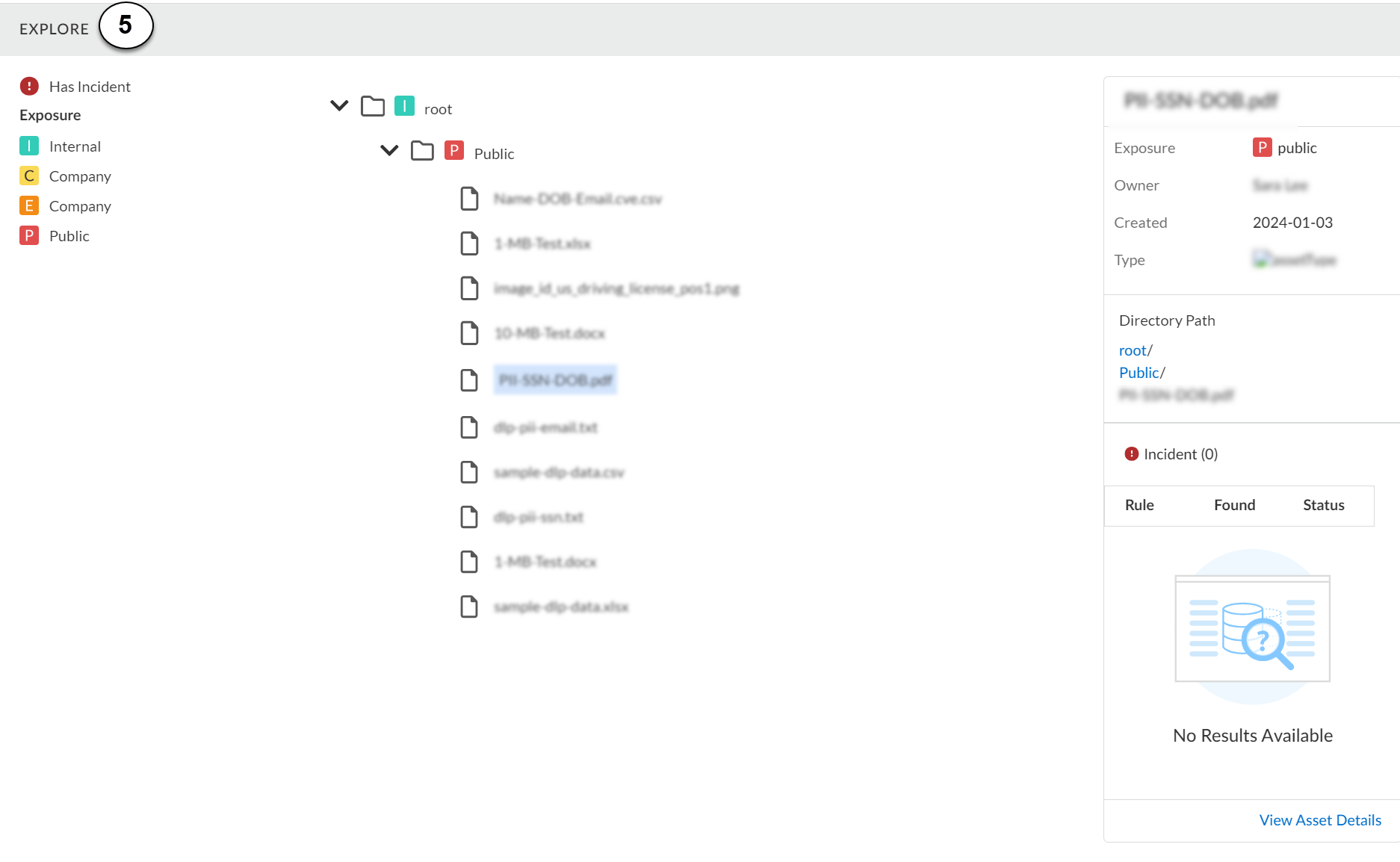
5 |
Explore
Explore on Cloud App
|
Displays the asset tree, policy violations, and exposure level for a
given asset. View the asset in the context of its file and folder
hierarchy to help you identify risks and inherited exposure.
Displays a list of collaborators (members) to help you identify who
has access to shared drives (Google Drive) or team folders (Dropbox)
and inherited exposure.
|
