Next-Generation Firewall
Import a Certificate and Private Key
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Import a Certificate and Private Key
Follow this procedure to import a certificate and private key from an enterprise
CA.
If your enterprise has its own public key infrastructure
(PKI), you can import a certificate and private key into the firewall from your
enterprise certificate authority (CA). Enterprise CA certificates (unlike most
certificates purchased from a trusted, third-party CA) can automatically issue CA
certificates for applications such as SSL/TLS decryption or large-scale
VPN.
On a Palo Alto Networks firewall or Panorama, you can import
self-signed certificates only if they are CA certificates.
Instead of
importing a self-signed root CA certificate into all the client systems, it is a
best practice to import a certificate from the enterprise CA because the clients
will already have a trust relationship with the enterprise CA, which simplifies
the deployment.
If the certificate you will import is part of a
certificate chain, it is a best practice to import the entire chain.
- From the enterprise CA, export the certificate and private key that the firewall will use for authentication.When exporting a private key, you must enter a passphrase to encrypt the key for transport. Ensure the management system can access the certificate and key files. When importing the key onto the firewall, you must enter the same passphrase to decrypt it.Select DeviceCertificate ManagementCertificates, then Device Certificates (PAN-OS 11.2 and earlier) or Custom Certificates (PAN-OS 12.1.0 and later).If the firewall has more than one virtual system (vsys), select a Location (vsys or Shared) for the certificate.Click Import and enter a Certificate Name. The name is case-sensitive and can have up to 63 characters on the firewall or up to 31 characters on Panorama. It must be unique and use only letters, numbers, hyphens, and underscores.To make the certificate available to all virtual systems, select the Shared check box. This check box appears only if the firewall supports multiple virtual systems.Enter the path and name of the Certificate File received from the CA, or Browse to find the file.Select a File Format:
- Encrypted Private Key and Certificate (PKCS12)—This is the default and most common format, in which the key and certificate are in a single container (Certificate File). If a hardware security module (HSM) will store the private key for this certificate, select the Private key resides on Hardware Security Module check box.
- Base64 Encoded Certificate (PEM)—You must import the key separately from the certificate. If a hardware security module (HSM) stores the private key for this certificate, select the Private key resides on Hardware Security Module check box and skip the next step. Otherwise, select the Import Private Key check box, enter the Key File or Browse to it, then continue to the next step.(Panorama managed firewalls) You are required to Import Private Key if you enabled Block Private Key Export when the certificate was generated to successfully push configuration changes from the Panorama management server to managed firewalls.
- (SD-WAN IKEv2 Certificate Authentication Support) (Beginning with SD-WAN 3.2.0 Release) Multiple Certificates (.tar)—Contains multiple certificates archived in a tar format.Use CSV file to bulk import the certificates into the Panorama management server. Follow these steps if you select Multiple Certificates (.tar).
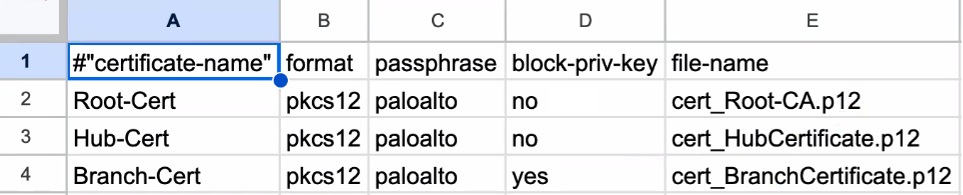
- Download Sample CSV to download and save
the Certificates.CSV template. Populate
the template with certificate related information: certificate
name, format, passphrase, block private key, and file
name.Following is a sample Certificates.CSV:
![]()
- Enter the certificate file name with an extension. The file name should exactly match the certificate that you will be uploading to the device.
- All the certificate fields are case-sensitive except the format and passphrase field.
- To import multiple certificates, archive all the certificates and the populated Certificates.CSV file in .tar format. Browse and select a .tar file to bulk import the Certificate File. Certificate format .PKCS12 is supported. The size of the archive(.tar) file should be less than 10MB. Ensure that the extension of the tar file is .tar.All the certificates must be signed by the same CA within the SD-WAN VPN cluster. You must import the CA certificate along with the device certificate. Device certificate must be directly signed by the root CA (no intermediate certificates are allowed).
- You must commit after bulk import for the certificates to be available for further configuration.
- Download Sample CSV to download and save
the Certificates.CSV template. Populate
the template with certificate related information: certificate
name, format, passphrase, block private key, and file
name.
Enter and re-enter (confirm) the Passphrase used to encrypt the private key.Click OK. The Device Certificates page displays the imported certificate.