Next-Generation Firewall
Rule Cloning Migration Use Case: Web Browsing and SSL Traffic
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Rule Cloning Migration Use Case: Web Browsing and SSL Traffic
Example of migrating port-based Security policy rules
for web browsing and SSL traffic to app-based rules without affecting
application availability.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
This is a core Network Security feature for NGFWs and Prisma
Access; no prerequisites needed.
|
A port-based rule that allows web access on
TCP ports 80 (HTTP web-browsing) and 443 (HTTPS SSL) provides no
control over which applications use those open ports. There are
many web applications, so a general rule that allows web traffic
allows thousands of applications, many of which you don’t want on
your network.
This use case shows how to migrate a port-based
policy that allows all web applications to an application-based
policy that allows only the applications you want, so you can safely
enable the applications you choose to allow. For rules that see
a lot of applications, cloning the original port-based rule is safer than
adding applications to the rule because adding replaces the port-based
rule, so if you inadvertently forget to add a critical application,
you affect application availability. And if you Match
Usage, which also replaces the port-based rule, you
allow all of the applications the rule has seen, which could be
dangerous, especially with web browsing traffic.
Cloning
the rule retains the original port-based rule and places the cloned
rule directly above the port-based rule in the rulebase, so you
can monitor the rules. Cloning also allows you to split rules that
see a lot of different applications—such as a port-based web traffic
rule—into multiple application-based rules so you can treat different
groups of applications differently. When you’re sure you’re allowing
all the applications you need to allow in the cloned rule (or rules),
you can remove the port-based rule.
This example clones a
port-based web traffic rule to create an application-based rule
for web-based file sharing traffic (a subset of the application
traffic seen on the port-based rule).
This example does
not apply to using the New App Viewer to clone
App-ID Cloud Engine (ACE) applications (see the ACE documentation for
examples of how to do this); ACE requires a SaaS Security Inline license.
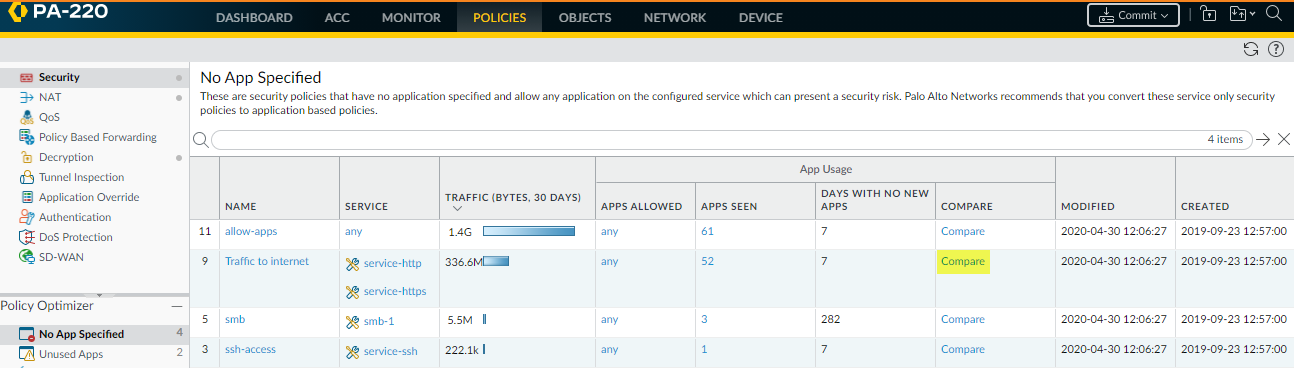
- Navigate to PoliciesSecurityPolicy OptimizerNo App Specified to view the port-based rules.Click Compare for the rule you want to migrate.In this example, the port-based rule that allows web access is named Traffic to internet.
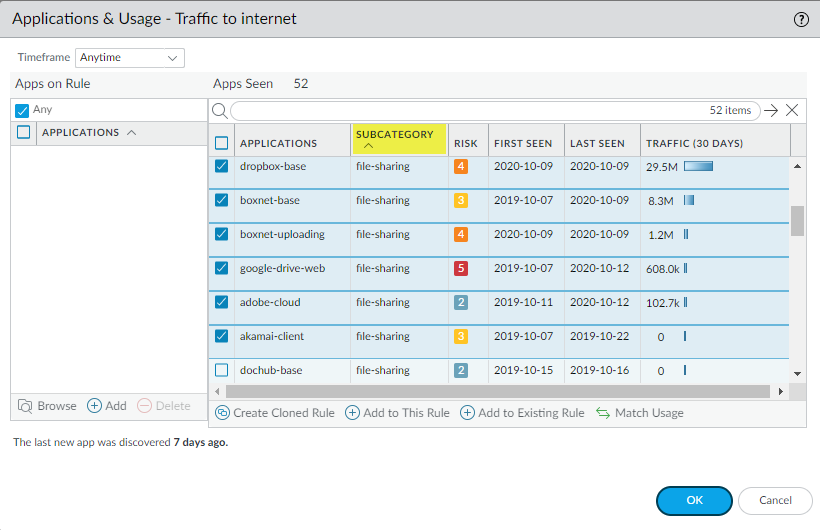
![]() Use the sorting options to review and select the applications you want to allow from Apps Seen.The number of Apps Seen is updated approximately every hour, so if you don’t see as many applications as you expect, check again after about an hour. Depending on the firewall’s load, it may take longer than one hour for these fields to update.For example, click Subcategory to sort the applications, scroll to the file-sharing subcategory, and then select the applications you want to allow. Alternatively, you can filter (search) for file-sharing applications.
Use the sorting options to review and select the applications you want to allow from Apps Seen.The number of Apps Seen is updated approximately every hour, so if you don’t see as many applications as you expect, check again after about an hour. Depending on the firewall’s load, it may take longer than one hour for these fields to update.For example, click Subcategory to sort the applications, scroll to the file-sharing subcategory, and then select the applications you want to allow. Alternatively, you can filter (search) for file-sharing applications.![]() Click Create Cloned Rule and Name the cloned rule (file-sharing-apps in this example).Create Cloned Rule shows the selected applications shaded green, the container apps shaded gray, individual applications in the container that haven’t been seen on the rule in italics, and individual applications that have been seen on the rule in normal text font. Scrolling through Applications shows all the container apps and their individual applications.
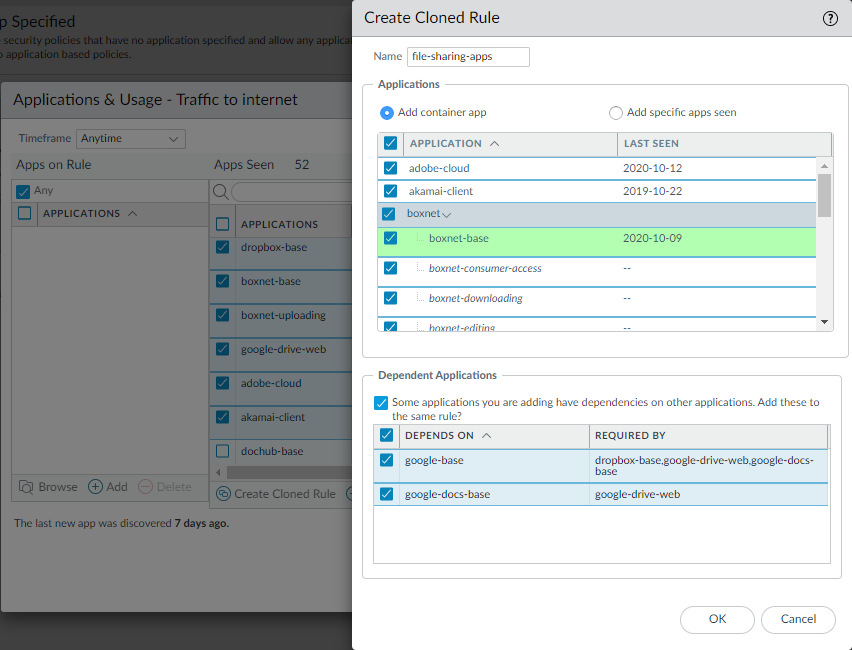
Click Create Cloned Rule and Name the cloned rule (file-sharing-apps in this example).Create Cloned Rule shows the selected applications shaded green, the container apps shaded gray, individual applications in the container that haven’t been seen on the rule in italics, and individual applications that have been seen on the rule in normal text font. Scrolling through Applications shows all the container apps and their individual applications.![]() Create Cloned Rule also shows the dependent applications for the selected applications. In this example, some of the selected applications require (Required By) the google-base and google-docs-base applications to run.Select the applications you want in the cloned rule.For applications you don’t want to include, uncheck the corresponding box, which also unchecks the container app. If you don’t include the container app, then when new apps are added to the container, they won’t automatically be added to the rule.If you uncheck the container app, all the individual applications in the container are unchecked and you must select the apps you want to add manually.Click OK to create the cloned rule.In PoliciesSecurity, the cloned rule (file-sharing-apps) is inserted in the rulebase above the original port-based rule (Traffic to internet).
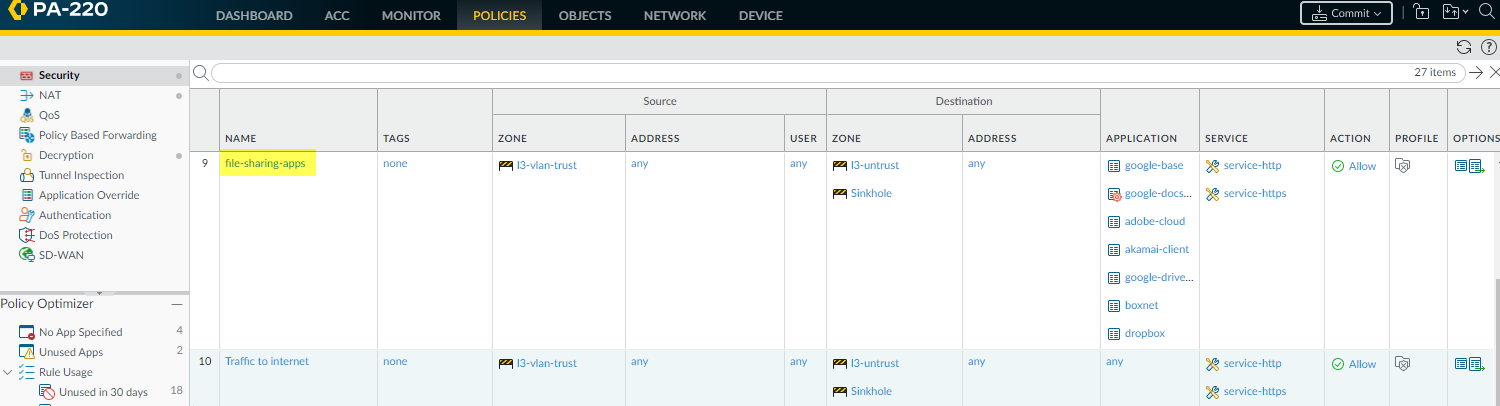
Create Cloned Rule also shows the dependent applications for the selected applications. In this example, some of the selected applications require (Required By) the google-base and google-docs-base applications to run.Select the applications you want in the cloned rule.For applications you don’t want to include, uncheck the corresponding box, which also unchecks the container app. If you don’t include the container app, then when new apps are added to the container, they won’t automatically be added to the rule.If you uncheck the container app, all the individual applications in the container are unchecked and you must select the apps you want to add manually.Click OK to create the cloned rule.In PoliciesSecurity, the cloned rule (file-sharing-apps) is inserted in the rulebase above the original port-based rule (Traffic to internet).![]() Click the rule name to edit the cloned rule, which inherits the properties of the original port-based rule.On the Service/URL Category tab, delete service-http and service-https from Service.This changes the Service to application-default, which prevents applications from using non-standard ports and further reduces the attack surface.If business needs require you to allow applications (for example, internal custom applications) on non-standard ports between particular clients and servers, restrict the exception to only the required application, sources, and destinations. Consider rewriting custom applications so they use the application default port.On the Source, User, and Destination tabs, tighten the rule to apply to only the right users in only the right locations (zones, subnets).For example, you may decide to limit web file sharing activity to only the user groups that have business reasons to share files across the web.Click OK.Commit the configuration.Repeat the process for other application categories in the port-based web access rule until your application-based rules allow only the applications you want to allow on your network.When traffic you want to allow stops hitting the original port-based rule for a sufficient amount of time to be confident that the port-based rule is no longer needed, you can remove the port-based rule from the rulebase.
Click the rule name to edit the cloned rule, which inherits the properties of the original port-based rule.On the Service/URL Category tab, delete service-http and service-https from Service.This changes the Service to application-default, which prevents applications from using non-standard ports and further reduces the attack surface.If business needs require you to allow applications (for example, internal custom applications) on non-standard ports between particular clients and servers, restrict the exception to only the required application, sources, and destinations. Consider rewriting custom applications so they use the application default port.On the Source, User, and Destination tabs, tighten the rule to apply to only the right users in only the right locations (zones, subnets).For example, you may decide to limit web file sharing activity to only the user groups that have business reasons to share files across the web.Click OK.Commit the configuration.Repeat the process for other application categories in the port-based web access rule until your application-based rules allow only the applications you want to allow on your network.When traffic you want to allow stops hitting the original port-based rule for a sufficient amount of time to be confident that the port-based rule is no longer needed, you can remove the port-based rule from the rulebase.