SD-WAN
Configure Certificate-based Authentication for Strong Security
Table of Contents
Expand All
|
Collapse All
SD-WAN Docs
-
-
-
-
- 3.4
- 3.3
- 3.2
- 3.1
- 3.0
- 2.2
- 2.1
- 2.0
- 1.0
-
Configure Certificate-based Authentication for Strong Security
Configure SD-WAN devices with certificate-based authentication type
for strong security.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
You can authenticate an SD-WAN device using either of the following
two authentication types:
- (Default authentication type) Pre-shared key
- (SD-WAN plugin 3.2.0 and later releases) Certificate
When you create a new SD-WAN cluster or refresh the key with an SD-WAN plugin version earlier than 3.2.0, the SD-WAN
plugin generates the pre-shared key automatically. In addition to the pre-shared key
authentication type, we provide certificate-based authentication with SD-WAN plugin 3.2.0 and later releases for next-generation firewalls
to fulfill your security needs. Take your security to the next level with stronger
authentication and validation for all SD-WAN sites with
certificate-based authentication.
We support certificate-based authentication on all software and hardware devices
running legacy or advanced routing engines that support SD-WAN.
Follow the steps mentioned in the upgrade and downgrade considerations
before you upgrade or downgrade your current SD-WAN plugin.
Use the following workflow to configure certificate-based authentication for your SD-WAN device:
- Log in to the Panorama Web Interface.Generate a certificate for SD-WAN devices on Panorama.
- Select PanoramaCertificate ManagementCertificates.Create a self-signed root CA certificate or import a certificate from your enterprise CA. Based on the root CA, generate devices certificate for an SD-WAN device. We do not support SCEP-generated certificates.The generated certificate must be unique for each SD-WAN device. That is, you can't generate a certificate and share it among multiple SD-WAN devices.Keep the following in mind while generating the branch and hub firewall certificates that is used for SD-WAN tunnel authentication:
- Two different hub devices can use the same hub certificate.
- Two different branch devices can use the same branch
certificates if the following conditions are met:
- Branch devices are not part of the same VPN cluster
- There is no common hub device between the VPN clusters that these branch devices would be part of
- (HA deployments only) Two different branch devices can also have the same branch certificates if they are configured as HA members.
- If the hub device is common between VPN clusters, certificates for branch devices part of these VPN clusters should have unique certificates with all attributes having unique values. If you don't ensure the uniqueness of the certificate and its values, then commit will fail on the hub device (no commit failure on Panorama).
Also ensure that the leaf certificates (branch and hub firewall certificates) used for SD-WAN tunnel authentication are generated meeting the following criteria:- Key usage should have digital signatures.
- All certificates must be signed by the same root CA.
- The device certificate must be directly signed by the root CA.
- Certificate format should be PKCS12.
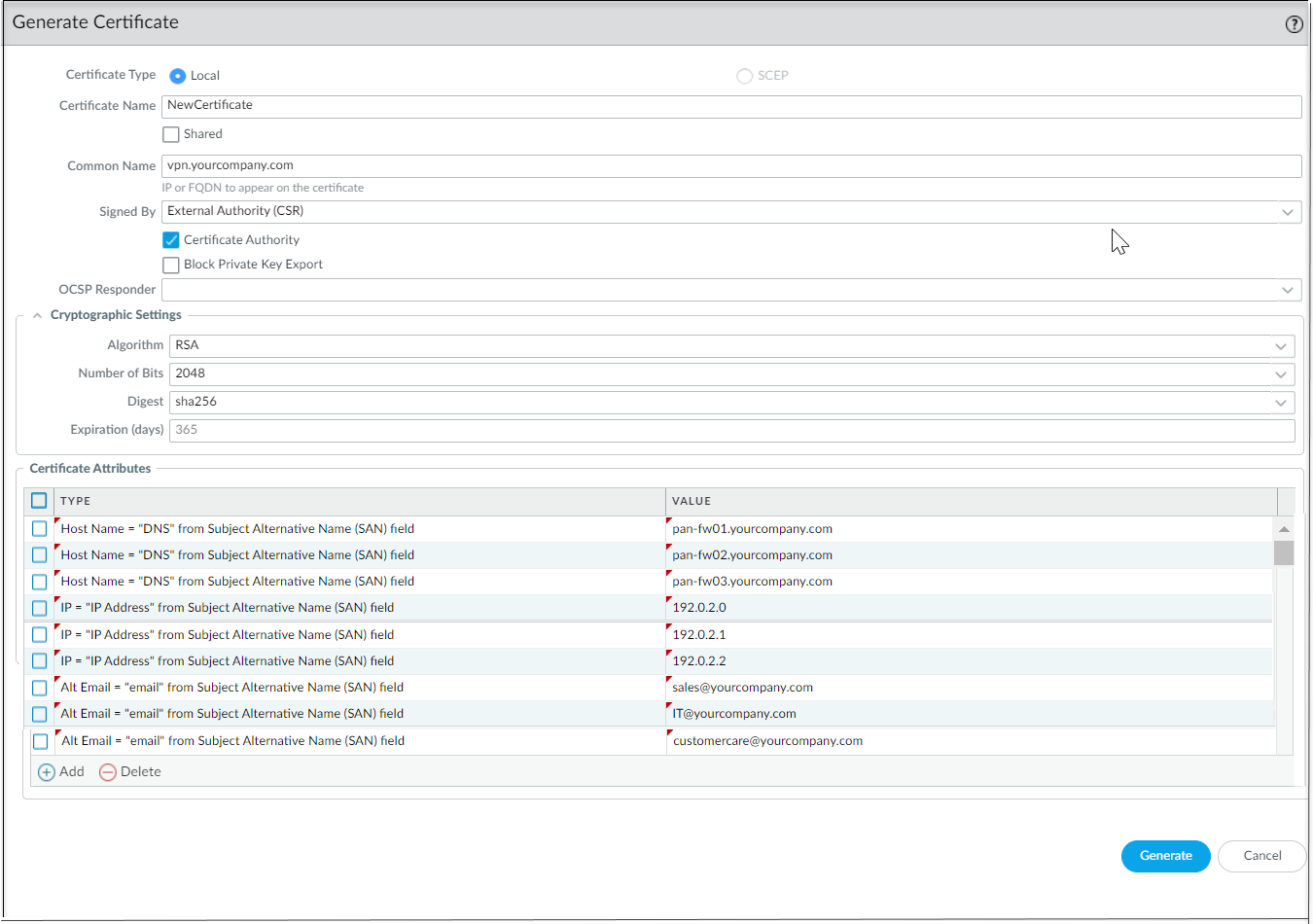
The certificate attributes are used for determining the local ID and peer ID for IKE gateways. Hence, the leaf certificates, that is, the branch and hub firewall certificates that are used for SD-WAN tunnel authentication must be generated with the following three certificate attributes and each certificate attribute should be assigned with three unique attribute values. Otherwise, a commit error will be thrown.- FQDN (Host Name)
- IP address (IP)
- User FQDN (Alt Email)
It's mandatory to have unique Host Name, IP, and Alt Email certificate attributes among all certificates. That is, none of the certificates should have these attribute values in common.In the below example, NewCertificate is generated with the total of nine mandatory certificate attributes. The Host Name certificate attribute is configured with three unique attribute values: pan-fw01.yourcompany.com, pan-fw02.yourcompany.com, and pan-fw03.yourcompany.com. The IP certificate attribute is configured with three unique attribute values: 192.0.2.0, 192.0.2.1, and 192.0.2.2. The Alt Email certificate attribute is configured with three unique attribute values: sales@yourcompany.com, IT@yourcompany.com, and customercare@yourcompany.com.![]() (Optional) Configure a Certificate Profile that includes the root CA and intermediate CA for secure server communication.
(Optional) Configure a Certificate Profile that includes the root CA and intermediate CA for secure server communication.- Select PanoramaCertificate ManagementCertificate Profile.Configure a certificate profile.If you configure an intermediate CA as part of the Certificate Profile, you must also include the root CA.This Certificate Profile defines how the SD-WAN hubs and the branches authenticate mutually.Import the CA certificates to validate the identity of the SD-WAN devices.
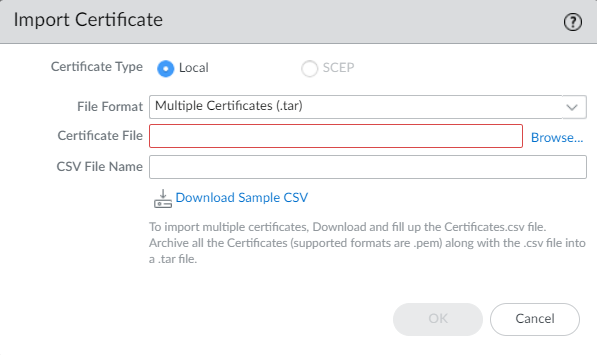
- PanoramaCertificate ManagementCertificatesImport the CA certificate and the key pair on Panorama for each SD-WAN device in a cluster or import multiple certificates using Multiple Certificates (.tar). Use CSV to bulk import the certificates into the Panorama management server. The CSV allows you to import multiple certificates at once, rather than adding each certificate manually.
![]() Commit your changes. It's important to commit after importing the certificates for the imported certificates to be available for further configuration.Configure a certificate-based authentication type while adding an SD-WAN hub or branch firewall to be managed by the Panorama management server. When adding your devices, you specify what type of device it is (branch or hub), an authentication type for the device, and you give each device its site name for easy identification.
Commit your changes. It's important to commit after importing the certificates for the imported certificates to be available for further configuration.Configure a certificate-based authentication type while adding an SD-WAN hub or branch firewall to be managed by the Panorama management server. When adding your devices, you specify what type of device it is (branch or hub), an authentication type for the device, and you give each device its site name for easy identification.- Select PanoramaSD-WANDevices to add an SD-WAN device (SD-WAN hub or branch firewall) to be managed by the Panorama management server.Select the VPN Tunnel tab and configure the authentication type. For certificate-based authentication, select Certificate and configure the certificate-related fields. It's mandatory to select an authentication type while adding an SD-WAN device.Configure certificate-based authentication when onboarding PAN-OS firewalls to Prisma Access.
- Select PanoramaSD-WANDevices to select the SD-WAN branch firewall to connect to the Prisma Access hub and configure the connection.Select Prisma Access Onboarding and Add a compute node to a Region. In the VPN Tunnel, it's mandatory to select the authentication type to authenticate the CN (Prisma Access hub). For certificate-based authentication, select Certificate as the Authentication type and configure the certificate-related fields. It's mandatory to select an authentication type while onboarding PAN-OS firewalls to Prisma Access.Ensure that you select the same authentication type for all the branch devices and the Prisma Access hub that is added. A commit failure occurs on Panorama if you try to use different authentication types for the branch and the Prisma hub.Configure certificate-based authentication while planning your topology for SD-WAN with Auto VPN.
- Select PanoramaSD-WANVPN Clusters.Select the VPN cluster Type.Select the Authentication Type as Certificate. It's mandatory to specify the authentication type to add a device in a VPN cluster. A VPN cluster should have the same authentication type selected for all its devices. You can't change the authentication type of an SD-WAN device that has been added to a VPN cluster already. If you want to change, then remove the VPN cluster and its SD-WAN devices and configure it again with the authentication type of your choice. By default, we support the pre-shared key authentication type for the devices in a VPN cluster (if you have not selected the certificate type manually).Commit your configuration changes.Select Push to Devices to push your configuration changes to your managed firewalls.